Table of Contents
What is SAML?
Security Assertion Markup Language (SAML) is a cornerstone for sharing authentication and authorization data between different systems. We'll cover the fundamentals of SAML, showing its role in facilitating safe communications between users and web services without sacrificing convenience.
But before we dive into SAML specifics, knowing the following terms is essential:
Identity Provider (IdP): The IdP is the entity responsible for verifying the identity of the user and passing along the authentication and authorization to the service provider (SP). Common IdPs include Azure Active Directory and Okta.
Service Provider (SP): The SP is the entity that the user is trying to access. The SP receives the data from the IdP and grants the user access. Some applications, like Salesforce or Descope, can act as both IdPs and SPs.
SAML assertion: An SAML assertion, an XML document sent from the IdP to the SP, contains user data in three forms: authentication, attribute, and authorization decision assertions.
What is SAML?
SAML is an open standard that uses Extensible Markup Language (XML) to pass user data between web-based IdPs and SPs. It acts as the intermediary that verifies user credentials with IdPs, ensuring swift and secure access to resources and applications.
It is commonly used for Single Sign-On (SSO) and other forms of federated identity management, which allow users to access multiple web applications with a single set of credentials. This simplifies the login process while relieving application owners of the complexities of user authentication.
The first version of SAML, SAML 1.0, was released in November 2001. It laid the foundation for secure identity and attribute exchange in web-based applications. In March 2005, SAML 2.0 was published, introducing more robust security features, greater flexibility, and broader adoption. SAML 2.0 remains the most widely used version today.
The protocol continues to evolve, with updates and extensions to address emerging security challenges and changing technology landscapes. The SAML authentication market is projected to grow to $3.1 billion by 2030.
B2B Enterprise Readiness Checklist
Score your tech stack on enterprise readiness pillars - from dev and IT experience to security and architecture.
Download
SAML vs. SSO
While SAML and SSO are closely related and often confused, they are not the same. In essence, SAML is one of the protocols that governs SSO implementation.
SSO is a user authentication method that allows a user to access multiple applications with one set of credentials. SAML is one of several protocols (others include OAuth and OpenID Connect) that can be used for SSO.
SAML vs. OAuth
While both protocols deal with authentication and authorization, they excel in different areas. SAML is well-suited for enterprise applications and establishing trust between organizations in federated identity scenarios. In contrast, OAuth authorizes third-party applications to access user data securely.
Imagine you're going to Six Flags amusement park. When you arrive, the park staff will check two things before letting you in: your ID and your ticket.
First, they'll look at some form of government-issued identification (like a driver's license) to ensure you are who you claim to be. This is similar to how SAML works – it verifies your identity.
Second, they'll check your ticket, which determines the type of access you have within the park. Your ticket might grant access to the fast lane, unlimited rides, or VIP areas. This is like OAuth, as it controls what actions or resources you're authorized to use.
Read more: SAML vs OAuth Differences Explained
| SAML | OAuth |
|---|---|---|
Purpose | Secure data exchange for authentication and authorization in web-based applications. | Delegated authorization for third-party access to user data without exposing credentials. |
Data Format | XML-based assertions | JSON Web Tokens (e.g., access tokens, refresh tokens) |
Primary Use Cases | SSO and federated identity management | API authorization and delegated access to user data |
Applications | Mainly used in web-based applications and SSO scenarios. | Primarily used to secure APIs and enable third-party app integrations. Also useful for mobile applications. |
SAML vs LDAP
SAML and Lightweight Directory Access Protocol (LDAP) serve different purposes and have distinct features and use cases.
LDAP is a protocol used for accessing and maintaining distributed directory information services over an Internet Protocol (IP) network. It looks up information in directory listings often used for storing organizational entities like users, groups, and their associated details
LDAP can authenticate users in a single system or across a limited number of closely related systems.
| SAML | LDAP |
|---|---|---|
Purpose | Secure data exchange for authentication and authorization, mainly for web-based applications | Directory service for storing, retrieving, and managing structured data, including user and resource information |
Data Format | XML-based assertions | Hierarchical data structure |
Primary Use Cases | SSO and federated identity | Centralized user account management and directory services for authentication / authorization |
Authentication | Focuses on user identity and access control in web applications | Primarily focused on authentication and data retrieval from the directory service |
Authorization | Manages user permissions within web applications | Typically does not handle authorization directly; it provides user data for authorization decisions |
How does SAML work?
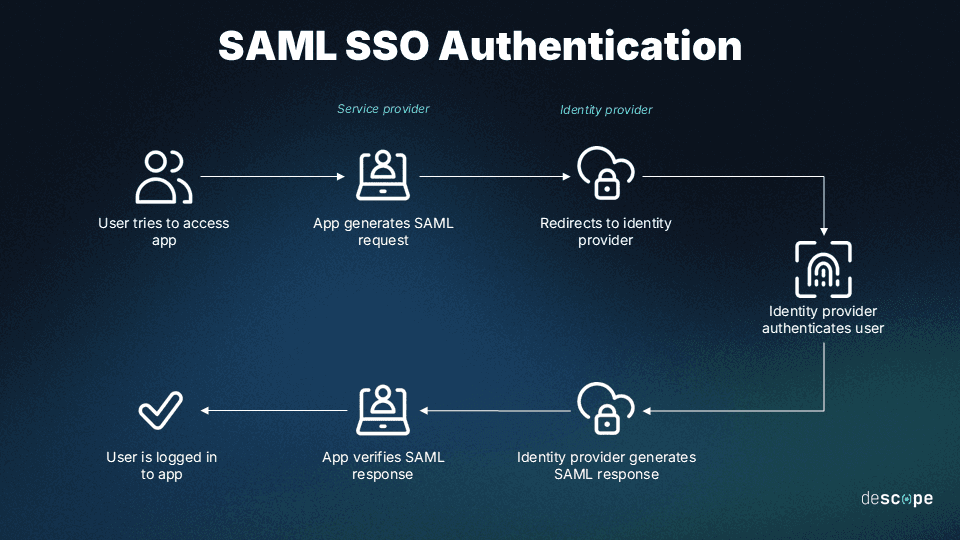
As mentioned before, at its core, SAML is the linchpin for exchanging authentication and authorization data between IdPs and SPs. Here's a simplified flow:
User request: A user tries to access the SP.
Redirect to IdP: The SP redirects the user to the IdP for authentication.
User authentication: The user logs in with the IdP, which verifies the credentials.
SAML assertion: The IdP creates a SAML assertion and sends it back to the SP.
Access Granted: The SP receives the SAML assertion, validates it, and grants the user access to the requested service.
SAML example
Let’s consider the following example to understand better how SAML works. Consider the following scenario:
The user works at an organization that uses SAML SSO for workforce applications.
The user is trying to access SpaceBNB, an application meant for renting spots on other planets (why not?). In this case, SpaceBNB is the SP.
The user’s employer uses Authsome to manage user authentication. Authsome is the IdP.
So it goes like this:
Step 1: The user tries to log in to SpaceBNB from their web browser.
Step 2: SpaceBNB generates a SAML request.
Step 3: The browser redirects the user to an SSO URL from Authsome. Authsome parses the SAML request and authenticates the user (with username-password, social login, OTP, etc.). This step will be skipped if the user already has an existing session with Authsome.
Step 4: Authsome generates a SAML response and sends it to the browser. This response contains assertions about the user’s identity and other attributes.
Step 5: The browser sends the SAML response to SpaceBNB for verification.
Step 6: SpaceBNB checks that the response from Authsome is legitimate and that none of the attributes have been modified.
Step 7: SpaceBNB extracts the user’s identity and other relevant attributes from the SAML response and logs the user in.
In this example, the user can log in to SpaceBNB without creating or remembering another set of unique account credentials. Since SpaceBNB delegates user authentication to Authsome, app builders do not have to worry about storing user passwords, managing password reset flows, and other organizational overhead.
Benefits of SAML
Here are some key advantages of using SAML authentication.
Enhanced security
SAML reduces the attack surface by eliminating the need for SPs to store user credentials, making app servers less attractive targets for cybercriminals. By reducing the number of passwords in circulation, SAML minimizes the likelihood and impact of attacks like credential stuffing and phishing.
Improved user experience
SAML streamlines the login process, resulting in a faster and more convenient user experience. Rather than creating and remembering unique passwords for every application, users simply navigate to the desired application and are authenticated by the IdP. The only credential they need to remember is the one used for the IdP.
IdPs that use passwordless authentication further improve user experience by freeing users from maintaining complex passwords.
Streamlined app development
By using SAML, SPs can place the burden of authentication and identity management on the IdP. This means app developers no longer have to expend resources on password management and storage, protecting against password-based attacks, and implementing password reset flows. These resources can now be diverted to the SP’s area of expertise and focus.
SAML sans struggle with Descope
SAML is the key to simplifying user authentication, enhancing security, and streamlining access to multiple web applications.
However, learning and debugging SAML can be a complex and time-consuming process. Descope helps developers easily add SAML SSO to their apps with no-code workflows, along with:
Full self-service provisioning for tenant admins
User attribute and group mapping
Testing
Viewing, selecting, and editing IdPs
SSO domains
With identity federation, Descope can also broker connections between any combination of SAML / OIDC clients and IdPs, helping customers unify user identities across customer-facing applications.
Sign up for Descope or schedule a demo today to start your journey towards seamless authentication with SAML.





