Table of Contents
What is credential stuffing?
In a world where cyberattacks are becoming more frequent and sophisticated, credential stuffing has emerged as a critical threat to organizations. One of the most significant vulnerabilities they face today is the widespread practice of credential reuse. Despite constant warnings to avoid using the same passwords across multiple accounts, many users continue to recycle their usernames and passwords for convenience.
This risky habit creates a fertile ground for credential stuffing attacks, where cybercriminals leverage stolen, reused credentials to gain unauthorized access to systems. Understanding the dangers of credential stuffing and implementing robust security measures is crucial to protecting sensitive data. Let’s explore how you can strengthen your defenses against this growing threat.
Main points:
Credential stuffing targets reused passwords: Attackers use stolen credentials to access many accounts. Users increase the risk by reusing passwords across sites.
Multi-factor authentication adds a barrier: MFA requires an extra step to access accounts. It blocks attackers even if they have the correct login credentials.
Passwordless authentication eliminates risks. Passwordless login methods remove all passwords, preventing attackers from exploiting stolen credentials.
What is credential stuffing?
Credential stuffing is a type of cyberattack where adversaries use previously breached credentials to gain unauthorized access to accounts across various services. These attacks are based on the premise that people reuse usernames and passwords across online accounts.
In a credential stuffing attack, cybercriminals use automated bots to systematically attempt logins with the stolen credentials on a wide range of websites. These automated attempts are made en masse, targeting many accounts across numerous sites in the hope that some login attempts will succeed.
Credential stuffing is a growing concern for organizations of all sizes, and its scale is staggering. According to a 2023 report from Akamai, nearly 61 billion credential stuffing attempts were made across an 18-month period. This shows just how prolific these attacks have become and underscores the widespread nature of the threat.
Credential stuffing attacks are also becoming increasingly sophisticated. According to statistical reports, 81% of hacking-related breaches involve the use of stolen credentials. As more personal data gets exposed in breaches, the number of credential stuffing attempts continues to rise, with cybercriminals now targeting not just user accounts but also high-value systems, such as corporate networks and cloud services.
Credential stuffing vs. brute force attacks
Credential stuffing is a subset of brute force attacks. While both these attacks follow some common themes, they have several noteworthy differences.
While credential stuffing attacks use stolen passwords to attempt logins, brute force attacks try to guess passwords using dictionaries of common phrases or popular “boilerplate” passwords like Qwerty, 123abc, and Password.
How bots are programmed in credential stuffing and brute force attacks also differ. While credential stuffing bots are programmed to try the same username-password combination across various sites, brute force bots are programmed to try multiple username-password combinations on the same site.
Credential stuffing and brute force attacks share one key similarity. They both exploit passwords' inherent weaknesses. Passwords are a flawed authentication method. Brute force attacks assume people use common phrases as passwords. Credential stuffing relies on the assumption that people reuse passwords across accounts.
Credential stuffing vs credential harvesting
While both credential stuffing and credential harvesting are designed to compromise user accounts, they represent different stages in the cycle of cybercrime. Credential stuffing leverages existing compromised data for unauthorized access across multiple platforms, whereas credential harvesting focuses on the initial acquisition of user credentials through deceitful means.
As the name suggests, credential harvesting aims to collect username and password combinations directly from users through deception. This technique often involves phishing, such as sending emails that appear to be from reputable sources asking for sensitive information, creating fake websites that mimic legitimate ones to trick users into entering their login details or distributing malware that captures keystrokes.
Credential harvesting aims to amass as many valid credentials as possible, which can later be used in credential stuffing attacks, sold on the dark web, or leveraged to gain direct unauthorized access to systems and data.
How credential stuffing works
Here’s how a typical credential stuffing attack looks in practice:
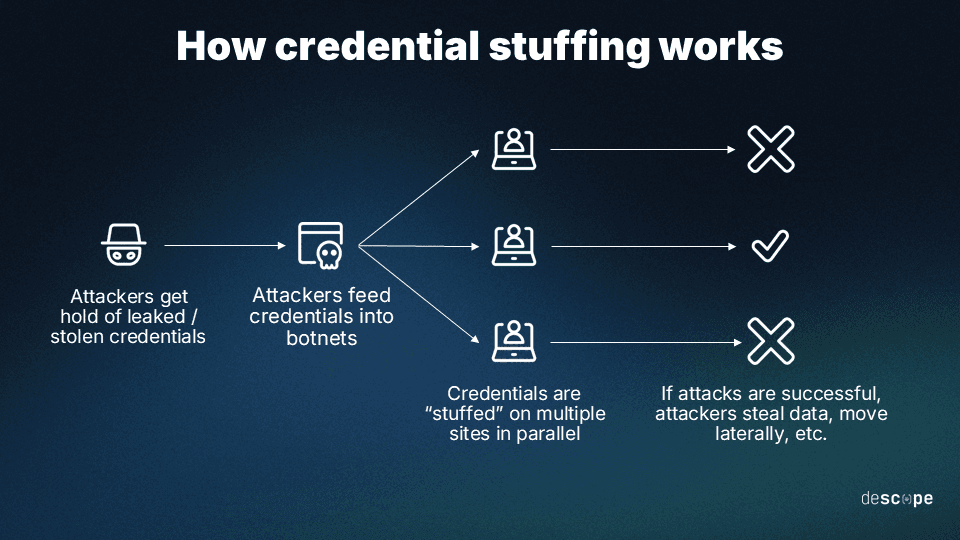
Attackers get hold of stolen usernames and passwords. This is a trivial exercise. Billions of leaked passwords are on the dark web. Phishing attacks are still successful.
Attackers feed the stolen username-password pairs into a botnet, a network of Internet-connected devices controlled by the attacker. Botnets and automation magnify the scale and impact of credential stuffing.
The botnets simultaneously try to "stuff" stolen credentials into many website login forms.
If a login is successful, attackers usually steal personal data, including credit card details and anything else, for profit or further attacks.
A successful credential stuffing attack presents many downstream opportunities for the attacker.
They can sell the validated, stolen login credentials online. Streaming and entertainment services are common victims.
They can commit e-commerce fraud by using saved payment details that allow them to complete high-value transactions for personal use or reselling.
They can change the password and other settings to lock the user out of their account and steal their online identity.
If the account takeover is successful, the attacker can use the victim’s account as a vector to carry out new scams. For example, a Facebook scam involved attackers. They asked for money by pretending to be the victim's friend, stranded in another country.
If the attacker hacks a victim's work account, they can access sensitive information. They can sell it to the highest bidder or use it to ransom the company. People often reuse passwords across personal and work accounts. So, there is a risk.
Learn more: Broken Authentication 101
Why is credential stuffing on the rise?
Credential stuffing is not new, but it has grown in popularity in recent years. Research shows that one in five login attempts comes from bots, which attackers use in credential stuffing attacks. Various market, technological, and societal factors contribute to credential stuffing attacks' popularity.
Passwords are fallible. Users often reuse them across accounts, even though they know it’s risky. Email addresses often double as usernames, increasing the chances of stolen credentials being used on many websites. Passwords rely on something the user knows, leading to poor security hygiene.
Botnets make credential stuffing more scalable and more challenging to detect. They obfuscate or spoof their IP address to bypass security blocklists. Bots are programmed to attempt login on a web application only once, bypassing lockouts caused by repeated failed login attempts.
It's low-cost. It's easy to get credentials and launch credential stuffing attacks. Leaked passwords and stuffing tools are widespread. Attackers only need a few hundred dollars and some patience to strike digital gold.
Remote work, social media, and digitalization have changed our lives. Almost every aspect of life is now online, and there’s an app for everything. This leads to an increase in online accounts and access credentials, which in turn increases the attack surface for credential stuffing.
Credential stuffing risks and impact
Credential stuffing raises various concerns for businesses. It affects their operations, legal status, finances, and reputation. Let’s explore some of the risks and outcomes of these attacks:
Risks
Data breaches: Credential stuffing can allow unauthorized access, leading to data breaches. This exposes sensitive user and business data. It causes many issues for both.
Account takeover (ATO): Attackers can hijack user accounts. This is especially harmful for accounts with special access. It leaves critical system areas vulnerable.
System downtime: A high volume of login attempts can slow down or crash the system, affecting user experience and disrupting operations.
Consequences of successful attacks
Data breaches and privacy concerns: A successful attack often causes data breaches, which endanger user privacy and put companies at risk of legal trouble under strict data protection laws.
Loss of customer trust: Trust is crucial online. Breaches tarnish a brand’s reputation, deterring customer engagement and fostering user turnover.
Legal and compliance issues: Failure to protect user data can breach laws like GDPR and CCPA, leading to fines, lawsuits, and required actions.
Financial impact: The financial toll includes direct losses from fraud, increased security costs, and legal expenses. Losing customers may lead to a potential revenue drop. Harming the brand’s image adds to the financial impact. These impacts hit small to medium businesses particularly hard.
How to prevent credential stuffing
Theoretically, complete credential stuffing prevention is possible. People can achieve this by using unique passwords for each account. But the average person has 100 passwords to remember.
This makes password reuse the most convenient, though unsafe, option. Password managers are another option. One in five Americans uses them. However, attackers need one set of stolen credentials to bypass their security. There's also the fear of forgetting the master password or stealing it. Attackers would then access all the victims' login data.
Organizations can take measures to stop attackers. These measures prevent attackers from using stolen credentials and ensure that they cannot impersonate users.
Passwordless authentication
Passwordless authentication can stop credential stuffing at the source. If there are no passwords to steal, attackers will move on to their next target. Passwordless authentication verifies users with something they have or are. It uses a device, a security key, or biometrics, not a password.
Passwordless authentication improves users' login experiences and reduces organizations' overhead from password storage, management, and resets.
Multi-factor authentication
For organizations that need more time to be ready to ditch passwords, MFA helps stop credential stuffing attacks. MFA adds an extra factor after the username-password combination is entered. This can be a one-time password sent via SMS or email or a biometric check with a fingerprint. The attacker will not have access to any of these.
MFA prevents the attacker from accessing the user’s account, but it does not prevent the attacker from knowing that the username and password are valid.
Sign up for a Free Forever Account with Descope to seamlessly implement advanced authentication, MFA, and bot protection into your applications.
Password hashing
Organizations can use password hashing before storing passwords in their databases. It turns the password into a scrambled representation. This won't stop password theft or decryption. It will give users more time. They can change their passwords on other accounts after a credential theft.
ReCAPTCHA
ReCAPTCHAs show puzzles or challenges. They're easy for humans but hard for bots. Integrating reCAPTCHA can stop bots from submitting login requests, making it harder for attackers to run credential stuffing attacks.
Breached password monitoring
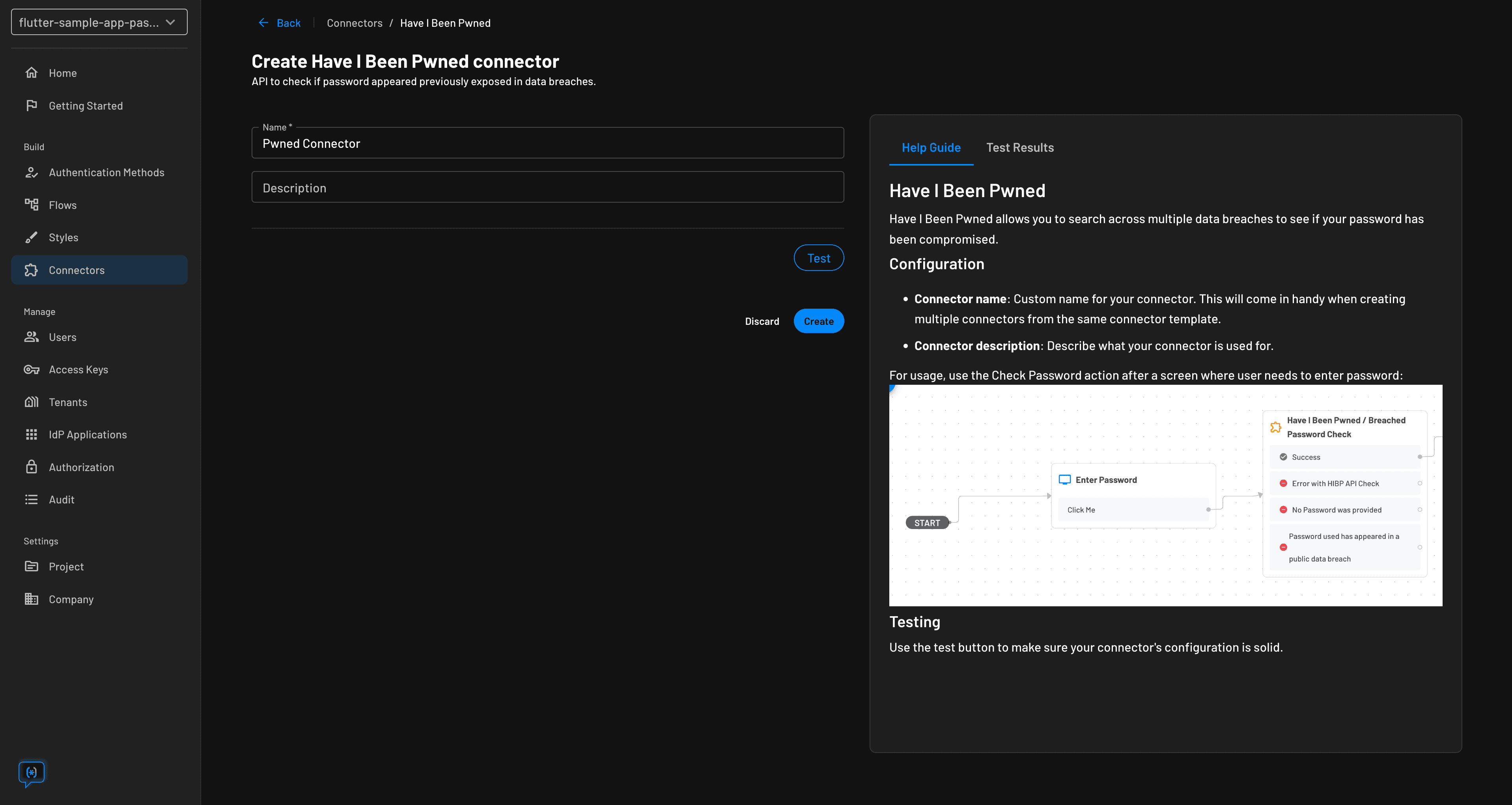
Organizations can check entered credentials against compromised databases like Have I Been Pwned. This helps identify and stop credential stuffing. In fact, organizations can inform the user if the login details match the breached credentials, ask the user to change their password, and request extra factors through step-up authentication.
Prevent credential stuffing with Descope.
Protecting applications from the widespread risk of credential stuffing is essential. Developers and product owners must take critical actions, including setting up in-house protection systems.
Or, they can use third-party systems to prevent and mitigate threats. Descope can help. Our drag-and-drop customer authentication platform helps organizations easily add signup and login capabilities. It also adds MFA, bot protection, and other user interactions to their apps.
Hundreds of customers use Descope to go passwordless and eliminate credential stuffing since there are no credentials to stuff. Our platform makes it easy to add strong MFA, which protects against ongoing stuffing attacks.
Descope is strongly integrated with reCAPTCHA. It helps developers add bot prevention to their auth flows by dropping reCAPTCHA actions into user journeys.
Descope can also improve security without harming UX in a password-auth system.
Our connector with Have I Been Pwned checks for leaked user-submitted passwords.
Configurable security requirements, like password length and complexity, help customers align their password flow with their app's security needs.
Visual error handling and password reset processes can simplify operations and strengthen a password-based system's security.
Sign up for a Free Forever account with Descope to start your journey towards credential stuffing prevention. Have questions about our platform? Book time with our auth experts.





