Flexible, secure, enterprise-grade B2B CIAM
Configure SAML / OIDC SSO with a no-code visual editor.
Add fine-grained authorization (RBAC and ReBAC) to your app.
Save time for tenant admins with self-serve SSO / SCIM setup.
Add risk-based MFA and step-up auth to secure user journeys.
From scratch to SSO in 10 minutes
Enterprise SSO, SAML and OIDC support, self-service setup, testing, attribute and group mapping, multiple IdPs per tenant...there's no SSO box we don't check.
B2B CIAM built with enterprise readiness
B2B SSO and IAM
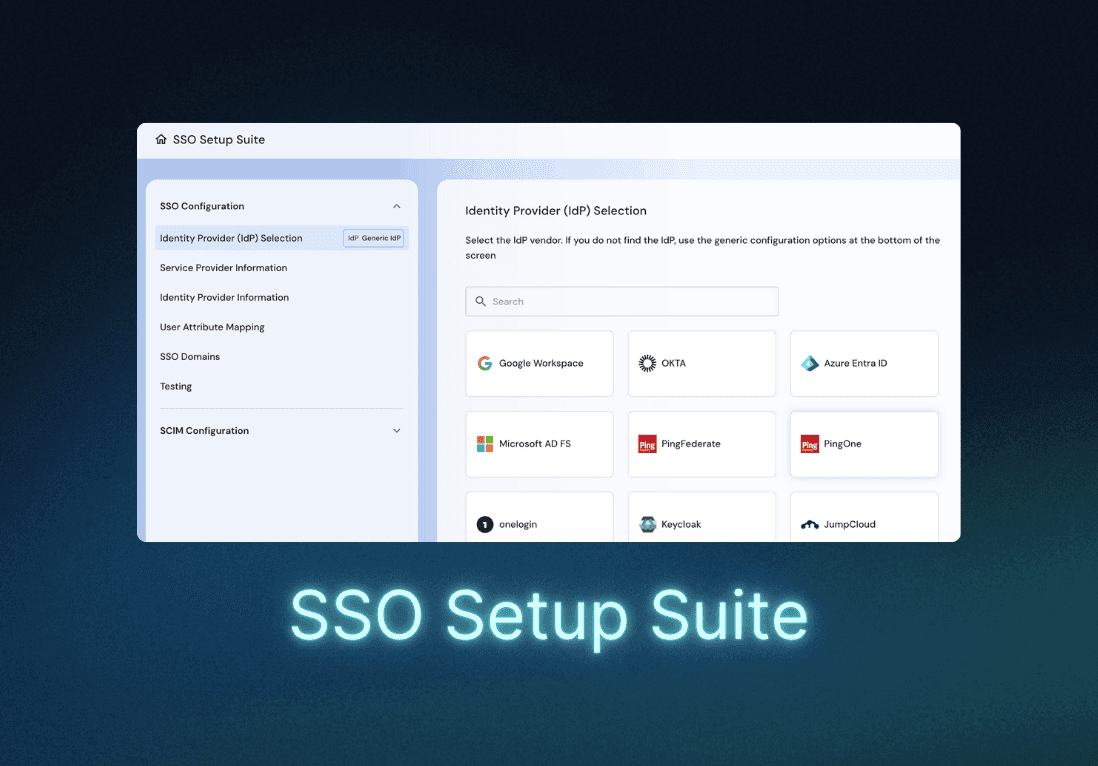
Add every flavor of external SSO
Easily support SAML and OIDC single sign-on for your app.
Add SSO for third-party and hosted apps by using Descope as an OIDC Provider.
Support customer orgs. that need multiple IdPs per tenant.
Use Descope as both IdP and SP, sometimes in the same flow.
SSO Setup Suite
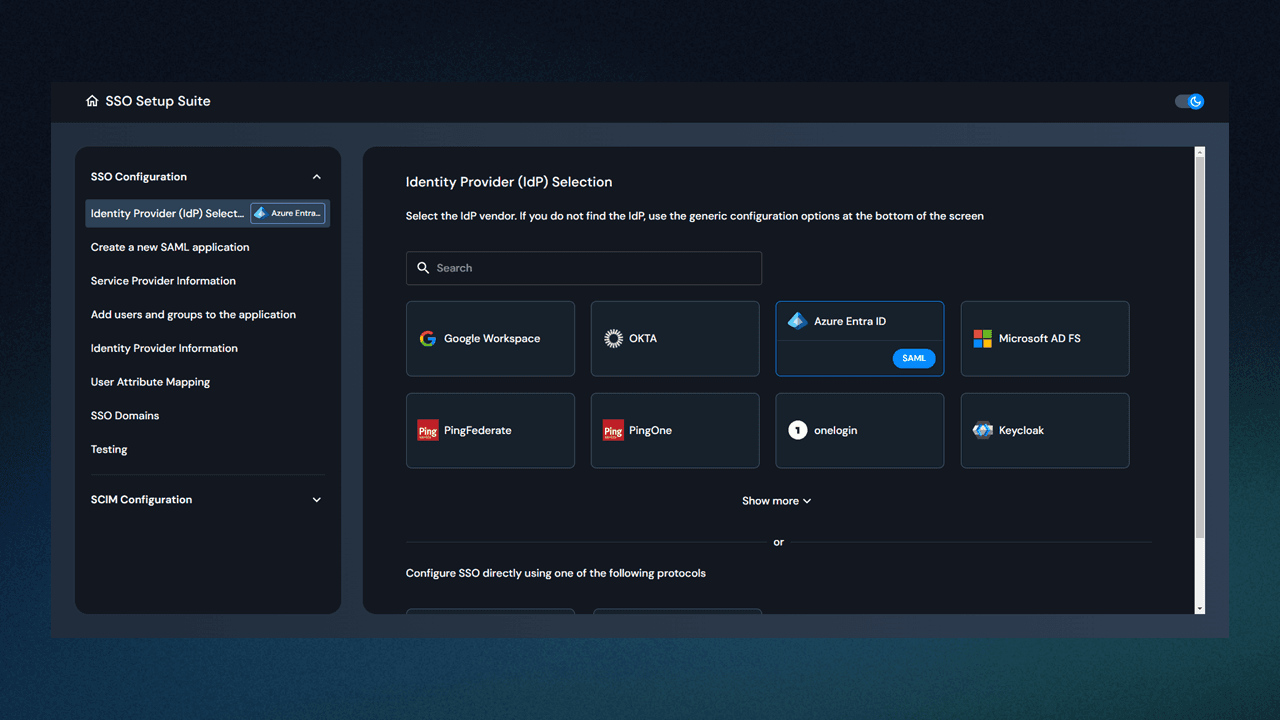
B2B CIAM that turns admins into SSO superheroes
Generate self-service SSO and SCIM setup portals for each tenant.
Use prebuilt guides for 15+ IdPs with attribute and group mapping.
Let customer admins set up, manage, and test SSO connections entirely on their own.
Force domain verification through DNS checks for additional security and control.
Seamlessly migrate existing SSO connections with zero downtime.
Widgets
Delegate identity management to your customers
Embed UI widgets in your app with a few lines of code.
Customize the layout, fields, and styling of widgets to suit your business needs.
Empower tenant admins to manage their own roles, users, access keys, audits, and more.

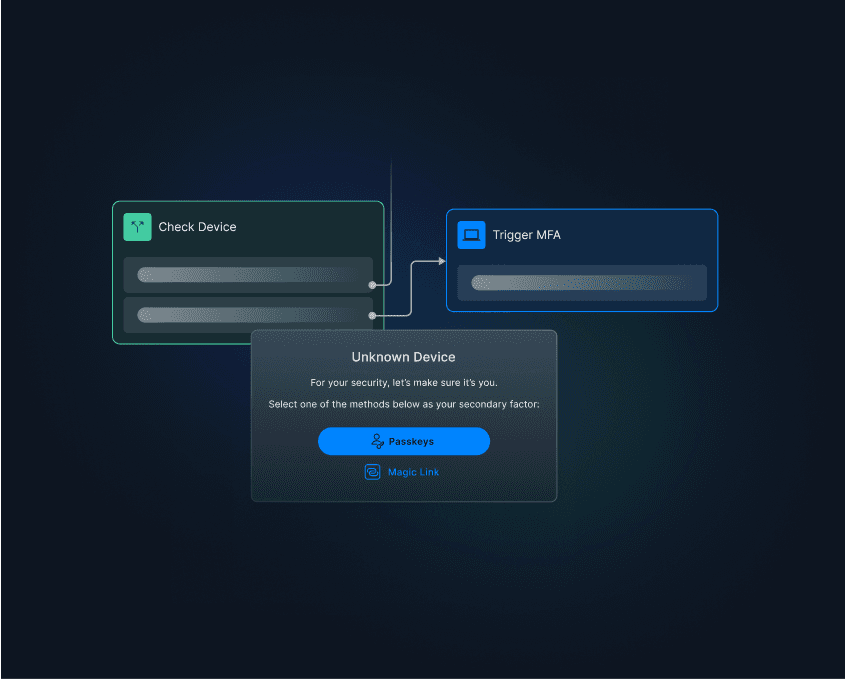
ATO Prevention
Security minus friction
Add adaptive MFA for suspicious logins without impacting real users.
Adopt user-friendly and secure MFA methods like magic links and passkeys.
Leverage native risk signals like new / trusted devices, impossible traveler, and VPN checks.
Utilize risk signals from connectors with AbuseIPDB, reCAPTCHA, Forter, Fingerprint, and many others.
Your guide to moving upmarket
As your product scales, so do the expectations: SSO, SCIM, uptime SLAs, audit trails. Get the checklist B2B SaaS apps need to meet to sell to enterprises.
Download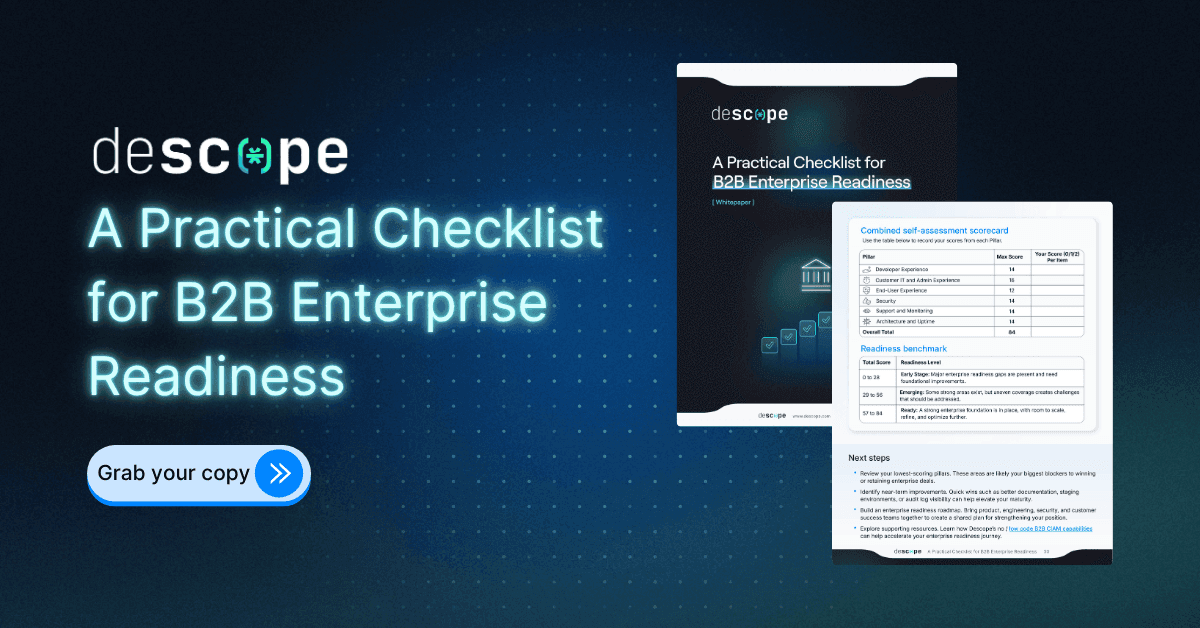
We play well with others
Enrich and secure your user journeys with third-party connectors. Go passwordless without changing your primary IdP using OIDC federated authentication.
More B2B CIAM resources
Auth that meets devs where they are
Code as much (or little) as you want. Your choice: no-code workflows, SDKs / APIs, and everything in between.
Descope SDKs
“I’ll build the authentication screens and flows, but may need help with session management.”
Explore SDKsReady for liftoff?
If you’ve seen all you need to see, sign up and get started with Descope. If you'd like a demo, meet with our auth experts.







































