Table of Contents
Quick refresher: OAuth 2.0
OAuth has long been the backbone of secure, delegated access, allowing third-party apps to access user data without ever handling passwords or other sensitive credentials. OAuth 2.0, introduced in 2012, remains the most widely used version today. But as threats grow more sophisticated, the standards we build on need to evolve.
That’s where OAuth 2.1 comes in.
OAuth 2.1 isn’t a full rewrite. It’s a security-focused update that consolidates proven best practices and deprecates outdated flows that can introduce vulnerabilities. While still a draft specification, OAuth 2.1 is already being adopted by many libraries and teams that want a cleaner, safer path forward.
In this article, we’ll break down what’s new, what’s gone, and what these changes mean for developers building secure authorization flows.
Main points
OAuth 2.1 is a streamlined update, consolidating proven best practices and removing insecure grant types like implicit and password flows.
PKCE is now required for all authorization code flows, closing off common interception attacks across all app types.
Redirect URIs must match exactly, reducing the risk of token theft through open redirect vulnerabilities.
Refresh token rotation is strongly recommended, limiting the impact of stolen tokens and helping prevent replay attacks.
Quick refresher: OAuth 2.0
OAuth 2.0, introduced in 2012, is an open-standard framework that allows third-party applications to request limited access to user data, without ever seeing the user’s credentials. It became the go-to protocol for delegated authorization across web and mobile applications, powering everything from social logins to enterprise integrations.
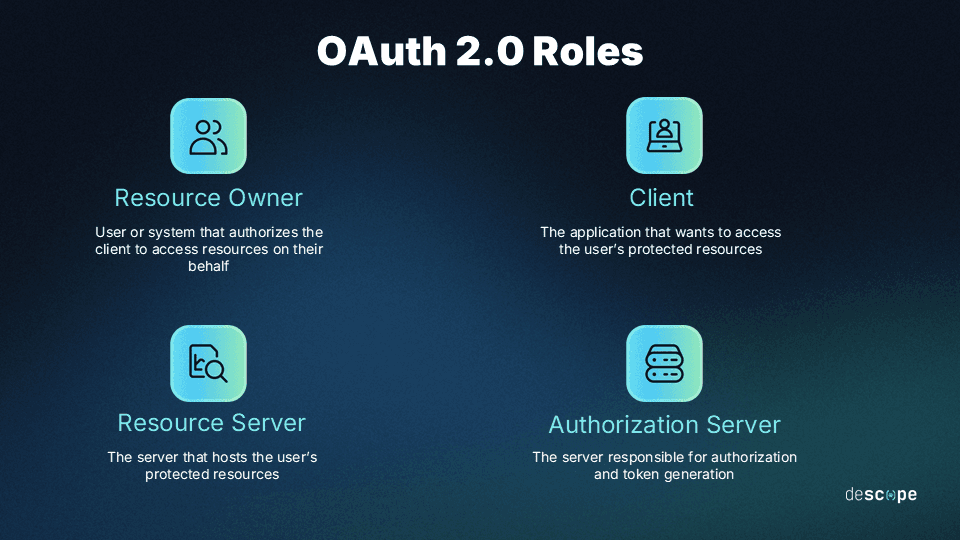
At the heart of OAuth are four core roles:
Resource owner: The user who grants access to their data
Client: The application requesting that access
Resource server: The system that stores and protects the user’s data
Authorization server: The service that verifies user consent and issues the tokens used to access resources
OAuth uses short-lived access tokens to grant permission to specific resources, and refresh tokens to obtain new access tokens without requiring the user to reauthenticate. This token-based system allows for secure, temporary access, but it’s not foolproof.
Over the years, attackers have found ways to exploit misconfigured flows, steal tokens, and impersonate users. These vulnerabilities—and the inconsistent way OAuth 2.0 has been implemented—are a key reason why OAuth 2.1 was introduced: to streamline best practices and close common security gaps.
Read more: 5 Ways OAuth Can Go Wrong (and How to Avoid Them)
OAuth 2.1
OAuth 2.0 has been extended and adapted through community-driven best practices, optional security add-ons, and third-party library conventions. While flexible, this patchwork approach often led to inconsistent implementations and avoidable vulnerabilities.
OAuth 2.1 was introduced to bring clarity and cohesion to the ecosystem.
Rather than reinventing the protocol, OAuth 2.1 streamlines it, retaining only the most secure, widely adopted practices while removing outdated and risky features like the implicit and password grant types. It formalizes what secure OAuth should look like in 2025 and beyond.
The result is a cleaner spec that’s easier to implement correctly and harder to get wrong, especially for developers building modern apps with high security expectations.
Although OAuth 2.1 is still in draft status, several core changes have already been adopted by many frameworks and security-conscious teams. These updates aim to reduce the risk of common misconfigurations by hardcoding today’s best practices into the spec.
PKCE is now required
Proof Key for Code Exchange (PKCE) is now mandatory for all clients using the authorization code flow.
Originally designed to secure native and mobile apps, PKCE prevents attackers from intercepting authorization codes and exchanging them for tokens. It works by having the client generate a random code verifier and a code challenge (a hashed version of the verifier) during the initial request. The authorization server stores the challenge, then verifies the client’s original code verifier before issuing tokens.
In OAuth 2.0, PKCE was recommended only for public clients. OAuth 2.1 removes that distinction, requiring it for all clients to close a critical attack surface across the board. With PKCE also being the recommended modality by the MCP specification, developers have all the more incentive to support this in their auth flows.
Implicit grant removed
The implicit grant flow has been removed.
Implicit flows allowed access tokens to be returned directly in the URL fragment, skipping the intermediate step of exchanging an authorization code. While convenient for early single-page apps (SPAs), this shortcut made tokens vulnerable to leakage via browser history, referrer headers, or malicious scripts.
With modern browser support for secure cross-origin requests (CORS) and the rise of frontend-backend architectures, the implicit flow is no longer needed and is now formally deprecated in OAuth 2.1. SPAs should use the authorization code flow with PKCE, which enables secure token handling and supports refresh tokens.
Password grant removed
The Resource Owner Password Credentials (ROPC) grant is also deprecated.
This flow required users to share their credentials directly with the client, which then exchanged them for access tokens. While it simplified things in tightly controlled environments, it introduced significant risks, exposing user credentials to apps and making features like multi-factor authentication (MFA) or single sign-on (SSO) hard to enforce.
OAuth 2.1 removes the password grant to align with modern security models that minimize credential handling by third parties.
Exact redirect URI matching
OAuth 2.0 allowed flexible redirect URI matching using wildcards and substring patterns—intended to make development smoother. Unfortunately, this flexibility opened the door to open redirect vulnerabilities, where attackers could manipulate redirect URIs to steal tokens or impersonate apps.
OAuth 2.1 requires exact string matching for redirect URIs. Clients must pre-register every allowed redirect URI, and the authorization server must enforce an exact match. This eliminates ambiguity and makes unauthorized redirects far harder to exploit.
Refresh token rotation
Refresh tokens let clients renew access tokens without requiring the user to log in again. But if refresh tokens are not rotated, and an attacker steals one, they can bypass the entire authorization process indefinitely.
OAuth 2.1 strongly encourages refresh token rotation, where each token is single-use and replaced on every request. If a rotated token is replayed, it’s immediately invalidated, stopping token replay attacks in their tracks.
While not strictly required by the spec, rotation is now treated as a best practice, referenced in RFC 6819 and supported by most modern identity platforms. Combined with sender constraints or token binding, rotation significantly raises the bar for attackers attempting to abuse stolen tokens.
Who should migrate to OAuth 2.1?
OAuth 2.1 is designed for anyone building secure, modern applications—but it’s especially relevant for new projects that want to start on solid ground. For developers prioritizing strong security and simplified flows, adopting 2.1 principles is a no-brainer.
For existing systems, the decision to migrate depends on your current setup. If you rely on flows deprecated in OAuth 2.1, you’ll need to evaluate the effort required to refactor, update your clients, and ensure compatibility with modern security requirements.
Many popular OAuth libraries have already started adopting OAuth 2.1 defaults, making it easier to phase in best practices without a full rebuild. And as security expectations rise across the industry, aligning with 2.1 isn’t just about compliance—it’s about staying ahead of known risks.
Migration considerations
When considering whether to migrate to OAuth 2.1, consider the following checklist:
Current implementations: Audit your existing OAuth implementation. If you’re still using implicit or password grant types, begin planning a transition to supported flows like authorization code with PKCE.
Assess client compatibility: Confirm that all client applications—especially SPAs, mobile, or IoT apps—can securely handle the authorization code flow with PKCE. This is now required in OAuth 2.1.
Revise redirect URIs: Ensure that all pre-registered redirect URIs use exact string matching. Wildcards and flexible patterns are no longer supported.
Implement refresh token rotation: Check whether your refresh tokens are reused. If so, update them to rotate on every use, and consider using short lifespans and sender constraints for added protection.
Replace deprecated flows: Begin deprecating and disabling implicit and password grant flows. OAuth 2.1 assumes these are no longer part of your stack.
Educate your team: Make sure your developers understand the changes, especially those managing client registration, token handling, and security reviews. The shift to 2.1 is as much about education as it is about enforcement.
Side-by-side comparison: OAuth 2.0 vs. 2.1
Password Grant (ROPC) | Supported | Removed (deprecated for security and MFA incompatibility) |
Redirect URI Matching | Flexible (wildcards and substring matches allowed) | Exact string matching required |
Refresh Token Rotation | Optional | Strongly recommended (best practice to prevent replay attacks) |
Browser-Based SPA Support | Typically used implicit flow | Must use auth code flow with PKCE |
Spec Status | Finalized (RFC 6749) | Draft (in progress, consolidates best practices) |
Security Focus | Open to misconfigurations | Secure-by-default through enforced best practices |
Embracing OAuth 2.1 for enhanced security
OAuth 2.1 isn’t about reinventing the wheel—it’s about making sure the wheel is bolted on securely. By consolidating years of hard-earned best practices and removing outdated, risky flows, it gives developers a cleaner, more reliable foundation for building secure auth systems.
Whether you’re launching a new app or tightening up an existing one, aligning with OAuth 2.1 will help you avoid common missteps and future-proof your implementation against emerging threats. The spec may still be in draft form, but the direction is clear: simpler, safer, and harder to get wrong.
Now’s the time to take stock of your current setup, start phasing out legacy flows, and adopt the practices that make secure authorization the default—not the exception.
Looking to modernize your authentication flow? Sign up for a Free Forever account on Descope or book a demo to see how we can help you build secure, OAuth 2.1-ready experiences—fast.