Table of Contents
What is SSO?
In an era where digital platforms are not just tools but lifelines for organizations, user authentication and managing access have emerged as critical tasks. Single Sign-On (SSO) technology addresses this challenge head-on by allowing users to access multiple applications across different platforms with one set of login credentials.
But this seemingly simple convenience masks a complex interplay of security protocols, identity verification, and interoperability standards that underpin modern access management systems.
Let’s explore what’s underneath the surface of SSO.
What is SSO?
SSO is a user authentication method that allows users to access multiple related applications and services with a single set of login credentials. Instead of creating and remembering separate usernames and passwords for each service, the user is required to log in only once, gaining access to all connected applications.
Besides improving and simplifying the login experience for the user, SSO is also beneficial to organizations. It’s an easy, affordable and secure way to maintain control over access to applications and services.
An end user can start a single sign-on process by either selecting the "SSO" login option on any app that supports it (SP-initiated SSO) or by logging in to SSO provider portals like Okta or Microsoft Entra and accessing any app from there (IdP-initiated SSO). More on these two implementations later.


SSO vs MFA vs federated authentication vs password managers
SSO and password managers both aim to simplify logins but operate differently.
Password managers, like LastPass or 1Password, store user credentials protected by a master password and offer tools like password generation and autofill to enhance convenience and security. However, they do not reduce the number of passwords, but rather manage them more efficiently.
SSO, in contrast, enables access to multiple applications with a single set of credentials, thus truly minimizing the need for multiple passwords.
You can also check out the difference between SSO and MFA, and SSO and Federated Authentication.
How does SSO work?
It’s important to note that the SSO authentication process may vary depending on the SSO protocol (which we’ll talk about later) and the services that need protection.
But as a rule of thumb, SSO works by creating a central repository of user credentials and a secure protocol for communication between the user, the applications, and the repository. The user logs into a single entry point, which verifies their identity and then provides access to all the connected applications.
SSO can be implemented in different ways, but the most common approach is using identity providers (IdPs)—entities that authenticate users and authorize their access to multiple applications.
Once a user logs in to the IdP, the user's identity is verified, and a token is generated that represents the user's session. This token is passed along with each request the user makes to a connected application, and the application uses it to verify the user's identity without requiring additional authentication. This is called IdP-initiated SSO.
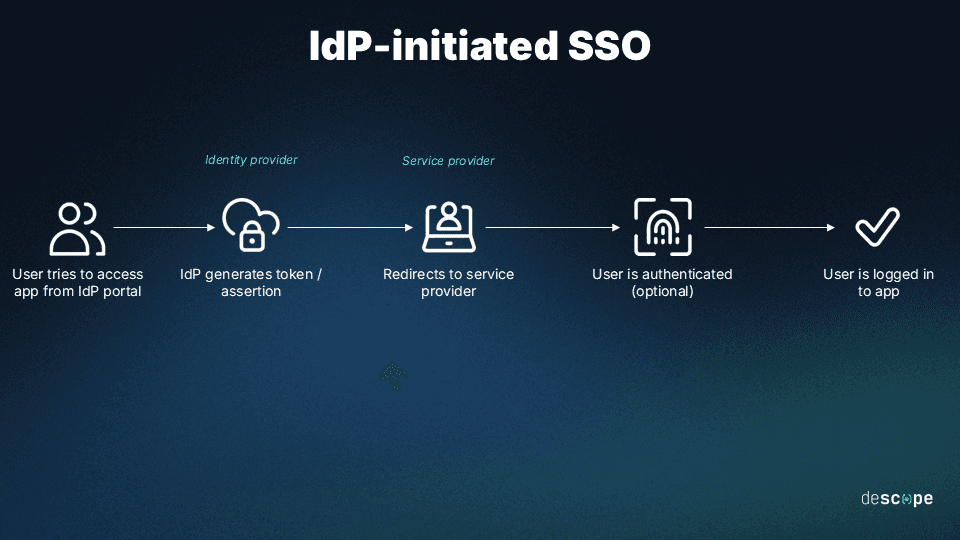
Alternatively, the user can directly try to access the app and start the SSO process that way. This is called SP-initiated SSO. Here's a simplified breakdown:
User authentication: When a user tries to access a service that is protected by SSO, they are redirected to the SSO provider's login page and prompted to enter their login credentials.
Verification of credentials: The SSO provider then verifies the user's credentials against its user database to ensure that the user is who they claim to be. If valid, it generates a token containing information about the user's identity.
Token distribution: The SSO provider sends the token to the user's browser, which then forwards it to the service that the user is trying to access.
Token validation: The service then validates the token to ensure that a trusted SSO provider issued it and has not been tampered with. If the validation is successful, the service provider creates a session for the user, granting them access.
Subsequent access: As long as the user’s session with the IdP is active, they can now seamlessly access other applications or services within the same SSO framework without re-authenticating.
Logout: When the session expires or the user logs out of the SSO provider, the token is invalidated, and they can no longer access the protected services without re-entering their login credentials.
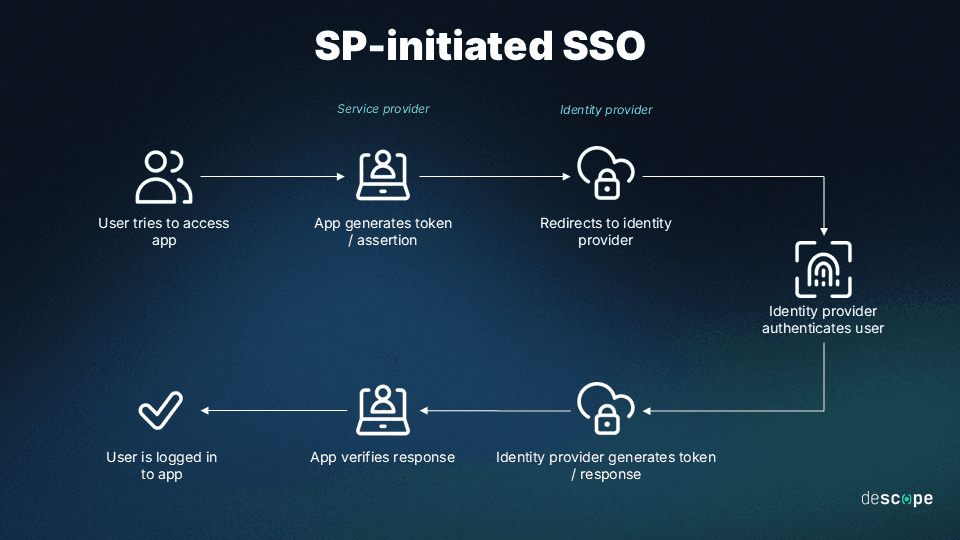
Read more: IdP-initiated SSO vs SP-initiated SSO
SSO protocols
There are many SSO protocols available, but here are a few of the ones with wide adoption:
SAML (Security Assertion Markup Language): SAML is a widely-used open-source XML standard for exchanging identity data between an IdP and service providers (SP). It’s mostly adopted by enterprises.
OAuth 2.0 (Open Authorization): As the name suggests, OAuth is designed for authorization instead of authentication. Unlike SAML, it uses JSON instead of XML. Supported by popular IdPs like Google and Facebook, it’s best used for consumer-facing mobile and website applications. Discover more about the differences between SAML and OAuth.
OIDC (OpenID Connect): OpenID Connect is another open standard that runs on top of OAuth, providing authentication. It is particularly effective in environments that include mobile APIs and single-page applications.
ADFS (Active Directory Federation Services): ADFS is a Microsoft-specific solution for SSO, mostly adopted by organizations that use Microsoft technologies.
Each of these SSO protocols has its own unique features, benefits and drawbacks. So the best choice for your organization would depend on your specific requirements and goals.
B2B Enterprise Readiness Checklist
Score your tech stack on enterprise readiness pillars - from dev and IT experience to security and architecture.
Download
Benefits of SSO
SSO has significant benefits that improve both the user experience and security of the services, making it one of the most convenient authentication methods. Here are a few benefits of SSO to remember when making the decision.
Centralized identity management: SSO enables centralized identity management, simplifying the monitoring and tracking of user activity across various services. This consolidation significantly reduces the risk of identity-related security breaches.
Simplified user access management: Administrators can easily manage user access, revoking or modifying as needed. This significantly reduces the risk of unauthorized access to sensitive information.
Extra layer of security: With SSO, enforcing strong password policies and multi-factor authentication becomes more straightforward. Ultimately, by requiring users to authenticate only once, SSO reduces the risk of password-related security breaches.
Improved user experience: There’s no need for users to remember and manage multiple usernames and passwords. This reduces password fatigue and creates a simple and quick login experience.
Boosted productivity: With a single point of access, workflows are not interrupted by frequent login prompts, allowing employees to concentrate on their tasks.
Compliance with regulations: SSO helps organizations meet stringent regulatory requirements concerning data privacy and security.
Streamlined integration: SSO facilitates the integration of different applications by providing a common method for authentication and authorization, simplifying the onboarding of new services and ensuring that they adhere to the organization's security standards.
Disadvantages of SSO
Like any technology, SSO comes with some risks and limitations:
Single point of failure: If an attacker gains access to a user's SSO credentials, they can gain access to all of the associated applications and services.
Dependency on the SSO provider: If the SSO provider experiences downtime or is compromised, users may lose access to all associated applications and services, potentially halting operations across an entire organization.
Common SSO use cases
SSO is widely used across the public and private sectors in industries like finance, retail and tech:
Enterprises: Large corporations use SSO to provide their employees with easy access to a wide range of internal applications and services, such as email, HR systems, CMS, and project management tools.
Educational Institutions: Universities and schools use SSO to provide students and staff with access to their educational resources, library resources, and administrative services.
Healthcare Organizations: Hospitals and healthcare providers use SSO to provide their staff with secure, HIPAA-compliant access to electronic medical records, scheduling systems, and other critical applications.
Government Agencies: Some government agencies use SSO to provide citizens or employees with secure access to databases and other online systems, such as license renewals and tax returns.
Retail: SSO is useful in online retail businesses to manage access to e-commerce platforms, customer databases, supply chain management systems, and employee portals.
Considerations for SSO implementation
If your business runs several services that are accessed by a large number of users (employees, vendors, consumers, etc.), then SSO is definitely worth considering.
However, when exploring SSO solutions for your organization, there are several key considerations to keep in mind. It needs to align with your specific needs, security requirements, and operational frameworks. Here are some critical considerations to evaluate:
Compatibility with existing systems: It should easily integrate with your existing infrastructure, including applications, databases, and directory services. Assess whether it can support any legacy systems you might have.
Scalability: The chosen SSO solution should be able to scale to accommodate your current and expected future number of users without compromising performance.
Simplicity: A critical goal of SSO is to simplify the user experience. The solution should offer a straightforward login process and seamless access to applications.
Vendor stability: Choose a vendor with a solid reputation for reliability, good customer support, and continuous innovation in identity and access management.
Looking to implement SSO for your app? Check out The Developer's Guide to Implementing Single Sign-On.
Easy SSO implementation with Descope
While implementing SSO, particularly through protocols such as SAML and OIDC, presents a significant technical challenge, it remains a non-negotiable requirement for enterprises looking to streamline their workflow and enhance security.
This is where Descope bridges the gap. Designed with developers and IT teams in mind, Descope's no-code workflows simplify the process of integrating OIDC or SAML SSO capabilities into your B2B application. This drag-and-drop approach not only gets your app enterprise-ready but does so in a way that's hassle-free, saving valuable time and resources.
Sign up for a Free Forever account to include SSO in your authentication flow today. Have questions about SSO implementation with Descope? Book time with our auth experts.




