Table of Contents
What is token-based authentication?
As cyber threats evolve, so too have the means to counter them, leading to the emergence of more sophisticated and secure authentication methods. Among these, token-based authentication stands out as a robust solution that not only enhances security but also streamlines user experiences across various digital platforms.
Let’s delve into the intricacies of token-based authentication, exploring its mechanisms, advantages, considerations, and the use cases it serves in the modern digital landscape.
What is token-based authentication?
Token-based authentication is a passwordless security mechanism that validates a user's identity through the use of tokens. A token is a unique piece of data, often a string of characters, that acts as a stand-in for the user's credentials.
Unlike passwords that a user must remember and enter manually, tokens are generated and managed automatically, either as a physical device (smart card or USB) or as a digital file. This token contains a unique identifier, which is critical for the authentication process.
The premise of token-based authentication is simple: It uses something the user has (the token) to access their account and resources. And the primary objective of token-based authentication is to provide a more secure and user-friendly authentication experience.
By requiring a physical or digital token that is hard to duplicate or steal, it adds an extra layer of security compared to conventional password-based methods. This makes token-based systems ideal for protecting access to sensitive data, conducting financial transactions, or any scenario where strong authentication is paramount.
Token-based authentication is particularly effective in workforce environments where employees need secure access to corporate apps and systems. Hardware tokens based on the FIDO2 standard represent one of the strongest forms of authentication available today, leveraging the uniqueness of the physical token to ensure that only the rightful user gains access.
That said, identity frameworks like OAuth and OpenID Connect are driven by tokens and can be used for customer authentication as well. Providing token-based passwordless login experiences to end users can result in increased adoption, improved retention, and stronger resilience to account takeover attempts.
Types of tokens that can be used for authentication
Unlike hardware tokens, which are physical devices, digital tokens are cryptographically generated strings that authenticate and authorize users within a system. While there are multiple forms of digital tokens, we’ll explore the most commonly used ones and their functions.
Access token
Access tokens are perhaps the most common type of digital token. They act as digital keys that provide short-term access to secured resources, such as APIs or websites, after the user has been authenticated.

Essentially, they tell the server what actions the bearer (the entity that presents the token) is allowed to perform and which resources they can access. Due to their short validity period, they minimize the risk of unauthorized access if intercepted.
Refresh token
Refresh tokens complement access tokens. They have a longer lifespan and serve a singular purpose: to obtain a new access token when the current one expires. They are vital for maintaining a user's session without requiring the user to re-authenticate frequently.
When an access token expires, the client application can present the refresh token to the server to get a fresh access token, thus ensuring continued access to resources without interrupting the user experience. Refresh tokens enhance security by limiting the lifespan of access tokens and reducing the exposure time of active credentials.
Refresh token deployments can further be enhanced by implementing refresh token rotation or reuse detection to ensure protection against token theft and malicious use.
ID token
ID tokens are used primarily in identity protocols like OpenID Connect, where they serve as proof of the user's identity. They are issued alongside access tokens when a user authenticates with an identity provider. ID tokens typically follow the JSON Web Token (JWT) format, carrying information about the user's identity, such as their username and the time at which they logged in.
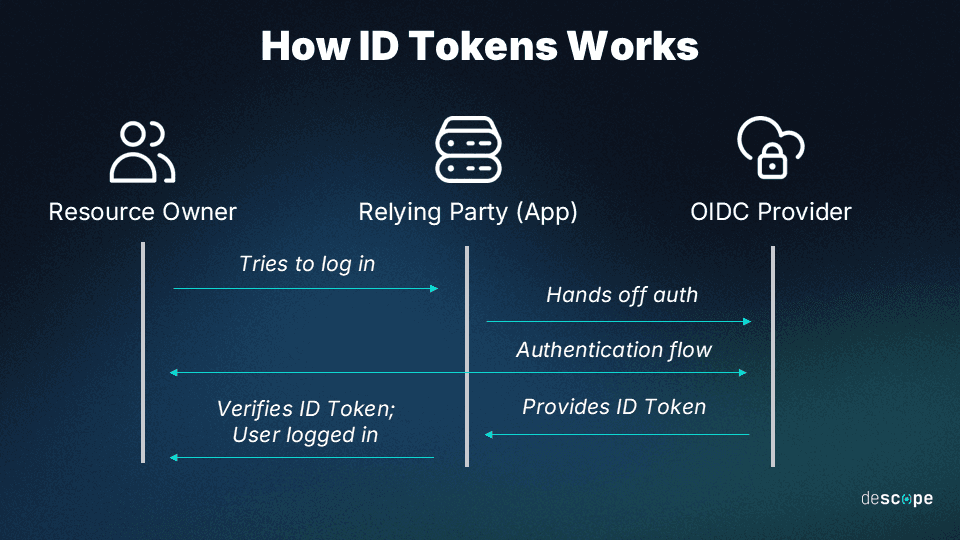
Clients can use ID tokens to verify the identity of the user and to tailor the user experience accordingly. For example, an application could extract the user's name from an ID token and display it on the dashboard.
How token-based authentication works in practice
In a token-based auth deployment, background processes do the bulk of the work in identifying users and maintaining security throughout their sessions through continuous re-authorization.
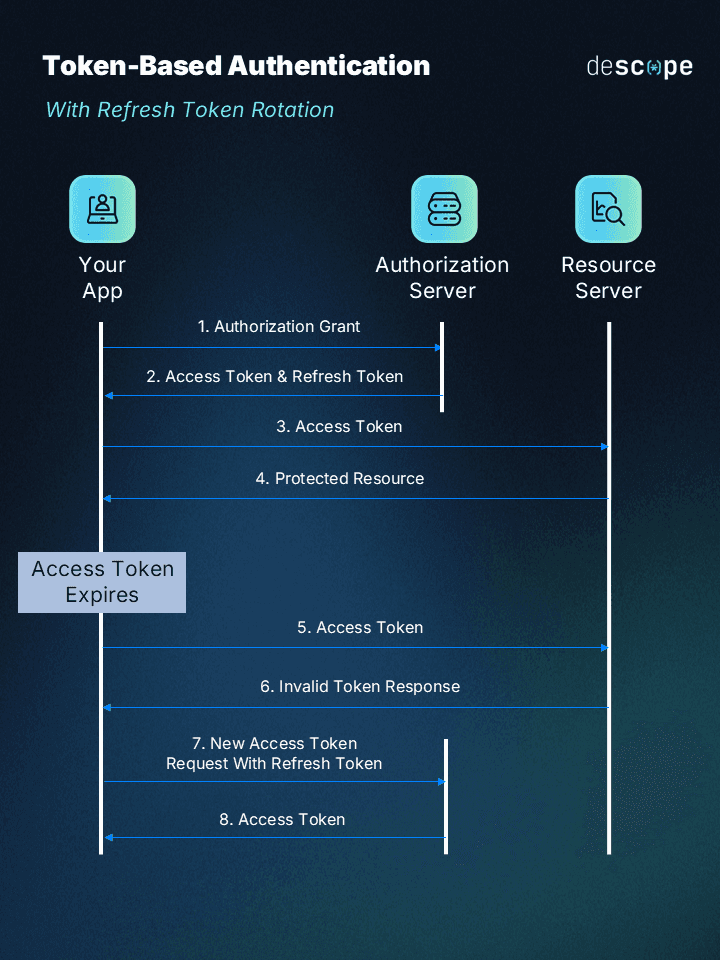
Here’s the process by which tokens are generated and used for authentication:
User Login: The process begins with the user providing their credentials.
Credentials Verification: The server verifies the provided credentials against its database.
Token Generation: Upon successful verification, the server generates a digital token, embedding within it the user's identity and any relevant data that would thereon be used for authorization purposes.
Token Issuance: This token is then returned to the user's client application.
Token Storage: The client securely stores the token, typically in local storage or as an in-memory variable.
This is where the authentication process concludes, and authorization takes over:
Accessing Secured Resources: For subsequent requests to access protected resources, the client includes the token in the request headers.
Token Validation on the Server: The server validates the token with each request, ensuring it's valid and authorizes access to the requested resource.
Resource Access: Upon successful token validation, the server grants access to the resource, completing the request-response cycle.
Token authentication streamlines the authentication process, reducing reliance on server-stored sessions and offering flexibility for distributed systems. By encapsulating user identity and permissions within tokens, applications can securely manage access controls and maintain user sessions across different services. This process exemplifies the balance between security and usability that modern web and mobile applications strive to achieve.
Advantages of token-based auth
Enhanced security: Tokens are much tougher to duplicate or compromise compared to traditional passwords. Since each token contains a unique identifier, it significantly reduces the risk of unauthorized access.
No need for passwords: With token-based authentication, the need for remembering complex passwords or storing them insecurely is eliminated. This reduces the risk of password theft or phishing attacks.
Scalability: Token-based systems are highly scalable, making it easier for businesses to manage access as they grow. They can quickly add or revoke token access for users without the cumbersome process associated with traditional password management.
Statelessness: Tokens are stateless; they carry all the necessary information within them. This means the server does not need to keep a session store, making the system more efficient and scalable.
Better user experience: Users enjoy a smoother experience since they no longer need to log in every time they access an app or service. As long as their token is valid, they are granted access, simplifying the user experience.
Multi-factor authentication: Token-based authentication easily integrates with MFA methods, adding an extra layer of security. Users might first log in with a password and then use a token for further validation.
Federated authentication: This system allows for delegated or federated authentication, where a third-party service can authenticate a user on behalf of the primary service. This is highly beneficial for services that rely on other platforms for user authentication (like social media logins).
Revocability: Tokens can be easily revoked or set to expire after a certain period, making it straightforward to manage access and respond quickly in case a token is compromised.
Potential risks of token auth
Despite its many benefits for all parties involved, there are some potential pitfalls that can negatively impact a company if token auth is not configured and maintained with care. Most cybersecurity implications of token auth stem from the fact that tokens themselves can be stolen, intercepted, or manipulated to give attackers illegitimate access to users’ accounts.
For instance, consider two recent instances in which cybercriminals targeted tokens:
In late 2022, Microsoft warned users about stolen tokens leading to MFA bypass. The company had detected an uptick in these attacks, which saw cybercriminals stealing already-vetted tokens to access accounts illegitimately and compromise users’ data.
In February 2024, Cloudflare disclosed details about a late 2023 attack tied to a single token and three service accounts’ credentials. These had been stolen during an earlier attack on Okta in which thousands of credentials (including tokens) were targeted.
As these examples illustrate, tokens can be used to infiltrate systems and neutralize other protections, allowing the very thing they exist to prevent—illegitimate account access. That’s why token auth needs to be paired with robust protections like encryption and session limits.
Common uses of token-based authentication
Token-based authentication's versatility and robust security features make it an essential component in a wide range of use cases. By employing token-based authentication, developers and organizations can build secure, user-friendly, and interoperable digital solutions that meet the evolving needs of their apps and userbase.
Single Sign-On: Token-based authentication is instrumental in implementing SSO systems, where users can access multiple related but independent software systems after logging in once. By generating a token upon the initial login, users can seamlessly navigate between services without needing to re-authenticate, significantly enhancing the user experience.
This makes it particularly beneficial in corporate environments, allowing employees to access various internal and external applications securely with a single set of credentials, thereby simplifying access management and improving security.
API security: APIs, which enable different software systems to communicate, require robust security to ensure that only authorized applications, services, or users can access them. Token-based authentication provides a secure way to manage API access, with tokens serving as keys that grant or deny permissions to API resources.
User authentication and session management: Both mobile and web applications can use token-based authentication to manage user sessions. After users log in, a token is generated and used for subsequent requests to authenticate and authorize access to application resources.
Token-based systems are also inherently platform-agnostic, making them ideal for applications that span multiple platforms (Android, iOS, Web).
Device authentication: In the IoT ecosystem, where countless devices need to securely connect to servers and each other, token-based authentication provides a lightweight and flexible solution.
Simple and secure token-based authentication
Token-based authentication provides a highly secure and scalable framework for managing user identities, improving API security, and enabling seamless access across platforms and devices.
However, the complexity of implementing token-based authentication can present significant challenges, from managing token lifecycles to ensuring secure storage and seamless user experiences.
For organizations looking to benefit from token-based authentication without the daunting task of custom implementation, Descope offers a simple drag-and-drop solution that integrates effortlessly into your existing infrastructure, providing robust authentication services with minimal effort.
Sign up for a Free Forever account with Descope to drag-and-drop your token authentication. Have questions about our platform? Book time with our auth experts.





