Table of Contents
Credential theft and walking through the front door
Credentials remain the number one battleground in cybersecurity, according to the newly released 2025 Verizon Data Breach Investigations Report (DBIR). While this report heavily focuses on enterprise-level security events, its findings are a signal for every part of our digital ecosystem, especially customer authentication. When the DBIR notes a trend, seasoned cybersecurity veterans and stakeholders across every organization take notice.
The 18th annual DBIR analyzed over 22,000 incidents, with roughly half being confirmed as actual data breaches. These episodes reveal an uncomfortable truth: even with strong authentication options available, attackers still target the path of least resistance, credentials. This year’s findings highlight the evolution of identity-based attacks and why traditional security approaches are failing to protect accounts.
In this analysis of the DBIR, we’ll unpack the most critical identity-focused findings from the report and explain what they mean for your security strategy.
Main points
Credential abuse: Stolen credentials remain attackers’ preferred entry point despite billions spent on stronger digital infrastructure, with only a fraction of compromised passwords meeting bare-minimum complexity requirements.
MFA bypass: Conventional multi-factor authentication is failing as attackers deploy prompt bombing, token theft, and other sophisticated techniques to waltz through typically robust protections.
Passwordless opportunities: With passwords still in the crosshairs, the DBIR’s findings make a compelling case for phishing-resistant passkeys as the path toward reliable security.
Credential theft and walking through the front door
The DBIR annually underscores what cybersecurity experts already know too well: when attackers have options, they choose the easiest path available. That means threat actors are less likely to probe for backend vulnerabilities and more likely to phish, guess, scrape, or simply buy credentials from a darknet broker. And, for yet another year in a row, credential compromise remains the number one initial access vector for breaches.
The DBIR’s credential-focused facts tell a story deeply relevant to customer identity:
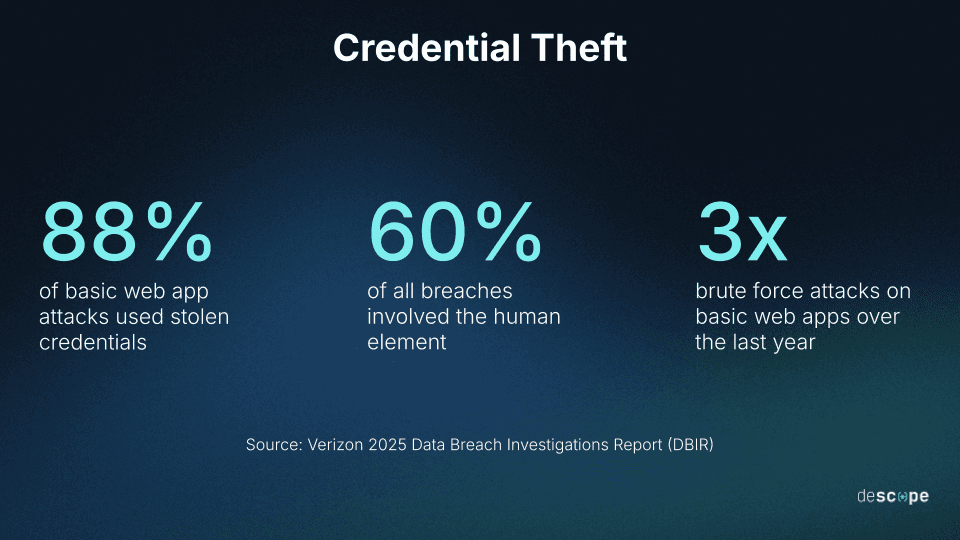
A staggering 88% of attacks against basic web applications involved the use of stolen credentials
60% of all breaches involved the human element (where users interact through actions like clicking phishing links or responding to social engineering)
Brute force attacks against basic web apps rose exponentially, nearly tripling over the last year (from roughly 20% to 60%)
In 2024, 2.8 billion passwords were posted for sale (or for free) on criminal message boards, in encrypted messenger groups, and on darknet markets. Gigantic data dumps are regularly circulated in these underground communities, and while passwords appear in 28%, other sensitive information often appears instead or alongside them.
This includes personal details like email addresses (in 61% of breached databases), phone numbers (39%), government-issued IDs (22%), IP addresses (13%), and even passports (1.8%). While one of these pieces of data may not constitute a serious threat, weaving them together can allow cybercriminals to more easily obtain access to accounts or credentials, if they don’t already have them.
But perhaps most alarming for customer-facing organizations is the dismal state of password quality: analysis shows that only 3% of compromised passwords met basic complexity requirements. These statistics paint a grim portrait of the current threat landscape: authentication remains the primary point of failure, with stolen credentials (namely, passwords) giving attackers unchallenged access to customer accounts and the sensitive data they contain.
The growing problem of MFA bypass techniques
We’ve said it before, and this year’s DBIR is saying it again: not all MFA is equal. The report reveals an increasing number of MFA bypass attacks, indicating that threat actors aren’t giving up when they hit a second layer of authentication. They’re finding ways to circumvent it: stealing codes in real time, hammering victims with prompts, and harvesting tokens that bypass MFA entirely.
Looking specifically at attacks against Microsoft 365 accounts, the DBIR found several MFA bypass techniques gaining traction:
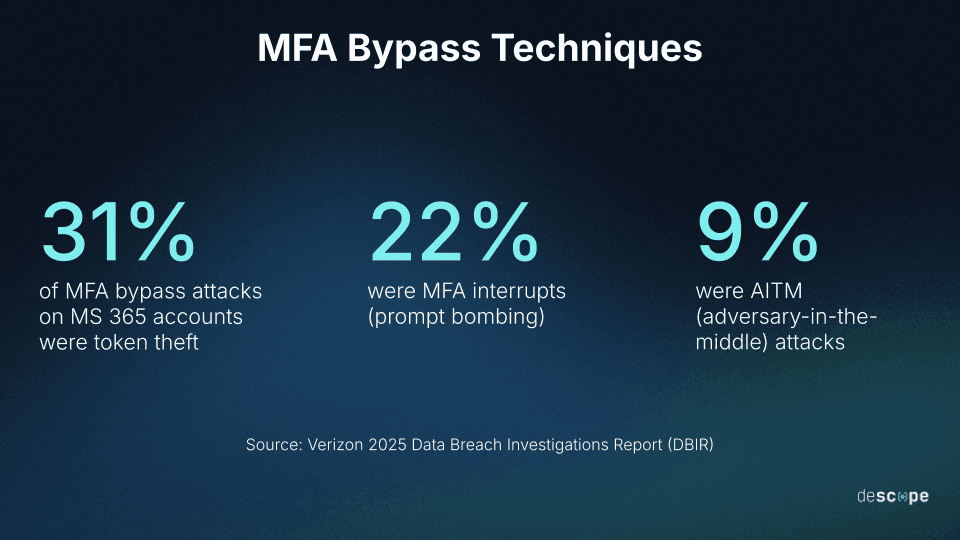
31% of threat actors chose token theft
22% were MFA interrupts (also known as MFA fatigue or prompt bombing)
9% of attacks were from the man-in-middle (MITM) variant, adversary-in-the-middle (AITM)
While the DBIR notes that having MFA turned on is still the “gold standard” for account protection, enabling it shouldn’t be a replacement for robust detection and monitoring. By the same token, they recommend against SMS (text message) one-time passwords (OTPs) for MFA, noting their vulnerability to SIM swapping and the potential for bypass. Instead, the DBIR points to time-based one-time passwords (e.g., authenticator apps) as a more secure option.
The report discusses MFA in another light, as well: third-party involvement in breaches, which doubled from 15% to 30% of all incidents in just a year. They examine the highly publicized Snowflake breach, a case in which simply enabling MFA might have thwarted the entire attack. This breach is notable both because of its reach (affecting major companies like AT&T, Ticketmaster, and Santander Group) and simplicity. The threat actors, realizing MFA was not mandatory at the cloud data provider, exploited vulnerable credentials to breach multiple Snowflake customers.
The rise of infostealer malware
In early 2025, Picus Security published a deep-dive Red Report analyzing over 1 million samples of malware. One of the most disturbing findings from this study was that 25% of all tested malware contained credentials from password stores. Some targets for this type of malware were Apple Keychain, web browsers (i.e., saved autofill info), Windows Credential Manager, and password managers. However, infostealers aren’t limited to simple passwords; they can also harvest cookies and valuable crypto wallet information just as easily.
This year’s DBIR indicates the infostealer malware trend is increasing in frequency and volume, with particularly troubling statistics for organizations managing customer identities. On darknet credential markets:
62% of infostealer logs contained logins for social media accounts
49% were gaming accounts
44% for streaming services
17% had banking site login details
Returning to the Snowflake breach example, approximately 80% of the compromised accounts in that attack (roughly 132) had prior credential exposure, “potentially collected by infostealers,” says the DBIR. And while organizations can’t guarantee that their users will be infostealer-free (as there’s no way to force customers to update their OS or virus protection), they should “assume compromise.” That means turning on MFA, even if bypass methods have become more effective.
Eliminating passwords is the path forward
While the rise of MFA bypass techniques may cast a shadow over conventional mutli-factor, the reality is that it’s still a highly reliable reinforcement that everyone should use whenever possible. However, there’s another conclusion we can draw from the DBIR’s findings, one that combines the obvious decline of password-based security and the need for stronger forms of MFA: passkeys.
The DBIR doesn’t directly address FIDO-based passkeys, which are inherently phishing-resistant and use cryptographic techniques to prevent MFA bypass attacks. For example, AITM or MITM attacks are completely useless against passkeys since the data these methods capture is inert without the user’s device. Similarly, passkeys only work on the site or service for which the originated; a user can’t be tricked into generating a valid token for the attacker to steal because their passkey won’t work on a spoofed site.
Microsoft recently dialed up their passkey adoption with the tagline “passwordless by default.” Now, all new accounts will be passwordless, and sign-in will prefer passwordless options (automatically showing them if available on the device). It’s a less dramatic move than it sounds, given Microsoft’s success with passkeys thus far:
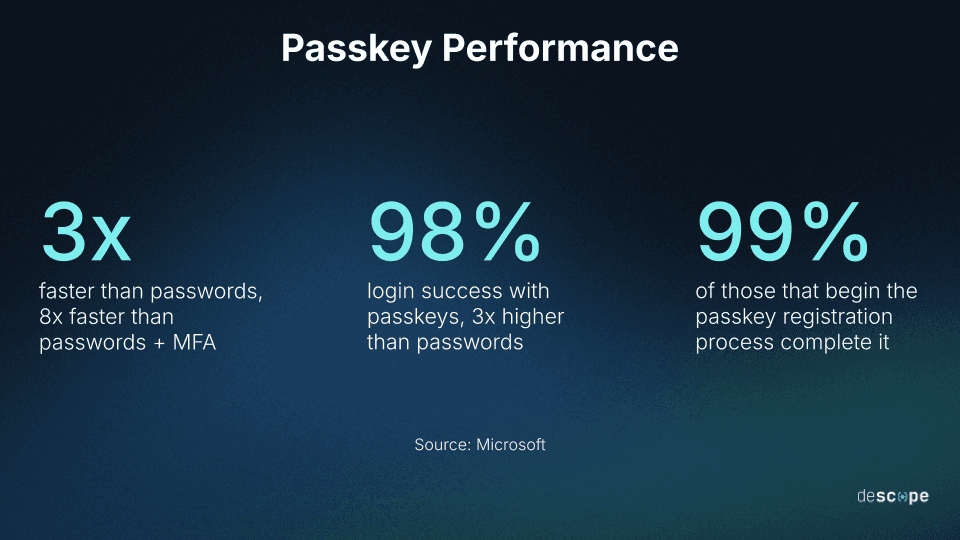
Login speed: Passkeys are 3x faster than traditional passwords and 8x faster than passwords with standard MFA
Sign-in success: Passkey logins succeed 3x more often than passwords (98% vs. 32%)
Onboarding is easy: 99% of those who begin passkey registration complete it
Passkeys solve two of the biggest challenges the DBIR discusses: credential abuse (via infostealer, phishing, etc.) and MFA bypass. And while strengthening existing systems (including weak passwords) should remain a goal for customer-facing organizations, eliminating traditional credentials isn’t quite the paradigm shift it used to be. More and more, it looks like the only path forward.
Learning from DBIR data to create better auth experiences
Starting a passkey implementation from scratch comes with considerable cost: dev cycles, maintenance, integrations, and more. Descope’s comprehensive CIAM solution makes adding passkeys to your existing identity infrastructure as simple as dragging, dropping, and pasting a few lines of code. Once Descope is working on your application, you can easily make real-time changes without touching your codebase again.
Ready to explore how passkeys can help your organization eliminate the threats of stolen credentials, MFA bypass, and phishing? We’ve got you covered:
Try our interactive demo at passkeys.guru, which allows you to experience passkeys firsthand
Sign up for a Free Forever Descope Account to start designing your own identity flows
Join our dev community, AuthTown, and connect with like-minded builders
You can also reach out to our auth experts to learn more about how Descope can help you solve countless CIAM challenges, from securing your AI agents to creating the ultimate end-to-end ecommerce experience.