Table of Contents
Understanding authentication in ecommerce
Identity management is a critical part of every modern, customer-facing organization. However, in ecommerce, effective authentication can cement strong customer relationships, prevent drop-offs, and even boost conversion rates. Leading ecommerce companies don’t stop at simply confirming user identities and preventing fraud—they leverage better authentication journeys as a competitive advantage.
In online retail, authentication serves a dual purpose: protecting sensitive customer data and ensuring a smooth, trustworthy shopping experience. When done well, it helps protect customer data (PII), ensures compliance, and turns identity into a growth driver.
Let’s break down what authentication means for ecommerce, strategies that maximize ecommerce security without harming UX, and how you can turn customer identity from a checkbox into a conversion engine.
Understanding authentication in ecommerce
Authentication in ecommerce is the process of confirming a customer's identity before granting them account access on a shopping website or application, or the ability to take certain actions like viewing payment details or making a purchase.
It’s important for ecommerce and online retail stores to confirm that the person attempting to make a purchase or access sensitive information is indeed who they claim to be. Well-implemented ecommerce authentication helps protect customer data (like personally identifiable information, or PII), prevents unauthorized access, and reduces the risk of fraud while protecting user data while maintaining compliance with data protection regulations. It’s the first line of defense in securing online transactions and is also pivotal to helping organizations stay compliant with relevant customer data protection regulations.
That said, it’s imperative for ecommerce businesses to balance security with user experience, as overly complex login processes can lead to cart abandonment and lost sales.
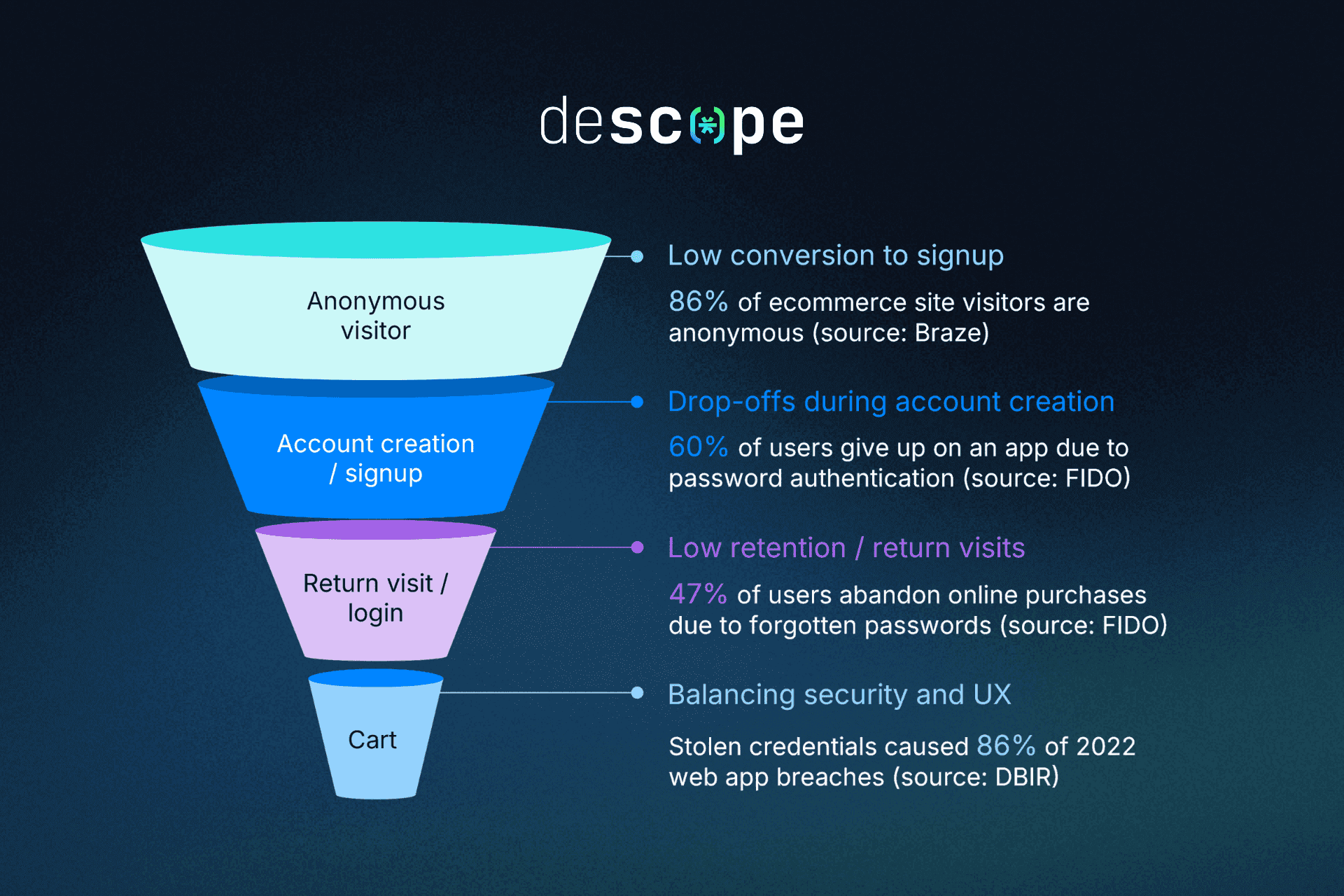
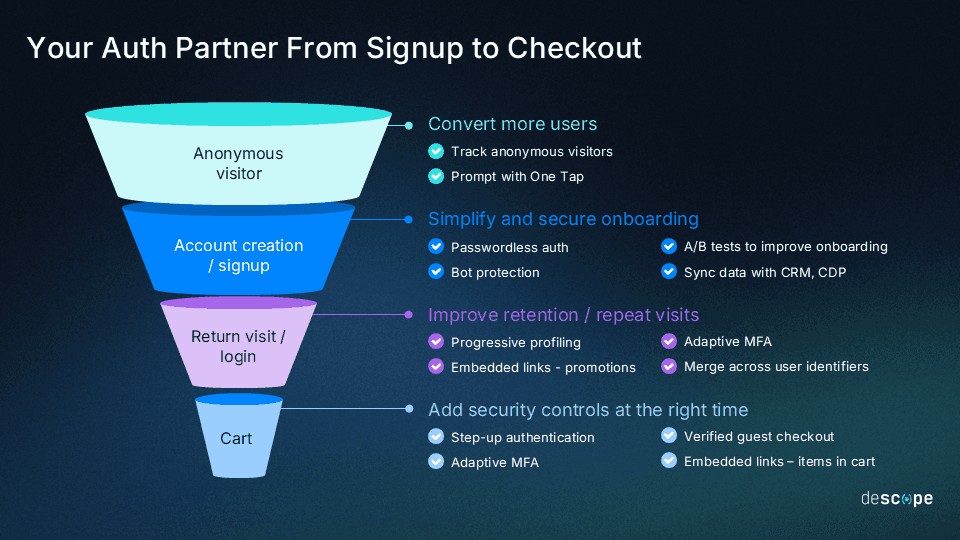
The customer authentication journey touches multiple points in the ecommerce lifecycle, and each represents both an opportunity and potential friction:
Anonymous users: Unregistered users comprise your largest growth opportunity, but it’s also your biggest conversion challenge.
Account creation and signup: Friction during account creation has a tangible impact on conversions, and drop-offs often occur if registration is too complex.
Return visits and login: Returning customers aren’t always frequent shoppers. What if they don’t remember their years-old password?
Cart and checkout: The conversion point is particularly sensitive to friction. Customers readily abandon their carts when auth issues arise.
Some of the emerging and most advanced authentication methods in ecommerce include:
Biometric authentication: Already adopted by retail giants like Amazon, passkeys use the fingerprint scanners and facial recognition built into everyday smartphones to support a stronger approach to authentication.
Adaptive multi-factor authentication (MFA): Rather than standard MFA —which can cause unnecessary friction, risk-based approaches enforce MFA only for suspicious or anomalous login attempts.
Passwordless authentication: Improving the user experience and security by eliminating passwords altogether by adopting methods like social login, magic links, or biometrics.
FIDO and public key cryptography: FIDO (Fast IDentity Online) is an open industry standard that uses public-private key pairs to create phishing-resistant login experiences.
Why customer data protection matters in ecommerce
In ecommerce, every transaction involves the exchange of sensitive information, including payment details and personally identifiable information (PII) such as names, addresses, and contact data. Safeguarding that customer information has shifted from a regulatory obligation to a core business responsibility. Studies consistently show that data breaches significantly erode customer trust, in many cases, leading users to abandon or disengage from affected brands.
The risks of compromised customer PII
When customer PII is exposed, the damage goes beyond financial loss. Breaches can trigger customer churn, regulatory penalties, and lasting damage to reputation. Attackers often target online retailers precisely because of the volume and value of customer data they store. Once breached, this data can be used for identity theft, fraudulent purchases, and large-scale credential-stuffing attacks.
In Verizon’s Data Breach Investigations Report (DBIR), stolen credentials topped the list of web app breach causes — a reminder that weak or outdated authentication methods remain one of the biggest risks for ecommerce platforms.
The importance of strong authentication in ecommerce
Authentication plays a crucial role in the ecommerce ecosystem for several reasons, impacting both the security and operability of online retail environments. Beyond simply verifying who a user is, strong authentication methods help ensure that every login, purchase, and account interaction happens securely—without introducing unnecessary friction.
As the first step in any secure transaction, authentication ensures that the person initiating a purchase or action within an ecommerce platform is the legitimate owner of the account or payment method being used. This is critical in preventing fraudulent transactions, which can lead to significant financial losses and damage to the retailer's reputation.
Moreover, many regulations, such as the General Data Protection Regulation (GDPR) in Europe and the Payment Card Industry Data Security Standard (PCI DSS), require businesses to protect customer data and ensure the security of transactions. Failure to comply can lead to legal and financial penalties.
And while security is a primary concern, authentication also plays a vital role in the customer experience. Simple, yet secure authentication processes can significantly improve the ease with which customers access and use ecommerce platforms. Ultimately reducing friction in the shopping experience, leading to higher conversion rates, customer satisfaction, and loyalty.
The FIDO Alliance’s 2024 Authentication Barometer Report reveals just how significant this impact can be: 42% of people abandoned a purchase and 56% gave up on accessing a service entirely because they forgot their password.
Webinar: Ecommerce CIAM Best Practices
Best authentication strategies in ecommerce
Having observed hundreds of CIAM implementations at Descope, here are the authentication strategies we’ve seen yield the most success in ecommerce.
Passwordless authentication methods
Passwordless authentication doesn’t rely on knowledge-based credentials, making it an excellent choice for ecommerce. It delivers both robust security and a friendlier user experience, allowing your customers to focus on your products rather than remembering a secret code.
Passwordless methods include:
Magic links: These are unique, one-time-use links sent typically to the associated email. Clicking the link logs the user instantly, eliminating the need for a password.
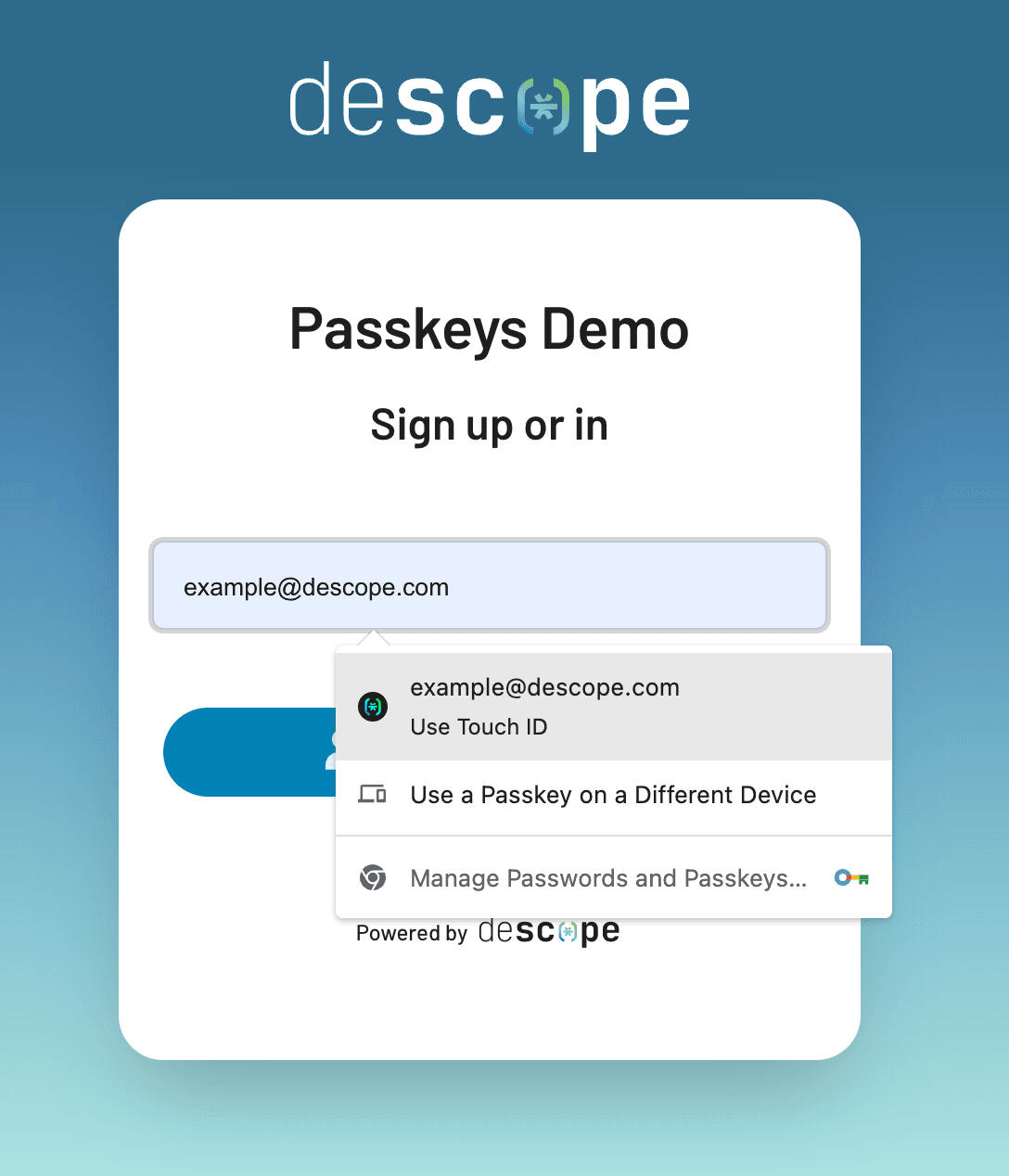
Passkeys: These FIDO-standard credentials use public key cryptography to create unphishable authentication. Adopted by tech giants like Amazon, Google, and Microsoft, passkeys are exploding in popularity for their security and ease of use. Check out this demo site to see passkeys in action.
One-time passwords (OTPs): These are random sequences of characters generated for one-time use and sent via SMS or email. Since they are valid for only a short period, they are less susceptible to cyberattacks than passwords.
WhatsApp authentication: Authenticating via messaging platforms like WhatsApp can help businesses unlock omnichannel communications with end users, provide a native experience, and protect against security attacks targeting SMS authentication.
Social login: An increasingly popular method for onboarding new customers, social allows users to select a “Log in with…” button for their preferred identity provider rather than creating a new account from scratch. While convenient, it’s best used in conjunction with a second factor for purchase confirmation.
Google One Tap: This Google-specific version of social login uses the customer’s browser for authentication. Users receive a native browser prompt which simply asks them to tap (or click) to continue with their existing Google session. Check out this demo site to see Google One Tap in action.
At every step of the customer journey, passwordless authentication can boost registrations, reduce drop-offs, and improve conversion rates. Case in point: Dashlane saw a 70% increase in conversions with passkeys, while Microsoft found that signing in with a passkey is three times faster than a traditional password and eight times faster than a password combined with standard MFA.
Plus, with passwordless, returning customers don’t need to fear forgetting their password anymore. Microsoft reports users are three times more successful signing in with passkeys than with passwords (98% versus 32%).
Gartner Buyers Guide for CIAM
Learn common CIAM use cases and recommended evaluation criteria.
Get copy
Tracking anonymous users and verified guest checkout
According to analysis by Braze, 86% of ecommerce site visitors are anonymous. For these visitors who just aren’t ready to commit to an account yet, anonymous user tracking provides a reliable, non-invasive way to start building a relationship. Without forcing them to sign up, you can create better experiences and learn how visitors naturally explore your offerings—even before they create an account.
This method uses tokens to identify users. When they’re ready to become a registered customer, the token associated with their “anonymous” identity is merged into the new account. They’ll retain all the custom data you choose: browsing history, preferences, geographical region, and much more.
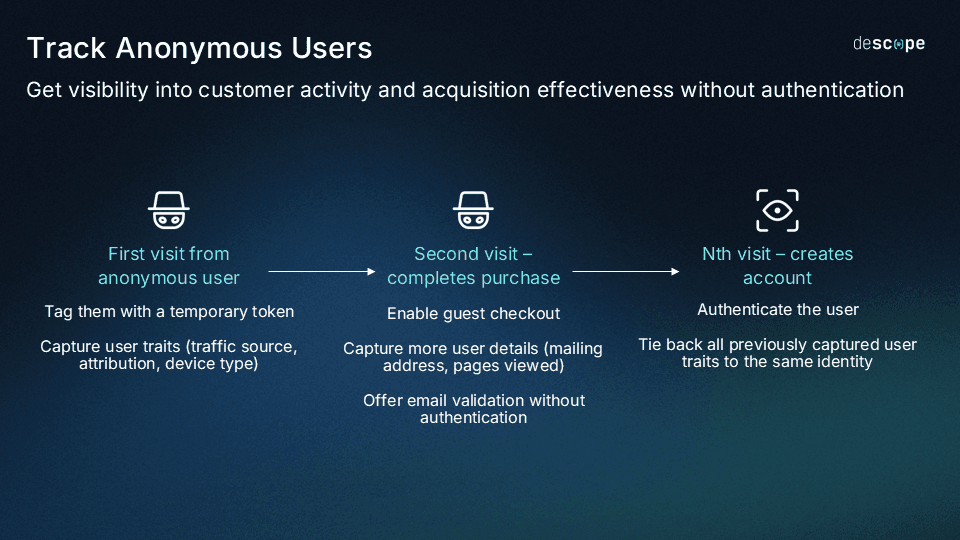
Verified guest checkout offers another way to lower barriers and reduce cart abandonment. Instead of forcing users into full account creation, this approach collects only the essentials—limited info necessary for shipping and payment—while maintaining a low-friction user experience. Combined with anonymous user tracking, this allows unregistered users to create a purchase history and incorporate it into their full account later. Learn how: Boost Conversions With Anonymous Users and Guest Checkout
These approaches not only improve UX but also strengthen customer data protection by minimizing unnecessary data collection during these early interactions.
Adaptive multi-factor authentication (MFA)
Multi-factor authentication, which includes 2FA (two-factor authentication), prompts users to provide a second factor when logging in or taking a sensitive action, like making a purchase. The factors of authentication include knowledge (something you know), inherence (something you are), and possession (something you have). The most common form of MFA is a password (knowledge) combined with a one-time password (OTP) sent to a device the user owns (possession).
Standard MFA implementations greatly enhance security by adding another layer of protection, but it often occurs at the cost of user experience. Passkeys resolve this issue by incorporating both factors involved in one action, like unlocking a smartphone (possession) with a fingerprint scan (inherence). However, more traditional MFA combinations can introduce unwanted friction for legitimate users rather than blocking threat actors.
Adaptive MFA addresses this friction by intelligently applying security based on context. Rather than requiring extra verification for every action, adaptive MFA assesses risk signals like device fingerprint, IP address, and geolocation to determine when additional authentication is necessary. Unlike standard MFA, adaptive authentication provides smooth sailing for legitimate customers, and it applies right-sized friction when the context demands it.
Other implementation considerations
Ultimately, the goal is to implement a secure, scalable, and user-friendly authentication system that aligns with your business objectives, regulatory requirements, and evolving cybersecurity threats and consumer expectations. Which means you need a customer IAM platform that grows alongside them.
As far as the chosen authentication methods go, you need to consider their integration with your existing tech stack and whether they are compatible and scalable to support business growth and maintain performance during peak periods.
Here are some other aspects to consider for frictionless and secure customer identity management:
Step-up authentication: This approach requests an additional authentication factor from the user before performing a sensitive action (e.g. making a high-value purchase). While adaptive MFA only kicks in when certain risk signals raise red flags, step-up authentication always takes effect if the user attempts certain actions. Step-up auth can greatly reduce the impact of account takeover and provide a visible sense of security to end users at the right time in their journey.
Progressive profiling: Long registration forms and lots of upfront user collection can harm your site’s adoption and conversion. In fact, Capterra research found that 82% of consumers have backed out of an online purchase because creating an account was too complicated. Ecommerce organizations should consider progressive profiling—an approach that “gets users in” quickly with minimal information and collects incremental data during future visits when users are more willing to part with those details.
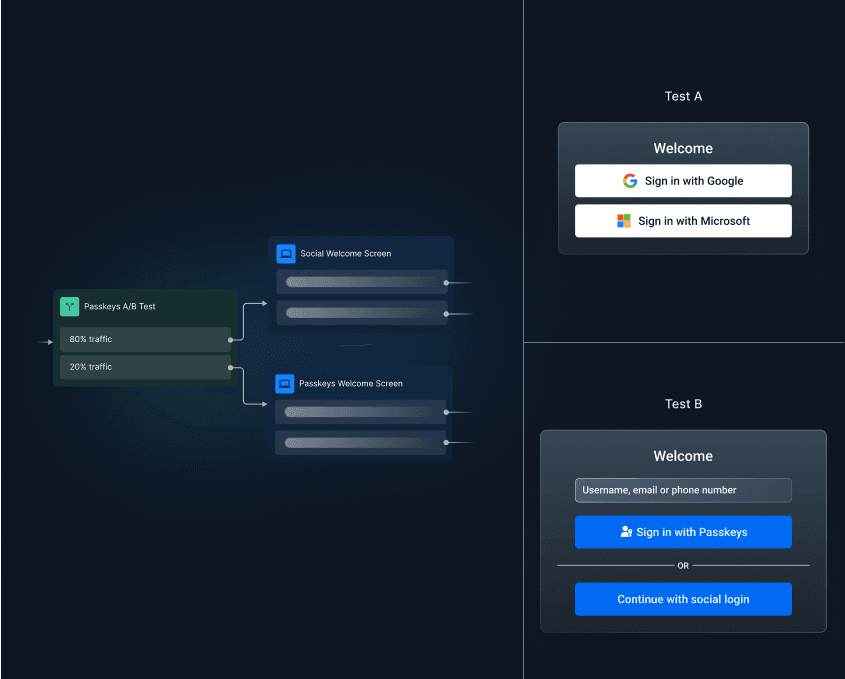
A/B testing: The success and continued growth of ecommerce companies is based on rapid adaptation and experimentation. Authentication flows are no exception—small changes to login experiences can drive profound improvements in conversion and retention while decreasing drop-offs. By A/B testing different authentication flows, messaging, or methods, you can optimize for actual user behavior rather than assumptions.
Cross-device and cross-brand authentication: As customers interact with brands across multiple touchpoints, like websites, mobile apps, and sub-brands, providing a consistent auth experience becomes increasingly important. Single sign-on (SSO) allows customers to use one set of credentials across an ecommerce brand’s entire lineup of digital properties, reducing repeated logins and increasing cross-selling opportunities.
Native mobile authentication: The typical flow for app-based authentication using modern methods involves redirects—abrupt, jarring transitions from the actual storefront to an authentication interface. Native mobile authentication avoids disruptive browser interruptions that can cause users to become confused. At the same time, it ensures continuity with your brand look and feel by maintaining a consistent experience.
Platform integrations: Many ecommerce businesses rely on platforms like WordPress, Shopify, or Salesforce Commerce Cloud (CC) to host their storefront and process customer transactions. While these platforms offer basic authentication options, augmenting them by connecting to a purpose-built authentication solution can provide passwordless options, MFA, SSO, and more.
Simple & effective ecommerce authentication with Descope
Every ecommerce transaction is a data exchange, making secure authentication the foundation of customer trust and business growth. The quality of that authentication now separates smooth, scalable experiences from broken logins and lost customers.
The Descope CIAM platform is designed to meet ecommerce demands with drag & drop simplicity. Descope Flows, our workflow-based identity flow editor, makes it easy to add cutting-edge authentication technologies—from passkeys and Google One Tap to magic links and nOTP Whatsapp authentication—which provides a developer-friendly interface for building robust security with maximum user convenience.
Descope’s comprehensive integration capabilities ensure customer identity flows seamlessly between your authentication system and business tools like CRM, CDP, and ecommerce hosting platform. This creates a more cohesive, unified view of your customer journey across all touchpoints while lowering friction and simplifying checkout.
Sign up for a Free Forever account with Descope and drag and drop your ecommerce customer journey flows. Have questions about our platform? Book time with our auth experts.