Table of Contents
What is MFA bombing?
You lock your doors to keep intruders out, but what happens when someone keeps knocking? MFA bombing is the digital equivalent—attackers flood users with authentication requests, wearing them down until they accidentally let the intruder in.
So, let’s understand how MFA bombing works and learn strategies to stop these attacks before they reach your doorstep.
Main points:
MFA bombing: Attackers flood users with repeated MFA prompts, exploiting "MFA fatigue" to trick them into approving a fraudulent request, granting unauthorized access.
Attack strategies: Tactics include sending high volumes of requests in bursts, spreading prompts over time, or using social engineering to deceive users into approving requests.
Protective measures: Educate users on recognizing suspicious activity, use strong or passwordless authentication methods, and set up automatic account lockouts after multiple failed attempts.
What is MFA bombing?
MFA bombing, also known as MFA prompt bombing, is a type of cyberattack where threat actors exploit a phenomenon called “MFA fatigue” to gain unauthorized access to users’ accounts.
MFA fatigue occurs when users are overwhelmed by repeated authentication prompts and become less vigilant about security. The strain of managing MFA across personal and professional accounts can lead users to make poor decisions or simply give in to the constant barrage of requests.
Prompt bombing takes advantage of this fatigue, overwhelming users with frequent, fraudulent MFA prompts. When users are tricked into approving these false requests, attackers can take over the accounts, gaining unauthorized access to sensitive systems and data. Once inside, attackers can disrupt operations, steal intellectual property, or even hold organizations hostage for ransom.
"MFA prompt bombing" and "MFA spamming" are often used interchangeably to describe the same tactic. Regardless of the name, the method remains a popular tactic to bypass MFA protections.
Read more: Broken Authentication 101
How MFA prompt bombing works
Prompt bombing allows attackers to bypass MFA protections by bombarding users with fake MFA requests until they make the mistake of approving one. Attackers use different strategies to carry out these attacks, including.
Request bursts: Attackers send a high volume of MFA requests in a short time frame. The goal is to overwhelm users, creating confusion or frustration that prompts them to approve a request simply to stop the notifications.
Slow and steady requests: Alternatively, attackers may spread prompts over a longer duration, sending small, seemingly harmless daily prompts. This approach is subtler, allowing the attackers to fly under the radar while wearing down the user’s resistance to repeated requests.
Targeted requests: Attackers may also combine MFA bombing with social engineering tactics. They can call or email the victim, posing as an authoritative figure within the organization. A notable example of this method is the 2022 LAPSUS$ attack against Uber. The threat actor sent a series of MFA prompts to the target, then contacted them claiming to be from Uber IT. Believing the requests to be legitimate, the user followed the cybercriminal’s instructions and approved a prompt.
No matter the method used, even a single successful breach can have significant consequences. Once an attacker gains access to an account, they can move laterally within the system, accessing other data or accounts, potentially wreaking havoc.
How to protect against MFA bombing
To protect against MFA bombing attacks, it’s crucial to implement both technical defenses and user awareness initiatives. While identity and access management (IAM) systems, firewalls, and content filters are essential, several additional methods can help safeguard against prompt bombing.
Train your users
Protection against prompt bombing begins with user awareness. In corporate environments, this means training employees during onboarding and providing regular security awareness sessions. For clients or other users, you should provide clear, easily accessible instructions on protecting their accounts.
You should teach users how to recognize suspicious behavior and encourage them to report any unusual activity. Well-informed users are much less likely to fall victim to MFA prompt bombing.
Use strong (preferably passwordless) authentication methods
The effectiveness of MFA bombing attacks depends on weak or compromised authentication factors. To thwart these attacks, it’s critical to use strong authentication methods. Ideally, move towards passwordless authentication, which is less prone to compromise than traditional passwords.
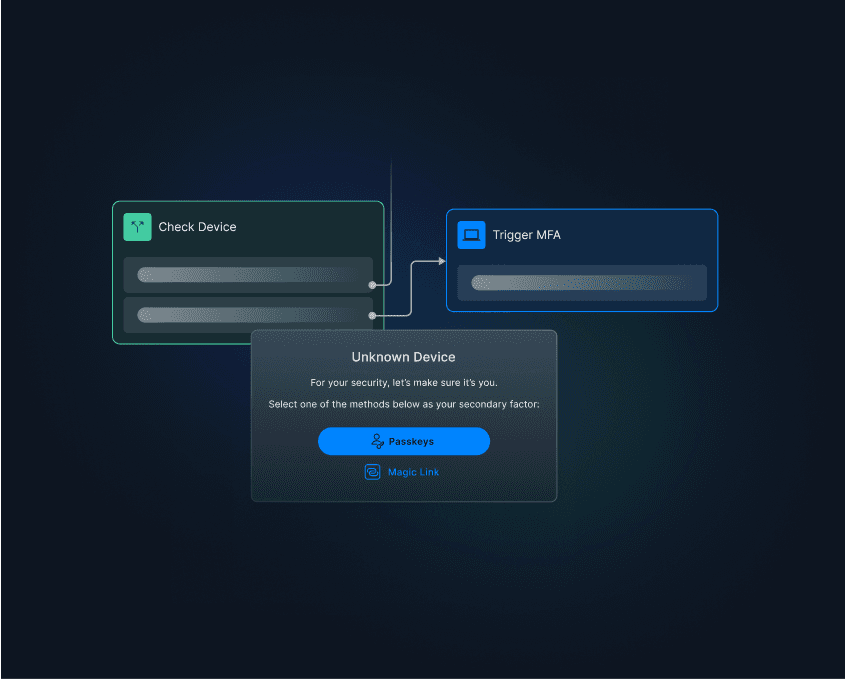
Methods like magic links, social logins, and biometrics are more secure and harder to manipulate. If attackers can’t bypass the first authentication factor, they are effectively blocked from carrying out prompt bombing attacks.
Implement automatic account lockout controls
Another way to limit the risk of prompt bombing is by configuring account lockout policies. Set up systems to lock accounts after a certain number of failed login attempts, requiring additional verification to regain access. This is a form of rate limiting, a threshold that prevents additional actions once a specific number of attempts during a set window is met.
However, as demonstrated by the AuthQuake exploit, rate limiting is still vulnerable to manipulation by threat actors. To reinforce it, you can also implement anomaly detection systems that assess the risk of login attempts based on various factors, like the frequency of requests or the location from which a user is attempting to log in.
We also recommend re-authentication, particularly for high-risk or regulated industries. Prompting users to re-authenticate periodically ensures that sessions are not left open indefinitely, reducing the chance of unauthorized access.
Move to phishing-resistant MFA
The best defense against MFA bombing is phishing-resistant MFA, which complements strong authentication with behavioral monitoring.
By analyzing user behavior, these technologies establish a baseline of normal activity—like login locations and trusted devices. When anomalies, such as an unusually high volume of MFA requests, are detected, the system can trigger additional authentication steps or lock the account to block unauthorized access.
While this type of attack often targets specific users, like in the 2022 Uber breach mentioned above, threat actors may choose to automate elements of MFA bombing. In this scenario, they will typically harness a botnet (a group of compromised devices that do their bidding without the owners’ knowledge) and a list of compromised login credentials. The botnet will attempt to authenticate using the stolen credentials, only notifying the botnet’s controller when they work.
Threat actors would also employ automation tools to issue a barrage of MFA prompts much faster than a human could manually. This is why analyzing sessions for anomalies can prevent MFA bombing from achieving its goals. Behavioral monitoring identifies suspicious, bot-like behavior and locks cybercriminals out before an attacker gains access to the account.
Drag & drop MFA with Descope
Not all MFA setups are built the same, and securing them against attacks like prompt bombing takes more than just basic implementation. It requires time, expertise, and the right tools.
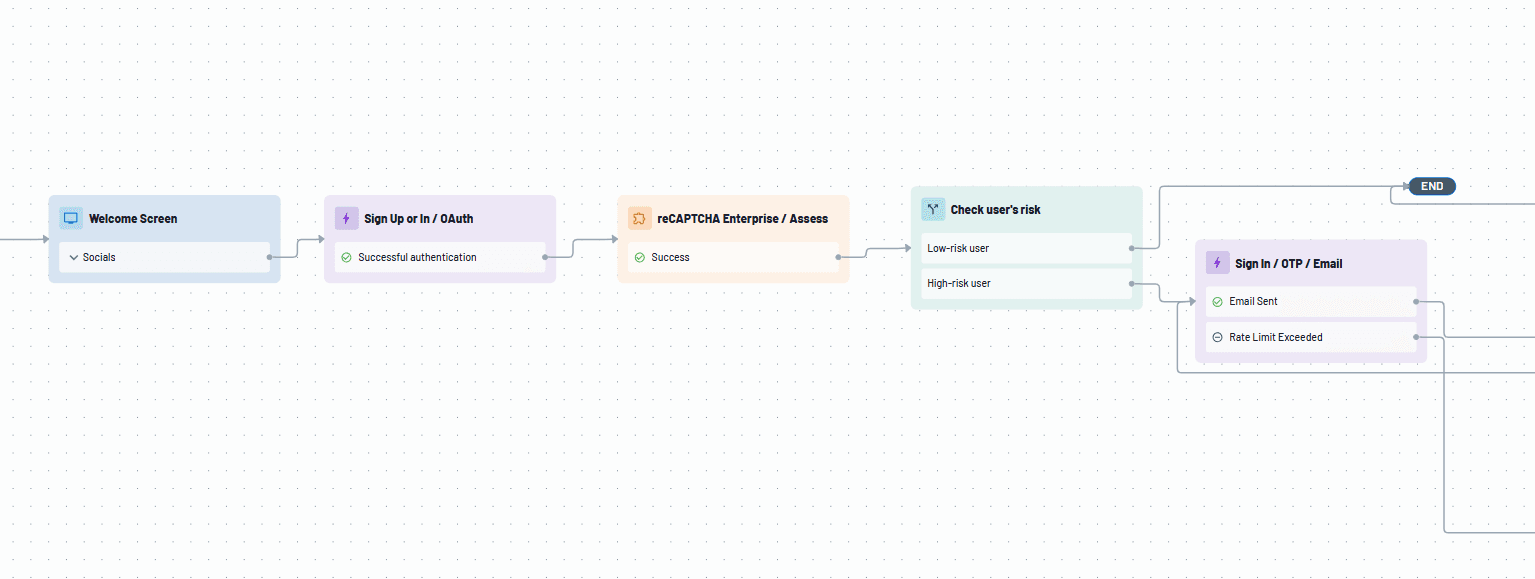
That's where Descope comes in. Our no / low code CIAM platform makes adding robust MFA controls effortless through intuitive visual workflows. Plus, with risk-based MFA, you can customize user journeys based on login attempt risk levels. And with connectors to top-tier fraud prevention systems like reCAPTCHA Enterprise, Fingerprint, and Telesign, you can add extra protection to your user journeys.
Sign up for a Free Forever account to get started with Descope. Have questions about our platform? Book time with our auth experts to learn more.
Sign up for a Free Forever account to get started with Descope. Have questions about our platform? Book time with our auth experts to learn more.





