Table of Contents
What is an ID token?
Navigating the complexities of implementing authentication in web applications can be a daunting task, especially when it comes to distinguishing between the different types of tokens used in authentication and authorization.
In this article, we'll shed light on the distinct function of ID tokens in the authentication process, and delve into their importance in modern web security and digital identity validation.
What is an ID token?
An ID Token is a type of security token used primarily in identity confirmation. Typically formatted as a JSON Web Token (JWT), it contains authenticated user profile information. When a user logs in via an authentication process like OpenID Connect (OIDC), they receive an ID token alongside an access token.
Here’s an example of the structure of an ID token:
{
"iss": "https://example.com",
"sub": "1234567890",
"aud": "myapp",
"exp": 1698300000,
"iat": 1698296400,
"name": "John Doe",
"email": "john@example.com"
}Here’s a quick description of the fields:
iss (Issuer): Indicates the issuer of the token, in this case, "https://example.com". This field helps to identify the authentication server that issued the token.
sub (Subject): Represents the subject of the token, often a unique identifier for the user, which is "1234567890" in this example. It's used to identify the entity that is the subject of the JWT.
aud (Audience): Specifies the intended audience of the token, here it is "myapp". This field is used by the receiving service to verify that the token is intended for it.
exp (Expiration Time): Provides the expiration time after which the token must not be accepted for processing. The value "1698300000" is a Unix timestamp indicating the exact moment of expiration.
iat (Issued At): Indicates the time at which the JWT was issued, as a Unix timestamp. In this case, "1698296400" is the timestamp for when this token was created.
name: A custom claim to include the name of the user, "John Doe" in this example. Custom claims are used to share additional information about the user or other metadata.
email: Another custom claim to include the user's email address, which is "john@example.com" here.
Access token vs ID token
While both access tokens and ID tokens are JWT-based tokens that are crucial in the authentication process, their purposes differ significantly. Access tokens are used to grant access to resources, acting like keys to data or functionalities. In contrast, ID tokens are used to authenticate the user's identity, providing information about the authenticated user.
The table below captures the main differences between an access token and an ID token:
| Access Token | ID Token |
|---|---|---|
Purpose | Delegated authorization | User authentication |
Protocol / Specification | OAuth2 | OpenID Connect |
Participating Entities | Authorization Server and Resource Server | OIDC Provider and the App |
Use Cases | Grant an app access to a protected resource; Call and API; Inspect content server-side | Confirm the identity of a user; inspect user profile data |
How ID tokens work
The flow diagram below provides a simplified look at how ID tokens work:
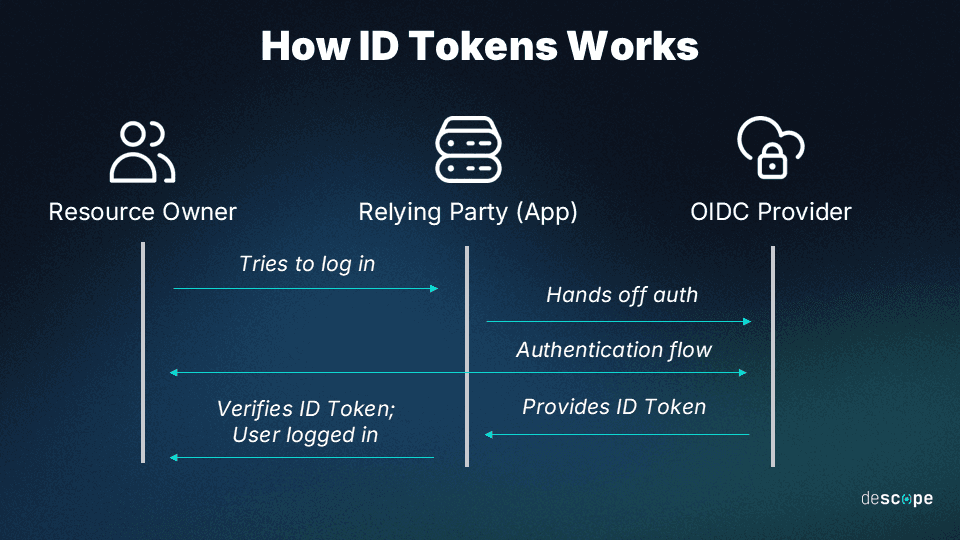
User login: The process starts when a user logs into an application using an identity provider (like Google or Facebook).
Token issuance: After successful authentication, the identity provider issues an ID token to the application.
Token reading: The application then reads this token to extract user information, ensuring the user is who they claim to be.
Authentication outcome: Successful authentication could return an access, refresh, and ID token along with the expiry time.
The primary role of the ID token here is to authenticate the user’s identity. It will contain claims about the authentication event and user (such as the user’s name, email, when they logged in, and so on). These claims can be used to personalize the user experience and ensure the user is authorized to perform actions specific to their identity.
Popular ID token use cases
Since OpenID Connect is a flexible and interoperable protocol, ID tokens find uses in many authentication processes. Some common applications of ID tokens include:
Single sign-on (SSO): In scenarios where users access multiple services or applications, ID tokens enable seamless authentication across these platforms.
Federated authentication: ID tokens are ideal for scenarios where identity information is managed and shared across different systems.
User profile access: ID tokens also come in handy when applications need basic user profile information after authentication.
Conclusion
ID tokens play a vital role in the digital authentication landscape. Their ability to securely convey user identity information while offering a seamless user experience makes them indispensable in modern web and mobile applications.
If you’re looking to simplify ID token management for your software project, Descope can help. Our drag-and-drop CIAM platform helps organizations add authentication, authorization, SSO, and federation capabilities to their apps using visual workflows.
Sign up for a Free Forever account or schedule time with our auth experts to get started with Descope.




