Table of Contents
What is authorization?
In today’s digitally connected age, managing who has access to what is both a technical and business necessity. Whether you're a startup or an enterprise, understanding and implementing the right authorization mechanisms is vital to the sustainable growth of your company.
Let’s learn how authorization works, the common models at play, and what challenges you might run into.
What is authorization?
Authorization in cybersecurity refers to the process of granting or denying access to resources based on the identity and permission level of a user or device (collectively referred to as an entity).
The authorization process implements access controls that determine the exact activities an entity is allowed to execute on a specific resource. Authorization may be granted to entities on a case-by-case basis or according to a predetermined model, such as role-based access control, which we’ll unwrap soon.
Authorization is a crucial component of cybersecurity, strengthening confidentiality, integrity, and availability of data and resources within an IT environment. It ensures that only authorized users may access and perform operations on them. It protects your company's sensitive information from unauthorized access, whether due to internal mistakes or external attacks. Properly set authorization can contain the damage by limiting entities to the least amount of data necessary to perform a job.
For example, Jane is an employee at XYZ Corporation. She logs into the company's document management system. Once logged in, Jane has access to edit and create documents in the Sales folder because she is part of the sales team. However, she cannot access the HR folder as she doesn't have the necessary permissions.
This control keeps sensitive information secure and ensures employees can only access data relevant to their role.
Authorization vs. authentication
Authorization works in tandem with authentication. Before a user is authorized access, they must first confirm their identity via the chosen authentication method, such as username and password, social login, biometrics, etc.
To understand the distinction between authorization and authentication, consider an example of exercising the right to vote vs. voter registration:
Completing the voter registration process authenticates an individual i.e., validates their identity and confirms voting eligibility.
Registered voters are authorized to vote at polling stations. Depending on criteria such as political party affiliation or location, some voters may hold additional authorizations, such as primary or mail-in voting.
| Authentication | Authorization |
|---|---|---|
Definition | Verifying the identity of a user, system, or process. | Granting or denying access to resources based on the authenticated user's permissions. |
Purpose | Confirming the user is who they claim to be. | Determining what actions or resources a user is allowed to access. |
Focus | Identity verification. | Access control. |
Process | Usually involves verifying credentials (e.g., username/password, biometrics). | Involves checking if the authenticated user has the necessary permissions for the requested action/resource. |
Goal | Ensuring only authorized users gain access. | Restricting access to specific functionalities or data based on permissions. |
Examples | Logging into an email account with a username and password. | A user with 'admin' privileges being able to configure system settings. |
Learn more: Authentication vs Authorization
How does authorization work?
As mentioned, authorization grants or denies access based on the user's permission level. For example, an employee may have read-only access to specific files, while a manager may have read-write access.
Authorization is typically managed by an access control system, which enforces the organization’s policies and rules.
Here’s a step-by-step overview of how authorization works:
Initial authentication: First, users must confirm their identities, typically by entering a username and password (note: other better methods exist!).
Authorization request: Once the user is authenticated, they can request access to a particular resource. This request includes user details like username, and relevant attributes like role or group affiliation.
Access control evaluation: The access control system receives the authorization request and checks whether the user can access the requested resource. This typically involves checking policies or rules defining who can access resources under what conditions.
Authorization decision: Based on the access control policies, the system makes a decision, either granting or denying the user's request. If the user is granted permission, they can access the resource. If access is denied, the user is informed that they do not have permission to access the resource.
Activity logging: Following the authorization decision, the system records all relevant information, such as the time of access, the user's identity, and activity. This information can be used for auditing and compliance purposes and for detecting and investigating security incidents.
Revoking permissions: Access permissions can be withdrawn at any time, either automatically (based on predefined policies) or manually (by an administrator). When access is revoked, the user can no longer access the resource. Their activities are then logged for auditing and investigation.
B2B Enterprise Readiness Checklist
Score your tech stack on enterprise readiness pillars - from dev and IT experience to security and architecture.
Download
Types of authorization
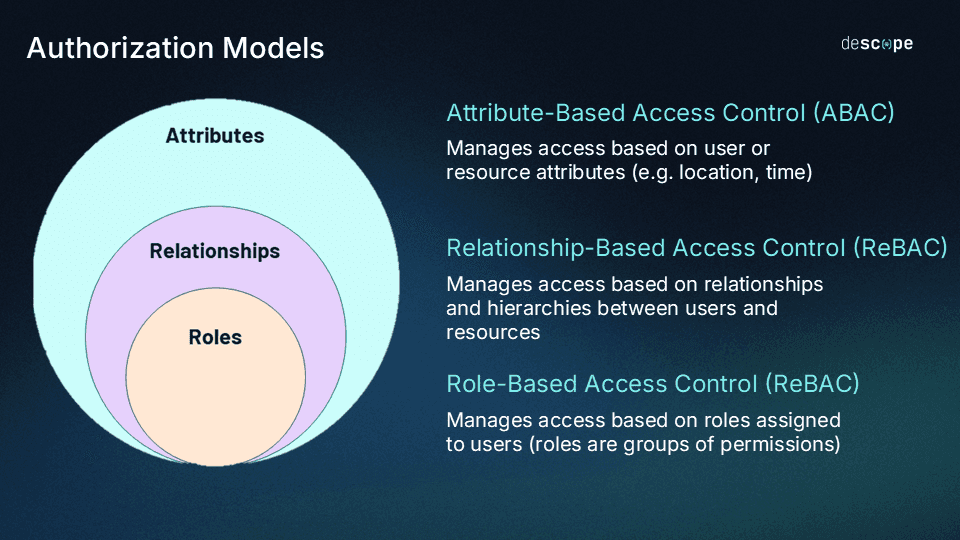
Authorization may be granted based on various criteria or access control models. The three main models used are:
Role-based
Relationship-based
Attribute-based
Attribute-based models are the broadest way to grant authorization since anything can theoretically be considered an attribute. Roles can be viewed as a subset of attributes, and relationships fall somewhere in between.
Standard models used to govern authorizations include the following:
Role-Based Access Control (RBAC)
RBAC is a method of authorization that assigns users to specific roles based on their job responsibilities. Each role has a set of permissions that determine what actions the user can perform.
For example, a bookkeeper in an accounting department may have read-only access to financial reports, while a senior accountant may have read-write access.
Attribute-Based Access Control (ABAC)
ABAC determines user authorizations by the attributes associated with their identity or account. These attributes may include their job title (as with RBAC) but also other factors such as location, department, team lead, shift, current projects, etc.
As a result, ABAC is more granular than RBAC, allowing for more precise control over user access.
Learn more: RBAC vs. ABAC: What’s the Difference?
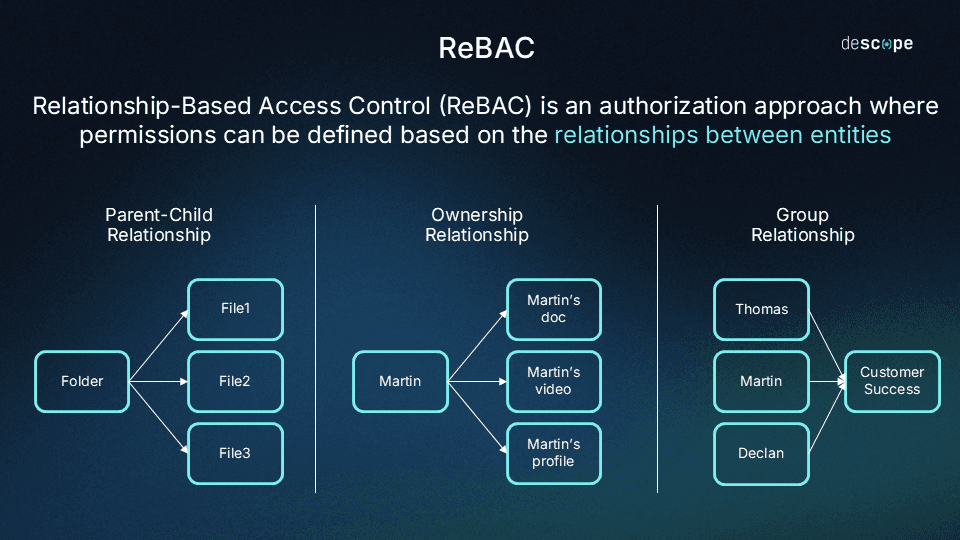
Relationship-Based Access Control (ReBAC)
ReBAC determines authorization based on relationships between resources and identities (or users). Some of these relationships include:
Data ownership: For example, after you create a post on LinkedIn, you can edit and delete it. However, you can't edit or delete the posts of others. You have these permissions for the posts you create since you are the "owner" of these posts.
Parent-child relationships: For example, if you have "edit" permissions for a folder, you automatically have "edit" permissions on all the files within that folder, since the folder and files have a parent-child hierarchy.
User groups: Rather than individually assigning permissions to roles, you can club users into groups and assign permissions en masse to a group. This approach avoids ballooning roles with individual permissions as organizations grow in size.
Learn more: RBAC vs ReBAC: Which Is Right for You?
Other access control models
Apart from RBAC, ReBAC, and ABAC, it's worth knowing a few other access control models:
Mandatory Access Control (MAC): MAC is an authorization model that relies on security attributes to restrict data access based on its sensitivity.
Discretionary Access Control (DAC): The opposite of MAC, DAC leaves authorization decisions to individual discretion. The resource owner most commonly has the deciding vote.
AuthZ use cases and examples
Here are some real-world scenarios demonstrating AuthZ in practice and the importance of proper management:
Authorization in operating systems: Operating systems often restrict access to sensitive files and settings. For example, a user may be required to enter an administrator password to install software or modify system settings.
Authorization in web applications: Web applications use authorization to restrict access to certain pages or features. For example, a user may need to be logged in and have a certain level of permission to view customer data or place an order.
Authorization in databases: Databases use authorization to restrict access to sensitive data. For example, a user may only be able to view data from a specific table or have read-only access to certain fields.
Authorization in cloud environments: Cloud environments use authorization to restrict access to virtual machines (VM), storage, and other resources. For instance, a user may be assigned the "VM Operator" role, which allows them to start, stop, and restart VMs. Another user may be assigned the "VM Administrator" role, which grants them complete control over the VMs.
Authorization in IoT devices: Authorization is a critical mechanism used to secure and control access to sensitive settings or data on connected devices. For example, a smart home device such as a security camera may require users to enter a password or authenticate with other credentials before they can connect to it remotely.
Common authorization challenges
Common challenges organizations face with authorization include the following:
Lack of understanding: Authorization depends on complex models that require active management. If organizations do not understand these complexities, misconfigurations, security vulnerabilities, and improperly provisioned or unrevoked authorizations (i.e., “permission bloat”) can quickly occur.
Weak authentication: Weak passwords and inadequate authentication methods can make it easy for attackers to bypass authorization controls and further infiltrate the environment.
Insufficient monitoring: Organizations remain in flux, with users joining, progressing through, and departing, among other changes. Over time, monitoring authorizations can become increasingly challenging. Organizations will struggle to detect unauthorized access or changes to authorization settings without the correct monitoring settings.
Human error: Humans maintain responsibility over security configurations and, in some cases, data entry. Errors can cause unintentional misconfigurations, data leaks, or incorrect provisioning.
Choosing the best authorization approach for your organization
When deploying authorization within your systems, it’s essential to choose the right model that aligns with your security needs, business scale, and operational complexity. There are primarily three approaches to consider:
Coarse-Grained Authorization: This approach provides a high-level control mechanism. It’s typically easier to implement and manage. Access is often based on predefined roles or groups within the organization, making it suitable for smaller companies or less complex systems where broad access levels are sufficient.
Fine-Grained Authorization: Here, control is much more detailed. Access can be tailored to the individual level, allowing for specific permissions to be granted for particular resources or actions. Descope champions this model as it caters to dynamic and large-scale environments, offering granular control and the ability to fine-tune access policies to reflect intricate business rules and compliance requirements.
Hybrid Authorization: A combination of both, this approach balances ease of management with tailored access. It might involve setting coarse-grained roles with some fine-grained rules for sensitive operations, providing flexibility and control where needed.
When deciding on the best authorization model for your organization, take into consideration factors such as:
Sensitivity of controlled data
Necessity of compliance with regulations
Complexity of user roles within your system
Potential need for scalability
Fine-grained authorization, as provided by Descope, is often the go-to for organizations that require robust access control without sacrificing the adaptability needed to respond to evolving business needs.
Criteria | Fine-Grained Authorization | Coarse-Grained Authorization |
|---|---|---|
Granularity | Offers a high level of granularity, allowing for precise control over individual actions or data elements. | Provides a broader, more generalized control, often based on roles or high-level permissions. |
Use Cases | Ideal for scenarios requiring detailed control, such as financial transactions, healthcare records, or intellectual property access. | Suited for situations where simplicity and efficiency are prioritized, such as general employee access levels or public-facing information. |
Flexibility | Offers a high degree of flexibility in defining specific access rights for different users or roles. | Provides less flexibility as permissions are predefined based on roles, limiting customization for individual users. |
User Experience | Offers a more tailored user experience with users having precisely the permissions they need for their roles. | Provides a simplified user experience by grouping users into roles, reducing the need for individual permission management. |
Security | Enhances security by limiting access to only necessary actions or data, reducing the risk of unauthorized activities. | Maintains security through predefined roles but may have a slightly higher risk of over-permissioned users. |
Fine-grained authorization with Descope
Adding authorization to a B2B app can be complex and time-consuming. Thinking about tenants, roles, relationships, and permissions diverts developers from other business-critical initiatives.
Moreover, before authorization comes authentication, which can also prove to be a laborious process to handle in-house. Not to mention, making mistakes with authentication and authorization can have grave consequences.
Descope helps developers build secure, frictionless authentication and user journeys for their apps. Descope’s drag-and-drop workflows, SDKs, and APIs abstract away the complexity of authentication so developers can spend time building their core product. B2B app builders can also use Descope to add RBAC and ReBAC to their app easily.
Sign up for a "Free Forever" Descope account to get started, or schedule time with our auth experts if you have any questions.




