Table of Contents
What is FIDO2?
In 2023 47% of online shoppers abandoned their online cart because they forgot their password. And 60% gave up accessing an app for the same reason.
With passwords creating such friction and being a constant target of cybercriminals, how can organizations provide a better user experience and security? A popular answer has emerged: FIDO2 passwordless authentication.
In this blog, we'll break down the essentials of FIDO2, exploring its features, and share how it's shaping the future of online user identification.
What is FIDO2?
FIDO2 is an open authentication standard that enables users to log into desktop or mobile applications without using passwords.
FIDO2 was developed by the FIDO (Fast Identity Online) Alliance, an open industry consortium of tech companies formed in 2013 with the mission to develop and promote passwordless authentication standards and protocols.
Instead of passwords, FIDO authentication uses registered devices or FIDO2 security keys to validate user identities.
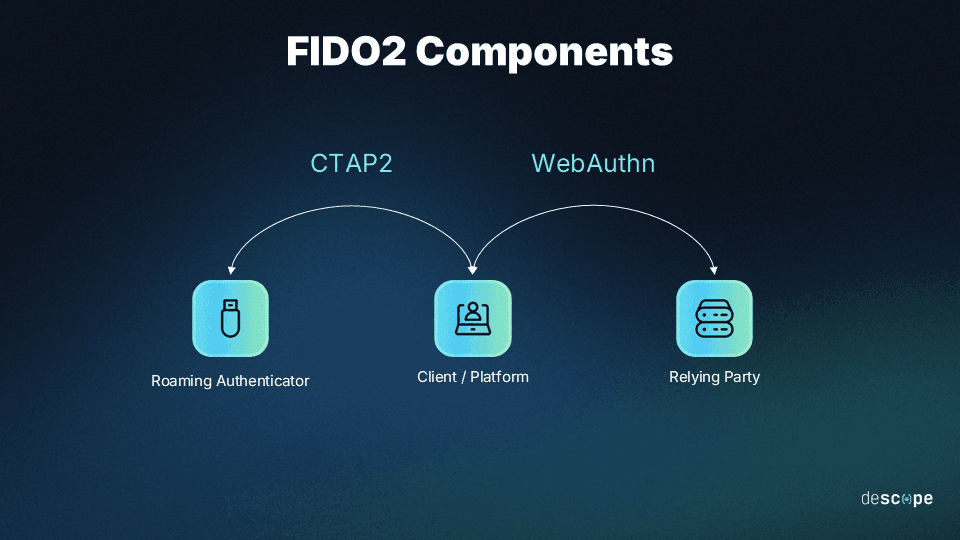
FIDO2 consists of two components:
The Web Authentication API (WebAuthn), which enables applications to authenticate users with possession-based and biometric authentication.
The Client to Authenticator Protocol (CTAP), which enables the client to communicate with a roaming authenticator, such as a hardware security key or a smartphone.
By combining these components, FIDO2 provides a more secure and user-friendly authentication experience, reducing the reliance on passwords that are often susceptible to various security threats like phishing and credential stuffing attacks. FIDO2 is supported by 95% of global user devices, making it a standard for modern, secure authentication.
What is a FIDO authenticator?
A FIDO authenticator is a software component or a piece of hardware possessed by the user that is capable of performing FIDO authentication. FIDO authenticators are used to verify possession and/or confirm user identity. They are also responsible for generating keypairs during user registration, protecting private key details, and signing digital certificates for attestation.
There are two types of FIDO authenticators: roaming authenticators and platform authenticators.
Roaming authenticator
A roaming authenticator is a device separate from the client device that can perform FIDO authentication. Roaming authenticators connect with client devices over USB, Near-field communication (NFC), or Bluetooth. These authenticators enable users to carry their credentials and use them to authenticate on multiple devices. For this reason, roaming authenticators are also referred to as cross-platform authenticators.
Examples: Tapping a USB security key, authenticating using a smartphone when logging in from a laptop
Platform authenticator
A platform authenticator is built into the user device that acts as the FIDO client. Common implementations of platform authenticators include some form of user biometric authentication backed by hardware chips (e.g. Trusted Platform Module, Trusted Execution Environment) that protect cryptographic keys. When a user authenticates using the same device they are logging in from, platform authenticators are at work.
Examples: Apple Touch ID, Apple Face ID, Windows Hello
How FIDO2 works
The goal of FIDO authentication is to shift from “legacy, knowledge-based credentialing” to “modern, possession-based credentialing”. The standard relies on public-key cryptography to achieve this. By using a private-public keypair where the private key never leaves the user’s device, FIDO authentication removes the need for shared secrets between a client and a server.
Here’s how FIDO registration works:
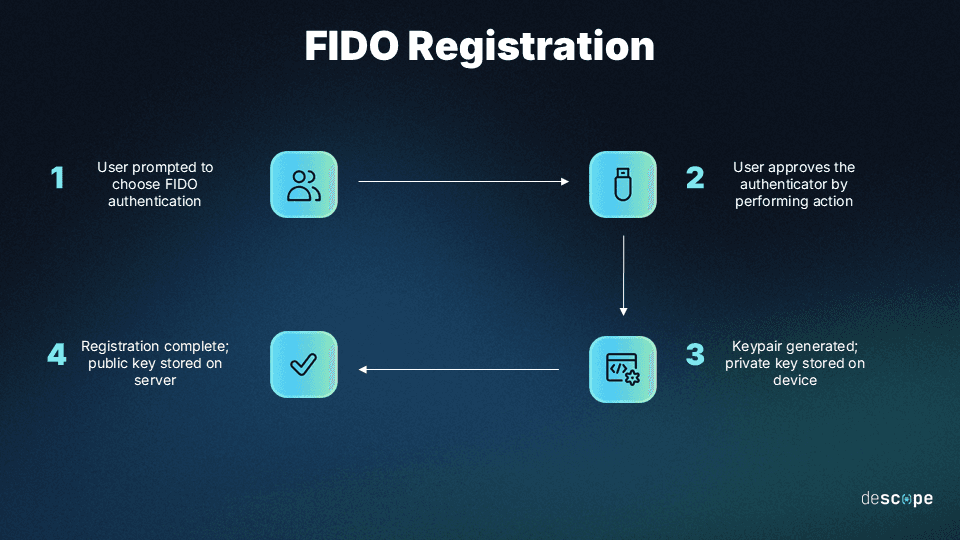
Step 1: During account registration, the user is prompted to choose a FIDO authentication mechanism supported by the application (also called the relying party).
Step 2: The user approves the FIDO authenticator by performing an action that depends on the authenticator. Common actions include touching a fingerprint reader, touching a security key, entering a PIN, or other approved authentication methods.
Step 3: A public-private keypair is created that is unique to the user’s device, the user’s account, and the application.
Step 4: The public key is sent to the application and associated with the user’s account. The private key never leaves the user’s device.
Here’s how login using FIDO works:
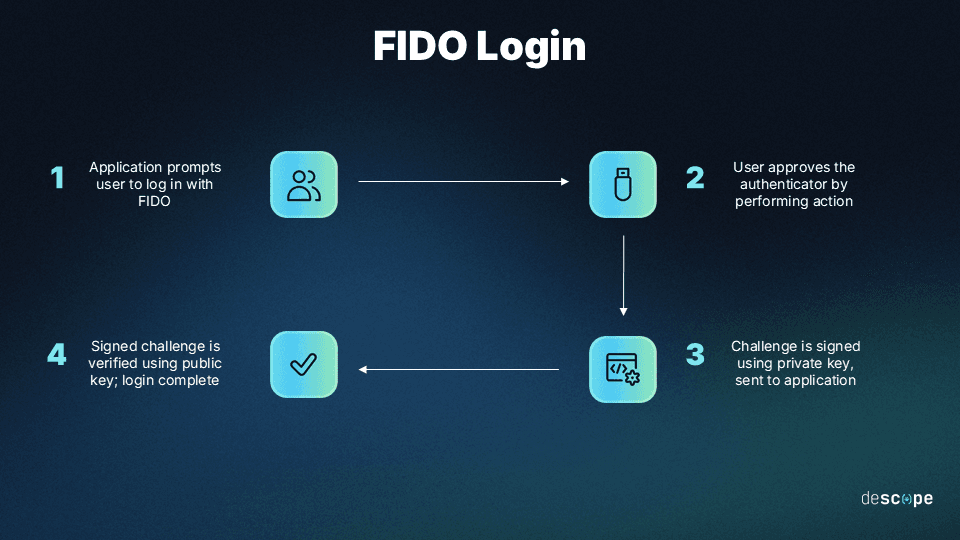
Step 1: During login, the application requires the user to log in with the FIDO authenticator used during registration.
Step 2: The user unlocks the authenticator using the same action that they performed during the registration process.
Step 3: The device looks up the private key based on the ID provided by the application. It signs the request and sends it back to the application.
Step 4: The application verifies the signed request with the stored public key. The user is logged in.
Looking for a way to test your WebAuthn flows? Check out Virtual WebAuthn, a set of Go tools that help developers test WebAuthn flows without needing a browser or an actual authenticator.
FIDO2 vs U2F vs UAF
FIDO2, U2F (Universal 2nd Factor), and UAF (Universal Authentication Framework) are all authentication standards developed by the FIDO Alliance, but they serve different purposes and have some key differences:
FIDO2 is the latest of these standards, combining the best features of U2F and UAF while expanding the scope to provide a comprehensive passwordless authentication mechanism.
Let’s cover the basics of FIDO UAF and FIDO U2F to understand their differences.
Universal Authentication Framework (UAF)
FIDO Universal Authentication Framework (UAF) is an earlier version of FIDO’s open standards that provides passwordless authentication. FIDO UAF enables online applications to leverage native security features on end-user computing devices (like mobile devices and laptops) to perform strong authentication and reduce the reliance on passwords.
FIDO2 is broadly seen as the successor to FIDO UAF.
Universal Second Factor (U2F)
FIDO Universal Second Factor (U2F) is the first FIDO open standard, focused on providing two-factor authentication. FIDO U2F enables applications to supplement the security of their existing password infrastructure by adding a strong second factor of authentication. U2F defines how to establish communications between FIDO2-enabled browsers / operating systems and a FIDO U2F device (like a YubiKey) to implement multi-factor authentication.
After the release of FIDO2, U2F was renamed and is now known as CTAP1.
| FIDO2 | U2F | UAF |
|---|---|---|---|
Primary Focus | Comprehensive passwordless authentication | Strong second factor for 2FA | Passwordless authentication |
Authentication Methods | Biometrics, external security keys | External security keys | Biometrics, local authentication |
Platform Support | Widely supported across platforms, browsers, and devices | Initially focused on 2FA, now supported in various platforms | Varied support, may be limited compared to FIDO2 |
Biometric Data Handling | Stored and processed locally on user's device | N/A | Stored and processed locally on user's device |
Use Case | Comprehensive authentication solution for various scenarios | Strong second factor in two-factor authentication | Passwordless authentication, though less widely adopted |
Benefits of FIDO authentication
FIDO authentication provides a secure, private, convenient, and scalable way for users to access applications without using passwords.
Security
FIDO2 is more secure than traditional password-based authentication methods. Since FIDO authentication doesn’t use shared secrets like passwords, no sensitive user information is stored on application servers. This reduces the attack surface and makes applications less attractive targets for attackers.
Removing passwords also prevents bad behaviors like reusing passwords across online accounts and using boilerplate passwords. This in turn stops identity attacks like credential stuffing, phishing, and account takeover.
Convenience
FIDO2 provides a more user-friendly experience and simplified login process. With FIDO authentication, users don’t have to create and remember passwords, use password managers, or go through cumbersome password reset flows. Instead, users authenticate using built-in device capabilities like fingerprint readers or face scans, or by leveraging easy-to-use FIDO security keys.
FIDO authentication is also convenient for application builders. Developers no longer have to spend time on managing password infrastructure and can instead focus on building core application capabilities. IT teams save time on password-based help desk requests. Product teams prevent user friction and churn caused due to forgotten passwords.
User privacy
FIDO2 results in safer, decentralized storage of biometric data. The use of fingerprint or other biometric authentication methods often raises concerns about user privacy. However, privacy is one of the cornerstones of FIDO authentication. The biometric data used in FIDO authentication is securely stored on the user's device and not transmitted to any external servers. Moreover, since FIDO key pairs are unique for each application, cybercriminals cannot use them to access other services.
Interoperability
FIDO2 is interoperable across various platforms, devices, and web browsers. It’s an open and license-free standard that is meant to be used as widely as possible while also maintaining high security. Any FIDO-certified service undergoes rigorous testing to ensure that clients, servers, and authenticators are all compatible.
Websites can enable FIDO2 with a JavaScript API call that is widely supported across major browsers and platforms, as well as billions of user devices.
FIDO2 implementation considerations
While FIDO2 authentication brings significant advantages, it's important to consider some potential challenges associated with its implementation:
Initial setup complexity: The initial setup process for FIDO2, involving the registration of devices and keys, can be more complex compared to traditional password setup. Users may need assistance or guidance during the setup phase. Organizations implementing FIDO authentication need to invest in user education and awareness programs to ensure smooth adoption and understanding.
Cost of hardware tokens: While some authentication methods within FIDO2 are cost-effective (such as biometrics), external hardware tokens can incur additional costs. This may be a consideration for organizations implementing FIDO2 at scale, especially for their employees and other non-customer stakeholders.
Limited support in legacy systems: Legacy systems and applications that rely on traditional password-based authentication may not readily support FIDO2. Migration to FIDO2 might require updates or modifications to existing systems, which can be a challenge for organizations with a large legacy infrastructure.
Drag-and-drop FIDO authentication with Descope
FIDO2 paves the way to a passwordless future, offering a robust blend of security, privacy and user convenience. However, adding FIDO authentication to your app can be a complex and time-consuming endeavor.
Descope can help you easily add FIDO-certified biometric authentication to your apps with drag-and-drop workflows, SDKs, and APIs. Even if you’re looking to pilot FIDO authentication alongside other auth methods, Descope can federate with your existing IdP to help you add biometrics to Auth0, Amazon Cognito, Firebase, and more.
Sign up for a Free Forever account to get started with Descope and add FIDO2 to your app with only a few lines of code. Have more questions about FIDO2 or our platform? Book time with our auth experts.





