Table of Contents
What is passwordless authentication?
More passwords have led to more problems for everyone on the Internet. While they are useful for securing information in theory, passwords often create hurdles for users, developers, and admins alike. Using passwords leads to forgotten credentials, frustrating user experience, and (paradoxically), a plethora of security threats.
Enter the era of passwordless authentication—a new approach that precludes the need for passwords and embraces seamless and secure user journeys.
Let’s dive in and see why passwordless authentication is reshaping the experience of users and developers alike. We’ll discuss why it’s needed, cover common passwordless authentication methods in use today, and share how app builders can get started on their passwordless journey.
What is passwordless authentication?
Passwordless authentication is the collective name given to various user identity validation methods that do not use passwords. Instead of relying on traditional password-based authentication, it utilizes alternative forms of validation such as biometrics, magic links, authenticator apps, or similar methods that we’ll explain shortly.
If implemented thoughtfully, this approach not only simplifies the login process but also helps applications get to market faster, adopt and delight more users, and reduce their risk surface against credential-based attacks.
By removing passwords – which are often weak, reused across services, or susceptible to phishing attacks – passwordless authentication reduces the risk of account breaches and identity theft. It represents a paradigm shift in how online accounts are secured without negatively impacting the user experience.
Passwordless authentication vs. MFA
Passwordless and multi-factor authentication (MFA) are sometimes mentioned in similar contexts. Therefore, it’s worth defining the terms separately and understanding where they differ. While passwordless auth replaces password-based authentication with other factors, MFA refers to using two or more authentication factors to validate user identities.
While common MFA implementation involves augmenting passwords with a second (passwordless) authentication factor, MFA can also be completely passwordless. For example, an app can use a fingerprint scan as the first authentication factor and an email magic link as the second authentication factor.
How does passwordless authentication work?
Before getting into the details, it’s worth noting the three generally accepted authentication factors:
Knowledge: Something only the user “knows” (e.g. passwords, security questions).
Possession: Something only the user “has”.
Inherence: Something only the user “is”.
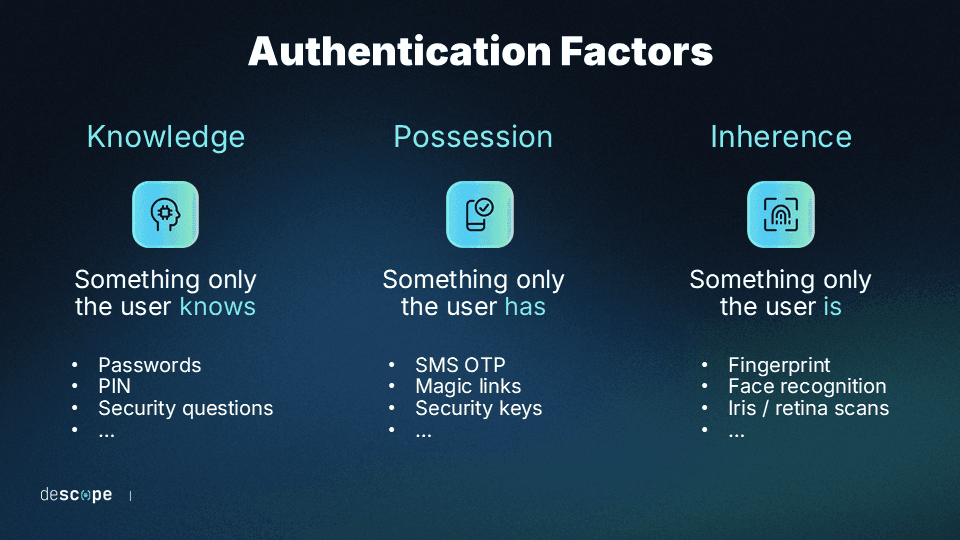
Passwordless authentication works by confirming the identity of a user through alternative means to passwords, focusing on something the user has and something the user is, rather than something the user knows. Here's an overview of the underlying principles and mechanisms:
Something the user has: This could be a mobile device, a security token, or a security key. Authentication is achieved through a unique code or signal generated by the device. For example, a user might receive an email with a one-time passcode which they could use to log in.
Something the user is: Biometric authentication leverages unique physical characteristics of the user, such as fingerprints, facial recognition, or retinal scans. For instance, many smartphones now allow users to unlock their devices and access applications securely using their fingerprint or face scans.
Drag & drop passwordless authentication with Descope
Going passwordless improves user experience and security for any app. However, setting up these authentication systems can be time-consuming. Descope abstracts away the complexity of authentication with a no-code workflow builder, ensuring that developers can spend more time building their core product.

Sign up for Descope's passwordless authentication solution to start your app's passwordless journey.
Password-imposed problems
It's a “shared secret” that passwords can be a hassle. Whether you're trying to remember the right combination of letters and characters, coding them into an app, or working to keep them safe, passwords add a layer of complication to our online lives.
Passwordless authentication methods are the modern answer to this old problem, paving the way toward a smoother and safer digital experience. Here are some reasons why passwords have fallen out of favor and how passwordless authentication addresses these shortcomings.
User friction
There’s no password fan club. The typical Internet user dislikes passwords and the friction they cause from login to checkout. Whether having to create and remember hundreds of unique passwords, going through laborious password reset flows, or constantly updating passwords for security reasons (that aren’t really secure), passwords offer no redeeming value to the average person online.
More than half of respondents to a study by Ponemon said they would prefer a security measure that doesn’t involve passwords. With many applications and websites adopting passwordless login options, users readily switch to platforms offering this seamless experience.
Let’s consider two equivalent applications vying for the same user: One app asks users to create a strong and unique password, while the other authenticates them with a fingerprint on their phone.
Which app is the user more likely to have a good first experience with? More importantly, which app is the user more likely to return to?
The statistics don’t lie – According to FIDO, one-third of consumers have abandoned attempts to access an online service due to forgotten passwords.
Security headaches
Passwords are the “keys to the kingdom” most attackers seek and easily find. According to the 2023 Verizon DBIR, 86% of basic web application attacks can be attributed to stolen user credentials. Why is this number so high?
Firstly, it’s because there’s no shortage of leaked passwords at the attackers’ fingertips. Research from 2022 found 24 billion username and password combinations available on the dark web and other cybercriminal forums.
Secondly, users often adopt bad behaviors when dealing with passwords. Since no one can realistically keep track of hundreds of unique passwords, users resort to “boilerplate” weak passwords or reuse the same password across multiple online applications. This means a data breach on one application gives attackers the ammunition to try the same password on other applications through credential stuffing.
Thirdly, and most importantly, passwords are not a reliable indicator of a user’s identity. Initially designed for individuals to memorize, passwords become a vulnerability the moment they are compromised, allowing anyone who acquires them to masquerade as a legitimate user.
High cost
Implementing passwords compels product owners and app developers to spend time and effort on non-core initiatives, like:
Managing password infrastructure and storage
Creating and updating password reset flows
Adding security controls that protect against password-based attacks
Allotting the help desk’s time to deal with password reset and locked account requests
The list of “password-related labor” is long. Considering these user frustrations and security issues, it's clear this is not work that's greeted with enthusiasm. Time and resources devoted to maintaining password systems come with significant trade-offs, diverting attention from potentially more valuable initiatives.
Benefits of passwordless authentication
Passwordless authentication systems help apps get to market faster, shut down most credential-based attacks at their source, and delight end users. Here are some advantages of going passwordless:
Reduce fraud and account takeover: Eliminating passwords prevents attackers from breaking authentication through credential stuffing, brute force attacks, and phishing.
Onboard and engage more users: Apps that do not require creating and remembering passwords will likely onboard users faster, keep them coming back, and generate a positive brand perception.
Focus resources on core initiatives: Going passwordless eliminates password management and storage, password reset flows, and security investments to protect app servers against password-based attacks.
Passwordless authentication methods
Passwordless methods verify users through a combination of possession and inherence factors. These factors are typically harder to spoof and more reliable indicators of a user’s identity than knowledge factors.
Before we explain the different methods, it’s worth noting that while often considered passwordless, social logins and single sign-on technically are not that. Instead, they delegate authentication to identity providers where users have already created passwords.
Magic links
Magic links are URLs with embedded tokens that – when clicked – enable users to log in without a password. These links are usually delivered to the user’s email account but can also be sent via SMS and other messaging services like WhatsApp.
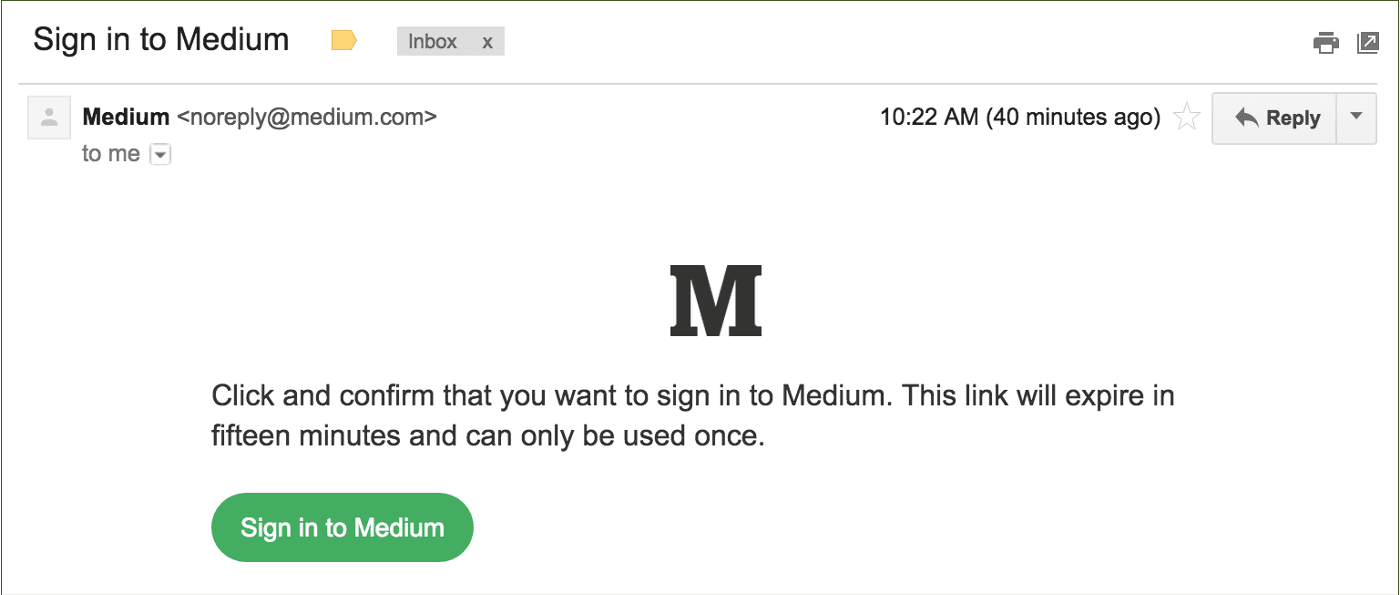
Magic links indicate a user’s identity by verifying “something the user has.” This can be the user's email address (for magic links delivered as an email) or their phone (for magic links delivered via SMS or other phone-based messaging apps).
Did you know? In addition to authentication, you can use magic links in many other scenarios to activate users and grow adoption. For example, if users have items in their shopping carts but do not complete the purchase, you can send magic links that take users directly to those carts.
One-time passwords (OTP)
One-time passwords or passcodes are dynamically generated numbers or letters that grant users one-time access to an application. Unlike passwords, an OTP is not static and changes every time the user attempts to log in.
OTPs can be delivered via SMS, email, messaging apps, and dedicated authenticator apps. Users like one-time passwords because they don’t need to remember them, they usually don’t require new hardware, and they’re already familiar with standard OTP delivery methods.
, showing the Acorns logo at the top and a centered message with the heading Your login code, text stating Thank you for verifying your identity. Your unique login code is followed by a five digit code 19531, and a note below indicating that account security is a priority and recommending changing the password if this was not initiated by the recipient, displayed within a standard email client interface.](/_next/image?url=https%3A%2F%2Fimages.ctfassets.net%2Fxqb1f63q68s1%2F2xUsJ7RqeZAuwyJt3s0O2P%2F8deb2e6c06a927ba44a50b2f7ce8c32b%2FEmail_OTP_example.png&w=3840&q=75)
That said, OTPs can be phished. SMS authentication, in particular, can be vulnerable to SIM swapping and man-in-the-middle attacks. In 2016, NIST proposed that SMS be deprecated as an out-of-band second authentication factor.
Authenticator apps
Authenticator apps operate based on time-based one-time passwords (TOTP). A TOTP code is generated with an algorithm that uses a shared secret and the current time as inputs. This means the code changes at set intervals, usually between 30 to 90 seconds.
Hardware tokens like physical fobs or security keys can also generate TOTP codes. However, authenticator apps (software tokens) are the more widely adopted implementation since they don’t require users to carry hardware other than their mobile phone.
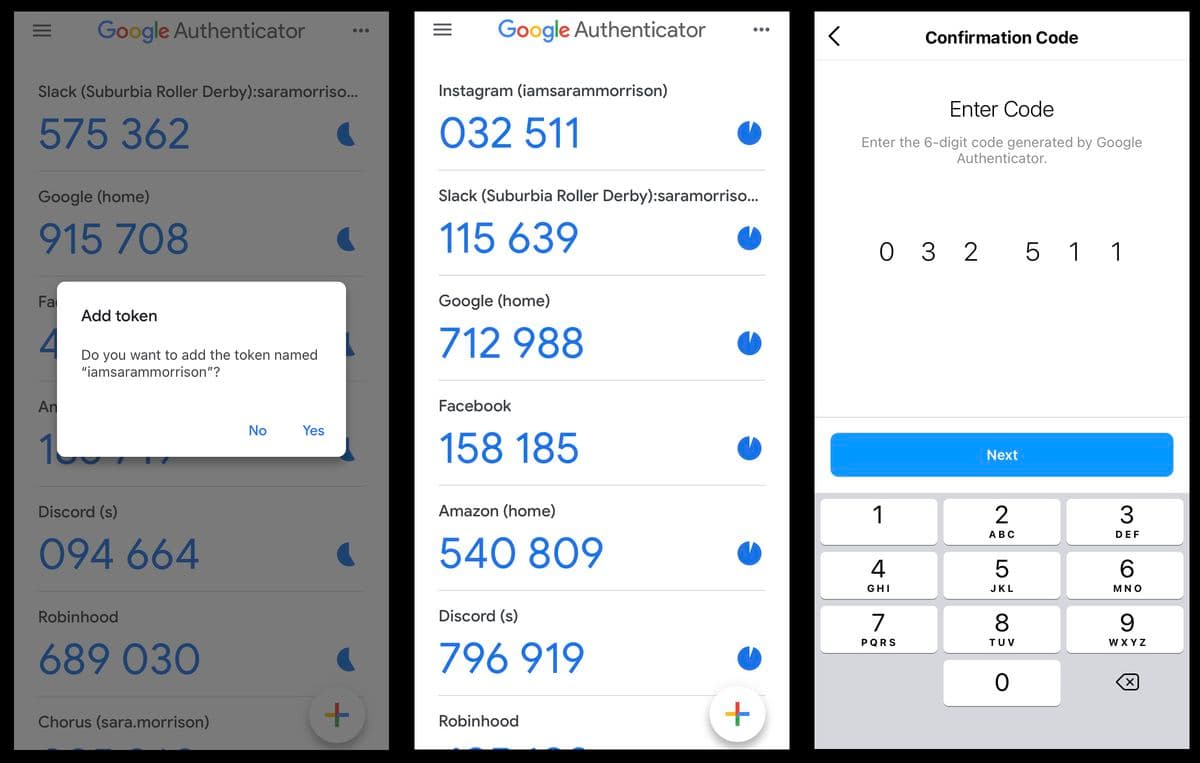
Authenticator apps are considered to be more secure and user-friendly than SMS authentication. It’s very tough for attackers to intercept TOTP codes and gain fraudulent account access.
Additionally, authenticator apps don’t depend on internet connectivity, mobile carriers, or delivery rates, making them usable in a broader range of scenarios than SMS OTP.
Biometric authentication
Biometrics are physical or behavioral traits unique to an individual. Biometric authentication checks these traits to grant users application access. Popular biometric authentication methods in use today include fingerprint scanning and facial recognition.
Biometric authentication adoption has soared due to Apple, Google, Microsoft, and Samsung launching devices with built-in fingerprint scanning and facial recognition capabilities. Cross-device support with methods like passkeys have further accelerated this trend.
Since biometric authentication is based on “who users are,” they are much more challenging to steal and repurpose than passwords, PIN codes, and other forms of knowledge-based authentication.
Did you know? Biometric authentication implemented with the FIDO standard and WebAuthn ensures that the biometric characteristics are securely stored and verified locally on the user’s device. This addresses privacy concerns associated with reading users’ biometric data. Since the data never leaves the device, there is nothing for attackers to compromise.
Read more: 3 Benefits of Biometric Authentication
Tips to implement passwordless authentication
Adopting a passwordless approach can seem like a daunting project to take on at first glance. Here are some tips to help app builders prioritize and phase out passwordless initiatives.
Choose the right method(s) for your users
Not all passwordless experiences are created equal. Above all, the success of a particular authentication method depends on user fit. Consider the following questions before choosing a preferred authentication method:
Are users likely to be aware of the method? Have they used similar techniques on other apps?
Are users accessing the app mainly through desktop or mobile?
How discerning are users about parting with their personal information (even if it’s just their email ID or phone number)?
How security-conscious is the average user? Is security a deciding factor in choosing between two otherwise equivalent apps?
For example, consider a fintech app that users mainly access on their mobile phones. Since the app directly impacts users’ wallets, security is essential.
Considering all these points, this app might consider using WebAuthn-based fingerprint scans to authenticate users. This option is convenient for users (since they are on their mobile devices anyway) and is one of the most secure authentication methods available.
Biometric authentication using WebAuthn uses both a possession factor (the user’s phone) and an inherence factor (the user’s fingerprint), but without the perceived inconvenience that sometimes comes with other MFA implementations.
Pilot, then scale
For apps with plenty of users, it’s prudent to ask some users to test a passwordless technology pilot before rolling it out to the rest of the user base. Lessons learned from the pilot can be applied to the broader rollout.
Moreover, if the pilot's results are encouraging, product owners can share positive user stories to speed up adoption from subsequent user sets.
Invest in user education and messaging
While going passwordless improves user experience, implementing it without proper user education and messaging can have the opposite effect. This is especially true for apps that already have password-based authentication that users are familiar with.
Ensure that users receive communication about the upcoming change to their login flow, why the new way is better, and where they can reach out for any clarification.
Go passwordless with Descope
If you've made it to the end of this article, you likely agree that going passwordless improves both the UX and security of any app. Organizations are sometimes hesitant to go passwordless because of the development effort required to migrate existing authentication systems, implement sophisticated methods like passkeys, and merging users across authentication methods.
Descope can help. Our no-code workflow builder makes it very easy to create and customize passwordless user journeys. You can choose any combination of passwordless methods to create phishing-resistant MFA flows, gradually enroll existing users if you wish, and easily switch out or add other passwordless methods as your app grows.
Sign up for a Free Forever account to start your passwordless journey today. Have questions about our product or an active company project? Book time with our auth experts.





