Table of Contents
What is step-up authentication?
A recent poll from The Baymard Institute reveals that the one of the most-cited reasons customers abandon their carts is “I didn’t trust the site with my credit card information.” This highlights a dilemma for businesses: strengthen security too much, and risk losing customers to friction; lower barriers too far, and potentially expose users to fraud.
Enter step-up authentication, an approach that lets organizations safeguard the most critical touchpoints in the user journey with surgical precision. By reserving stronger authentication for high-risk actions while keeping casual browsing frictionless, step-up authentication offers both security teams and customers the solution they’ve been craving.
This guide walks you through all things step-up auth: how it works, when to use it, and examples to inspire your own implementation.
Main points
Strategic defenses: Applying stronger authentication requirements only to high-risk actions will help organizations focus security resources where they matter most.
Satisfying regulations: Step-up auth enables organizations to meet compliance requirements like PSD2 in finance and HIPAA in healthcare.
Right-sized UX: Users encounter friction proportional to the actions they take; browsing offers smooth sailing, but high-value purchases call for extra security steps.
What is step-up authentication?
Step-up authentication, also known as route-based or “just-in-time” authentication, is a process where the user is asked to provide additional evidence of their identity to access sensitive resources, perform higher-risk actions, or behave in other ways that deviate from their typical usage patterns. This additional layer of security is implemented in response to specific triggers that suggest a higher risk of unauthorized access.
Traditional approaches typically authenticate users once at login, then grant access to all authorized resources. This binary method can add unnecessary friction (since the user might only be browsing) or even leave security gaps (if the barrier for entry is too low). By requiring additional authentication for sensitive resources and actions, “stepping up” security provides an extra layer of protection precisely where it matters most.
This concept is similar to how physical security works in a controlled location. For example, in a hospital, anyone can enter the main lobby with minimal screening, but accessing the pharmacy storage room would require multiple verification steps like ID badges, key cards, and even biometric scanners. Picture this same strategy at work in a digital environment: Even if threat actors bypass the initial authentication check (e.g., with stolen credentials), they’ll encounter more steps before they can access sensitive data or take certain actions.
Common triggers for step-up authentication
Step-up authentication is activated by specific actions or resource requests that have been predefined to “step up” security. Unlike adaptive authentication, which responds to contextual risk signals, step-up authentication triggers are based on what the user is trying to do, not how they’re doing it.
Accessing sensitive data: Whether it’s checking your user profile or protecting your company’s trade secrets, step-up auth creates a fixed barrier to privileged data.
Performing high-value transactions: Most ecommerce organizations want customers to browse unhampered, but when it comes to making a big purchase, step-up kicks in to ensure the right person is at the reins.
Making account changes: Fraudsters often alter account details (email, phone, etc.) to complete their takeover, but step-up auth ensures that only the account owner can commit changes.
Administrative functions: Some actions, like making changes to web pages or adding content to a site, could be damaging in the wrong hands; step-up auth keeps tight control over who can complete these admin functions.
Benefits of step-up authentication
Step-up authentication provides end users and organizations alike with several key advantages:
Enhanced security for critical operations without burdening routine tasks with extra friction
Reduced authentication fatigue as users only encounter additional steps when taking certain actions
Strong defensive posture that’s well-suited for different environments, from customer-facing to high-security
Improved regulatory compliance for strict industries with specific security requirements
Better user experience by applying security in sensitive contexts rather than universally
Reduced fraud risk from focusing security attention on high-risk transactions
Step-up authentication works well because it’s proportional to the sensitivity of the action, so pushback is limited—especially compared to hitting friction from simply logging in. Your organization gets all the benefits of better security where it counts, but you won’t wear out everyday users.
Step-up authentication vs. other security approaches
Understanding how step-up authentication compares with related security methods helps clarify when and how you should implement it.
Step-up auth vs. MFA
Step-up authentication is a subset of multi-factor authentication (MFA), with its main purpose being reduced friction during initial sign-up or log-in, without compromising security. But unlike always-on MFA, rather than front-loading all authentication to the login stage, step-up authentication allows users to access certain resources with one set of credentials while protecting other resources behind additional sets of credentials. Additional security measures are invoked only when the circumstances demand it.
Aspect | Standard MFA | Step-Up Authentication |
|---|---|---|
When It’s Applied | At initial login | During the session when triggered |
User Experience | Front-loads all authentication | Distributes authentication based on actions taken |
Security Philosophy | Same for all users at the same point in their journey | Varies based on sensitivity of task or data |
Optimization | Less optimal; may apply security unnecessarily | Stronger security where needed; doesn’t disrupt low-level actions |
Step-up auth vs. adaptive authentication
Step-up authentication and adaptive authentication both aim to enhance security by adjusting the level of authentication based on certain factors. However, they differ in their approach and scope.
Adaptive authentication, also called risk-based authentication, is another subset of MFA where additional authentication factors are automatically triggered according to contextual risk. It is a more comprehensive approach that adjusts the authentication level based on characteristics like device fingerprint, IP address, geolocation, and so on.
While step-up authentication is linked to the sensitivity of the action or resource, adaptive authentication is linked to the risk signals associated with the current session. In practice, many modern security systems combine elements of both approaches, using predefined security triggers for different actions while also considering contextual factors.
Aspect | Adaptive Authentication | Step-Up Authentication |
|---|---|---|
Scope | Broader scope encompassing various risk factors | Targeted towards specific predefined situations |
Trigger | Continuous assessment of various risk factors and contextual information | Event-specific triggers (e.g., high-risk transactions, sensitive data access) |
Implementation | Real-time decision-making based on evolving risk profile during the session | Applied in response to specific triggers |
Continuous Assessment | Continuous evaluation of risk throughout the session | Not continuously assessing risk; triggered by specific events |
Step-up authentication vs. authentication gateways
One of the key characteristics of step-up authentication is that it happens during an existing session where the user is logged in. In other words, it applies additional authentication requirements within an already authenticated session—not before, and not at initial login.
Authentication gateways, by contrast, simply require different levels of initial authentication. While both approaches involve gating access, step-up authentication specifically focuses on verifying identity within an existing session when the risk level changes.
In the image below, we’re prompted to create an account or log in in order to read the article. This is not step-up authentication, but it is an authentication gateway that prevents guest users from accessing content.
Step-up authentication vs. access control
Access controls determine what resources a user can access based on their permissions and role. While step-up authentication may be used to implement access controls, the concepts are distinct:
Access controls define what a user can do
Step-up authentication adds additional security layers when a user attempts high-risk actions
Continuing from our previous example, the image below shows what an unsubscribed user will see if they exhaust their free daily articles. The user is already logged in, but they lack the permissions to view this article because they don’t have a subscription. Although a prompt appears that blocks their access, this is not step-up authentication because they don’t need to further prove their identity. They simply need to pay for a service.
How step-up authentication works
To understand how step-up authentication works in practice, let’s look at how it functions (or doesn’t) in different environments: banking, ecommerce, and healthcare.
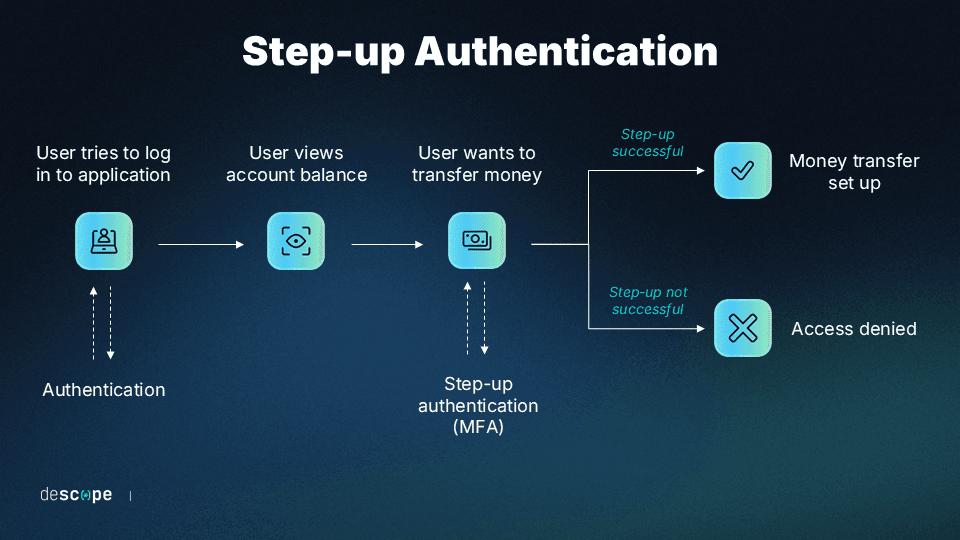
Banking and financial services
When a customer logs into their banking application, they typically enter a username and password. This initial authentication grants access to basic functions like checking balances or reviewing recent transactions.
However, when the user tries to:
Transfer money to a new recipient
Change account settings or contact information
Access investment portfolios
Request a credit limit increase
That’s a step-up trigger. The application will require an additional authentication step, like a one-time password (OTP) or a fingerprint scan with device biometrics, increasing assurance that the user really is the account owner.
Read more: Customer IAM in Banking: Considerations & Best Practices
Ecommerce and retail
Major online retailers have long since embraced step-up authentication models to balance convenient browsing with strong account protection. Amazon, the world’s largest ecommerce organization, provides an excellent example of this approach in practice.
Users can log in to their Amazon accounts with standard credentials (assuming MFA is not enabled account-wide) to browse, view orders, and make routine purchases using saved payment methods. However, when users try to access security settings—the main attack vector for completing account takeovers—Amazon triggers an additional authentication step using the customer’s contact information.
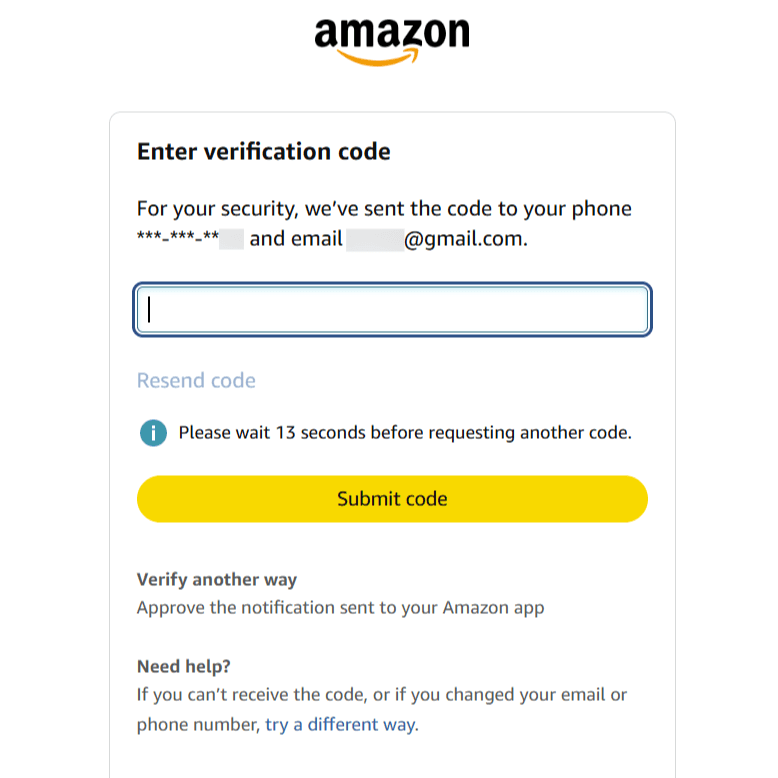
This typically involves sending a OTP via email or SMS that the user must enter to proceed with the sensitive operation. Amazon takes this protection even further by sending an email with the subject line including “Account data access attempt.” This happens whether or not the logged in session completes the MFA challenge, ensuring that the account owner knows someone (even if it was them) tried to access their Amazon security settings.
Read more: Authentication in Ecommerce: Best Methods & CIAM Tips
Healthcare and hospitals
Not all industries benefit from step-up authentication. The tightly regulated world of healthcare provides a compelling case for always-on MFA. After all, the low-risk actions a logged-in user can take in this environment are relatively few.
When to use step-up authentication
You might be tempted to say, “I’m in ecommerce, so step-up is a great fit!” But despite the cross-industry appeal of step-up authentication, it’s crucial to assess whether it would benefit you and your user base. Before fully embracing the step-up approach, developers and product owners should think about whether the following touchpoints apply to them.
When protecting sensitive data and actions
The most obvious use case for step-up auth is protecting high-risk or sensitive operations. Like in the banking and ecommerce examples above, industries that can neatly separate low-risk and high-risk activities are well-suited to step-up authentication.
How do you know if your application is a good fit for step-up authentication? Answer these key questions:
What damage could result if an unauthorized user simply logs in?
Can the most sensitive data and actions be separated from routine use?
What regulatory requirements apply to your organization?
These considerations can work in both enterprise and consumer settings. For instance, if an organization uses GitHub Enterprise, employees might be allowed to review code and create branches easily. However, they might trigger step-up flows if they attempt to change settings, add users, or push code into production.
When balancing security with user experience
Prompting users with step-up authentication in the middle of a session can lead to frustration. But if users know that specific actions are risky and can cause damage if carried out by an attacker, they will understand and even appreciate this type of authentication at the right time.
For example, if an online food delivery app performs step-up authentication every time users place an order, it’s likely to annoy and cause drop-off. However, if the app requires step-up authentication when users try to change their delivery address or credit card details, they are likely to be patient and agreeable to those flows.
Users want to browse applications with minimal friction while having peace of mind that their data and access are secure and can’t be compromised. Implementing step-up authentication at the right time can help app developers “show” users that their sensitive data is safe.
How to implement step-up auth effectively
A thoughtful step-up authentication deployment will balance both experience and security. Start by assessing your risk: where does sensitive data live, and how can it be sequestered without disrupting routine, everyday use? The following framework provides a structured way to approach implementation:
Phase | Key Motions | Best Practices |
|---|---|---|
Risk Assessment | • Map application functions by security sensitivity
• Group functions together, separating them by risk tier | • Document assessment parameters (like regulations)
• Focus on actions with significant security impact |
Selecting Authentication Methods | • Choose methods that fit your user base
• Prepare fallback methods (support tickets, backup codes, etc.) | • Not all MFA is equal; consider the security and UX impact
• Offer alternatives when possible for maximum accessibility |
User Experience Design | • Create easy-to-follow flows with direct instructions
• Educate users about step-up auth through subtle prompts | • Offer limited choices, but don’t compromise security
• Show users “what’s in it for them”; consider incentivizing with promos |
Test Implementation | • Roll out new auth changes incrementally
• Consider success rates across devices, browsers, demographics | • Auth is a sensitive touchpoint; don’t rush it
• Consider a test period of at least two weeks |
Full Deployment | • Integrate step-up auth with your production environment
• Announce the change via email, socials, etc. | • Use clear, concise messaging across all channels
• Give users advance notice to ease the change |
Monitoring & Feedback | • Track user feedback both in-app and externally
• Continuously track drop-off points and adjust as needed | • Remember that no deployment is completely flawless
• Take all feedback seriously, but only act when supported by data |
This implementation framework will set you up to create a step-up authentication experience that provides clarity, security, and a better identity journey. By carefully deploying to a subset of users, you’ll gather valuable feedback from real-world use that can contribute to your overall rollout strategy.
This helps reduce the adoption hurdles and user pushback—but, as with any change to authentication models, expect light resistance. Be ready to explain why this change is good for your end users. Ultimately, everyone will benefit from reduced fraud thanks to step-up auth focusing additional security where it matters most.
Step up your authentication with Descope
Step-up authentication proves invaluable in securing applications without compromising user experience. However, its implementation requires thoughtful consideration, including which authentication methods to use, which actions or resources to trigger the step-up flow on, and so on.
Descope can help you implement step-up authentication within your application by leveraging drag & drop workflows and SDKs. You can choose from a wide range of auth methods, create and customize user-facing screens, and deploy it in your app with a few lines of code.
Sign up for a Free Forever account to get started with Descope. Have questions about step-up authentication or our platform? Book time with our auth experts.





