Table of Contents
IdP-initiated SSO
In an age where the average human interacts with multiple apps a day, single sign-on (SSO) has become a staple form of user authentication. And while the experience is almost always identical for the end users, developers can build SSO workflows within their applications in a couple of ways.
This article explains the differences between IdP- and SP-initiated SSO, their pros and cons, and which one would be the better option for our application.
IdP-initiated SSO
Before delving into the intricacies of IdP-initiated SSO, let's first understand what an Identity Provider (IdP) is. An IdP serves as a central repository for user identities and their credentials. Essentially, it's the gatekeeper that says, "Yes, this person is who they claim to be," granting them access to the app or website at hand.
Now, as the name suggests, IdP-initiated SSO is a workflow where the journey of accessing a service or multiple services begins at the IdP. Here’s how it usually works:
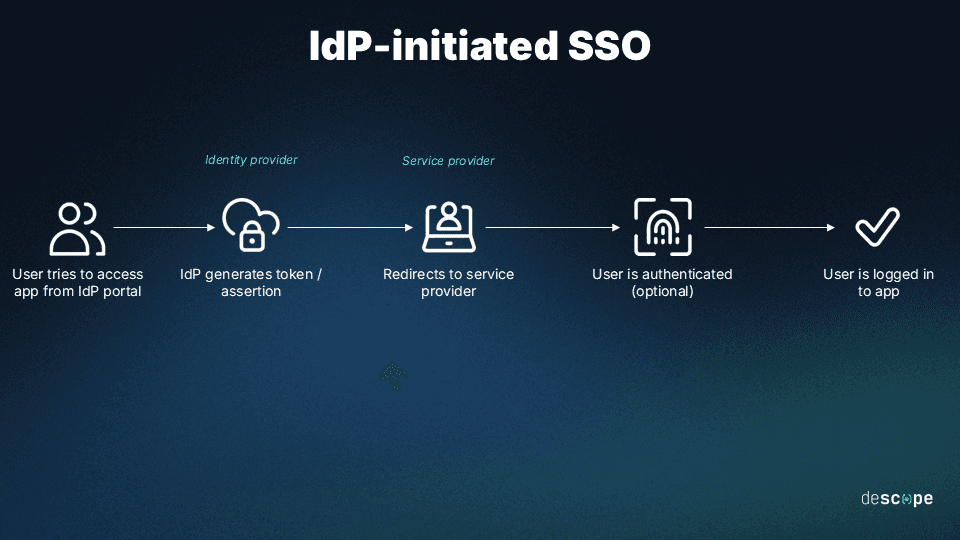
A user logs in to the IdP.
Upon logging in to the IdP, a user is presented with a dashboard of available services.
Selecting a service triggers the IdP to generate a token or SAML assertion with the user's access permissions. Typically, this assertion contains information about the user’s identity, their location, risk level, recent activity, and other similar traits.
This token is then securely communicated to the Service Provider (SP) to determine whether to grant access directly or trigger re-authentication.
Advantages of IdP-initiated SSO
Enhanced user experience: This approach streamlines the login process, allowing users direct access to applications from a single dashboard.
Increased security: IdP-initiated SSO minimizes the attack surface by reducing the number of times a user must enter their credentials.
Centralized authentication control: This method provides organizations with a consolidated view of user activity and access management.
Read more: 6 Benefits of Single Sign-On (SSO)
Disadvantages of IdP-initiated SSO
Dependence on initial login: Users must first access the IdP's portal, which adds an extra step if they want to directly access a specific service.
Potential for phishing: The centralized login interface might make the user’s IdP credentials a target for phishing attacks.
Certain integrations required: Not all services or applications may support the seamless functionality required for IdP-initiated SSO.
By weaving together user-centric convenience and stringent security practices, IdP-initiated SSO offers a robust solution for managing access to multiple services. While it may not be the panacea for all scenarios, its benefits make it an invaluable tool in the appropriate contexts.
SP-initiated SSO
Service Providers (SPs) are the destinations in an SSO process — the websites or applications users wish to access. SPs can’t perform user authentication in this context, so they rely on IdPs for that.
With SP-initiated SSO, the process kicks off when the user attempts to access a protected service, without first authenticating through the SSO platform. Here’s how it works:
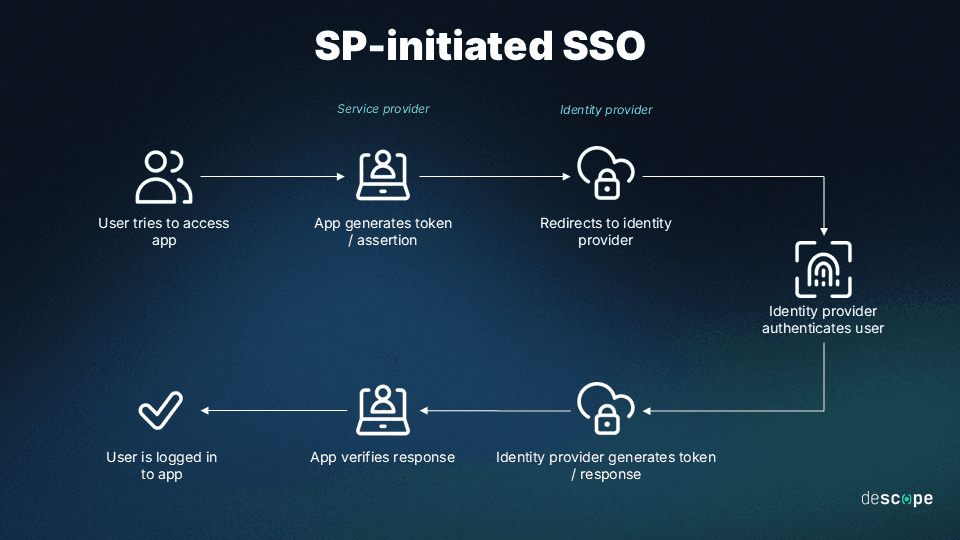
User attempts to log in.
The SP, recognizing the user is not yet authenticated, redirects them to the associated IdP.
The user logs in to the IdP, which then sends an assertion back to the SP.
Upon receiving this assertion, the SP reviews it and decides whether or not to grant the user access.
The user is logged in and now has access to the service.
Advantages of SP-initiated SSO
Direct access to services: Users can head straight to the service they need without an intermediate step.
Enhanced security and compliance: By ensuring authentication through a trusted IdP, services can maintain high security standards and compliance.
Flexibility for users: Offers users the choice of services without the need to navigate from a centralized dashboard.
Disadvantages of SP-initiated SSO
User experience variability: The need to be redirected for authentication can disrupt the user experience, especially if not seamlessly integrated.
Initial setup complexity: Requires careful coordination between SP and IdP to ensure a smooth authentication flow.
Varying levels of support: Some IdPs may not support all the nuances of SP-initiated SSO, leading to compatibility challenges.
IdP- vs SP-initiated SSO
The choice between IdP- and SP-initiated SSO hinges on your specific needs for security, user experience, and administrative ease. Both approaches aim to streamline access and enhance security, but their effectiveness can vary based on your operational context and how users engage with your services.
Here’s how IdP and SP SSO stack up against one another:
| IdP-initiated SSO | SP-initiated SSO |
|---|---|---|
Initiation Point | Begins at the Identity Provider | Begins at the Service Provider |
User Journey | User logs in to IdP and then selects services to access | User goes directly to SP and is then redirected to IdP for authentication |
User Experience | Streamlined after initial IdP login, good for accessing multiple services | Direct access to services, minimal initial interruption |
Security | Strong baseline security but select vulnerabilities related to the single point of failure | Has lower phishing risk but requires secure management of redirects |
Best Use Cases | Environments with multiple service access (corporate, educational) | Scenarios needing direct service access (customer-facing platforms) |
When to use IdP-initiated SSO
IdP-initiated SSO is most common in more rigid and formal business environments where users spend the most time in a closely connected group of apps and programs. For example:
Corporate environments: Where employees access a suite of internal and external tools through a corporate portal.
Educational institutions: Allowing staff and students to access a centralized dashboard for resources like email, learning management systems, and library services.
In situations requiring high security: Such as accessing banking or healthcare portals, where a central point of stringent authentication is advantageous.
IdP-initiated SSO is also favored due to its superior compatibility with numerous legacy software systems. It is particularly beneficial in conventional office settings that employ these older platforms.
When to use SP-initiated SSO
SP-initiated SSO is particularly prevalent in dynamic work environments where users frequently interact with a diverse array of mobile, desktop, or cloud apps. Additionally, it proves advantageous in organizations where the technology stack is constantly evolving, with frequent additions and removals of software. This approach leans towards greater adaptability under such conditions. Here are some examples:
Consumer applications: Where users typically visit the service directly, like online shopping or streaming services.
Business-to-business (B2B) services: Enabling employees from different organizations to access shared resources seamlessly.
Scenarios requiring immediate access to specific services: When users need to access a service directly from a link, email, or bookmark, bypassing the need to visit an IdP's portal first.
Another point to note is the potential for boosting the security features of SP-initiated SSO through the integration of additional safeguards, such as multi-factor authentication (MFA). While both SSO and MFA can be implemented in both IdP- and SP-initiated setups, their combination makes more sense with SP-initiated configurations.
When to use both IdP- and SP-initiated SSO
Leveraging both IdP-initiated and SP-initiated SSO approaches within the same environment can optimize user experience and security, though it requires careful consideration of when and how each method is applied. Here’s an overview:
Diverse user base: When you have a diverse range of users (e.g., employees, partners, customers) with varying access needs and behaviors.
Varied access points: In scenarios where some users might benefit from a centralized portal (IdP-initiated) while others require direct access to services (SP-initiated), depending on their roles or the devices they use.
Security and compliance: When your security framework or compliance requirements dictate varying levels of authentication rigor or audit controls for different services or user groups.
Hybrid IT environments: Organizations with both legacy systems that lean towards IdP-initiated SSO and modern, rapidly changing tech stacks that favor SP-initiated SSO.
IdP and SP-initiated SSO with Descope
Choosing between IdP-initiated and SP-initiated and implementing it doesn’t have to be as complex as it sounds. Descope allows organizations the flexibility to tailor their SSO processes to fit diverse needs and scenarios.
Descope’s visual workflow editor makes deploying end-to-end SSO easier than ever. You can deploy IdP- and SP-initiated SSO, enforce SSO for enabled domains during login, and even let tenant admins set up their own SSO and SCIM connections.
Sign up for a Free Forever Descope account or schedule a demo to start your journey toward drag-and-drop SSO.