Table of Contents
What is broken authentication?
One of the largest security incidents in history, the Equifax 2017 breach, exposed the sensitive data of 147 people. Here’s the surprising part: much of the attack was far from sophisticated. One critical failure was the company using “admin” as both the username and password to protect a portal containing personal information.
This kind of security gap is what is commonly referred to as broken authentication—when an attacker uses exploits that could have been prevented by following security best practices. Ultimately, the goal of any organization charged with protecting user data should be to eliminate these gaps.
This guide will help you understand broken authentication: what it is, why it’s flawed, and how attackers can exploit it. Most importantly, we’ll show you how to avoid the same critical mistakes that lead to breaches that make headlines.
Main points
Authentication breakdowns: Weak credential management and flawed session controls create exploitable vulnerabilities in seemingly secure systems
Attack patterns in real life: Understand the real-world techniques criminals use, from automated credential stuffing that leverages millions of stolen passwords to session hijacking that steals active logins
Modern defenses and tactics: Learn which authentication methods actually prevent breaches, including passwordless solutions, adaptive authentication, and airtight session management.
What is broken authentication?
Authentication is the process of verifying the identity of a legitimate user or entity requesting access to a system or application. Broken authentication is the inverse: when a threat actor takes advantage of preventable vulnerabilities to gain unauthorized access.
Think of authentication as your digital bouncer. When they’re not checking IDs against the guest list properly, anyone can slip through the door. And while an extra face at your house party might seem innocuous, the consequences of uninvited guests exfiltrating user data can be costly. Equifax paid hundreds of millions in settlements, and their reputation is still recovering. And even startups can feel the heat when their users’ credentials are spotted for sale on the dark web.
A successful broken authentication attack can provide cybercriminals with access to:
Sensitive personally identifiable information (PII)
Confidential and proprietary information
Administrative account passwords and access privileges
Financial data and access to bank accounts
The potential impact on an organization can be significant, depending on the type of account compromised or the extent of the broken authentication attack. As an organization handling end-user data, you know that you’re legally and financially liable for misfires.
That’s why it’s absolutely vital to understand one of the biggest attack vectors exploited in broken authentication: session management.
Broken authentication and session management
Session management is the process of securely handling user interactions after logging in. Here’s how a typical session works:
User logs in and gets a unique session ID
The session ID acts as a temporary pass, proving successful authentication
User navigates without re-entering credentials
Session expires after logout or a set period
When session management fails, vulnerabilities emerge that enable session hijacking. What this means is that attackers who compromise sessions can impersonate users without ever needing their password.
Frequent causes of broken authentication
Authentication vulnerabilities typically originate from critical (but often unintentional) oversights in system design, implementation, and security hygiene.
Weak or default credentials fail to enforce strong password policies or leave default credentials unchanged, allowing attackers to guess passwords easily. Using a connector like Have I Been Pwned to block already-breached passwords can help, but password reuse is common and tough to prevent.
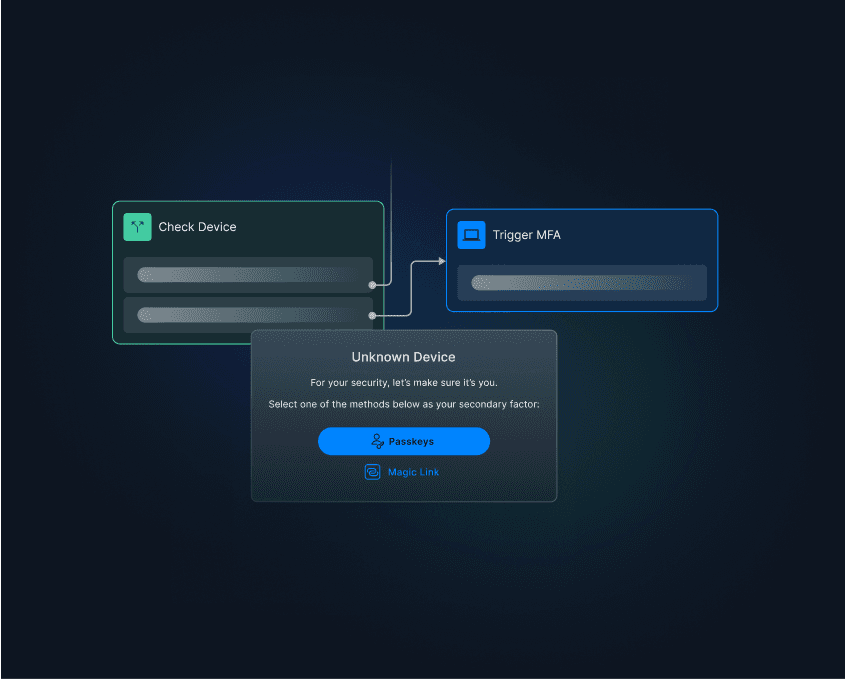
No multi-factor authentication (MFA) means threat actors only need to defeat one layer of security, typically passwords. Relying solely on password-based auth lets attackers through the door with a single credential, which can be phished, bought on the dark web, brute forced, or even guessed.
Poor session management creates opportunities for session hijacking. This includes session IDs exposed in the URL, sessions that never expire, or IDs that remain valid after logout. Each of these creates opportunities for session hijacking, potentially leading to unauthorized access.
Insufficient protection against automated attacks can take many forms: no rate limiting or account lockout policies can allow attackers to perform brute-force and credential stuffing attacks without restriction. A lack of bot or IP reputation detection opens the door to automated traffic, much of which is malicious.
Insecure password recovery processes involve gaps like weak security questions, unverified password reset emails, or predictable reset links. These create alternate paths for attackers to gain access without actually knowing the original passwords.
Plaintext or improperly hashed passwords pose a serious cybersecurity risk. Storing passwords without strong encryption and salting makes them immediately accessible if the database is ever compromised. That means attackers can not only access every user account on the breached system, but also every other account using the same credentials.
Common broken authentication attacks
Considering the vast majority of broken authentication vulnerabilities and their prevalence across business applications, cybercriminals tend to exploit them at every possible opportunity. Examples of broken authentication attacks include:
Brute force attack
When deploying a brute force attack, an attacker repeatedly attempts to bypass an application’s access controls by guessing the required credentials. If the initial attack is successful, the attacker can then deploy secondary attacks, such as account takeover and credential stuffing.
To increase their chances of success with deciphering account credentials, cybercriminals use automated tools such as botnets to conduct brute force attacks.
Cybercriminals deploy simple brute force attacks based on the assumption that application users implement simple, easy-to-guess passwords like “Password1234” across their accounts. However, for more complicated variants like rainbow table attacks, they use advanced algorithms to bypass security.
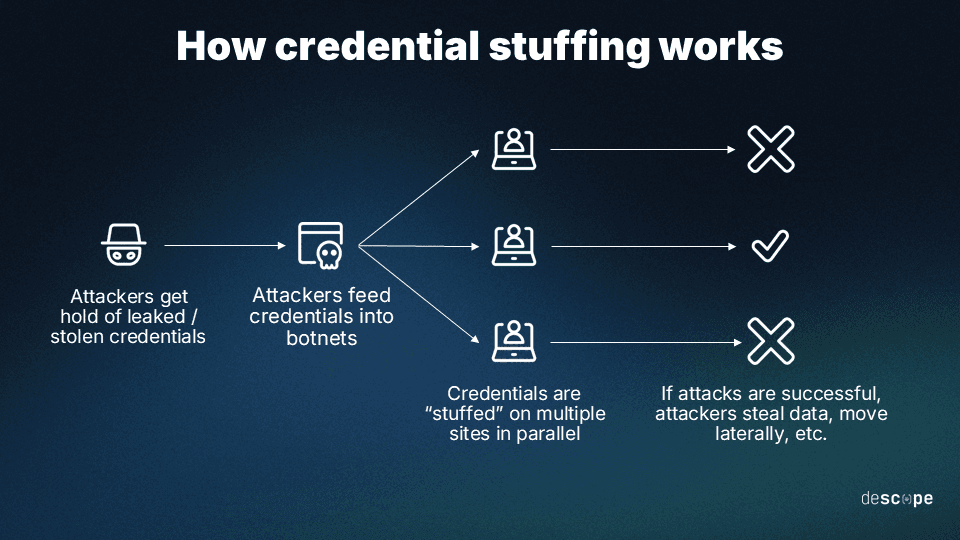
Credential stuffing
Credential stuffing is another common example of a broken authentication attack. It occurs when cybercriminals obtain login credentials through data breaches and then use these same login and password combinations to access unrelated accounts at separate services or organizations. This is possible because many people reuse the same password across different services.
Like brute force attacks, credential stuffing also leverages botnets to automate and increase the odds of success when plugging random passwords to bypass access controls.
Session hijacking
Session hijacking is a type of attack where an attacker takes over a valid user's session. Depending on the level of access the user has, the attacker can steal users’ identities, perform actions on their behalf, initiate transactions, etc.
Examples of session hijacking attacks include:
Session sniffing – Here, an attacker will use a sniffer to “sniff” around networks to identify exploitable vulnerabilities, like non-SSL/TLS-encrypted applications.
Cross-site scripting (XSS) – An attacker can also exploit web application vulnerabilities to inject malicious scripts in email or website links. Upon clicking these links, a user unknowingly grants the attacker control of an otherwise protected web session.
An infamous example of session stealing happened at CircleCI. Attackers infected an engineer’s laptop with malware to steal their 2FA-backed session cookie and used it to impersonate the employee from a remote location.
Phishing
Phishing is a type of social engineering attack where the attacker deceives an individual into revealing sensitive data. Since these attacks are socially engineered, victims are often clueless about when, how, or why the attack is happening.
Phishing attacks can take many forms, but some common examples include:
Emails that appear to be from a well-known company, such as a bank or ecommerce site, requesting the recipient to update their account information or confirm a recent transaction.
Messages that appear to be from a trusted person, such as a colleague or friend, requesting the recipient to click on a link or open an attachment.
Fake login pages that mimic a legitimate website to trick the user into entering their login credentials.
Most phishing attacks tend to appeal to victims’ emotions with a sense of urgency, eliciting excitement, confusion, or anguish that causes the victim to act impulsively.
Password spraying
Unlike brute force attacks, where cybercriminals try multiple passwords to access a single account, password spraying uses a single password across different accounts. This technique helps attackers stay undetected by security systems that lock out an account after too many failed login attempts.
Cybercriminals often use password spraying to target new accounts with common or weak passwords.
Broken authentication prevention and best practices
Now that we’ve explored how broken authentication works and common attack vectors, let’s talk about how to prevent it.:
Passwordless authentication
Many broken authentication attacks stem from the use of passwords as an authentication factor. Organizations should adopt passwordless authentication methods such as magic links, biometrics, social logins, and authenticator apps for their online services. While these methods vary in user-friendliness and security posture, they all have one thing in common: they’re far superior to passwords.
Passkeys have quickly emerged as a popular passwordless method, garnering adoption from tech giants like Apple, Microsoft, and Google. Passkeys are based on the FIDO2 open standard, which means they use encrypted keys instead of knowledge-based factors. They are also surprisingly easy to implement, with roughly 95% of devices already supporting them.
Multi-factor authentication
Gone are the days when users logged in to applications using a single form of authentication, such as a password.
To mitigate the risks of broken authentication, businesses must implement MFA. With MFA, users are required to provide at least two authentication factors before they can access their accounts.
These factors are knowledge (something you know), possession (something you have), and inherence (something you are). It’s important to remember that not all MFA is equal: some methods, like SMS one-time passwords, are more vulnerable to man-in-the-middle attacks than others. Even so, any MFA is better than relying on passwords as a single factor.
Enforce strong passwords
Simple, easy-to-remember passwords like Password123 are easily exploitable and present serious broken authentication vulnerabilities.
While passwordless authentication is the ideal end state, passwords (if and when they are used) must meet applicable standards for minimum length and character variety. A longer and more complex password is at a much lower risk of being compromised during a brute force or password spraying attack than a shorter and predictably common one.
Password hashing
Hashing is a form of password protection in which a one-way function converts a plaintext password into a non-reversible and unique string of characters. The hashed password is then stored in a database rather than the plaintext password. So, even with access to the database, it’s difficult for the attacker to use the passwords to cause compromise.
When combined with other techniques, like salting, password hashing makes it extremely difficult for cybercriminals to crack the credentials, making it one of the most effective protective measures.
Breached password detection
Adding breached password detectors like Have I Been Pwned to your arsenal will help you protect your business from broken authentication. These tools track the account data that’s been reported compromised or stolen by major breaches, and effectively recognize when an attacker attempts to log in to an account using these credentials.
Upon recognition of credentials in a breach, the breached password detector can notify users that their password has been compromised. The users can then change it, as per NIST guidelines.
Brute force protection
Your business can protect itself from brute force attacks by locking out an account as soon as multiple login attempts are registered to that same account. However, this is typically effective for a limited duration, say 30 minutes to an hour. And these brute force attacks can occur across multiple accounts, which could result in many users being locked out.
A more effective way to implement brute force protection is to block IP addresses detected as the source of multiple login attempts, whether at a single account or several of them. One such method is by using an IP reputation or scoring tool, like AbuseIPDB.
Regulate session length
Another common way businesses protect themselves from broken authentication is by limiting session length to a set time. Predefined session lengths reduce the risk of attacks like session hijacking.
Businesses that process highly sensitive data, such as banks and airlines, typically use this safeguard to automatically log out users when time runs out during idle sessions.
Remove session IDs in the URL
Since session IDs are unique identifiers, they should not be left in easily accessible locations like website URLs. By leaving them in URLs, your business increases the risk of these IDs being compromised and rewritten to regain access to a user session.
Rotate and invalidate session IDs
Upon completing a session, a user must be logged out. The session ID must also be invalidated on the client and server sides, so it cannot be reused.
Prevent broken authentication with Descope
Broken authentication isn’t just a security risk—it’s an open invitation. From token theft to brute force attacks, weak authentication can unravel even the most robust apps. The good news?
You don’t have to choose between building fast and building securely. With the Descope no / low-code CIAM platform, you can drag & drop secure, modern authentication flows without the usual complexity.
Don’t let auth be your weakest link—make it a strength. Sign up for a Free Forever account with Descope and unburden yourself from authentication security responsibilities.