Table of Contents
1. Biometric adoption is already mainstream
In digital security, the shift away from traditional passwords is unmistakable. With major players like Google moving to passwordless solutions, organizations across industries are rethinking how they approach user authentication. More and more, businesses are turning to biometric authentication for its unique blend of accessibility, security, and streamlined user experience (UX).
Picture your customers logging into your app or platform with a simple glance at their phone or a quick fingerprint scan. This isn’t a futuristic scenario—it’s how millions already access their personal devices. Offering biometric authentication builds on this familiarity to deliver a faster, more secure, and more user-friendly experience.
Let’s explore the key advantages of biometric authentication that help businesses deliver secure and seamless customer experiences.
Main points
Widespread adoption: Customers already trust and use biometrics daily.
Stronger security & privacy: Harder to breach, with data stored locally.
Frictionless UX: Faster logins, fewer resets, and higher retention.
Competitive edge: Stand out with modern, passwordless authentication.
1. Biometric adoption is already mainstream
Biometric authentication is no longer a niche technology:
A 2022 Ciso report analyzing 13 billion logins found that 81% of all devices had biometrics enabled.
In 2024, NordVPN conducted a survey that revealed half (50%) of US respondents use biometrics at least once a day.
Experian’s 2024 Global Identity and Fraud Report showed users felt most secure with physical biometrics (71% US, 75% UK)
For businesses, this presents a major opportunity: integrate biometric login methods that customers already trust and use daily. Whether it’s face recognition or fingerprint scanning, offering biometric authentication allows you to meet users where they are, reducing friction, eliminating password fatigue, and improving overall satisfaction from the very first interaction.
The bottom line? The adoption of biometric login is growing rapidly, and businesses that embrace it are well-positioned to deliver the convenience and speed that modern customers expect.
2. Stronger security for you and your customers
A leading advantage of biometric authentication is its ability to prevent account takeover and fraud. Traditional login methods like passwords and PINs are vulnerable to phishing, credential stuffing, and brute-force attacks. Even basic multi-factor authentication (MFA) often relies on credentials that can be intercepted or reused.
Biometric authentication removes this risk by tying access to something only the legitimate user is, using their unique physical characteristics to verify their identity. Whether it's a fingerprint, face scan, or iris recognition, biometric data is much harder to replicate than knowledge-based credentials.
For businesses, this means fewer compromised accounts, less fraud, and stronger protection across customer-facing applications. When combined with phishing-resistant MFA, biometric authentication offers a powerful upgrade to your existing security stack.
Read more: 5 Popular Biometric Authentication Methods
3. Privacy-first authentication users can trust
Another important benefit of biometric authentication is its privacy advantage. Many customers are understandably cautious about sharing their biometric data.
However, modern authentication standards like WebAuthn and FIDO2 are designed to protect user privacy. Biometric data is stored locally on the customer’s device and never shared with any third parties, including your servers. During authentication, the system uses cryptographic key pairs to verify identity without ever sharing the biometric itself.
This privacy-by-design approach supports compliance with regulations such as the Biometric Information Privacy Act (BIPA) and helps your business demonstrate a commitment to responsible data practices. For your users, it builds confidence that their sensitive information remains secure and under their control.
5. Unparalleled user experience
Another primary reason biometric authentication is so widespread is the UX it offers. For businesses, this presents a competitive advantage. Logging in with biometrics eliminates the need for complex passwords, forgotten credentials, or frustrating resets. It simplifies onboarding, speeds up access, and reduces drop-off at the login stage. This smoother authentication flow directly supports business performance:
Faster login leads to higher conversion rates
Fewer barriers improve customer retention
Reduced friction encourages more frequent logins and ongoing engagement
Since biometric login methods are intuitive and already built into most customer devices, there’s little to no learning curve. Customers can get started quickly, and businesses benefit from a more consistent and reliable access experience.
Bringing things full circle, the same UX improvements that make authentication easier for legitimate users also make it harder for attackers. Without passwords or other credentials to steal, organizations remove a common attack vector. In a threat landscape where more than 86% of web-based attacks involve stolen credentials, removing that risk while improving customer satisfaction is a clear win.
5. Reduced support and operational costs
Password-related issues are among the most common reasons customers contact support. Forgotten passwords, reset requests, and login lockouts generate ongoing costs and drain internal resources. By replacing passwords with biometric authentication, businesses can significantly reduce the volume of these support tickets.
This not only lowers operational overhead but also improves the overall customer experience. Users are more likely to stay engaged with your platform when access is reliable and frustration-free.
Read more: Passkeys vs Passwords: What’s the Difference?
6. Competitive differentiation in a passwordless future
As biometric authentication becomes more widely adopted, it is quickly shifting from a nice-to-have to a customer expectation. Businesses that invest in secure and user-friendly login methods stand out in a crowded market.
By offering biometric authentication, your organization demonstrates a forward-thinking approach to security and UX. It sends a clear message to your customers: that their privacy, safety, and convenience matter. In an increasingly competitive digital landscape, this kind of differentiation helps drive both acquisition and retention, helping grow your bottom line.
What to consider before rolling out biometric authentication
One potential obstacle to biometric authentication comes from users’ inability or unwillingness to use their biometric identifiers. Some customers may need guidance on how to use biometric scanners correctly, especially if they are new to this type of login. Providing simple, accessible onboarding materials can help ease adoption.
If customers express concern about the collection or potential use of their biometric data, it is important to communicate clearly about the privacy-first nature of FIDO-based authentication. Many people mistakenly believe their biometric data is shared with apps or stored on external servers. As mentioned before, biometric data is stored locally on the device and never transmitted elsewhere.
Beyond user-level concerns, the rights associated with biometric data collection are governed by regulations such as the BIPA. To meet compliance requirements and maintain customer trust, businesses should choose biometric authentication solutions that prioritize privacy and transparency.
Device variability is another factor to consider. Some customer devices support fingerprint scanning, while others use facial or retinal recognition. Most modern smartphones and laptops include some form of biometric capability, but it is still important to offer fallback authentication methods for users whose devices do not support biometrics.
The most effective approach is a flexible system that pairs biometric authentication with secure alternatives, ensuring that every customer can access your application with confidence and minimal friction.
Reap the advantages of biometric authentication with Descope
Biometric authentication unlocks a more intuitive, secure, and privacy-first experience for your users. With its seamless adoption, strong security, and improved UX, biometrics is quickly becoming a cornerstone of how people access applications online.
But implementing biometric authentication in-house can be complex and time-consuming. Developers must navigate protocols like FIDO2 and WebAuthn, manage integrations, and maintain the system over time.
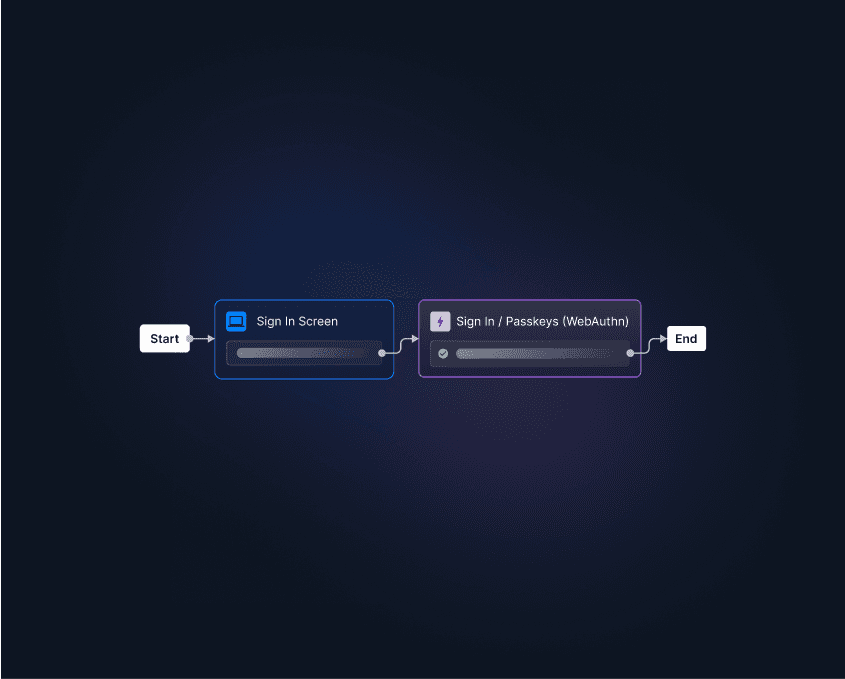
Descope makes it simple. Our no / low-code CIAM platform lets you add passkey-based biometric authentication using visual workflows or just a few lines of code. Built-in support for passkey autofill, multi-device credentials, and secure fallback methods means you can launch a robust, user-friendly biometric login in days, not months.
Sign up for a Free Forever account to get started with Descope. Have questions about our platform? Book time with our auth experts.