Table of Contents
What is multi-factor authentication (MFA)?
It’s well known that password-based authentication is vulnerable to human errors, like weak or reused passwords. Yet even a strong password isn’t a guarantee against broken auth, as an attacker can still gain unauthorized access to user accounts by stealing passwords outright. Unfortunately, password theft is more common than people think. Over 720 million credentials were leaked in 2022.
The upside is that secure alternatives or supplements to password authentication are available to app developers. Two of the more common and effective alternative auth methods include multi-factor authentication (MFA) and single sign-on (SSO).
In comparing MFA vs. SSO, it’s clear that both are upgrades over the conventional password-only approach to auth, with subtle differences in how they work.
Let’s unpack which auth approach is right for your next project.
What is multi-factor authentication (MFA)?
Multi-factor authentication is a login method that requires at least two authentication factors or credentials rather than just one. Given how weak passwords can be, logging in should require an additional step in case the user’s password is guessed or stolen.
Types of authentication factors include:
Knowledge factors: Things known to the user (e.g., a password)
Inherence factors: Unique physical aspects about the user (e.g., retinal or fingerprint scans)
Possession factors: A secondary account or device owned by the user (e.g., phone, laptop, email account)
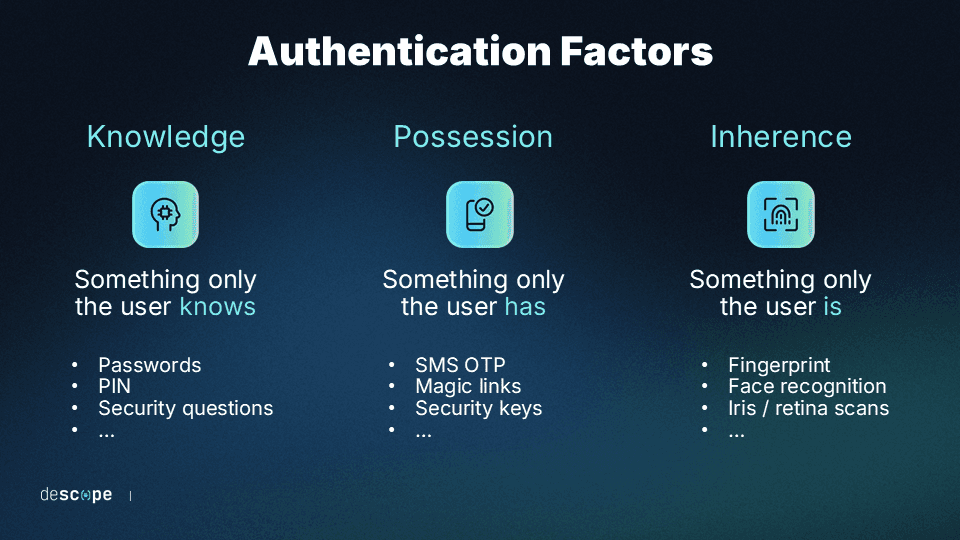
MFA can use multiple factors of the same type, like a password and a security question. Or they can use different types, like a PIN and facial scan.
MFA has been widespread since the 2000s, and most users who have ever forgotten a password know how it works. And while it may be slightly more cumbersome than a conventional single-factor login process, it’s significantly safer.
That said, MFA is not perfect. While some reports from Microsoft and others positioned its threat prevention at 100%, recent scholarship suggests MFA prevents 30-50% of attacks. Attackers have also started employing MFA bypass techniques to take over user accounts by exploiting the gaps in MFA.
Despite its gaps, MFA still provides a significant security upgrade over single-factor login.
What is single sign-on (SSO)?
Single sign-on is an auth method that unifies logins across multiple accounts. First, a user will establish an account with an identity provider (IdP). Then, when attempting to log in to another app or website, it will redirect them to the IdP login. Entering credentials there will generate a token that verifies the user’s identity and logs them in to the target location.
Interestingly, SSO can be considered a type of MFA (the IdP account is essentially a possession factor) and a “zero factor” authentication. Logging in to the apps or websites using SSO requires no unique credentials to memorize (or lose) to use the software in question.
SSO is commonly used in IT environments where many apps, websites, and other digital locations are closely related or share highly sensitive data (or both). For example, government agencies, healthcare providers, and large enterprises often require users to access their accounts through SSO. One login provides access to all software used daily for work.
The centralization of auth in SSO is its most significant benefit -- it makes logging in to connected apps much safer and easier. However, it is also the source of its downsides. These include limited flexibility with non-connected apps and vulnerability if the SSO account itself were compromised.
Comparing MFA vs. SSO: Which is better?
It’s often hard to distinguish auth solutions because they’re closely related or share the same qualities despite surface-level differences. That’s not the case with MFA and SSO, though. Unlike SAML vs. SSO, for example, these protocols are genuinely distinct.
Here’s how they compare:
| MFA | SSO |
|---|---|---|
Methodology | Users provide at least two authentication credentials to gain access to their accounts. | Users sign in to an IdP account that then authenticates them across other accounts. |
Security | MFA is significantly more secure than conventional password logins, but still susceptible to bypass. | SSO is secure but is a single point of failure; if the IdP account is compromised, many others may also be. |
Convenience | MFA adds a step beyond inputting a password but is still relatively seamless. | Logins across connected apps are easy once a user logs into the IdP account. |
Use cases | MFA is applicable in any situation where a single-factor auth method had been used previously. | SSO requires connectivity across apps and is used in healthcare, government, B2B, and enterprise environments. |
Given these differences, choosing between them often depends on your specific use cases.
When to choose MFA as your auth approach
Developers looking to improve their apps’ or websites’ security measures should start with MFA. It is a well-known solution that makes logging in more secure without burdening end users. And, while vulnerabilities still exist with MFA, implementing phishing-resistant MFA strategies will help to mitigate them significantly.
Ultimately, MFA is an excellent baseline upgrade over any single-factor authentication mechanism. When looking for an auth solution, MFA should be one of the first you consider by default.
When to choose SSO as your auth approach
SSO might be the best option if you’re working on an app or website used in an organizational tech stack or in a high-sensitivity environment. In the former case, SSO’s convenience will shine. In the latter, its improved security will be paramount. When SSO is a feasible option, it’s among the best.
Some auth solutions can optimize SSO even further. With Descope’s drag-and-drop workflows, you can automatically detect SSO-ready usernames at login and redirect them to SSO, making it even faster and safer.
That said, SSO is not always feasible. If your software project is niche and unlikely to be used in close conjunction with others, then there’s a chance SSO isn’t your best option. The same holds true if your app is meant for individual consumers rather than businesses.
Simplify your SSO or MFA rollout with Descope
MFA and SSO are improvements on conventional, password-only authentication methods. Incorporating either (or both) into your next software project will be a boon to its adopters and end-users alike. Both offer greater security and a seamless, user-friendly approach to login.
With the overall rise of cybercrime and sophisticated attacks in 2023, finding optimal authentication and authorization solutions has never been more critical. However, implementing MFA or SSO in-house can become complicated quickly, requiring changes to the codebase, reconfiguration efforts, and a deep understanding of auth protocols. For example, it took StackOverflow’s engineering team 3 months to add SSO.
Descope allows developers to add MFA or SSO functionality to their apps and websites with just a few lines of code (or sometimes no code at all). Our drag-and-drop workflows abstract away the complexity of MFA and SSO, handing more time back to developers to focus on core product and business goals.
Sign up for a Free Forever account with Descope to take advantage of optimized, drag-and-drop auth.