Table of Contents
What is authentication?
User authentication is no longer a checkbox; it’s your first line of defense. For organizations, it’s about more than just verifying credentials. The right authentication strategy shields sensitive data, stops account takeovers, and supports seamless user experiences at scale. As threats evolve and credentials flood the dark web, businesses face a new challenge: implementing authentication that’s both resilient and invisible to legitimate users.
This guide unpacks what user authentication is, how it protects your organization, and why modern businesses can’t afford to overlook it.
Main points
The cornerstone of digital security: Authentication serves as the first and most critical defense against cyber threats and data breaches, which means it’s constantly under attack.
Passwords on the way out: While traditional credentials remain common, businesses are rapidly adopting passwordless solutions for better security and user experience.
Implementation determines success: The right authentication approach balances robust security with seamless user experience, requiring careful planning for your specific use case.
What is authentication?
Authentication is how digital systems ensure users (or devices and services) are who they claim to be, using everything from passwords to fingerprints. Think of it like staying at a hotel: a keycard proves a registered guest’s identity and unlocks their specific room. Both hotels and online services want only legitimate access, but keeping digital “keycards” safe presents a challenge.
Case in point: In 2024, 2.8 billion passwords were leaked, and 88% of attacks against basic web applications used stolen credentials. That’s why businesses are moving away from passwords toward more secure, user-friendly methods that keep cybercriminals out without making life harder for everyone else.
Authentication vs. authorization
Authentication and authorization work together, but they serve different purposes.
Authentication asks “Who is the user?” and confirms identity, a bit like checking a guest’s ID at a hotel. Authorization asks “What are they allowed to do?” and determines permissions—if a keycard lets them on the lounge level, for example.
Here’s how they work in practice: When a customer logs into their mobile carrier account, authentication confirms their identity. Once in, authorization controls what they can access. Maybe they’re a member of the plan, but not the account manager. They can make changes that affect their phone number and device, but can’t order a service upgrade or cancel the subscription.
User authentication vs. machine authentication
Authentication isn’t just for humans. Machines (i.e., devices, apps, etc.) need to prove who they are, too. Understanding both types is helpful for building a more comprehensive understanding of authentication security.
User authentication is what most people think of when anything related to auth comes up. It’s the process where humans prove who they are to access systems, apps, and data. User authentication ranges from typing in a password, scanning their face or fingerprint, or entering a one-time code. Ultimately, it focuses on confirming human identity and is designed around human capabilities and behaviors.
Machine authentication (also known as machine-to-machine or M2M authentication) is how devices, applications, and services confirm identities with each other. Think of it like a handshake between two systems. For example, a smart home thermometer reports temperature readings to a cloud server, which requires it to authenticate with the remote service.
The primary use cases for M2M authentication are API communication, microservices, IoT and smart devices, and cloud networking. While each of these scenarios might use a slightly different type of machine authentication—access keys, client credentials flow, service tokens—they all require a machine to perform a backend “handshake” with another machine at some point in the journey.
Unlike user authentication, machine authentication happens automatically in the background and typically uses more complex credentials since there’s no human experience to consider. It’s also much more frequent, but since machines can complete authentication nearly instantaneously, it doesn’t negatively impact the user.
Learn more: Authenticating APIs With JWT Authorizers and OIDC
How does authentication work?
Authentication is a fundamentally simple process. When a user tries to log in to a system, that system determines the validity of one or more authenticators used to claim a digital identity (such as a password). Only two results are possible: “access granted” or “access denied.”
But while the concept of authentication is quite simple, the process of authenticating a user has become significantly more complex over the years. Let’s break it down into its core components.
The basic authentication process
Every authentication system follows the same core fundamentals and standards, like those defined in NIST SP 600-63-4:
Identity claim: The claimant (the user) asserts an identity to the system (such as with an email or username)
Authenticator presentation: The claimant presents one or more authenticators as proof (password, biometric data, a signed cryptographic challenge, security token, etc.)
Authenticator validation: The verifier (the system) validates the presented authenticators against stored authentication data
Access decision and session establishment: If validation succeeds, the system grants access and establishes a session with appropriate permissions
Let’s call back to the hotel analogy: the guest claims an identity by providing their name (identity claim), present their confirmation email or an ID/credit card (authenticators), the front desk validates these in their system (authenticator validation), then either provides a keycard (access granted) or informs the guest of a problem (access denied).
The three authentication factors
Authentication is designed around three fundamental factors:
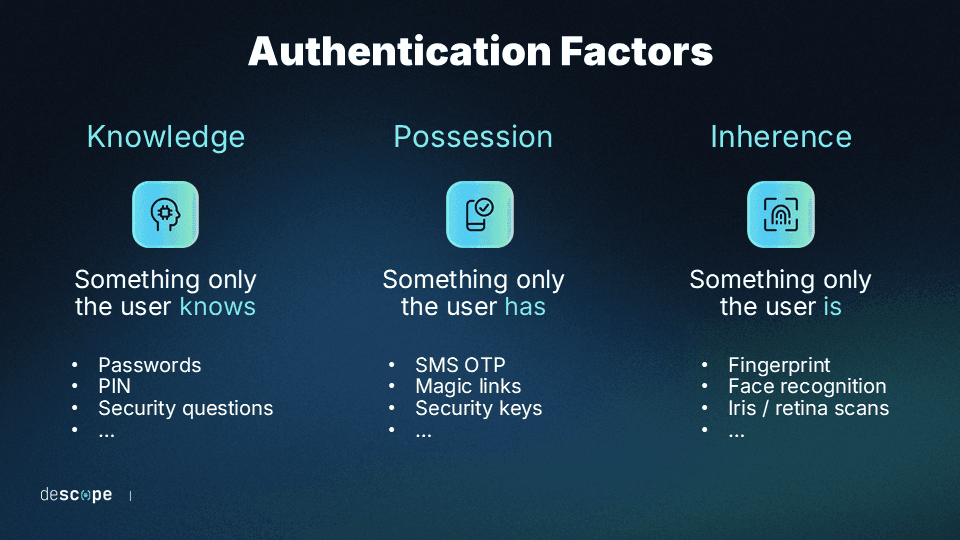
Knowledge (something you know) includes passwords, PINs, security questions, and passphrases. These are the most common but also the most vulnerable. They can be guessed through brute force attacks, stolen through credential phishing, or compromised in data breaches. The challenge with knowledge factors is that to be truly secure, they need to be difficult for humans to remember and use.
Possession (something you have) relies on physical authenticators that hold a digital secret. These include devices like smartphones (which have dedicated hardware for auth secrets), security keys (e.g., YubiKeys), and smart cards. Such devices are highly secure because an attacker would need both physical access to the device and the ability to breach it. However, possessions can be lost, stolen, or damaged, which can necessitate less-secure fallback methods.
Inherence (something you are) uses biometric characteristics like fingerprints, facial recognition, voice patterns, and iris scans. These immutable and universal traits are extremely difficult to fake, but they require specialized hardware to validate. Biometric authentication also presents its own unique set of challenges, such as user pushback due to misunderstandings about how their data is used.
Importance of authentication
Authentication is critical to securing users’ sensitive data, whether it’s stored on networks, applications or systems. Strong authentication is necessary for:
Security: Authentication is the most critical layer in your defense against account takeovers. Without robust authentication, even the strongest backend firewalls become meaningless once an attacker gains legitimate-looking access.
User experience: Poor authentication creates friction that drives users away. Complex password requirements, frequent re-authentication, and confusing multi-factor flows all contribute to user frustration and abandonment. Modern methods like passwordless auth can actually improve user experience while enhancing security.
Regulatory compliance: Industries like healthcare (HIPAA), retail and finance (PCI DSS), and government (FedRAMP) have strict authentication requirements. Failing to implement proper authentication controls can result in hefty fines, regulatory body audits, and loss of certifications. Many regulations now specifically require multi-factor authentication for accessing certain data.
Modern authentication challenges and solutions
Today’s traditional, password-based authentication faces a crisis: credentials are routinely exposed, sold to the highest bidder, and even posted for free on underground networks. These billions of credentials are fed into botnets to attempt account takeovers en masse, prompting organizations to enforce increasingly demanding password policies.
Yet, users already struggle to create and remember complex passwords, which leads to password reuse (making them vulnerable to credential stuffing)—thus, the cycle continues. This is why modern systems often implement multi-factor authentication (MFA), adopt passwordless methods, and leverage adaptive authentication.
We’ll cover more about how these authentication strategies solve today’s challenges in the following section.
Types of authentication
Authentication can take many forms, and the right method depends on your organization’s security needs, user experience goals, and regulatory requirements. Below, we break down the most common types of authentication, each with its strengths, limitations, and ideal use cases for modern applications.
Password-based authentication
Password-based authentication is a method of verifying a user's identity by requiring them to enter the password associated with their account.
To authenticate with the system, the user enters their username and password, which are then compared to the stored values in the system's database. If the username and password match, the user is granted access.
Although this is the most common type of authentication due to its simplicity and convenience, it is also probably the least secure. Passwords can be easily forgotten, stolen, or guessed, especially if the password is weak or reused across multiple systems.
Token-based authentication
Token-based authentication is a method of verifying a user's identity by requiring them to present a token that is associated with their account. The token is a physical device or a digital file that contains a unique identifier, such as a smart card, USB key, or a software token.
Token-based authentication provides an extra layer of security compared to password-based authentication, as the physical token is harder to steal or replicate than a password. They are often used in situations where strong authentication is necessary, such as accessing sensitive data or performing financial transactions.
However, although tokens are a reliable method of authentication, they are more expensive and less convenient. They can be lost, stolen, or damaged, so users must take appropriate measures to safeguard them.
Certificate-based authentication
This method verifies the user’s or machine’s identity by using digital certificates. A digital certificate is an electronic document typically issued by a trusted third-party authority. They contain the user's digital identity, a public key, and the digital signature of the certification authority.
As digital certificates are difficult to forge or steal, certificate-based authentication is considered to be highly secure. Usually, it’s used in enterprise environments dealing with sensitive data. However, it is more complex to set up and manage than other authentication methods, so it’s not the most convenient method for widespread use.
Multi-factor authentication (MFA)
MFA requires users to verify their identities using one or more factors (which may or may not include a password) at the time of login. Two-factor authentication (2FA) is the most common version of MFA, with only two identification factors needed.
With rapidly growing application security risks, more businesses are starting to rely on MFA to secure their applications against cybersecurity threats.
Passwordless authentication
Passwordless authentication refers to a range of authentication methods used to verify a user's identity without the need for passwords. Instead, passwordless authentication uses a combination of possession and inherence factors, such as:
Magic links – A URL sent via text message or email containing a token that allows the user to log in without requiring a password when they click on it.
One-time passwords (OTP) – Unique, dynamically generated codes with numbers and/or letters that grant one-time access to the user.
Authenticator apps – An authenticator app is a software application installed on the user’s device that generates time-based one-time passwords (TOTP).
Biometrics– A physical trait unique to the user, such as fingerprints, voice, face, etc.
By removing passwords, passwordless authentication reduces the risk of unauthorized access, making it superior to other methods. Additionally, it’s more convenient for users, as they no longer need to remember complex passwords.
Passwordless authentication is used in a variety of applications, including online banking, ecommerce, and enterprise environments. As technology continues to advance, passwordless authentication is likely to become more widespread as a secure and convenient alternative to traditional passwords.
Adaptive authentication
Adaptive authentication scores each login attempt based on contextual risk factors: where the user appears to be located, whether they’re using a new device, etc. This scoring system determines next steps, such as whether they’ll be prompted to complete additional authentication (like MFA).
Also known as risk-based authentication (RBA), adaptive authentication elegantly balances security rigor with seamless user experience. It ensures that legitimate users sail through with only necessary friction, while potential threats are mitigated as early as possible.
Modern authentication protocols
Today’s authentication systems rely on standardized protocols that ensure secure, interoperable identity and access management across diverse platforms and services:
OAuth 2.0/2.1 is the industry standard for authorization. Notably, OAuth isn’t an authentication protocol on its own, but it is a core part of OpenID Connect (below). OAuth powers social login, like “Sign in with Google/Apple/Microsoft,” and it’s a key ingredient in modern AI security.
OpenID Connect (OIDC) is built on top of OAuth 2.0 to add an authentication layer. OIDC is what actually authenticates users in modern single sign-on (SSO) systems.
SAML 2.0 (Security Assertion Markup Language) is an older SSO protocol mainly used in enterprise environments. SAML works by securely exchanging authentication data between identity providers and applications.
WebAuthn and FIDO2 are a pair of standards that enable passwordless authentication on the web. They’re supported natively by modern browsers and operating systems.
System for Cross-Domain Identity Management (SCIM) automates user provisioning and deprovisioning (enabling and disabling access) across multiple systems, making it essential for enterprise identity.
These authentication protocols work together to create an interwoven, interoperable authentication ecosystem. Combined, they can create seamless auth experiences for users. For example, you might use OIDC to sign into an app with your Google account, while WebAuthn/FIDO handles the actual authentication through your fingerprint via passkeys.
Authentication best practices
Authentication best practices evolve over time, but industry standards (like those provided by NIST) and implementation successes serve as reliable barometers. The following tips and tactics will help you build authentication that is both secure and user-friendly.
Embrace passwordless authentication
Passwordless authentication reduces the risk of account takeovers and identity theft while improving user experience. FIDO2 is supported by 95% of global user devices, making passwordless a practical choice for modern applications. When launching a new auth method like magic links, email-based OTPs, or passkeys, consider gradually rolling out to a smaller cluster of users first.
Implement adaptive MFA
Not every login attempt carries the same risk. Adaptive MFA adjusts the level of validation required based on factors like device reputation, geolocation, and login behavior. This approach introduces unnecessary friction for legitimate, trusted users while strengthening security for suspicious activity. Consider requiring additional authentication steps only for high-risk scenarios like new devices or unusual locations.
Use phishing-resistant methods
Traditional MFA can still be vulnerable to phishing attacks and MFA bypass techniques. Prioritize phishing-resistant methods and factors that can’t be easily stolen or replicated, such as FIDO2-based passkeys that leverage device-bound biometrics. Avoid SMS-based codes when possible, as they’re susceptible to SIM swapping, man-in-the-middle (MITM), and adversary-in-the-middle (AITM) attacks.
Follow security fundamentals
Keep token expiration short, and use refresh tokens behind secure storage. Implement comprehensive logging to detect anomalies like tokens being used from multiple locations. Enforce strict rate limiting to prevent bot-based attacks, and leverage strong password policies if you decide to use traditional credentials. For example, you can integrate your password requirements with Have I Been Pwned to prevent users from setting their password to one that’s been breached previously.
Authentication in action: Real-world case studies
Planning and theorizing about authentication can certainly help you prepare for production, but eventually, it’s time to solve real business challenges. Authentication can have a huge impact on security, user experience, and the bottom line across a wide range of industries. Here’s how different sectors implement authentication to meet their specific needs:
Banking and finance
GradRight, an EdFinTech platform helping students finance education abroad, required defense from bot attacks without affecting their user experience. They added conditional checks for bot traffic, automatically branching journeys based on the risk level. If the system uncovered a likely bot, it was given additional auth steps. Legitimate users continued undisrupted.
Ecommerce
CARS24, a multinational online car marketplace, serves diverse stakeholders, including customers, dealers, and internal users across multiple applications. CARS24’s authentication solution could set different session times, activity timeouts, and other settings to cater to each app’s security requirements, meeting the different needs of their diverse user base.
Insurance
Branch Insurance, a cloud-native insurance provider, moving to phishing-resistant passkey authentication to serve their 12,000+ independent insurance agents. They saw auth-related support ticket volume by about half, and saw 25% adoption in the first 90 days. They also created a fallback flow for the small fraction of devices that might not support passkeys, ensuring users never encountered unnecessary roadblocks.
Healthcare
SmithRx, a full-service Pharmacy Benefit Manager, needed to unify authentication across multiple portals while implementing fine-grained access control for their complex healthcare ecosystem. By consolidating their authentication backend, they were able to significantly reduce development overhead while maintaining a HIPAA-compliant login experience.
SaaS applications
Notch, an AI-native customer support platform, needed flexible authentication to serve both startups and enterprises. With their auth implementation, Notch customers gained the benefits of SSO, SCIM provisioning, and tenant-level access controls with RBAC.
Easy and secure authentication for your app
Authentication is at the heart of securing modern applications, and getting it right is critical for protecting your users, your data, and your business. From passwordless logins to adaptive MFA, the challenge is building robust, scalable flows without slowing development or adding friction.
Descope’s drag & drop CIAM platform helps organizations deliver secure, seamless authentication across every touchpoint—without the complexity. Whether you’re securing customers, employees, or partners, Descope lets you focus on your business, not building auth from scratch.
Get started with a Free Forever Descope account, or book a demo to see how we can support your authentication strategy.