Table of Contents
Main points
The complexity of managing user identities grows exponentially with the increasing reliance on cloud services. Did you know the average employee uses 36 cloud-based services daily, and the typical enterprise juggles nearly 1,300 cloud services? IT teams are responsible for ensuring users can seamlessly access these apps and utilize their functionalities as intended. With organizations' digital footprints expanding rapidly, reliable syncing of user identity information across applications has become more vital than ever.
That’s where SCIM comes in. This article will explore SCIM's role in user identity management, covering its benefits and role in making user experiences more secure and efficient.
Main points
SCIM automates identity management by automatically syncing user identities across apps, saving time and reducing errors.
SCIM keeps authentication data updated to prevent unauthorized access. It deactivates accounts when users leave, or roles change.
SCIM with SSO allows access to many apps with one login. It simplifies workflows and boosts productivity.
SCIM manages large user bases with standardized APIs. It eliminates the need for custom coding.
What is SCIM?
SCIM stands for System for Cross-Domain Identity Management. It is an HTTP-based open standard built for user provisioning between Identity Providers (IdP) and cloud-based Service Providers (SP).
SCIM is a set of JSON and REST-based specifications developed to simplify user identity management across multiple domains. It provides a consistent schema for representing users and groups and a standardized API for managing these identities. By using SCIM, organizations can streamline the process of creating, reading, updating, and deleting (CRUD actions) user accounts and group memberships across different platforms.
For example, a company may use Microsoft Azure as the IdP, containing a directory of user identities. The company may also use SaaS apps like Slack or Dropbox for its employees, which would need some user identity info. Instead of syncing all apps, IT teams can use SCIM. SCIM will update and delete identity details, automating and simplifying the process.
Try Descope’s security solutions today for free to protect your users and keep your business secure.
How SCIM relates to authentication
Authentication is the process of validating the identity of a user, device, or system. Authentication is vital in ensuring that only intended users have access to specific protected resources. Utilizing SCIM allows applications to manage their user identities across multiple systems, creating an easy environment for maintaining accurate and up-to-date authentication information.
How SCIM works
As mentioned, SCIM provides a standard schema and protocol. It automates the exchange of user identity info between IdPs and SPs. Here's an overview:
The core components of SCIM are usually defined as follows:
Schema: This defines the structure and attributes of resources, like users and tenants. It ensures a consistent description of user identities across systems. This makes data integration and mapping easier.
Protocol: It uses RESTful APIs to enable communication for user identity management tasks and supports standard CRUD operations for managing user and group objects.
Endpoints are URLs for API operations: They perform actions on resources, like users and groups, defined in the SCIM protocol.
As the diagram below shows, a SCIM provider offers endpoints that applications can use to make and deliver requests.
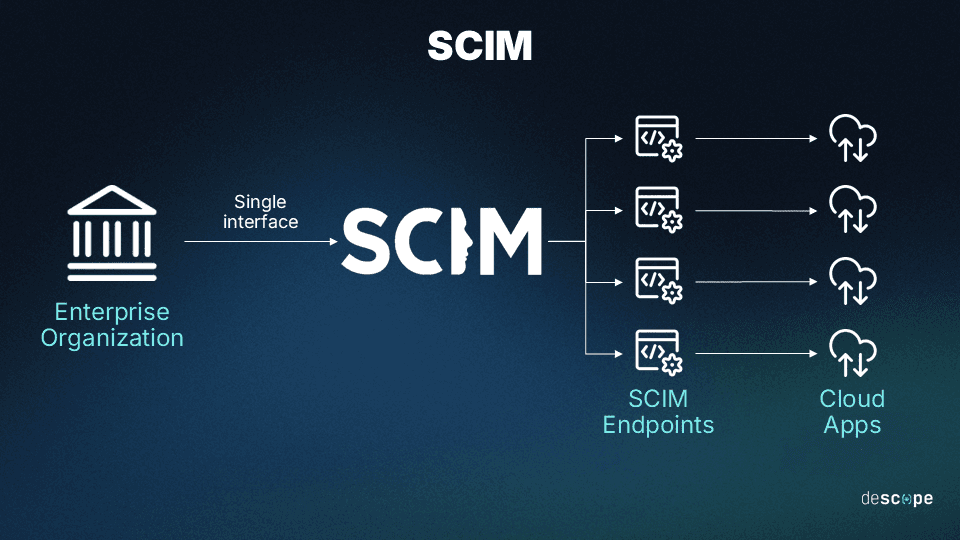
A typical SCIM flow would look like this:
Provisioning (Onboarding): When a new user is created or updated in the IdP, it requests the SCIM endpoint to create or update the corresponding user account. This process keeps the user data synchronized between the IdP and the application, ensuring that the user always has the appropriate access to protected resources.
Synchronization. SCIM synchronizes user attributes like job title, department, or email across systems. When a user's details change, SCIM updates target systems to ensure consistency.
Deprovisioning (Offboarding). SCIM supports filtering and pagination, enabling the IdP to search for specific users or tenants based on certain attributes or conditions. This feature is helpful for large organizations managing a voluminous set of user accounts.
To install SCIM, both the source and target systems must support the SCIM standard. The source system is a SCIM client, and the target systems are SCIM servers or SPs. They respond to RESTful API calls from the client to manage user identities.
Common SCIM use cases
SCIM can streamline and automate user identity management across systems, platforms, and apps. You can use it in various scenarios. These are some of the most common use cases for SCIM with an IdP:
The system creates or updates a new user in the IdP. The IdP sends a request to the SCIM endpoint. It makes or updates the corresponding user account. This process keeps the user data synchronized between the IdP and the application. It ensures that the user always has the appropriate access to protected resources.
User deprovisioning. When the IdP needs to revoke a user's access, it sends an HTTP request to the SCIM endpoint. This is for cases like when an employee leaves a company. This request removes the user account or restricts access. It ensures that the user can no longer access the SP's resources.
Filtering and pagination: SCIM supports these features. They let the IdP search for users or tenants based on certain attributes, which helps large organizations manage many user accounts.
Benefits of SCIM
Adopting SCIM provisioning helps enterprise organizations in different ways:
Simplified identity management (SCIM) helps IT teams manage identities across platforms. It provides a consistent schema for users and groups, reducing the complexity of managing many systems. This is critical in large, distributed systems, where manual syncing of user information can lead to errors.
Enhanced security: SCIM maintains up-to-date authentication information. It lowers the risk of unauthorized access to outdated user data. Implementing SCIM with SSO eliminates the need for password sharing. It also removes the security vulnerabilities that come with sharing passwords. For example, deprovisioning user accounts when employees leave helps prevent unauthorized access. SCIM also supports fine-grained access control by allowing precise control of user permissions that follows the least privilege principle.
Improved user experience: SCIM integrates with SSO to allow users to access many applications and services. Users can do this with a single set of credentials. This simplifies the authentication process. It also reduces the likelihood of credential-related security breaches. Moreover, it reduces reliance on IT support for routine account management tasks.
Scalability: Developers designed SCIM for scalability. It supports large-scale identity management in organizations of any size. SCIM eliminates the need for developers to work with custom APIs. Instead, developers use standardized schemas. This saves time and effort.
B2B Enterprise Readiness Checklist
Score your tech stack on enterprise readiness pillars - from dev and IT experience to security and architecture.
Download
SCIM vs. SAML vs. SSO
SCIM, SAML, and SSO are all important standards and methods used for identity and access management (IAM), but they serve different purposes and operate in distinct ways:
SCIM | SAML | SSO | |
|---|---|---|---|
Purpose | Automates management of user identities across systems | Exchanges authentication and authorization data | Allows access to multiple applications with one login |
Main Use Cases | User provisioning and deprovisioning | Single Sign-On (SSO), Federated Identity Management | Streamlining user access to multiple services |
How It Works | Uses RESTful APIs to manage create, read, update, delete operations on identities | Uses XML-based assertions for exchanging auth data between IdP and SP | Provides seamless access via a single authentication process using protocols like SAML, OAuth |
SCIM vs SAML
Security Assertion Markup Language (SAML) is an open XML-based standard that helps IdPs and SPs exchange authentication and authorization information. SAML and SCIM are protocols used for IAM but fulfill different purposes.
SAML handles authentication and authorization. SCIM automates user provisioning and de-provisioning across apps. SAML allows users to access many apps with a single set of credentials. SCIM helps the IT team synchronize user information across apps. It ensures that we create, update, or remove users as needed.
SCIM vs SSO
A key benefit of a SCIM specification is its support for SSO. It lets users access many apps with a single set of credentials. This cuts the need for many usernames and passwords. It improves the user experience and boosts security. It does this by lowering the risk of password breaches.
SCIM and SSO work together, but they serve different goals. SCIM primarily aims to share identity information with apps across domains, while SSO authenticates users with a single set of credentials across apps. Integrating SCIM with an SSO solution allows central user account management and ensures consistent authentication information across all apps and services.
Seamless SCIM provisioning with Descope.
SCIM provisioning and deprovisioning are fundamental components of modern identity management systems. They provide a standardized framework for syncing user identities across many platforms.
Today, B2B applications must incorporate SCIM. It is no longer a luxury but a necessity for serving enterprise clients because installing and maintaining SCIM in-house may be complicated. Descope’s drag-and-drop CIAM platform helps organizations become enterprise-ready. It offers features like single sign-on, fine-grained authorization, and SCIM provisioning.
Check out our SCIM management docs and demo videos with Okta and Microsoft Azure.
To get started with Descope, sign up for a free forever account. Have questions about deploying SCIM? Book time with our experts.




