Table of Contents
What is facial recognition authentication?
Facial recognition isn’t just a way to unlock your phone anymore. As businesses seek faster, more secure, and user-friendly login options, facial recognition is emerging as a go-to solution for applications ranging from banking apps to patient portals.
Most people are familiar with facial recognition, but fewer understand how it works in authentication. This guide covers the mechanics behind facial recognition login, its key business benefits, and where it’s being used today.
Whether you’re exploring biometric authentication for your product or looking to replace passwords in high-risk environments, this will provide you with the context to make informed decisions.
Main points
Facial recognition enables fast, secure, and passwordless login across high-risk industries and consumer apps.
Authentication happens locally with encrypted data, aligning with WebAuthn and privacy-first security standards.
Reduces login friction, support tickets, and abandonment to boost user retention and operational efficiency.
Easily integrates into apps with device-native biometrics, like Face ID and Android BiometricPrompt.
What is facial recognition authentication?
Facial recognition authentication uses a person’s unique facial features to verify their identity. It’s a type of biometric authentication that relies on an “inherence factor” (something you are), as opposed to a password (something you know) or a device (something you have).
This is a one-to-one verification process, where the facial scan presented at login is compared to a previously stored image of the user's face. This differs from facial recognition used in surveillance, which attempts to identify unknown individuals by scanning large groups.
In practice, the most familiar example is unlocking an iPhone with Face ID. Since Apple introduced it in 2017, facial recognition has become a mainstream authentication method across consumer devices. Its ease of use and strong security profile have made it a go-to solution for organizations looking to modernize access control.
How does facial recognition work?
Facial recognition authentication begins by capturing a user’s facial data through the camera on their device. This data is abstracted into a secure, non-reversible format—typically a mathematical representation of facial features—and stored locally within a secure enclave or biometric vault.
During authentication, the device prompts the user to present their face again. A new scan is captured and compared to the original data:
If the scan is a close enough match, access is granted.
If not, the user may be prompted to try again or use another method, such as a passcode or recovery token.
Most modern facial recognition systems use infrared sensors, structured light, or time-of-flight cameras to build a detailed 3D model of the face. This ensures accuracy across different lighting conditions and prevents spoofing with photos or masks. Behind the scenes, facial features are converted into vectors and processed through a trained neural network that determines similarity based on a predefined threshold.
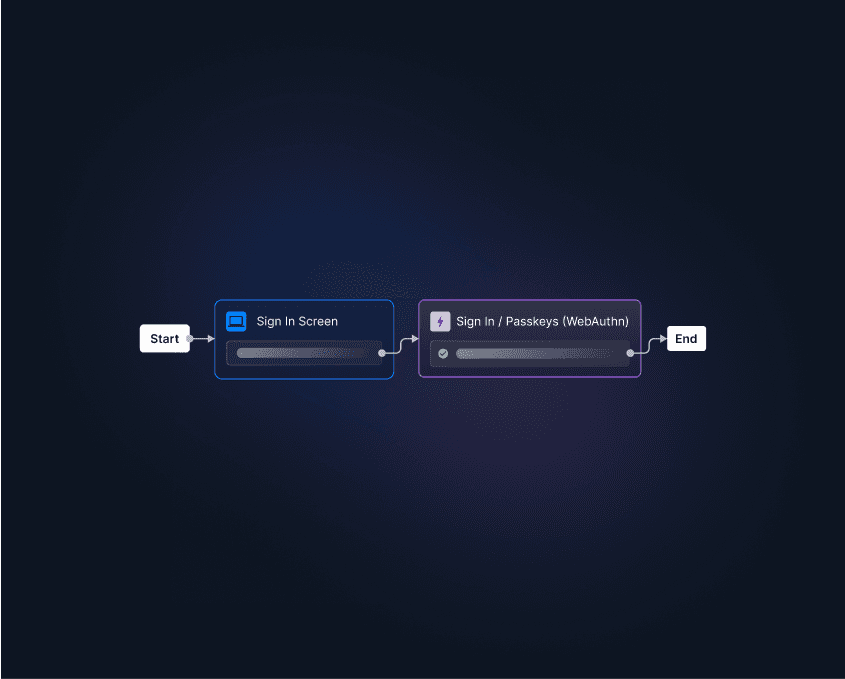
The authentication flow varies by implementation. In most cases, such as Face ID or Android’s BiometricPrompt API, the entire process occurs on the user’s device, never sending biometric data to the cloud. This local-first approach aligns with FIDO2 and WebAuthn standards, helping organizations adopt passwordless login flows while maintaining user privacy.
How accurate is facial recognition?
Facial recognition algorithms have become remarkably accurate in recent years. Top-tier systems now outperform humans in face-matching tasks, even when variables, like age, lighting, or camera angle, come into play.
That said, accuracy can still vary depending on the device hardware, environmental factors, and algorithm training. Some systems may struggle with extreme angles, occluded faces (such as sunglasses or masks), or poor lighting conditions. Additionally, research has shown that facial recognition accuracy can be affected by demographic bias if the training data isn’t sufficiently diverse.
Responsible use entails ongoing improvements, transparent algorithm design, and regular updates to ensure consistent performance across diverse user populations.
Advantages of facial recognition auth
Here are four advantages of using facial recognition technology:
Improved conversion and retention
Facial recognition reduces friction at login, helping users access your product faster and more reliably. By removing the need for passwords or verification codes, it lowers barriers during onboarding and everyday use, leading to higher conversion rates, fewer drop-offs, and greater user satisfaction.
Stronger security posture
Every face is unique, and when paired with liveness detection, facial recognition makes it significantly harder for attackers to gain unauthorized access. This reduces risk from credential stuffing, phishing, and account takeover attacks, helping your organization protect sensitive data and meet compliance standards.
Apple estimates that, with Face ID’s technology in particular, the odds of a random person’s face unlocking another user’s account are less than one in one million.
Lower support and operational costs
Forgotten passwords and account lockouts are top drivers of support tickets. Facial recognition minimizes these incidents by enabling passwordless login, freeing up your support team and reducing operational overhead.
Modern, touchless UX
Offering facial recognition shows users you’re investing in a modern, seamless user experience. The hands-free, contactless nature of this method is particularly valuable in sectors like healthcare, finance, and retail, where safety and speed are paramount. And because it’s built into most smartphones, personal computers and tablets, there’s no need for extra hardware.
Facial recognition applications
Facial recognition authentication has broad utility across industries. Here are just a few examples:
Access control and security
Employee authentication: Organizations can use facial recognition to grant secure access to offices, labs, or restricted areas. Employees authenticate themselves without needing badges, keycards, or PINs.
Visitor management: Approved visitors can verify their identity using a facial scan at self-service kiosks for faster and more secure check-ins.
Financial services
Mobile banking access: Customers can use face authentication to securely log into banking apps and authorize sensitive actions like wire transfers or password changes.
Fraud prevention: Face scans add a biometric layer to high-risk workflows, helping reduce impersonation and unauthorized transactions.
Read more: Customer IAM in Banking: Considerations & Best Practices
Retail and ecommerce
Account login and checkout: Users can authenticate with facial recognition to access accounts, manage orders, or complete purchases, reducing reliance on passwords and improving conversion.
Loyalty program access: Facial authentication enables faster sign-in to member accounts, streamlining repeat purchases and enhancing the customer experience.
Read more: Authentication in Ecommerce: Best Methods & CIAM Tips
Healthcare
Patient portal login: Patients can securely access their health records, test results, or virtual visits using facial recognition on their devices.
Staff access to systems: Clinicians can authenticate into EHR systems or medication dispensing tools with a quick facial scan, improving workflow efficiency in time-sensitive settings.
Read more: Healthcare Identity and Access Management Best Practices
Education
Student portal authentication: Students can log into digital learning platforms or campus apps with face authentication, improving access while minimizing password resets.
Exam proctoring and virtual learning: Facial recognition can be used to verify student identity before remote exams or secure classroom logins.
Enterprise SaaS and workforce tools
SSO and identity verification: Businesses can offer facial recognition as an option in their SSO flows for frictionless workforce authentication across internal tools.
Developer platforms: API-first companies can build facial authentication into their own apps to simplify user access and increase trust.
Read more: The B2B SaaS Guide to Enterprise Readiness
Embrace facial recognition technology with Descope
friction, and adapts to a wide range of use cases. Whether you’re building for finance, healthcare, education, or any other sector, it offers a secure and seamless login experience users already trust.
With Descope, developers can easily add facial recognition to their apps—no deep biometrics expertise required. Our platform supports device-native biometrics, like Face ID and Windows Hello, through passkeys and WebAuthn, all integrated via drag-and-drop workflows.
Need identity verification too? Descope integrates bidirectionally with Amazon Rekognition to support ID collection, selfie checks, and risk-based MFA. These flows can be embedded directly into your user journeys with just a few clicks.
Get started with a Free Forever account and take the complexity out of authentication. Have questions? Book time with one of our auth experts.