Table of Contents
Why strong healthcare IAM is critical
Healthcare identity and access management (IAM) is critical because of the sensitivity of medical records and the regulatory landscape governing their use. At its core, compliance depends on having robust IAM systems that restrict access to PHI and continuously monitor for unauthorized use.
For example, in the United States, organizations that handle personally identifiable information (PII) related to treatments must safeguard protected health information (PHI) under HIPAA. They may also need to comply with other evolving privacy laws like HITECH and state-specific mandates such as the CPRA.
In this article, we’ll discuss how compliance starts (and often fails) with IAM.
Main points
IAM is foundational to compliance and security. With rising data breaches and strict privacy laws like HIPAA, IAM is a non-negotiable for healthcare organizations.
Authentication must balance security and usability. MFA, passkeys, and adaptive auth help keep accounts secure without disrupting patient or partner experiences.
Modern authorization requires layered models. RBAC, ABAC, and ReBAC work together to grant the right level of access based on role, context, and relationships.
Implementation should prioritize interoperability and consent. IAM systems must integrate across platforms, support mobile flows, and give users control over their data.
SMART on FHIR compatibility ensures compliant authorization. Applying this standard ensures seamless integration with major health record systems like Epic and Cerner.
Why strong healthcare IAM is critical
Over the past decade, the healthcare industry has seen a dramatic increase in security incidents. In 2014, there were 39 reported breaches; by 2024, that number had surged to 598. The number of individuals impacted rose even more significantly, from under 25,000 in 2014 to over 250,000 in 2024. These breaches not only compromise patient privacy but also result in serious consequences for the organizations involved. HIPAA penalties can exceed $2 million per violation, and reputational damage, remediation costs, and patient churn often add significantly more.
That’s why IAM must be a central pillar—not an afterthought—for any healthcare organization.
Today’s healthcare ecosystem is increasingly digital, with patients and providers interacting through telehealth, mobile apps, e-prescription platforms, and patient portals. According to recent industry data, 78% of hospitals now offer telehealth services, and patient portal usage has significantly grown in recent years. Each of these touchpoints creates new risk vectors that require secure authentication, access control, and identity lifecycle management.
Gartner Buyers Guide for CIAM
Learn common CIAM use cases and recommended evaluation criteria.
Get copy
Beyond regulatory compliance, strong IAM enables:
Reduced breach risk with resilient security and well-defined authorization models
Lower incident response costs via rapid account removal and automated policy audits
Faster access to care with secure, seamless onboarding and user-friendly login options
Improved patient trust and satisfaction through consistent identity experiences
Secure collaboration across labs, payers, pharmacies, and other third-party associates
Authentication: The first layer
In healthcare, authentication isn’t just a technical checkpoint but a critical layer of trust. Whether it’s patients accessing personal records, partners submitting claims, or vendors logging into supplier portals, organizations must ensure that users are who they say they are. Authentication is foundational not just for HIPAA compliance, but for protecting every interaction that touches PHI.
Strong authentication strategies reduce breach risk, streamline access, and uphold patient consent protocols without compromising user experience.
Here are the authentication approaches modern healthcare organizations should consider:
Multi-factor authentication (MFA)
MFA requires at least two factors from different categories: something the user knows (password), has (device), or is (biometric). In healthcare, MFA is now considered a minimum standard for PHI protection. It helps prevent credential-based attacks without introducing excessive friction, especially when paired with mobile push or biometrics.
Passwordless authentication
By removing the need for passwords altogether, passkeys eliminate one of the weakest links in healthcare security. Passwordless methods such as device-bound biometrics or authenticator apps streamline the login process while minimizing the risk of phishing and credential stuffing. They also improve the patient and clinician experience by reducing forgotten-password friction.
Adaptive authentication
Not every login attempt carries the same risk. Adaptive authentication uses contextual signals like device type, location, access time, and behavioral patterns to assess risk in real time. If the risk is low, login proceeds seamlessly. If anomalies occur, step-up authentication kicks in. This allows healthcare systems to reduce friction for legitimate users while elevating defenses for suspicious behavior.
Identity verification
Authentication confirms you’re the right user. Identity verification confirms you are a real person (and the right one). This is especially critical in healthcare, where patient access often involves uploading a driver’s license, passport, or performing a selfie liveness check. By integrating identity verification with services like Incode and Amazon Rekognition into authentication journeys, healthcare orgs can verify identities without pushing users to third-party sites or disrupting flow.
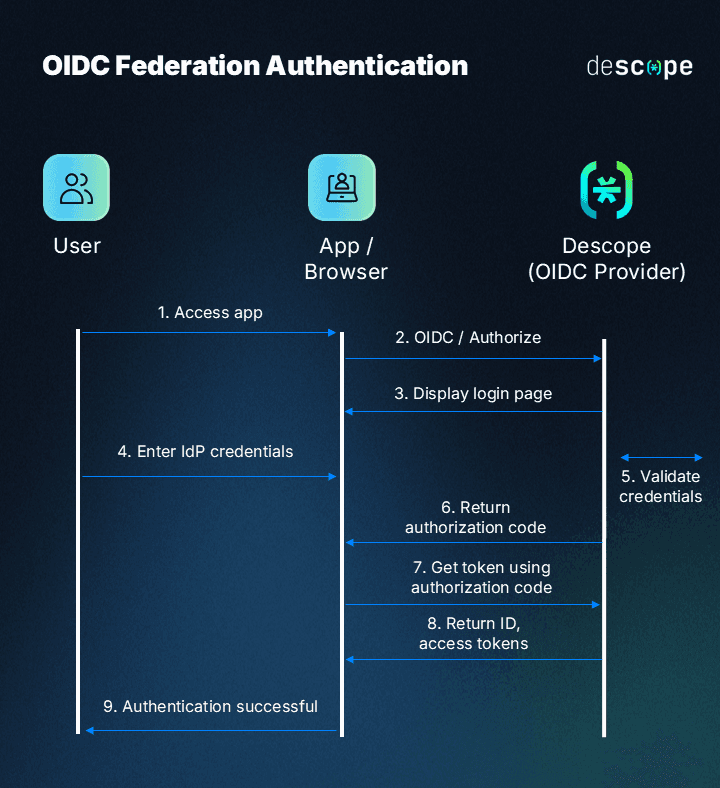
Federated authentication
Healthcare organizations often work with a network of external portals for suppliers, labs, payers, and even internal apps. Federated authentication allows these systems to trust a single identity provider, enabling secure and seamless access across platforms. This centralizes identity management, simplifies user experience, and improves visibility across all access points, which is key for governance and auditing.
Authorization: The second layer
Once the system confirms a user’s identity through secure authentication, the next step is determining what they’re allowed to access and under what conditions. That’s where authorization comes in.
In healthcare, authorization governs how patients, providers, partners, and vendors interact with sensitive data. It defines the boundaries: who can access what, when, where, and how. As more users engage with systems across portals, apps, and third-party platforms, managing external access with precision is critical to minimizing risk and maintaining compliance.
To manage this securely and efficiently, organizations can implement a layered authorization strategy:
Role-Based Access Control (RBAC)
RBAC assigns permissions based on predefined user roles, each with an associated access template: pharmacist, lab partner, billing vendor, and so on. This approach is ideal for healthcare scenarios with clearly defined and predictable roles.
For example, a pharmacy partner might have permission to submit prescription data, but no access to diagnostic notes. RBAC enforces the principle of least privilege at scale, helping organizations meet HIPAA and HITRUST requirements with less overhead.
Fine-Grained Access Control (FGA)
Fine-grained authorization enables more granular control than RBAC. FGA’s two implementation patterns are Attribute-Based Access Control and Relationship-Based Access Control. Consent-driven, fine-grained policies enforced by these authorization strategies are crucial for modern patient-centric care models and are often required under data privacy regulations like the 21st Century Cures Act.
Attribute-Based Access Control (ABAC)
ABAC adds contextual awareness by using attributes like user role, location, device, access time, and behavior to determine access rights dynamically. This is especially useful in healthcare, where sensitive data may need tighter controls.
For instance, ABAC can block access to patient records outside business hours or from unapproved geographies. It's more flexible than RBAC and essential for organizations with complex workflows and compliance constraints.
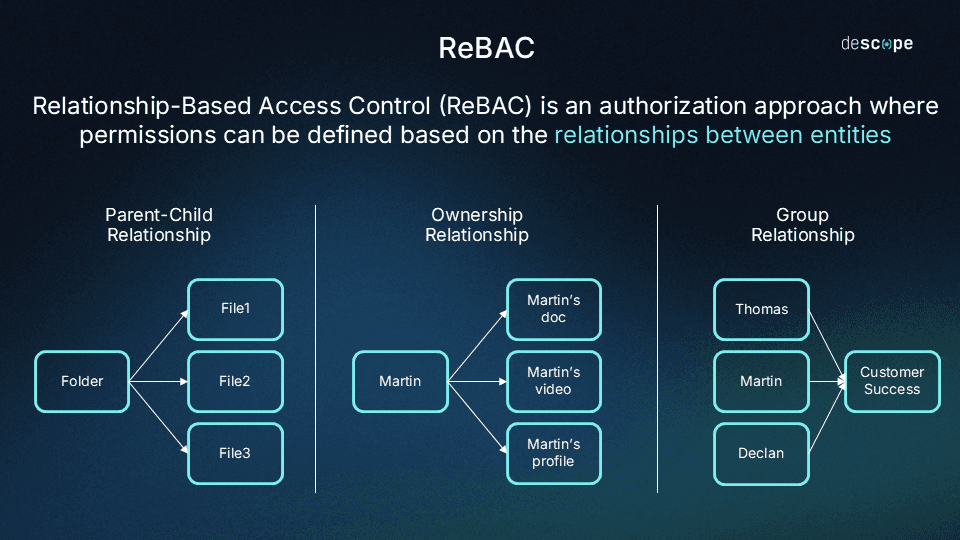
Relationship-Based Access Control (ReBAC)
ReBAC determines access based on relationships between entities, for example, between a patient and their primary care provider, or a caregiver and a dependent. It’s especially valuable in healthcare, where permissions often depend on contextual relationships rather than static roles or attributes. ReBAC enables granular sharing, like allowing a specialist to access only the records of referred patients.
Read more: RBAC vs ReBAC: Which Is Right for You?
Combining models for real-world flexibility
These models aren’t mutually exclusive. In practice, many healthcare orgs implement RBAC with ABAC overlays, using role templates for standard access while layering on dynamic rules (e.g., denying access from outside the U.S. even for authorized roles). This hybrid approach supports scalability while offering the precision needed for patient privacy.
Read more: RBAC vs. ABAC: What’s the Difference?
Healthcare EHR integration
Healthcare organizations increasingly need their applications to work seamlessly with EHRs like Epic, Cerner, and other clinical systems. SMART on FHIR is the healthcare industry standard that makes this possible. By leveraging OAuth 2.0 and OpenID Connect (OIDC), SMART on FHIR lets apps (and users) securely connect to any major EHR platform.
With SMART on FHIR, healthcare organizations can:
Connect new apps to existing EHR systems without custom integrations
Ensure patients and providers have consistent login experiences across all apps
Meet healthcare compliance requirements for data sharing and interoperability
Reduce development time and costs when building healthcare apps
Instead of building separate connections for each EHR system, SMART on FHIR allows you to use one standard approach that works for every app. That makes it easier to scale your healthcare stack and provide better patient care, everywhere.
Implementation considerations and best practices
Designing and deploying a healthcare IAM system isn't just about choosing the most secure option but it's about balancing security with usability, especially across patient-facing apps and external partner workflows. The best solutions protect sensitive data while keeping the user experience intuitive and responsive.
Here are key considerations healthcare organizations should prioritize:
Balance security with usability
Patients expect seamless access. Long load times, password resets, or complex login flows create friction and can lead to disengagement or abandonment. That said, convenience can’t come at the cost of security. IAM solutions must provide smooth experiences while resisting phishing, account takeovers, and credential stuffing.
Prepare for evolving threats
Healthcare remains a top target for ransomware, phishing, and supply chain attacks. IAM implementations should prioritize phishing-resistant authentication, device-based trust, and adaptive security policies that evolve with the threat landscape.
Built-in consent and privacy controls
HIPAA and modern patient expectations both demand clear consent flows. Patients should be able to manage who accesses their data, when, and for what purpose—and IAM systems should enforce these rules dynamically. All access should be fully logged to support compliance reviews and incident forensics.
Prioritize interoperability
IAM should work across electronic health record (EHR) systems, pharmacies, lab networks, and payer portals without forcing workarounds. Supporting industry standards and APIs makes identity flows consistent across platforms, enabling care teams, patients, and partners to connect without compromising security.
Support native mobile authentication
The mobile health market (mHealth) is booming, expected to hit $296B by 2032. Healthcare apps must offer native, low-friction authentication that feels seamless across iOS, Android, and mobile browsers. Whether it’s biometric login or deep linking to native flows, poor mobile auth UX should never hold back engagement.
Offer self-service IAM
From resetting a password to registering a new device or managing account preferences, patients and partners should be able to manage their identities without relying on support. Embeddable UI components help healthcare organizations deliver a consistent, secure experience across every touchpoint.
Healthcare IAM that’s effective and simple
In healthcare, where patient trust, regulatory compliance, and seamless access are all mission-critical, a modern IAM approach is no longer optional; it’s foundational. Protecting sensitive health data while enabling secure collaboration across patients, providers, and partners requires authentication and authorization flows that are both airtight and user-friendly.
Descope helps healthcare organizations meet these challenges head-on. Our drag & drop CIAM platform supports passwordless authentication, consent-based access, mobile-native flows, and federated authentication across third-party systems, so you can secure every user interaction without compromising experience or compliance.
Get started with a Free Forever Descope account, or book a demo to see how we can support your IAM strategy.