Table of Contents
What is adaptive authentication?
Security teams today face a dilemma: How do you balance security with user experience without sacrificing either? While traditional multi-factor authentication (MFA) adds crucial protection, aggressive authentication methods frustrate legitimate users with roadblocks.
Enter adaptive authentication, which solves this challenge by dynamically adjusting security based on real-time risk signals. Instead of applying the same high-friction steps for every login, adaptive authentication intelligently assesses when to prompt for additional requirements.
This risk-based approach delivers stronger security for high-risk logins and maintains effortless access for known users. Smooth sailing when it’s safe, right-sized friction when there are red flags.
Main points
Dynamic risk signals: Adaptive authentication looks at contextual factors like device, location, and IP address to determine authentication requirements in real time.
Better user experience: Low-risk logins breeze by without triggering MFA; high-risk attempts trigger additional measures only when necessary.
Flexible implementation: Works in combination with existing MFA and aligns with modern security best practices, like zero-trust principles.
What is adaptive authentication?
Adaptive authentication, also known as “risk-based authentication” or “risk-based MFA,” is a dynamic form of MFA. Traditional MFA approaches require at least two authenticating factors by default at login. This usually includes at least:
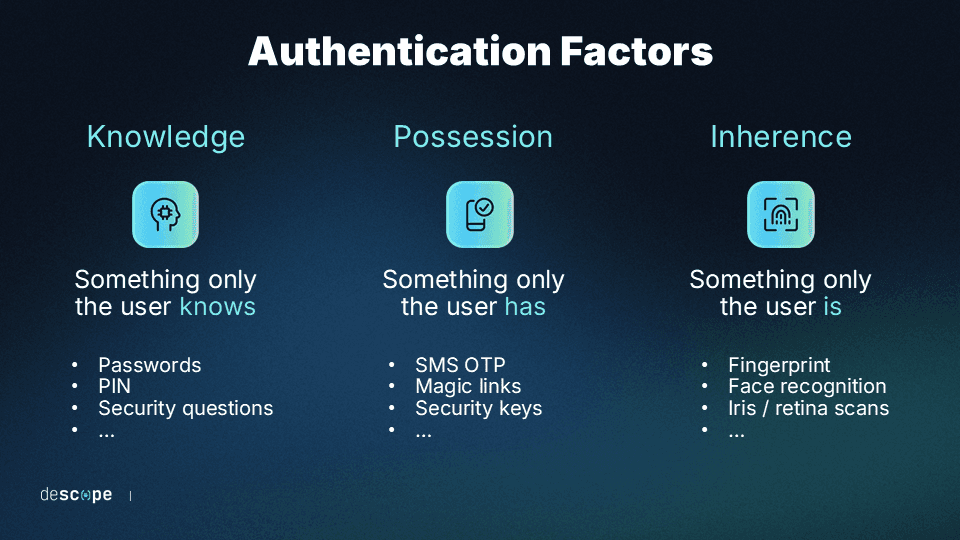
One knowledge factor (like a password)
One possession factor (like a secondary code or device)
One inherence or biometric factor (like a fingerprint or facial scan)
This is a static requirement in traditional MFA, meaning the same set is always required. But in adaptive authentication, the number and type of factors needed depends on the risk present during the login.
Some elements that determine whether and which additional credentials are needed are the hardware and software used. For example, users who log in from a new device or an unknown network may be asked for additional credentials.
Other factors involve the login attempt's context, like the time or the user’s location.
Adaptive vs. step-up authentication
Adaptive authentication is closely related to step-up authentication, where additional authentication measures are taken after login, depending on the user’s actions. The most significant difference is that adaptive auth front-loads the security assurance, factoring risks from the login attempt rather than post-login actions.
While both adaptive and step-up authentication enhance security by adjusting requirements, they differ fundamentally in their triggers and philosophy.
Adaptive authentication responds to risk signals present during the login attempt itself. It evaluates contextual risk factors like:
Device fingerprints and trust levels (i.e., has this device/browser been seen before)
Geographic location and IP reputation
User behavior (e.g., reCAPTCHA)
Think of adaptive auth like the door attendant at an upscale apartment building. They assess each person trying to enter and decide whether to examine additional ID. The attendant knows people who come through regularly, like frequent guests and residents. But if someone from out of town drops by, the attendant will ask for proof they’re allowed in.
Step-up authentication, by contrast, activates every single time during an already-authenticated session if users attempt specific (typically sensitive) actions. Common triggers include:
Accessing financial info or personal data
Initiating high-value transactions
Modifying account settings (like passwords and MFA)
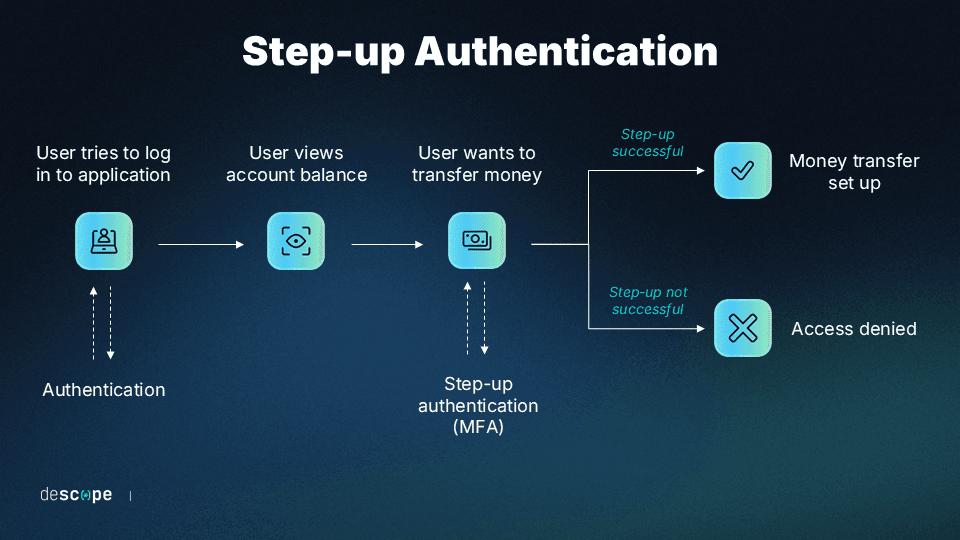
Step-up auth works more like security checkpoints within an airport. Anyone can hang out in the entry area without showing identification. Accessing the concourses means you need to prove your identity and that you have a legitimate reason to enter.
Aspect | Adaptive Authentication | Step-Up Authentication |
|---|---|---|
When Applied | At login (based on risk signals) | During a session (triggered by specific actions) |
Basis for Decision | Contextual risk factors | Predetermined sensitive actions |
User Experience | Variable based on context | Variable based on actions |
Primary Goal | Prevent unauthorized access to whole account | Protect sensitive actions and information |
In the real world, many organizations combine both approaches for comprehensive protection. For example, Amazon might use adaptive authentication and allow a known device to log in without a second factor. However, if the user attempts to change authentication settings during that session, they’ll be “stepped up” to submit a second factor.
This layered approach creates a consistent security environment where and when it’s needed. Since users rarely change their auth methods or private info, this friction is usually accepted as a necessary security measure. Meanwhile, adaptive auth is only seen when certain conditions are met, meaning regular activity is virtually never interrupted.
How does adaptive authentication work?
Adaptive auth works much like any other MFA system, with an added step to qualify which credentials are needed or if additional credentials are needed at all.
From the user experience side, logging in through adaptive authentication looks like this:
Users attempt to log in to their accounts in an app or website as they would normally
If the login attempt is deemed risky, they’ll be prompted for additional credentials
Upon entering the additional credentials, they’ll have access to their account
Other step-up authentication may be triggered, depending on their actions
Depending on the website, app, or program interface, the user may be prompted that a risk analysis is occurring. If conditions are normal, login could be seamless.
On the development side, processes that go into an adaptive auth workflow include:
Collecting user behavioral data and contextual information to form a baseline
Assessing risk levels based on user behavior baselines and anomalous conditions
Customizing specific authentication requirements based on the risk assessment
Automating the real-time decision of which factors are required to streamline login
It should be noted that every implementation of adaptive auth will work slightly differently. For example, apps with disparate access restrictions for different users might utilize other criteria depending on each account’s privileges. Those with access to the most sensitive data might require a biometric alongside a password and secondary account. In contrast, those with less sensitivity might require two knowledge factors, like a password and a security question.
Examples of adaptive authentication in the wild
Here are some potential uses of adaptive auth in real-world scenarios:
Example 1: Ecommerce protection
If you’re shopping online and log in to your preferred shopping app, adaptive authentication can notice you're on your usual device and network. Hence, it only asks for your password. If you add a pricey item to your cart, it senses the change and prompts for a fingerprint scan or phone code. Once verified, your purchase is secured, thanks to adaptive auth's watchful eye.
Note: The above is also an example of step-up authentication.
Read more: Authentication in Ecommerce: Best Methods & CIAM Tips
Example 2: Corporate network access
Logging in to your work network is usually password-only from your regular computer. But when you're on a new device in a different place, adaptive authentication steps in. It sends a mobile notification for your approval, ensuring safe access to company data even on the go.
Example 3: Social media security
Logging in to social media is usually a password-only affair on your device. But adaptive authentication steps in when you use a public computer in a new place. It sends an email code for extra verification, adding a layer of security to your account. Adaptive authentication keeps your online presence safe, no matter where you log in from.
Example 4: How Descope uses Descope
At Descope, we use opt-in adaptive authentication on our own platform to protect thousands of developer accounts. For companies that enable it, our implementation only requires additional authentication when we detect anomalies like new IP addresses or unfamiliar devices.
Meanwhile, devs can choose their preferred MFA method (passkeys, TOTP, etc.) to ensure minimal disruption.
Read more: How Descope uses Descope for Customer Authentication
Benefits and drawbacks of adaptive authentication
Adaptive authentication has notable benefits and some drawbacks to consider.
Benefits of adaptive authentication
Strong MFA when necessary: Similar to how MFA adds security layers over passwords, adaptive authentication further reinforces MFA by incorporating risk-based elements. While MFA is more secure than most traditional password-based solutions, it's still susceptible to attacks, such as SIM swapping, channel hijacking, and MFA bypass.
Improved user experience: Adaptive authentication addresses user experience concerns. It allows easy access for users under normal, lower-risk conditions with just one set of credentials.
Alignment with zero trust: Adaptive authentication aligns well with zero-trust architecture (ZTA) principles.
Drawbacks of adaptive authentication
New technology challenges: Being relatively new, adaptive authentication might not always work as intended when integrated into older technology systems.
Complexity: Adaptive authentication is more complex than static methods. It could require more resources for implementation and management, from employee understanding to account management.
While adaptive authentication offers various benefits, you must manage its challenges effectively for the best results. The best way to ensure the benefits outweigh the drawbacks is by streamlining your adaptive authentication flows with a platform like Descope.
Choosing the right adaptive authentication provider
When evaluating adaptive authentication provider solutions, consider the following key factors:
Flexible risk assessment: Look for customizable risk configurations that allow you to tweak parameters for different use cases and scenarios
Comprehensive signals: Be mindful of solutions that don’t integrate with external services and rely solely on internal data; these are unlikely to have a complete picture
No-code implementation: Adaptive auth can be tough to get perfectly right on the first try, which is why easy implementation can be a major differentiator
Proven at scale: Whether you’re already a large organization or not, serving adaptive auth to millions of users calls for strong backend infrastructure
Questions to ask vendors
The following questions will help you better understand a vendor’s strengths (and potential gaps) while moving a conversation about implementation forward:
How does your adaptive auth solution minimize false positives while maintaining a strong security posture?
What specific risk factors does your platform analyze, and can we add custom signals using our own data?
How quickly can we modify adaptive authentication flows when threats or needs change?
Can we A/B test adaptive auth flows against step-up MFA (or another scenario) before deploying them to every user?
Integration with IAM platforms and CIAM systems
Your adaptive auth solution should seamlessly connect with your existing (and future) infrastructure. Key connection points include:
Support for standard protocols (SAML, OIDC, OAuth 2.0/2.1)
REST APIs and SDKs for custom integrations
Works alongside (not replacing) your existing auth system
Provides identity federation, SCIM, and SSO to unify user management
Keep in mind that there’s rarely a one-size-fits-all approach to adaptive auth; in fact, it’s practically in the name. The right vendor will provide the tools your team needs to make adaptive authentication work for your specific users and business model without disrupting your existing identity management or degrading user experience.
Read more: IAM vs. CIAM Explained & How to Choose
No-code adaptive authentication with Descope
Adaptive authentication aims to blend safety and ease of use. Adjusting to real-time risks keeps your online world protected and hassle-free. However, building adaptive authentication in-house or stitching together various risk identification systems can be complex.
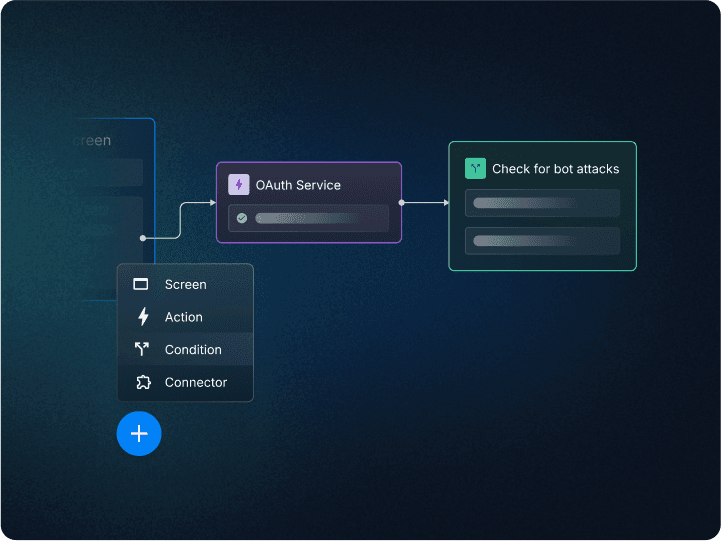
Descope helps organizations easily add adaptive authentication to their user journey flows with a no-code editor. Conditional steps can be added to auth flows that check the user’s risk levels and enable MFA only when the risk scores are high.
Apart from natively supporting user risk scores, Descope also integrates with third-party risk identification tools such as Google reCAPTCHA Enterprise and Traceable to enforce adaptive authentication based on external risk scores.
Sign up for a Free Forever account with Descope to “descope” authentication from your daily work. Interested to learn more about how we do adaptive authentication with third-party connectors? Book time with our auth experts.