Table of Contents
Google One Tap 101
Hello Descopers! We’re happy to announce that you can now add Google One Tap authentication to your apps using Descope SDKs. Using Flows, you can also run post-authentication user journeys such as verifying additional auth factors, calling actions from third-party connectors, and collecting more user information.
Customers can use Google One Tap to increase user sign-ups and retention, avoid the burden of credential management and storage, and provide a frictionless and unified auth experience across desktop and mobile web.
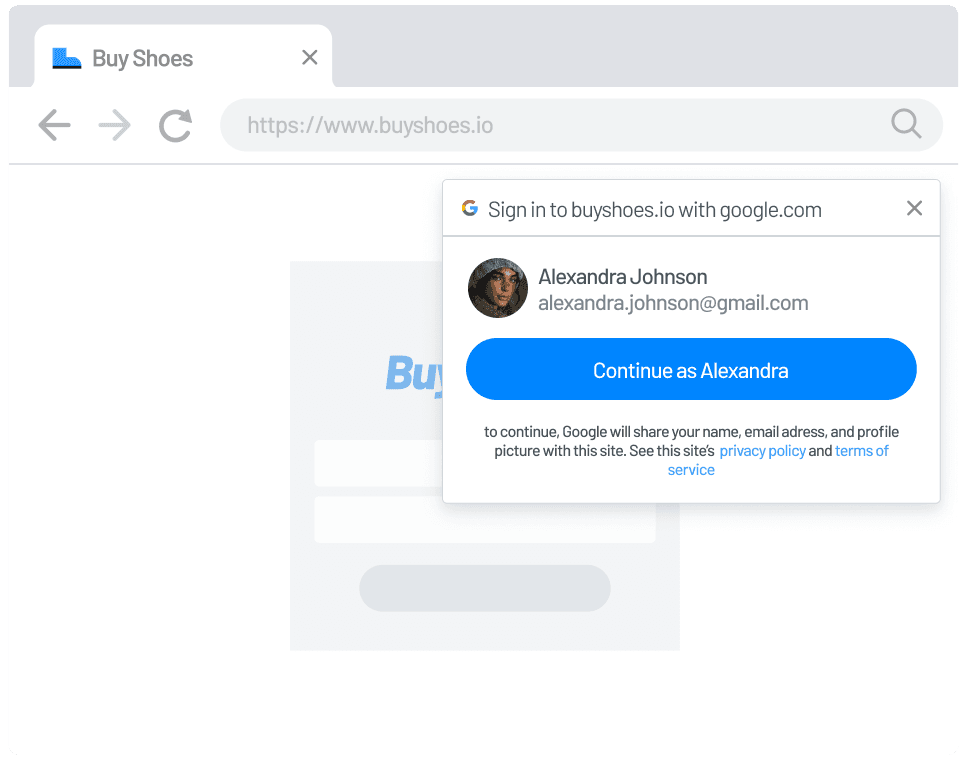
You can start implementing One Tap by reading our documentation. Want to experience One Tap for yourself? Check out this demo site.
To learn more about the benefits of One Tap, how to implement it with Descope, and running post-authentication flows, keep on reading.
Google One Tap 101
Google One Tap operates on the same principle of federated authentication that the existing OAuth option of “Sign up with Google” does. While social logins are popular themselves, One Tap is an improvement that identifies the user’s logged in browser or Gmail session and provides an active nudge to the user prompting them to sign up / in with their Google account.
While the earlier implementation of One Tap relied on third-party cookies, Descope supports the more modern approach based on FedCM.
A primer on FedCM
The Federated Credential Management (FedCM) API was created by a World Wide Web Consortium (W3C) working group to provide a privacy-preserving alternative to federated authentication on the Internet.
The fundamentals of FedCM are the same as any federation protocol – a Relying Party (RP) relies on an Identity Provider (IdP) to confirm the user’s identity. However, instead of relying on redirects, iframes, or cookies, FedCM imbues the browser with much more responsibility in the identity confirmation process.
With FedCM, the browser is able to:
Show native UI elements on the RP (your app or website)
Ask users to choose which Google account to use for login
Collect information from the IdP (Google) to populate the UI without the RP knowing anything about the user’s identity before they consent
While the future of third-party cookies continues swinging this way and that, implementing One Tap with FedCM ensures your app is in the best shape either way.
Benefits and success stories
Here are some ways One Tap improves the user journey:
It reduces the number of anonymous users by providing them active, low-friction prompts to sign up and see the full value of your app.
It’s fast and seamless, eliminating an entire screen compared to the traditional OAuth signup process of asking the user which Google account to use.
It greatly improves conversion and retention by reducing users’ cognitive load to almost zero. No new passwords to create or remember and no onerous login forms – just one tap.
It provides a consistent and unified experience. Whether users are on their desktop or mobile browser, One Tap works exactly the same. It’s also supported on most popular browsers like Chrome, Edge, Firefox, and Safari.
Companies that have implemented One Tap in-house have seen stellar results:
Reddit increased overall signups by 90%, with One Tap also driving a 100% increase in sign-ins on mobile web.
The News Minute saw immediate impact as signups increased by a whopping 833% in the first 90 days after implementing One Tap.
Pinterest observed a 47% jump in overall signups and an impressive 126% increase in signups on Android.

Google One Tap with Descope
To implement Google One Tap in your app with Descope, all you need to do is:
Configure your Google Provider in the Descope Console with the implicit grant type enabled, as shown here.
Add the One Tap component to your app through Descope frontend SDKs, as shown here.
That’s seriously it. If a few lines of code can 10x your user conversion, what’s not to like?
Post-auth user journeys
While One Tap is implemented through Descope SDKs, you can use the power of Descope Flows to run a number of custom user journey actions after the user has been authenticated by One Tap.
Phone verification: You can verify the user’s phone number, tie it to their identity, and use it in cases of MFA or account recovery.
Progressive profiling: You can collect custom information from the user and use it to both provide a personalized experience and lead them down the funnel (e.g. work email, job role).
Identity orchestration: You can run actions and weave in data from any of our 50+ third -party connectors, such as collecting risk scores from reCAPTCHA, updating the user record in HubSpot, or track user actions in Amplitude.
For example, the Flow below first checks if the user’s phone number already exists as part of their identity record. If it does, the user is signed in with an OTP, and if it doesn’t, the user’s phone number is collected, followed by OTP authentication.
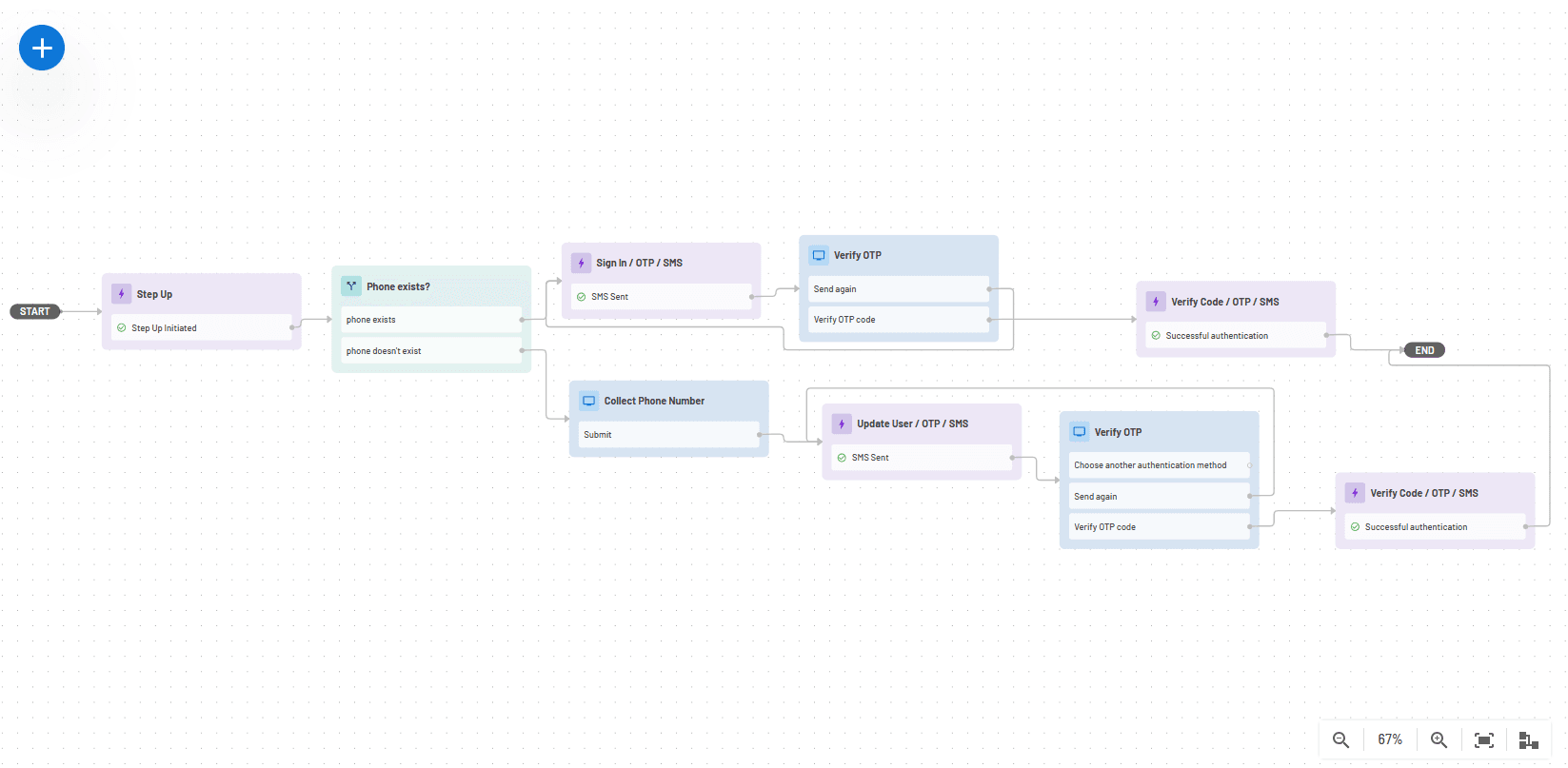
Using One Tap in conjunction with Flows gives your users a delightful login experience while also enabling you to run the business logic you need to effectively manage and secure identities across the user journey.
Conclusion
We hope you’re raring to add One Tap to your app after reading this blog! As a reminder, here are the docs to get started after you create a Free Forever account. If you run into any issues, head over to AuthTown where the #ask-a-descoper channel is forever online!