In today's interconnected digital world, managing identity and access to web applications and services has become more complex and challenging than ever. This is where identity and access management (IAM) protocols such as Security Assertion Markup Language (SAML) and Open Authorization (OAuth) come into play.
SAML and OAuth are widely used industry standards that enable secure identity and access management for web applications and services. And while these two protocols have some similarities, they are designed for different use cases and have distinct features. In this article, we will explore the differences and similarities between SAML and OAuth, and whether they can be used together.
What is SAML?
Security Assertion Markup Language (SAML) is an open standard for authentication that allows users or devices to log in to different web applications with just one pair of credentials. Utilizing Extensible Markup Language (XML), SAML transfers identity data between the Identity Provider and Service Provider.
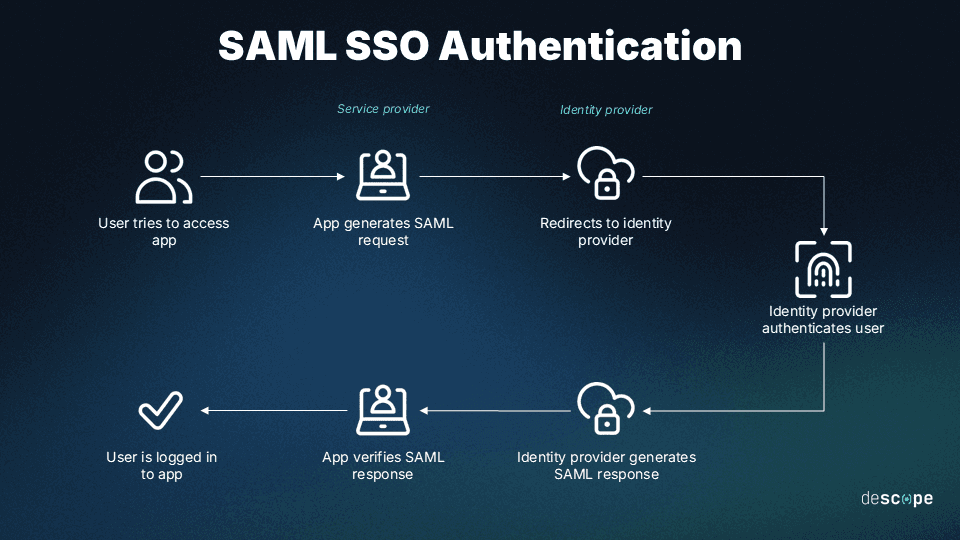
Here’s an overview of how SAML works in practice:
A user attempts to log in to a website, i.e. the Service Provider (SP)
The SP generates an authentication request (SAML Request) and sends it to the Identity Provider (IdP)
The IdP authenticates the user and creates a SAML Response, which includes the user's identity and authorization information
The IdP digitally signs the SAML Response and sends it back to the SP
The SP receives the SAML Response and verifies the digital signature to ensure it came from a trusted IdP
The SP extracts the authentication and authorization data from the SAML Response and creates a new session for the user
The user is redirected to the original SP website and is now logged in.
In summary, SAML allows a user to access multiple web applications using a single set of login credentials. For this reason, SAML plays a key role in the technology behind single sign-on (SSO) and other federated identity systems.
What is OAuth?
OAuth—short for “Open Authorization”—is an open, token-based authorization standard. It is used to delegate access to resources on behalf of users without sharing their credentials.
It works by delegating user authentication to the service that hosts the user account, and authorizing third-party applications to access that user's resources using access tokens. OAuth is widely used in social media, mobile applications, and APIs.
Let's say you want to use a third-party app, such as Buffer, to schedule posts for your Twitter account. Buffer uses OAuth to allow you to connect your Twitter account without having to share your login credentials with the app.
Here's how it works:
You sign up for Buffer and link your Twitter account to your Buffer account.
When you click on your Twitter account in Buffer to authorize it, Buffer sends a request to Twitter's authorization server using OAuth.
The Twitter authorization server prompts you to log in to your Twitter account and authorize Buffer to access your account information and post content on your behalf.
If you authorize Buffer, the Twitter authorization server generates an access token and sends it back to Buffer.
Buffer uses the access token to access your Twitter account and perform actions on your behalf, such as posting updates, scheduling posts, and analyzing engagement metrics.
If you revoke access, Twitter invalidates the access token, and Buffer will no longer be able to access your Twitter account.
In summary, OAuth allows third-party applications to access a user's resources on another website without having to know the user's username and password.
Differences between SAML and OAuth
While both protocols are in the realm of authentication and authorization, they have different strengths and applications, with SAML being more geared towards enterprise applications and federated identity, and OAuth being more suited for delegation of authorization to third-party applications.
Different purpose: The purpose of SAML and OAuth is different. SAML is primarily designed for authentication, authorization, and SSO, while OAuth is designed for authorization and delegation.
Different protocols: SAML uses the HTTP POST or HTTP Redirect binding, while OAuth uses the HTTP protocol with the Authorization and Access Token endpoints.
Different data formats: SAML uses XML-based messages, while OAuth uses JSON-based messages.
Different auth flow: The authentication and authorization flow of SAML and OAuth are different. SAML uses a browser-based flow, while OAuth uses a server-to-server flow.
Different security models: SAML relies on digital certificates and public and private keys, while OAuth relies on access tokens and refresh tokens.
| SAML | OAuth |
|---|---|---|
Purpose | Authentication | Authorization |
Data exchange format | XML | JSON |
Communication
| Between an identity provider and a service provider | Between a user, a client application, an authorization server, and a resource server |
SSO-Capable | Yes | Requires an authentication layer (e.g. OpenID Connect) |
Use Cases | Federated identity and single sign-on (SSO) for enterprise applications
| Authorization delegation for third-party apps to access user data |
Security | Uses digital signatures and encryption to secure the data exchange
| Relies on HTTPS encryption and bearer tokens for security |
Can SAML be used with OAuth?
Yes, SAML and OAuth can be used together to provide a more comprehensive authentication and authorization mechanism. Combining SAML and OAuth can provide benefits such as improved security, user experience, and access control.
For example, by using SAML for SSO and OAuth for authorization, an organization can improve security by reducing the number of login credentials users need to remember. Additionally, by using OAuth, users can delegate access to their resources without having to share their credentials, which improves the user experience.
Combining SAML and OAuth
Here’s an example of how SAML and OAuth can be put into action together.
A user pays for a subscription to a news site that keeps its content behind a paywall and requires authentication before revealing it. When the user attempts to log in, the news site generates a SAML request and sends it to the IdP. The IdP generates a SAML response, and if verified, the SP logs in the user and allows them to browse news articles.
While reading an article, the user decides they’d like to post it on their social media platform, facilitated by OAuth. After clicking “Share”, the authorization server collects the user’s consent and authorizes the news site to share the article on social media for them.
For the end user, the authentication and authorization processes involved merely a few clicks.
Drag-and-drop auth with Descope
While SAML and OAuth are important industry standards, implementing them can quickly become complex and time-consuming for application developers. Descope helps developers easily add authentication and user management to their apps with a few lines of code.
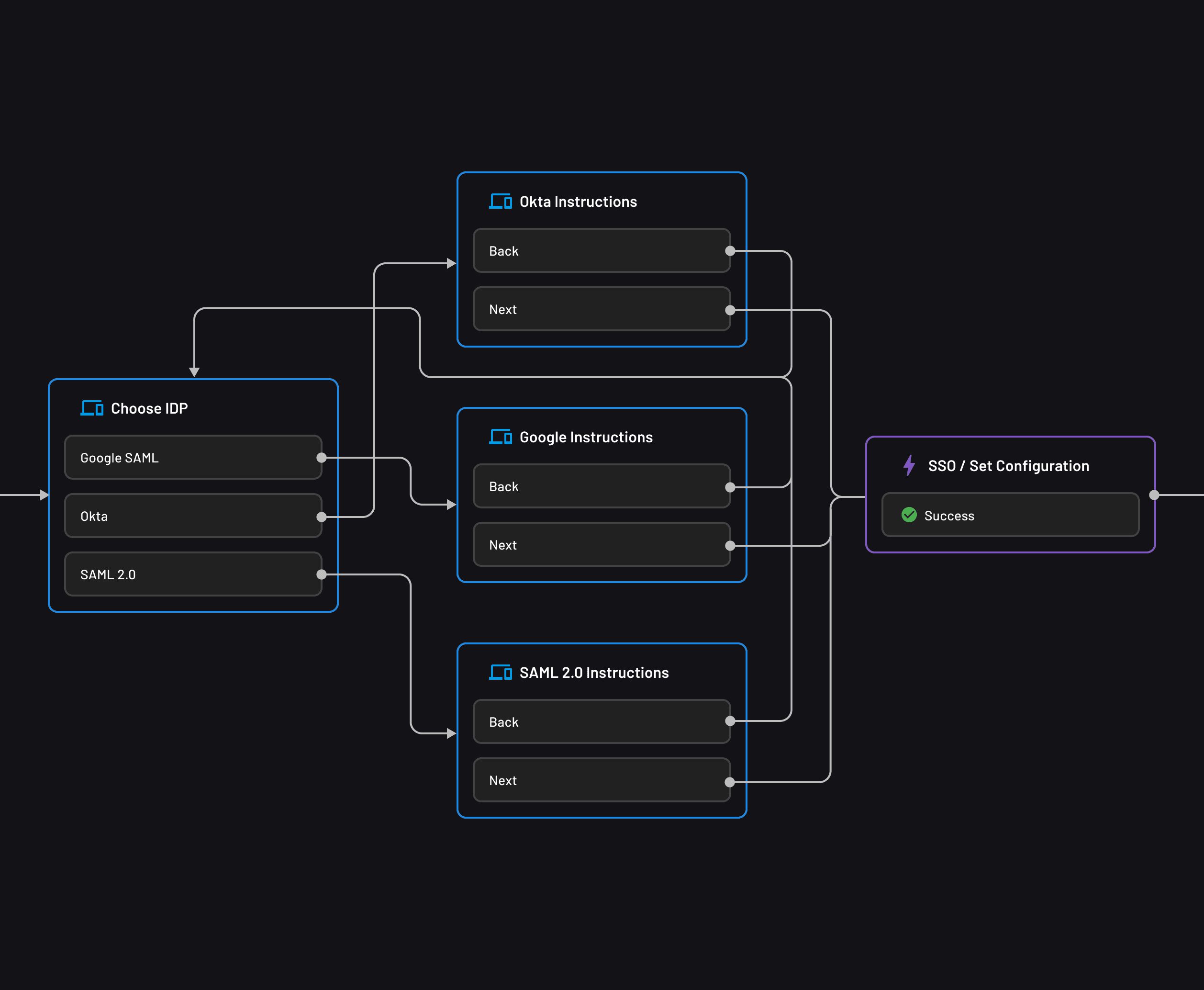
Using our drag-and-drop workflow editor, app builders can create authentication flows and login screens for SAML SSO, social logins, and many other authentication methods. Sign up for Descope to “descope” authentication from your daily work.