Table of Contents
What is an identity provider (IdP)?
The shift to centralized login methods is a major change in authentication over the past decade. Users increasingly benefit from the convenience of using their identities on one platform, like Google, to sign in to other platforms effortlessly.
Per one aggregate of social login studies, 86% of users express frustration when confronted with the need to create new accounts, and 77% favor social login or similar solutions as alternatives to traditional login.
However, users (and some developers) might not be aware of the role that Identity Providers (IdPs) play in this trend of centralizing and “outsourcing” user identity management. IdPs play an important role in authentication mechanisms like social login, single sign-on, and more.
In this article, we’ll cover the basics of identity providers, describe how they work, and highlight their role in simplifying identity management.
What is an identity provider (IdP)?
An identity provider is an entity that provides comprehensive management for digital identities, like identity creation and storage. IdPs actively engage with service providers (SPs) and other entities to facilitate authentication, authorization, and account management processes.
As an identity custodian, an IdP oversees users and other entities (like devices and networks), which are referred to as "principals". IdPs often have extensive user bases, such as Google, GitHub, Facebook, or enterprise platforms like Azure or SharePoint. That said, other products (including your own app) can also be IdPs depending on the use case.
It’s also worth noting that an entity can be an identity provider, a service provider, or both. For example, your product can be an identity provider if customers use usernames and passwords to log in, but can be a service provider when B2B users log in using SSO with an external identity provider. Descope can be both an identity provider and a service provider depending on the use case.
How IdPs work in practice
In practice, IdPs allow SPs to streamline the login process for their users by leveraging pre-existing relationships the users have with the IdP. If users already have an account with Google, Facebook, other prominent IdPs, or an internal enterprise account, logging in becomes much easier.
This is a typical workflow when users attempt to log in to a platform using their IdP identities:
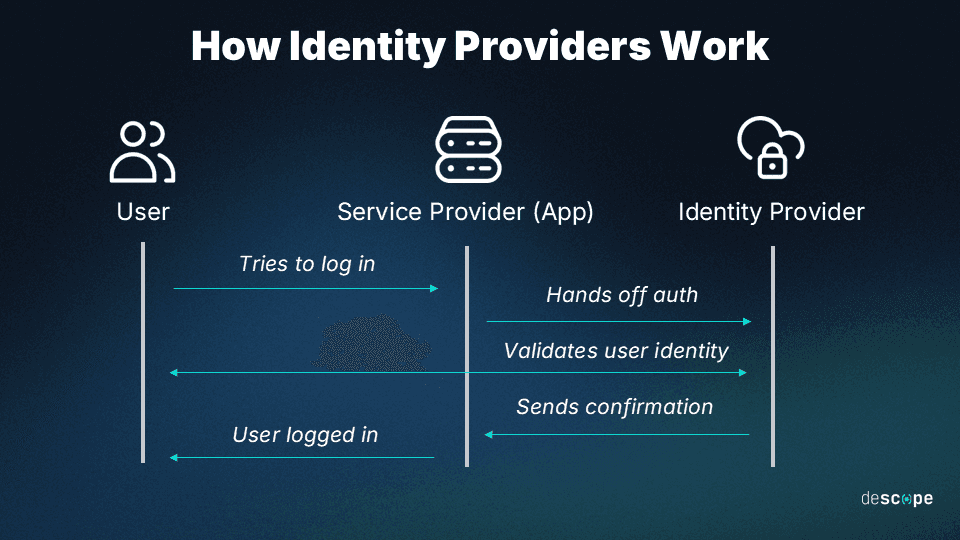
Users can choose to log in with their credentials through an IdP (e.g. “Sign in with Google”).
Users are redirected to an IdP-hosted page to authenticate their credentials there.
The IdP validates the user’s identity and communicates the confirmation to the SP.
With confirmation received, the SP grants the user access to the platform.
Communication between the SP and IdP commonly occurs through protocols such as Security Assertion Markup Language (SAML) or OpenID Connect (OIDC), which ensures that identity-related data is uniform and secure.
The importance of IdPs
Identity providers are central to storing and managing user identities across digital platforms. At the B2C level, social login streamlines user access, alleviating password fatigue and reducing friction for seamless engagement with websites and apps.
At the B2B level, IdPs provide the same customer- or client-friendly benefits, flexibility, and stability across other accounts (i.e., employees, management, and third parties). Working with an IdP streamlines account management and ensures compliance with privacy and security requirements organizations must adhere to. One of the ways IdPs do this is by enabling centralized and secure auth management through a single sign-on (SSO) platform.
Importantly, IdPs take the burden of user authentication off the shoulders of SPs and apps. By handing off these aspects to an entity that is focused on ensuring secure and frictionless identity management, app developers can better focus on core product initiatives.
The role of IdPs within SSO
Single sign-on is a specific use case for IdPs that leverages relationships to and between interconnected software. Most commonly used in enterprise environments, SSO facilitates authentication to a set of apps through a centralized IdP.
In practical terms, users (often employees) initiate the process by logging in to their SSO platform, which essentially acts as the IdP before logging in to connected apps. Once authenticated within the SSO app, users can access interconnected communication, reporting, and various enterprise apps.
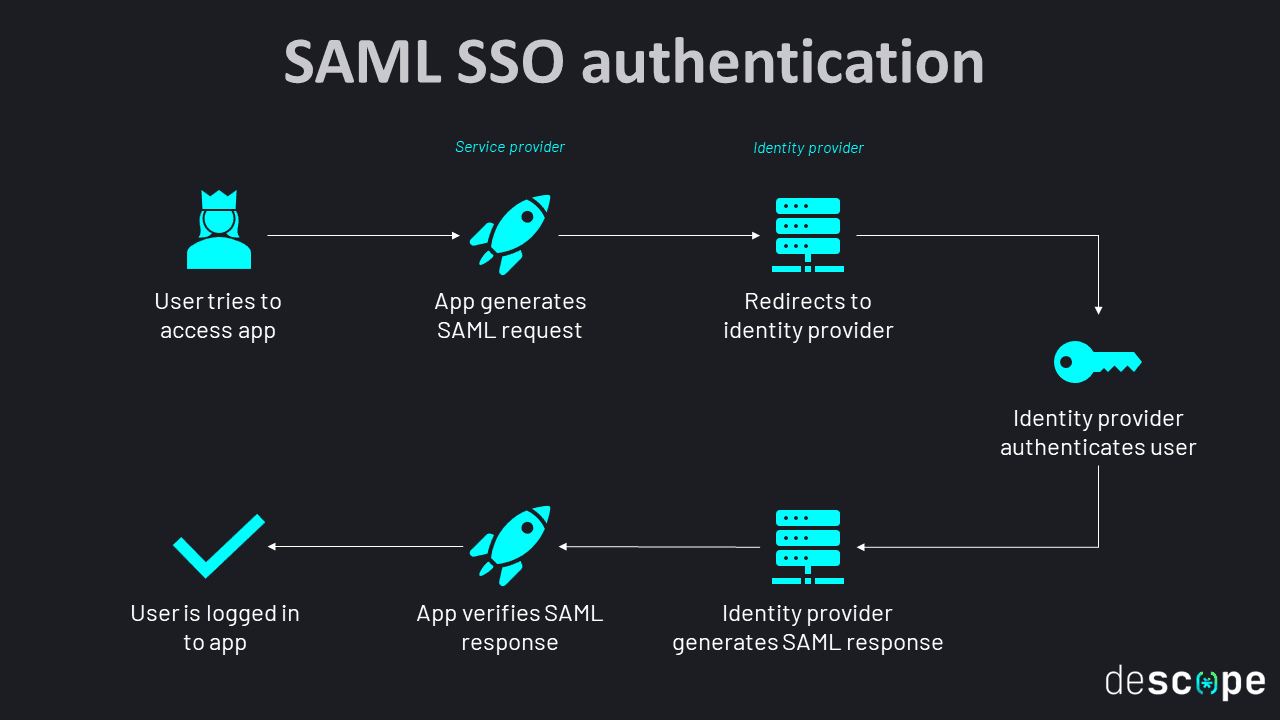
For B2B app developers, providing SSO capabilities to enterprise customers means working to integrate with popular IdPs as well as supporting popular standards such as SAML and OIDC.
IdP integration options
Selecting an IdP integration option largely depends on the target use case and customer environments:
SAML IdPs: SAML is a long-standing extensible markup language (XML) protocol. It has a commendable track record and is best suited to more traditional enterprise software suites.
OIDC IdPs: OpenID Connect (OIDC) is a newer, more agile protocol using JSON Web Tokens (JWT). OIDC is best suited to mobile and hybrid applications and social login.
IdPs work with a wide variety of traditional and non-traditional authentication protocols, well beyond SSO and SAML configurations.
The big question facing app developers is – should you integrate these IdPs in-house or rely on an external authentication service? While it’s certainly possible for engineering teams to do this themselves, the effort can quickly get unwieldy when supporting multiple IdPs, wrangling the specifics of their auth interpretations, and maintaining the implementation with time.
“Descoping” authentication from your app
Descope can help you easily add authentication, authorization, and user management to your apps. Our visual workflow editor lets you create and customize the entire user journey, as well as make ongoing modifications without redeploying your app or touching your codebase.
Descope can act as your identity provider or connect to any other IdP using SAML or OIDC. Our federation capabilities can even help you bridge user identities across disparate partner apps and IdPs.
Sign up for a Free Forever Descope account or schedule a demo to start your journey toward drag-and-drop auth.



