Table of Contents
What is an authentication method?
As the digital world evolves, so does the need for stronger security measures and seamless user experiences. Authentication methods are at the forefront of both these priorities, serving as the first barrier against unauthorized access as well as the first impression your users have of your application.
However, it can be difficult to choose from so many different authentication methods. So to help you make the right decision for your app and organizations, we’ll explore the most prevalent types of authentication, from simple passwords to advanced passkeys. We'll look at how these methods work, their benefits, and which situations they're best suited for.
What is an authentication method?
An authentication method is a process or technique used to verify the identity of a user or device before granting access to the service they’re trying to access. It ensures that the entity trying to gain access is indeed who or what it claims to be.
Passwords are the oldest type of authentication, dating back to the 1960s, when the first computing systems were introduced. However, as computer networks and technology evolved, so did the need for stronger security measures. Here’s a brief timeline:
1990s: The rise of the internet and web applications led to the development of Single Sign-On.
2000s: Advances in sensor technology and computing power made the use of biometric data a real thing, not just something we see in movies.
2010s: This was the decade when MFA and token-based authentication became more widespread.
2020s: Driven by the need to reduce password-related vulnerabilities, passwordless authentication methods gain traction.
The evolution of authentication methods reflects the ongoing need to balance security, user experience, and technological advancements. So, let’s unpack the most commonly used authentication methods today and see how far we’ve come since the first days of secret passwords.
Gartner Buyers Guide for CIAM
Learn common CIAM use cases and recommended evaluation criteria.
Get copy
Password-based authentication
One of the most common authentication methods employs passwords a.k.a. passcodes to grant access. To verify their identity, users are prompted to input a valid username and password combination known only to them. This is among the simplest authentication methods to implement as nearly everyone is familiar with how it works, regardless of their tech literacy.
However, password-based authentication is much less secure than other methods and poses a breeding ground for data breaches and cyberattacks. Some of the most common vulnerabilities include:
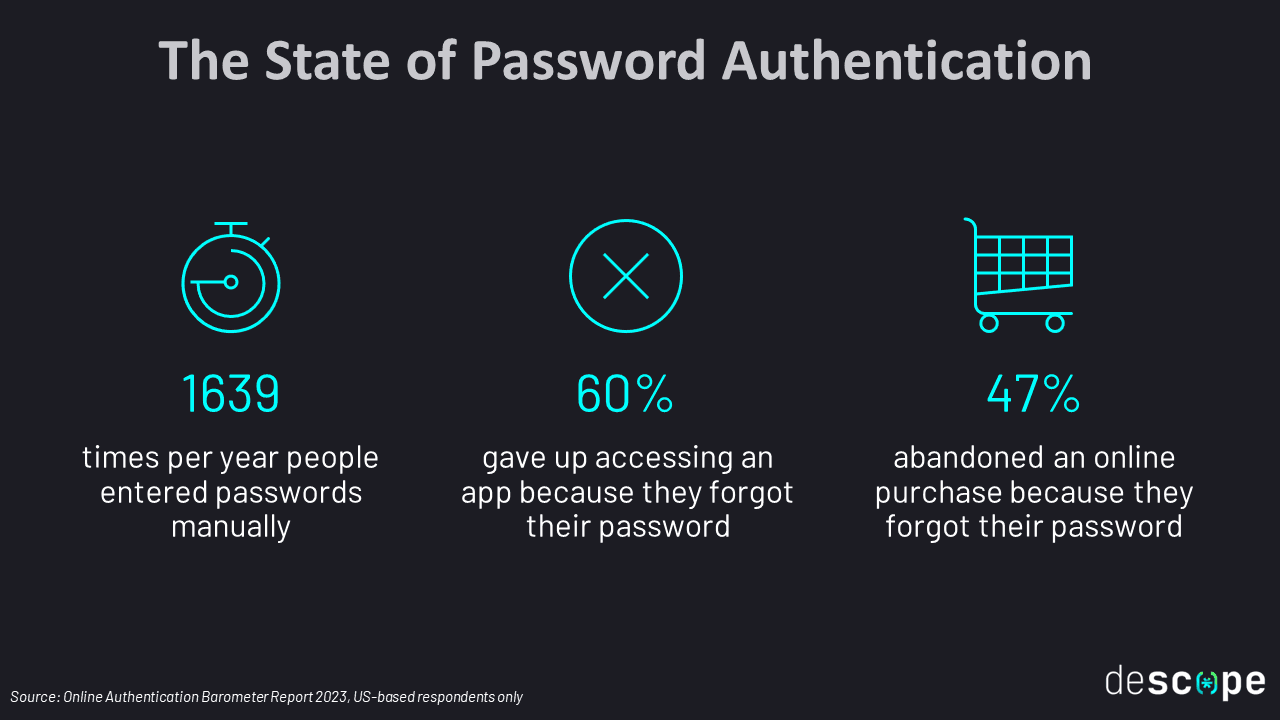
Weak passwords: Users often choose weak passwords that are easy to guess or crack, such as common words, personal information, or simple sequences. According to NordPass, in 2024, the most common online password was “123456.” This makes passwords vulnerable to brute-force or dictionary attacks. In 2023, the average number of brute-force attacks a month was 200 million—a fivefold increase from 2022.
Password reuse: Many users tend to reuse passwords across multiple accounts, which increases the risk of a security breach. If one account is compromised, attackers can gain access to other accounts as well through credential stuffing attacks.
Forgotten or lost passwords: Users often forget their passwords, leading to frustration and the need for password recovery or reset processes. This can result in additional support and administrative overhead for the service provider.
Vulnerability to phishing and social engineering: Password-based authentication is susceptible to social engineering attacks, where attackers manipulate users into revealing their passwords or related information through deception or coercion. Attackers can also create fake phishing sites to harvest user credentials.
Lack of scalability: As the number of users and accounts grows, managing and securing a large number of passwords becomes challenging. Scaling password-based authentication may require additional resources and security measures.
Read more: 2023 FIDO Report Findings
Passwordless authentication
Passwordless authentication methods include solutions that forego a static password in favor of other, more secure, authenticating factors. Passwordless solutions can be single-factor or MFA and rely primarily on possession and inherence factors. Common approaches include:
Magic links: Instead of asking for a password, your app can request an email address or phone number to send a link to the user, identifying them by their access to said account and / or device.
One-time passwords (OTP): Rather than sending a link, you can send users a unique, randomized string of characters that functions like a password but for a single use.
WhatsApp authentication: By using WhatsApp rather than SMS for authentication, businesses can save on OTP costs while providing users with a more secure and friendly experience.
Authenticator apps: You can also require users to retrieve a time-based OTP (TOTP) from apps like Google Authenticator and Authy, with codes expiring after a set interval (usually 60 to 90 seconds).
Passkeys: A passkey is a modern authentication method that uses cryptographic keys stored on the user’s device to securely log in. It typically relies on biometrics or a PIN for user authentication.
Enchanted links: Enchanted links are a cross-device login method where users click a unique link sent to their email and confirm a number shown during login.
Embedded links: Embedded links are single-use tokens that let an existing user log in. They can be shared via email or SMS. Embedded link tokens are verified using the magic link verification function.
On the user side, passwordless authentication removes the cognitive load and increases their engagement with the app. For organizations, not having to manage passwords frees up bandwidth and reduces overall identification and access management (IAM) expenses. It also greatly reduces the likelihood of account takeover and password-related breaches.
, showing the Acorns logo at the top and a centered message with the heading Your login code, text stating Thank you for verifying your identity. Your unique login code is followed by a five digit code 19531, and a note below indicating that account security is a priority and recommending changing the password if this was not initiated by the recipient, displayed within a standard email client interface.](/_next/image?url=https%3A%2F%2Fimages.ctfassets.net%2Fxqb1f63q68s1%2F2xUsJ7RqeZAuwyJt3s0O2P%2F8deb2e6c06a927ba44a50b2f7ce8c32b%2FEmail_OTP_example.png&w=3840&q=75)
Multi-factor authentication (MFA)
As the name suggests, multi-factor authentication (MFA) requires at least two factors to verify a user’s identity. The goal is to block unauthorized access if one of the authentication methods has been compromised and the account is exposed.
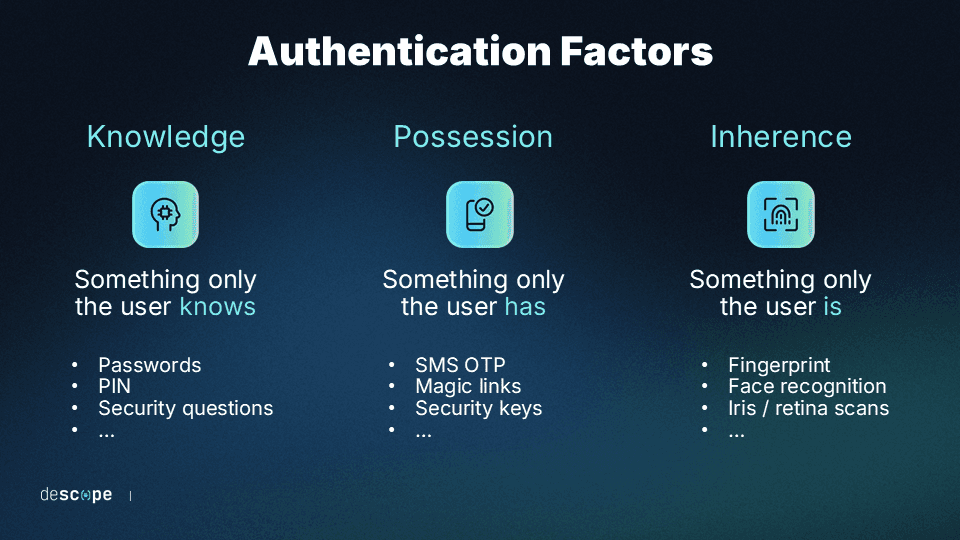
Most factors used for MFA fall into one of three categories:
Something you know: Information that only the user knows, like passwords, security questions, or personal identification numbers (PINs).
Something you have: This involves a device or account in the user's possession, such as a smartphone, email account, smart card, etc.
Something you are: This factor relies on the user's unique biological traits, such as a facial or fingerprint scan.
Although significantly more secure than password-based authentication, MFA is also susceptible to cyberattacks, commonly known as MFA bypass. For this reason, it’s crucial to set up phishing-resistant MFA flows that consider its weaknesses.
Federated authentication
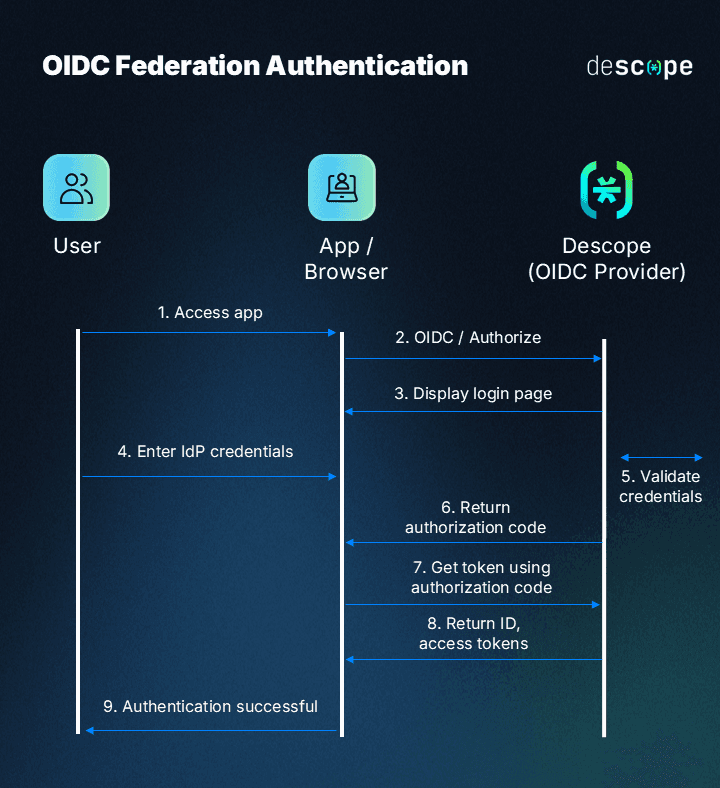
Federated authentication – also called federated identity management – is a process where authenticating to an app is handed off to an Identity Provider (IdP). This reduces the reliance on passwords since users don’t need to create new credentials for every app. It also lessens engineering work for app developers since they can hand off identity management processes to a trusted IdP.
Federated authentication is commonly exposed to end users in the form of Single Sign-On (SSO). Here are some popular SSO protocols and implementation methods:
SAML: Security Assertion Markup Language is a common XML-based protocol that enables Identity Providers and Service Providers to reliably exchange identity information during signup and login.
OIDC: OpenID Connect is a more modern JWT-based protocol that is built on top of the OAuth2 framework to enable user authentication.
Biometric authentication
Biometric authentication is a secure, convenient, and passwordless method of verifying an individual's identity based on their unique physical traits, such as fingerprints and facial recognition. Data shows that in 2023 biometrics was the preferred authentication method by users.
The technology behind biometrics involves capturing and analyzing these distinct physical characteristics and converting them into digital templates that are stored securely on the user’s device. When authentication is required, the presented biometric data is compared against the stored templates to determine a match.
This sophisticated approach offers numerous advantages, including:
Increased security: Biometric traits are almost impossible to replicate or forge.
Enhanced user experience: Individuals no longer need to remember and manage complex passwords or PINs.
As a result, biometric authentication is becoming increasingly prevalent in various domains, ranging from web applications, smartphones and laptops to border control systems and financial institutions, revolutionizing the way we protect sensitive information and establish trust.
The recent rise of passkeys based on the WebAuthn standard is the strongest example of biometrics being an authentication method preferred by users and organizations alike. With passkeys now supported by Google, Apple, Microsoft, and Shopify, biometrics are sure to grow in adoption in the years to come.
Token-based authentication
User authentication can also use physical assets, or tokens, to verify identity. This is a possession-based approach in which the user is associated with a physical object, such as a USB key or trinket, that contains a unique identifier. Hardware tokens based on the FIDO2 standard are among the strongest forms of authentication available today.
Typically, the identifier is a randomized sequence of information, such as a cryptographic key or a code (e.g., bar or QR) that an input device can scan.
Here are some advantages of using token-based authentication:
Less vulnerable to digital theft: Tokens are less vulnerable to attacks like phishing or digital theft since an attacker has to seize possession of the token to gain the access it grants. In 2022, Cloudflare was able to thwart a phishing attack because their employees used security keys.
Enhanced security: Tokens offer increased security compared to passwords, making them impervious to attacks.
Scalability: Token-based authentication is highly scalable, as it does not require server-side session storage. This makes it suitable for organizations with a large number of employees.
Since it’s unrealistic to expect users to own dedicated security keys, this authentication method is most prevalent in workforce scenarios i.e. for employees to authenticate on corporate apps and systems.
Factors to consider when choosing an authentication method
Choosing the right authentication method depends on several factors. For example, an eCommerce authentication flow catering to customers will differentiate from the authentication process of applications serving employees. As you configure auth in your next software project, you should weigh the following factors to determine which approach is best suited to your needs:
Security: Choose an authentication method that secures customer identities without imposing too much friction during the authentication process.
User experience (UX): Consider how your authentication method will make account management easier and more intuitive for users. Try to minimize burdens like memorizing complex passwords or answering security questions.
Scalability: An authentication method that works seamlessly for smaller businesses may not be as well-suited to larger enterprises. If you are a small business or early-stage startup, choose an authentication method that can scale with any potential future growth.
Compatibility: Your authentication method should fit seamlessly within your current tech stack, systems and protocols. Try to avoid overlapping or conflicting methods and consider integrations like enterprise SSO if you are building a workforce app.
End-user preference: If possible, conduct user research to determine which authentication methods your app’s users are already familiar with. Your users’ demographics, preferred devices, perceptions of privacy, and geolocation all influence their preferences.
Compliance: Several regulatory frameworks have IAM requirements you’ll need to uphold. For example, the Payment Card Industry (PCI) has long required MFA for DSS compliance with increased burdens on non-console access implemented in 2017.
Cost: Building authentication comes at a cost, especially if done in-house. Consider how adding an authentication method will impact your app’s architecture and code, what supporting systems you need to put in place (e.g. reset processes, account recovery), and whether you need to add fraud prevention controls in place.
When choosing between user authentication methods, prioritize solutions that make developers’ and end users’ lives easier without compromising security.
Drag-and-drop any auth method with Descope
There are many types of authentication developers can use when designing an application, but the bottom line is that building authentication in-house can get complicated quickly.
Descope, a no-code CIAM platform, can help you easily add any authentication method, whether password-based or passwordless, to your app using minimal coding. Our workflows also let you easily modify or update authentication methods in the future without rewriting your app’s code.

Sign up for a Free Forever account with Descope to drag and drop your authentication flow. Have questions about our platform? Book time with our auth experts.





