Table of Contents
About Incode
Verifying user identity is essential for protecting against fraud and ensuring regulatory compliance, especially in sectors like finance, healthcare, and government. Yet, implementing this capability in-house is often resource-intensive and hard to scale.
And the stakes have never been higher: 29% of U.S. adults have experienced an account takeover, a sharp rise from 22% just a few years ago, according to Security.org. Even more concerning, 21% of these cases involved work-related accounts, putting business operations and customer data at risk.
With ATO fraud accelerating, it’s never been more critical for organizations to implement effective identity verification measures. Descope’s connector with Incode lets developers embed real-time document verification, facial matching, and liveness detection into authentication and user journey flows.
About Incode
Incode delivers accurate identity verification, fully automated, secure, and engineered to maximize conversions while preventing fraud.
Its AI-driven platform helps enterprises effortlessly distinguish legitimate users from fraudsters through deterministic verification, advanced deepfake protection, and intelligent orchestration.
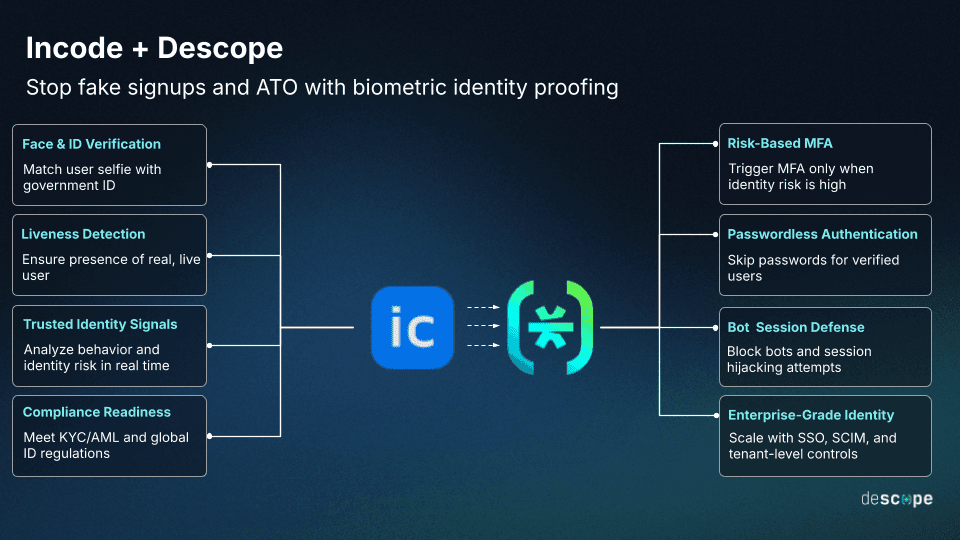
Connector overview
The Descope Incode connector allows teams to:
Collect and verify ID documents using Incode’s OCR and template-matching tools.
Compare user selfies against uploaded IDs to confirm facial identity.
Detect liveness during the selfie process to prevent spoofing.
Use verification confidence scores to build logic into Descope user journey flows.
Combine Incode checks with other fraud tools like reCAPTCHA Enterprise, Telesign, and Forter.
Leverage Incode IDV checks in Descope’s no-code UI or customize it with code-based logic for more advanced use cases.
Use case: Secure signup with ID and face verification
In industries such as finance, healthcare, and gaming, ensuring that users are genuine during the sign-up process is crucial to prevent fraudulent or duplicate accounts. These illegitimate accounts aren’t just a security risk. They create downstream costs across legal, compliance, and support teams.
According to AARP’s 2025 Identity Fraud Report, American’s lost a total of $47 billion to identity fraud and scams in 2024, marking a $4 billion increase from the previous year. Notably, ATO accounted for more than $15 billion of these losses, up from more than $12 billion in 2023. This escalating threat underscores the need for ID verification during onboarding.
By embedding document and facial verification into onboarding flows, organizations can reduce fraud, enforce Know Your Customer (KYC) policies, and preserve the integrity of their user base.
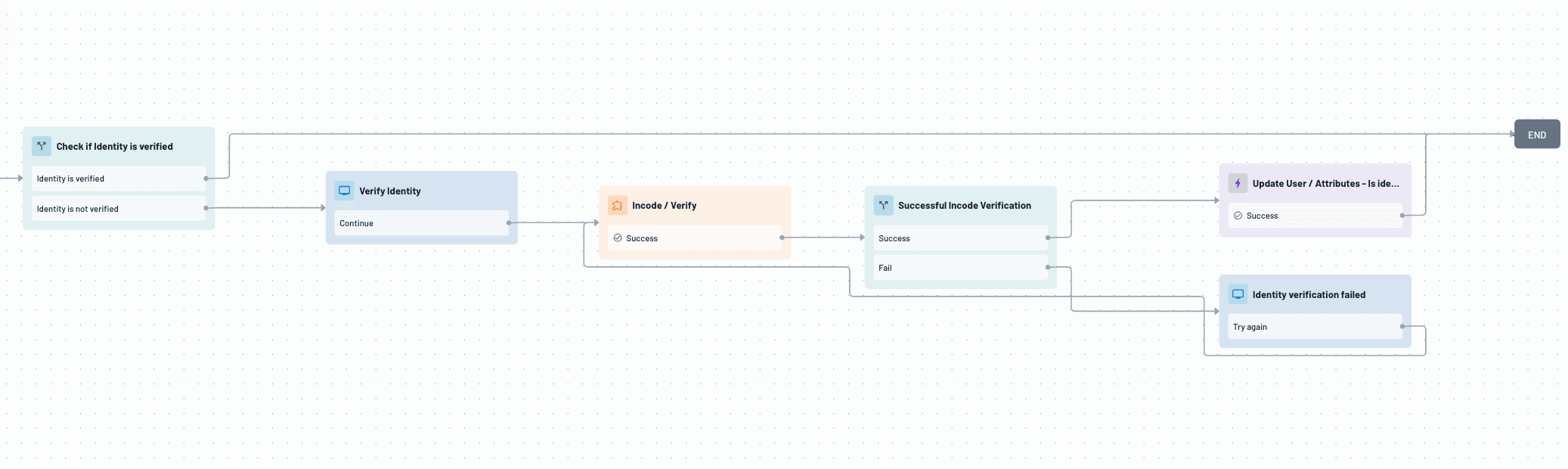
Here’s an example of a Descope Flow:
A user begins sign-up by providing an email or phone number.
After initial credential validation, Descope prompts the user to upload a government-issued ID and take a selfie.
Incode verifies the document’s authenticity, performs a facial match, and checks for liveness.
Based on confidence thresholds, users are either allowed to complete registration or routed to manual review.
This flow ensures that only verified individuals can create accounts—helping organizations cut fraud-related costs while meeting regulatory obligations.
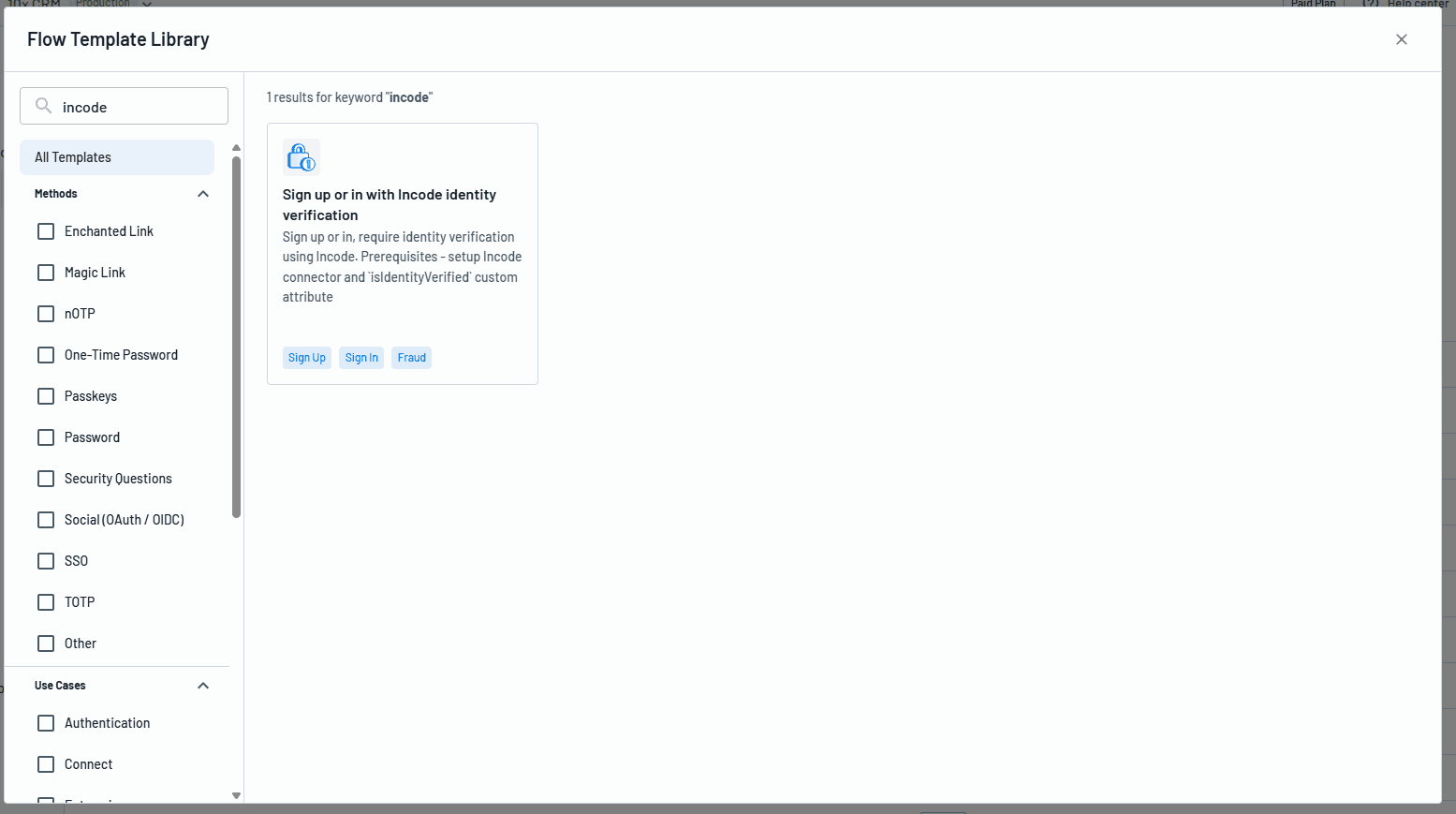
Get started quickly by using the “Sign up or in with Incode identity verification” Flow Template, available directly in the Descope Console to help you build and customize this flow with ease.
Use case: Self check-in at kiosk
Airports, convention centers, and large venues increasingly use self-service kiosks to speed up check-in and reduce staffing needs. However, while kiosks improve efficiency, they also introduce risks: without identity verification, it’s easier for someone to check in using stolen credentials or fake registrations.
Adding real-time ID and facial verification at kiosks helps ensure that the person checking in is the same person who registered.
Let’s say an attendee arrives at a conference kiosk and starts by entering their email or registration code. Descope handles this initial sign-in and, once confirmed, prompts the attendee to complete identity verification through Incode before issuing their event badge.
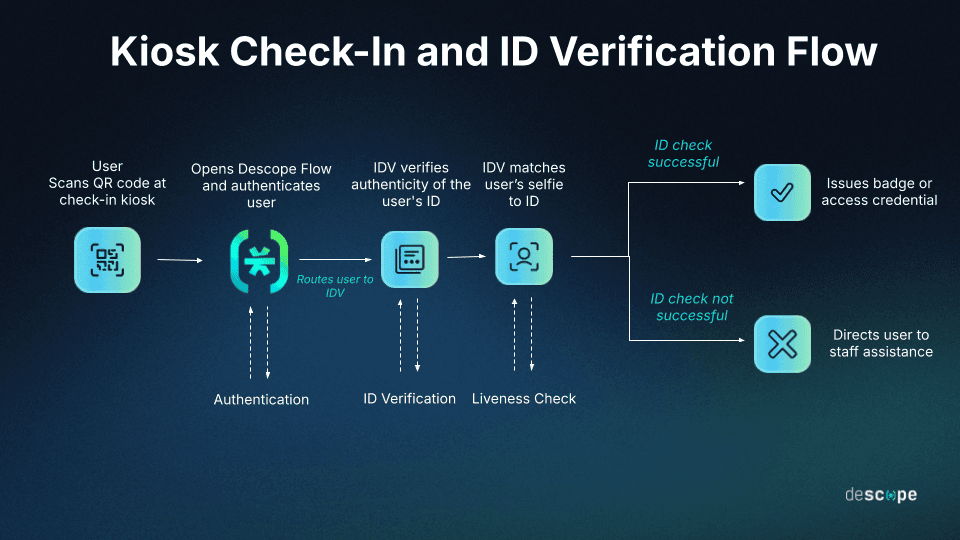
Here’s an example of a kiosk check-in flow:
The attendee starts check-in by entering their email, phone number, or registration code.
Descope authenticates the attendee’s registration details (e.g., via OTP or passwordless login).
Upon successful sign-in, Descope routes the attendee to Incode for identity verification.
Incode verifies the attendee’s ID authenticity.
Incode matches their selfie to the ID photo and checks for liveness.
Descope receives the results. If successful, the flow completes with the issuance of a badge or access credential. If not, the attendee is directed to seek staff assistance.
This setup helps prevent impersonation at self-check-in points, ensuring that only legitimate attendees or travelers can complete the process without slowing down the experience for verified users.
Conclusion
Descope’s connector with Incode helps teams embed high-assurance identity verification into their authentication flows, making it easier to reduce fraud, meet compliance requirements, and protect user accounts.
If you haven’t yet started your Descope journey, sign up for a Free Forever account and set up your own Incode connector. To explore other connectors, visit our integrations page.






