Table of Contents
What is federation and how does it work?
Organizations of all sizes struggle to manage the ballooning number of customer identities across their apps and other digital properties. Identity silos, hard-coded user journeys, and complex identity protocols result in poor user and dev experience as well as potential security gaps.
Two of the more prolific authentication methods that have recently come to the fore to combat this are federated authentication and single sign-on (SSO). Both offer greater security, better user experience, and lower IT support costs than legacy login systems. But the specific ways they achieve those ends differ, as do each approach’s most apt use cases.
Below, we’ll break down the differences of SSO vs. federation and explain when to use each approach.
What is federation and how does it work?
Federation is an authentication method that enables users to access multiple, separate services with a single set of login credentials across different domains or organizations. It’s like a master key that opens doors to different buildings.
Federated authentication relies on creating trust relationships between:
Service providers (SPs) — multiple different organizations i.e. domains
Identity providers (IdPs) — Descope, Google, Okta, etc.
Here's how it works:
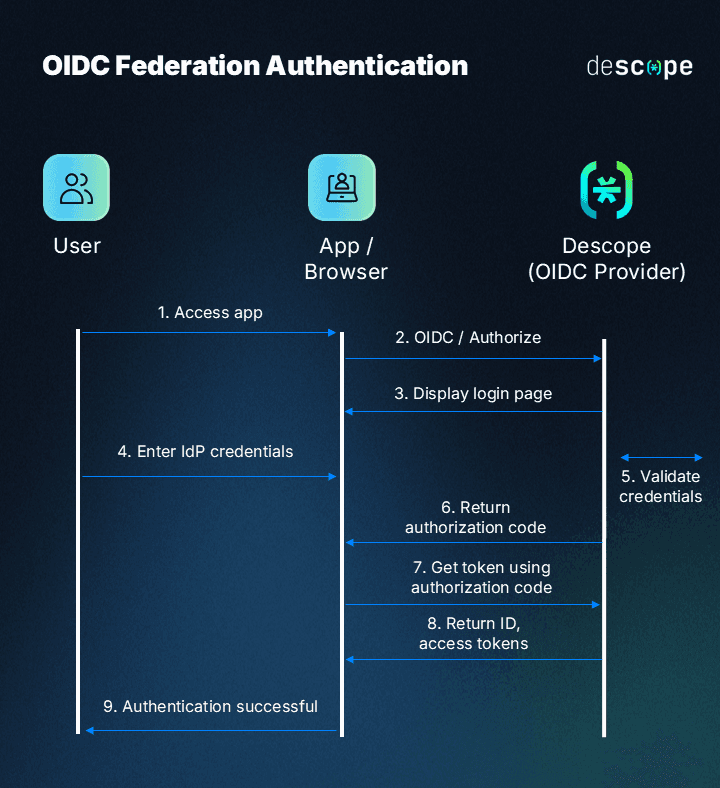
First, the user attempts to log into an app or website that uses federated authentication.
Then, the SP requests authentication from an IdP, typically using a protocol like Security Assertion Markup Language (SAML), Open Authorization (OAuth), or OpenID Connect (OIDC).
The IdP verifies the user’s identity and notifies the SP.
The user is granted access to the SP app they’re trying to access.
The diagram below shows an example of how OIDC federated authentication works with Descope:
Another term often used interchangeably with federated authentication is federated identity management (FIM). FIM refers to more than the proper authentication process. It broadly encompasses other identity and access management elements, like storage and change management policies governing accounts. For our purposes, fed auth and FIM are the same.
Federated authentication use cases
Enterprise Mobility Management (EMM): Federation allows employees to access various internal tools and platforms securely from any location, supporting remote work and mobile access.
Cross-domain identity management: Organizations with multiple domains or subsidiaries streamline authentication processes across various entities, making it easier for users to access necessary resources without repeated login prompts.
Partnership management: Businesses with partnerships may allow partners’ employees to access shared resources and applications, improving collaboration while maintaining security.
Cloud applications: Many cloud service providers support federated authentication to integrate with enterprise identity management systems, providing secure use of cloud resources without additional login credentials.
What is SSO and how does it work?
SSO is similar to fed auth in that users leverage a single set of credentials to access different applications but typically within the same organization. It’s like a master key that opens doors to different rooms in the same building. For example, logging into Google once grants access to Gmail, Google Drive, YouTube, etc., without further logins.
Usually, SSO works by establishing a centralized database of user credentials and using a secure communication protocol between the user, the applications, and this database. Users authenticate themselves through a single access point, which confirms their identity and grants entry to all associated applications. SSO can be either SP- or IdP-initiated.
Here’s how SSO works using SAML:
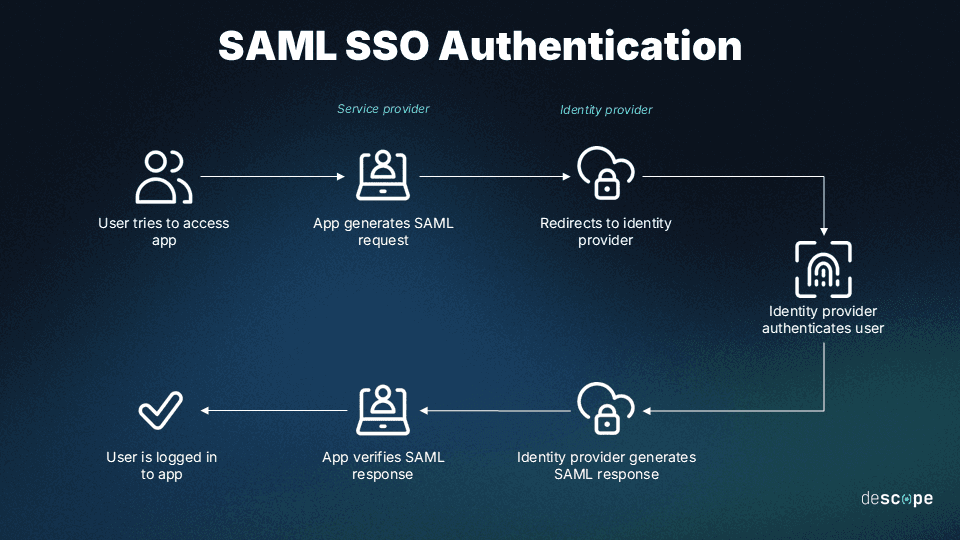
Typical SSO workflows are also slightly different from those in federated authentication. In most SSO scenarios, an employee or customer logs into the SSO platform once, receiving a token that grants them access to connected applications without needing to re-enter their credentials. However, SSO configurations can vary, and additional logins may be required in certain cases. For example, a step-up authentication may be triggered if a user attempts to access sensitive data.
SSO use cases
Enterprises: Large companies implement SSO for seamless access to various internal applications and services, including email, human resources systems, content management systems, and project management tools.
Educational institutions: Universities and schools leverage SSO to offer students and staff easy access to educational resources, library systems, and administrative services.
Healthcare organizations: Hospitals and healthcare providers use SSO to ensure their staff has secure, HIPAA-compliant access to electronic medical records, scheduling systems, and other essential applications.
Government agencies: Certain government agencies have SSO to enable secure and efficient access for citizens or employees to online services and databases, such as those used for license renewals and tax filings.
Ecommerce: Online retail businesses use SSO to manage access to ecommerce platforms, customer databases, supply chain systems, and employee portals.
What is federated SSO?
Beyond the baseline similarities in what SSO and federation provide, there are also many ways in which both approaches can be incorporated simultaneously. Some experts consider federation a means to SSO—or, conversely, see SSO as a kind of federation.
There are also links in terms of how these approaches work in practice. Namely, many SSO deployments rely on pre-existing federations between platforms. Furthermore, the federated single sign-on (SSO) approach routes SSO through federation entirely.
However, in most cases, developers decide between a more external-facing or internal-facing solution—an FIM-based or an SSO-based approach to authentication and identity management.
Read more: Customer IAM in Banking: Considerations & Best Practices
Federation vs. SSO: Differences and relationship
While often used interchangeably, SSO and federation are related but distinct concepts, serving different purposes,
SSO allows users to access multiple applications with one set of credentials, typically within a single organization. Federation extends this concept across multiple organizations, allowing users to access services in other domains with their existing credentials through a trust relationship. In essence, federation encompasses SSO but adds an extra layer of cross-domain authentication and collaboration.
Here’s a breakdown of federation vs. SSO:
| Federation | SSO |
|---|---|---|
Purpose | Allows users from one organization to access applications in another organization without creating new credentials. | Allows users to access multiple applications or services with one set of login credentials. |
Methodology | Each organization (or domain) trusts the other, enabling users to authenticate with their home credentials and gain access to applications in the federated environment. | When a user logs in once, their credentials or session information allows them to access other related applications seamlessly without re-entering their credentials. |
Scope | Meant for sharing and unifying user identities across multiple domains. | Meant for centralizing user access to applications on a single domain. |
User experience | Users can access applications across different organizations using one login | Users log in once and access all connected applications without re-entering credentials |
In practice, federated authentication and SSO are more similar than they are different. Both allow end users to access multiple accounts and platforms by logging in once. The main difference is in how each system achieves that end.
When you should use federation
Federation is ideal when multiple organizations or domains need to provide users with seamless access to shared applications without requiring separate credentials. Common scenarios include partnerships, B2B networks, or ecosystems where users from different organizations regularly interact with each other’s resources—such as universities sharing research tools, healthcare networks accessing patient data across facilities, or suppliers accessing a manufacturer’s inventory system.
Federation enables secure, convenient cross-domain authentication while maintaining each organization’s control over its own identity management system.
In such complex environments, the flexibility of federated authentication can enable organizations to:
Get a more complete picture of their customer identities.
Create personalized user journeys depending on the application and user.
Add bespoke security controls based on the nature of the application.
So, use federation if:
You need to enable access across multiple organizations
You have relationships with external parties
You require cross-domain authentication
You need scalable, secure access across diverse networks
Budget is not a huge consideration
When you should use SSO
SSO is a better solution when you need to streamline access within a single organization or a tightly controlled environment where users need to access multiple internal applications or services. SSO can work with one or multiple identity providers, depending on the use case.
It is particularly useful when you want to enhance user convenience, improve security by reducing password fatigue, and simplify administration.
A related consideration is the scope of your clients. A well-documented challenge facing newer and smaller tech firms is that many larger enterprise clients expect SSO functionality on software produced for them. Specifically, they expect seamless connectivity with their existing SSO deployments. So, if you’re directly developing a project for a larger enterprise client or expect to court them as adopters eventually, you should consider implementing SSO.
So, use SSO if:
Your organization is focused on internal applications
You want to improve user experience
You need centralized access
You’re looking for a cost-effective and efficient access management
No-code federation and SSO with Descope
When it comes to choosing between federation and SSO, the path you choose should align with your goals, whether it's enhanced user experience across disparate apps or enhanced security for sensitive data across your internal apps.
Either way, Descope can help.
Descope is a no-code CIAM platform that helps organizations easily add authentication, authorization, and identity management to their apps using drag & drop workflows.
Customers can use Descope to easily set up both SP- and IdP-initiated SSO, self-service SSO and SCIM setup, and adjacent capabilities such as fine-grained authorization.
By using Descope as an Identity Federation Broker, organizations can connect any combination of client and IdP to unify customer identities across apps. By running workflows to invite users, merge accounts, promote biometrics, and so on, organizations can create custom user journeys for each app depending on the user – all while ensuring that there are no visibility gaps when it comes to customer identities.
Sign up for a Descope Free Forever account to implement federated identity management or SSO for your project in minutes. Have questions about our platform? Book time with our auth experts to learn more about how we can help with your SSO or federation needs.