Table of Contents
Descope Flows and passwords
This blog is the latest the “The Power of Descope Flows” series which covers how our drag-and-drop CIAM platform can be used to add, modify, and update authentication on any app or website. In this blog, we cover how Descope Flows can be used to simplify and secure password-based authentication.
Check out our other "Power of Flows" blogs on user onboarding, enforcing SSO on enabled domains, streamlining in-person event registrations, replacing passwords with passkeys, and securely merging OAuth identities.
Building password authentication in-house is like stacking a house of cards that can come crashing down at any minute. Whether it’s setting up password complexity requirements for better security, creating account recovery flows for forgotten passwords, or dealing with common errors like “user-not-found”, building and maintaining password authentication can eat up developer cycles quickly.
Enter Descope Flows. In this blog, we will share how our drag-and-drop workflow interface helps developers easily implement password authentication in their app.
Note: While we do everything possible to help our users add seamless and secure password authentication to their apps, we cannot do much to counteract the friction and security issues inherent to passwords. If and when possible, we recommend going passwordless.
Descope Flows and passwords
If you already have battle scars from building password auth yourself, you must be searching for an easier way to do things. Here are some ways in which Descope Flows simplifies adding password authentication to your project:
Dev-friendly interface: Our visual workflow interface helps you easily create and customize a password flow for your app without writing custom code.
Future-proof: You can embed a Descope Flow in your app with a few lines of code. Additionally, if you want to make changes to your auth flow in the future, you can just change the Flow and the modifications will be live on your app in real time. No need to redeploy the app or touch your codebase!
Strong and secure passwords: Descope helps you keep your users’ passwords secure with capabilities including password complexity enforcement, password expiration and reuse policies, and connectors with tools like Have I Been Pwned to check for compromised passwords.
User-friendly error handling: Password-based user journeys tend to have some “unhappy” points for end users. Descope helps you easily present friendly screens to end users without giving too much away to attackers.
Fully customizable branding: Our screen editor gives you the power to customize user-facing interfaces with your branding without needing additional work from your design team.
In the rest of the blog, we will dive into examples highlighting all of the above points. Let’s get started!
User onboarding
Compared to passwordless methods, a password-based authentication flow has the potential to cause user friction during first-time visits if not implemented properly. With Descope Flows, you can create a streamlined sign-up-or-in process in a few simple steps.
This process is made even easier by using one of our sample password Flows from Descope Explorer.
Import your chosen password Flow from Descope Explorer.
Customize the layout of user-facing screens to align with your brand.
Connect the main Flow, adjust any error handling, and configure password security requirements.
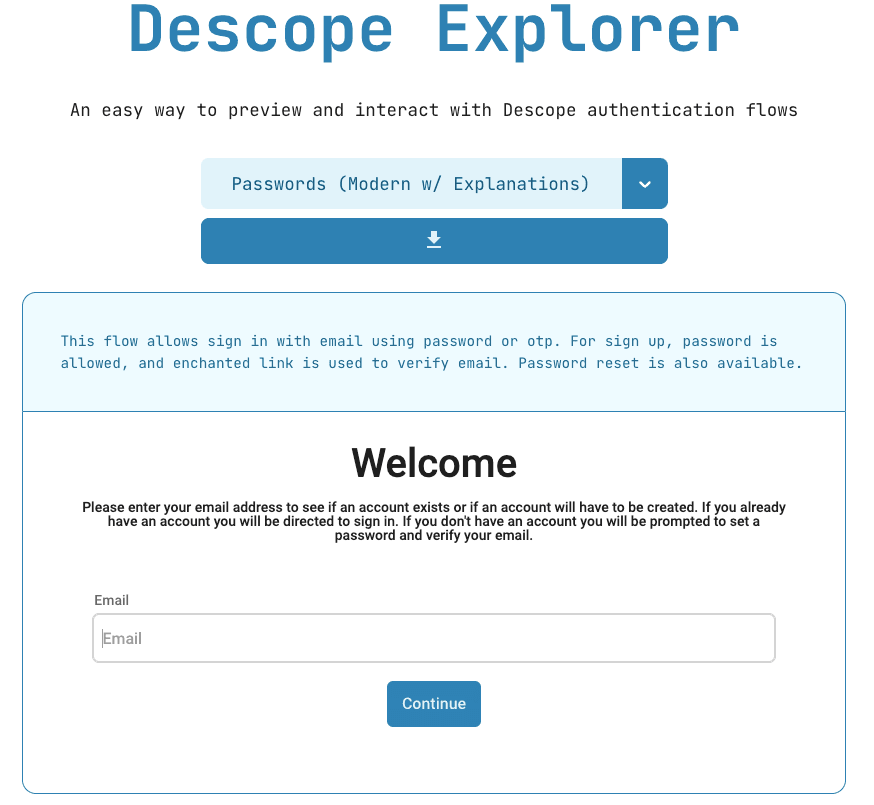
For the purpose of this blog we’ll be looking at the Modern Password Flow with Explanations, which is a more modern approach to sign in or up flows. This approach works by starting only with a user’s email address and directing them to sign in or sign up after checking if their account exists and other considerations.
Users will now be able to create passwords with ease, fostering a positive first impression. Further, the Flow seeks to automatically direct users based on if they already have a valid account or not. Let’s look at the Flow in more detail:
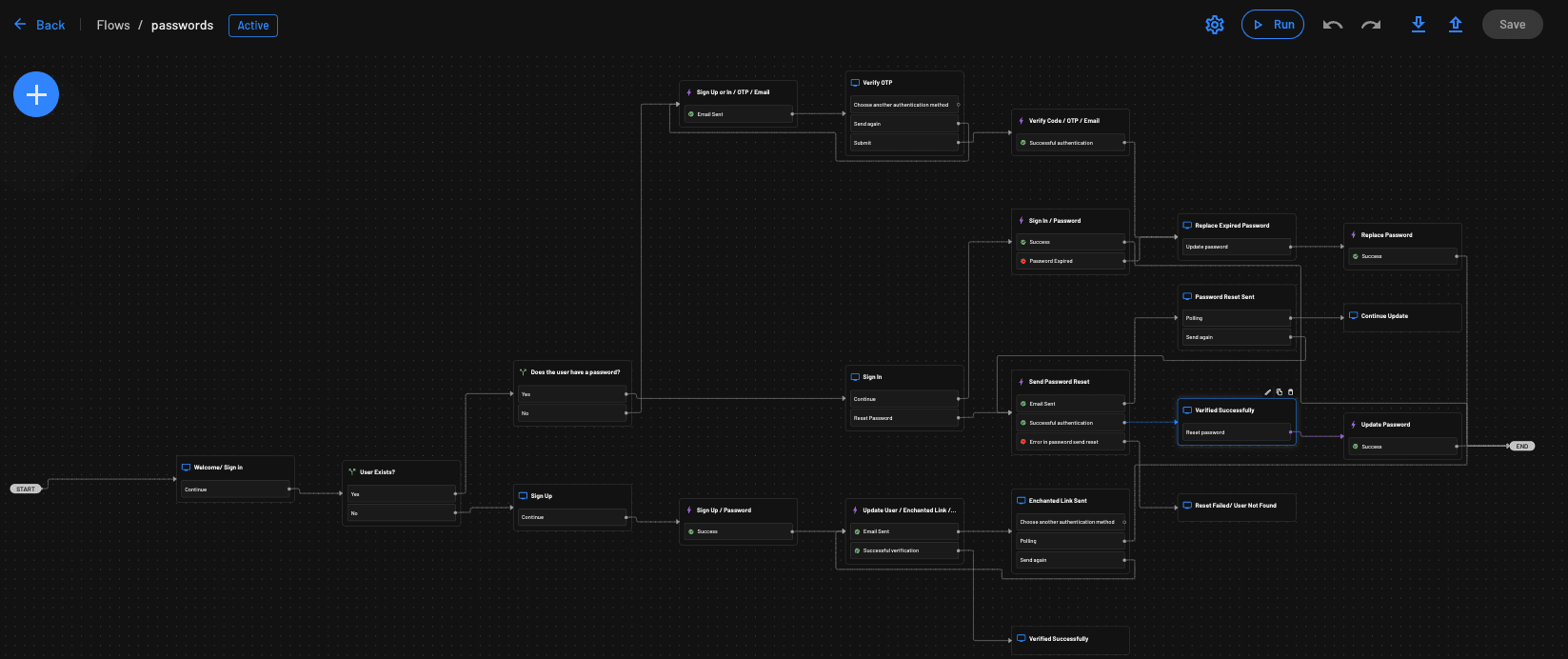
The Flow starts out with a Welcome Screen and prompt asking for the user’s email. The email is checked against existing users to see if the user exists, and if that user doesn’t exist then they are invited to sign up. Sign up is completed by selecting a password (in compliance with the password policy). Their email is confirmed via enchanted link and brought back to the end of the flow.
If the user exists, but does not yet have a password, they will be verified over email / OTP and then brought to a password reset screen to set their password.
Otherwise, if the user does exist and has a password, they continue through the password sign in flow, where they are asked to enter a password. If their password has expired, they are brought to a screen to update their password. If their password is valid, they are brought to the end of the flow and properly authenticated.
Adding password security measures
Descope grants you granular control over several password security measures to achieve a balance between “secure by default” and the right level of security for your app. Whether you want to enforce a policy requiring a mix of uppercase and lowercase characters, numbers, and special characters, mandate certain password lengths, or prevent password reuse, we have you covered.
Let’s start with password complexity. Simply navigate to Authentication Methods > Passwords in the Descope Console, select or specify your required password policies, and save. Now you can ensure a robust and secure password policy aligning with your security standards without trouble.
For more information, check out the Customizing Passwords documentation.
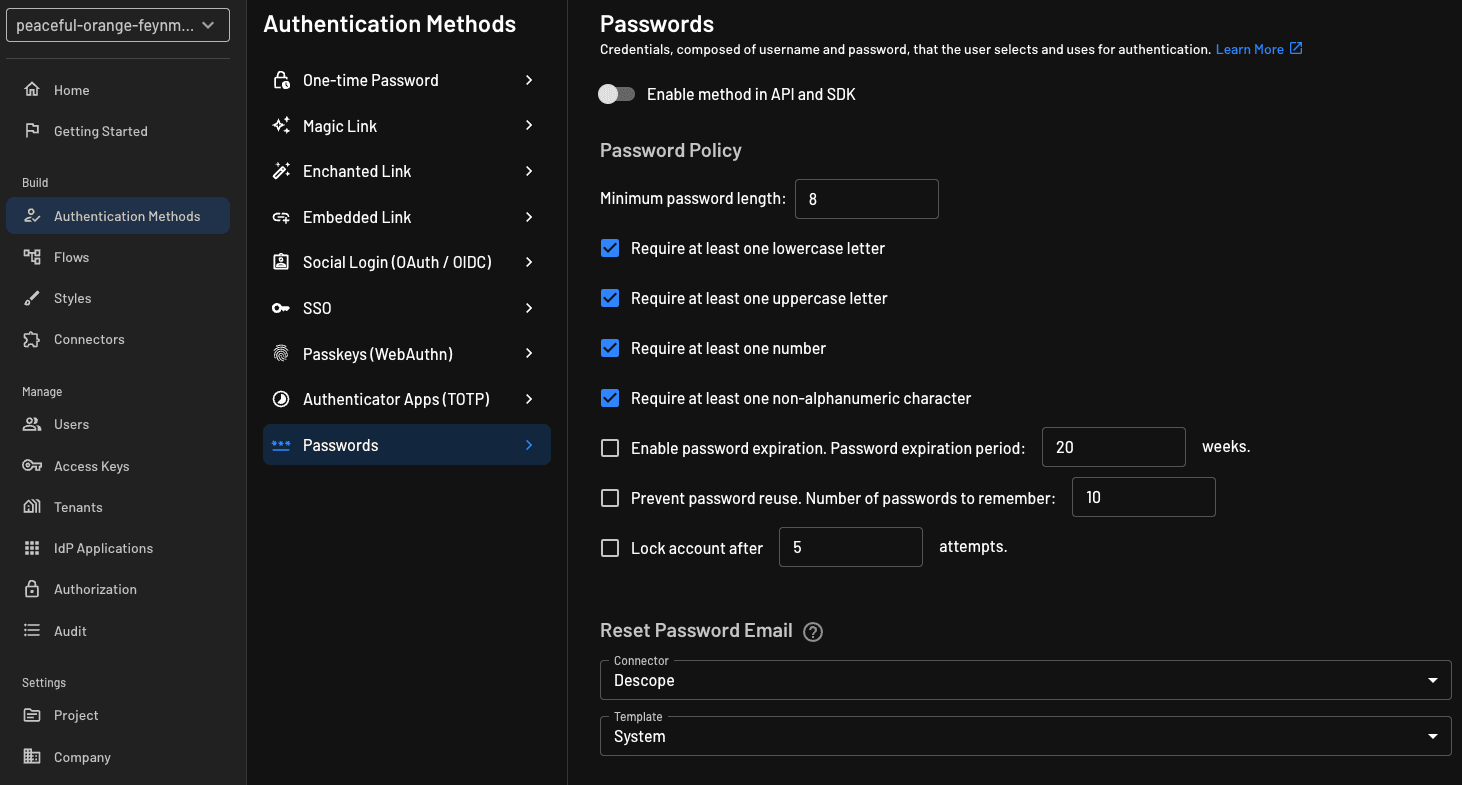
Two other important measures we support are enabling password expiration and preventing password reuse. These features help keep new and unique passwords in rotation and also create a barrier against attacks like credential stuffing and brute force. Configuring password expiration and password reuse policies work similarly to setting complexity requirements. Simply head to Authentication Methods > Passwords in the Console, select and set your policies, and save.
Now users will be prompted to change their passwords at the regular interval you select and won’t be allowed to reuse a certain number of recent passwords according to your set specification.
You can also supplement Descope’s native password security capabilities by using our connector with Have I Been Pwned. This connector cross-references passwords with an extensive database of past breaches, ensuring that your users avoid entering passwords that have been previously compromised.
Password error handling made easy
Providing the right level of information along with errors is critical to maintaining user satisfaction. Descope Flows provide a variety of straightforward ways to deal with potential users errors during password authentication.
Take the scenario of a user entering an incorrect password. You can add a conditional step that checks for an incorrect password and then connect it to a screen block that displays a user-friendly error message and starts a password reset flow. Or take the example Flow snippet found below, in which the user is securely granted access to securely reset their password via a link.
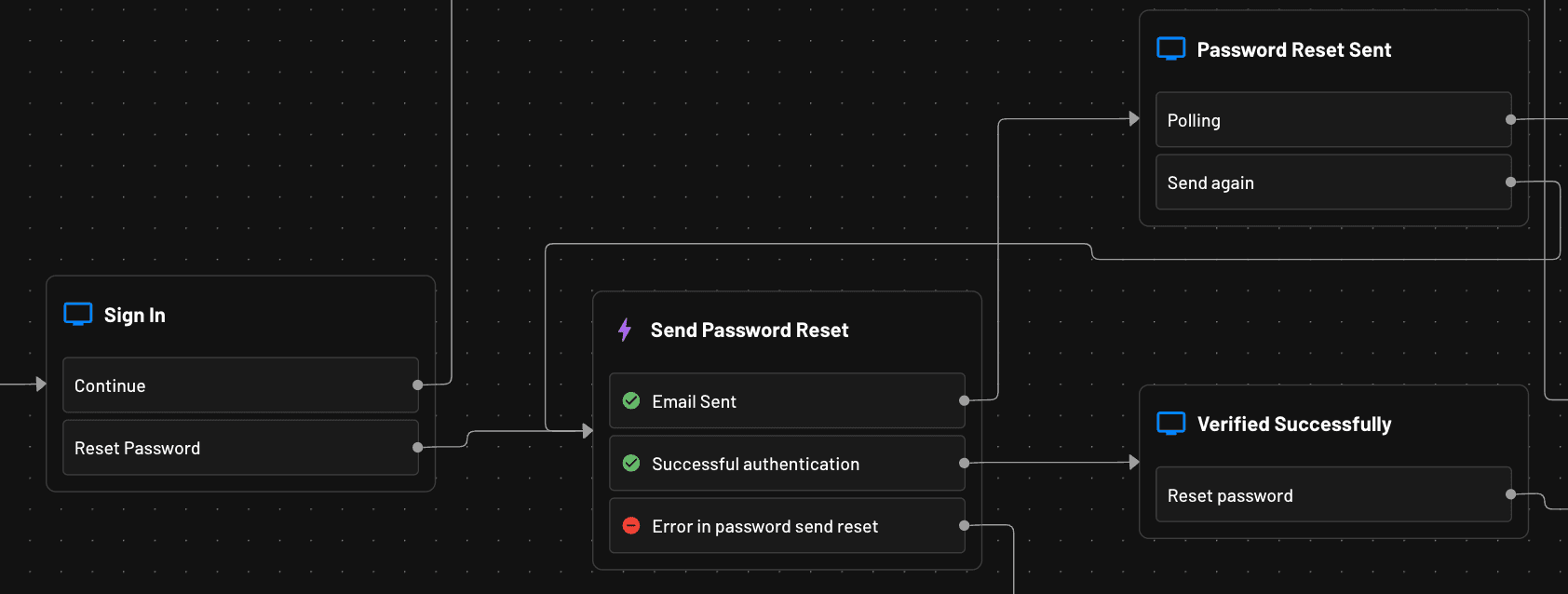
Another common concern is how to handle expired passwords. You can quickly direct a user to a screen that helps them change their password once it has expired. All you have to do is connect the “error handling” step of an expired password state to a screen that will start the replace password Flow.
An easy to implement example of this is found below. Here, if a user’s password is found to be expired during the sign in step, they are simply redirected to update their password.
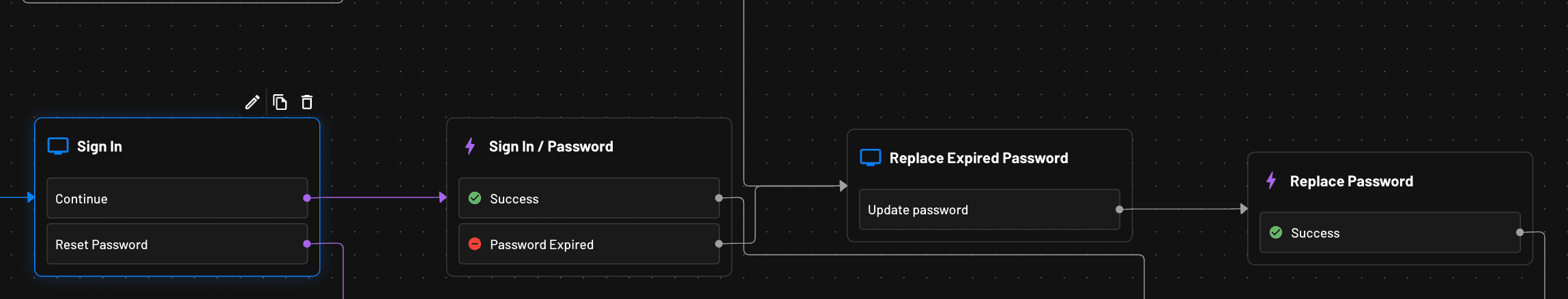
A note on “user not found” errors
Providing helpful error messages to end users is almost always the right way to go. One exception is the “user not found” error, where sharing an error message with too much context can hand valuable information to an attacker.
With Descope Flows, you can display custom error messages that guide real users towards resolution while withholding information from would-be attackers. For example, in the screenshot below, instead of being given information on whether the user account is valid, the user is simply told the password reset failed and that they should contact support.
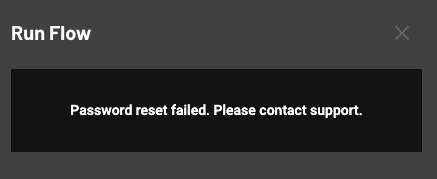
To achieve this with Descope, all you have to do is create a screen with the message that should be displayed and connect that to the main Flow and custom error handling.
Keep your brand yours
A brand is one of the foundational aspects of any business, so we have always put branding control in your hands when it comes to your user journey flows.
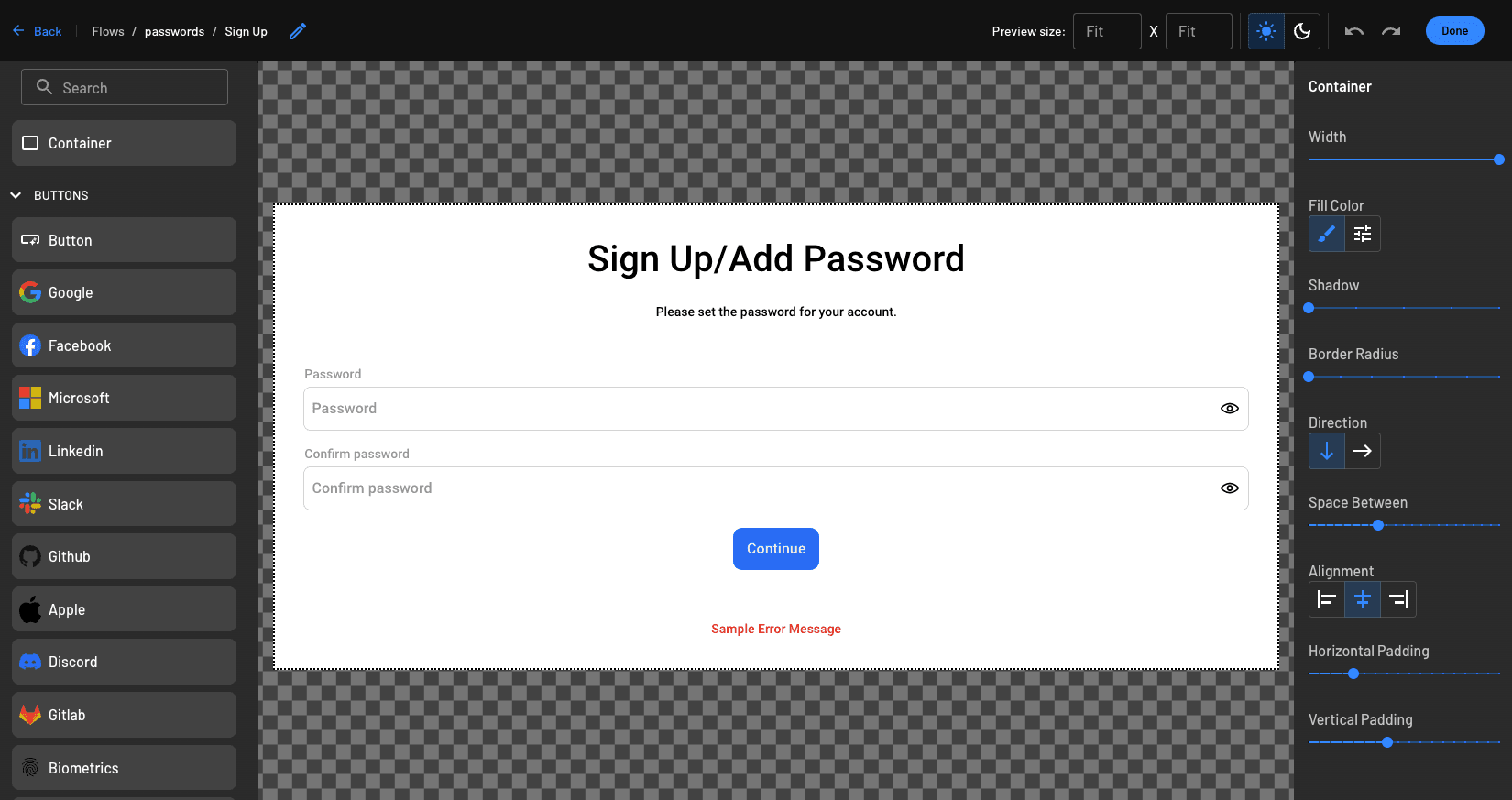
By using our screen editor, you can customize OOTB screens to create fully customized and branded signup / login pages as well as other user-facing screens. This includes the ability to add logos, links, and even granular control over visual elements like the spacing between password character fields.
Watch this video to learn more about how the screen editor works.
Conclusion
In this blog, you learned how Descope Flows simplifies adding secure, user-friendly password authentication to your app.
Our visual no-code editor helps you save coding time without sacrificing any customizability or control. Using branching paths and screens help you reduce friction during onboarding as well as “unhappy” password reset and expiration flows. Password security measures help enforce unique and strong passwords to raise the bar for cybercriminals.
Sign up for a Free Forever Descope account and get started with password auth in minutes. We’d also recommend bookmarking our comprehensive docs portal for detailed guides on different auth methods, tutorials for popular frameworks, and knowledge base articles for popular use cases.
If you have any questions that aren’t answered by our docs, we’d love to have you over at AuthTown, our open community for developers to learn more about authentication. See you in our next Power of Flows blog!