Table of Contents
Software experimentations
At fourteen, I wrote my first line of code. From my first print of “Hello World,” technology leaped ahead, with innovations bringing tools and methods to enhance the work of developers like me. The digital wave spared none, and I was carried along with the tide.
Software experimentations
In my high school years, I tinkered with myriad software projects. A calculator for determining the nutritional content of dishes. A web tribute to the great astrophysicist Carl Sagan. A publishing platform designed for the young minds of my high school.
As software engineering evolved, my skills sharpened and my creations gained complexity, morphing into more advanced, engaging, and effective web applications.
My first venture, initiated in the shadow of COVID-19 in March of 2020 with my brother and a friend, was Big & Mini – a digital meeting place that fostered meaningful connections between youth and elders to fight loneliness and bridge generational divides. It found an audience beyond our immediate circle, spanning all fifty states and beyond, even earning coverage on NBC's Today Show, Scientific American, and The New York Times.
The authentication challenge
In creating Big & Mini, we grappled with the intricacies of authentication and user management. A simple, intuitive login system was necessary, but its implementation was far from simple. Decisions had to be made:
Which authentication provider should we rely upon?
How much would it cost?
What security features do we need?
After considerable thought, we chose to handle auth in-house–a decision that proved to be costly. Even though the preliminary setup was straightforward, incorporating all security features was daunting. The vulnerabilities in our system were exposed over the years, resulting in a flood of false submissions and a bill to match from our email service provider.
Yet, we forged on with other projects, developing a messaging service that contributed to reforestation efforts, an artificial intelligence-driven character creation platform, and an app for the curation and sharing of personal favorites, whether it be food, activities, etc.
But irrespective of the project, user authentication remained a consistent burden, offering little to no differentiation from rivals and consuming an inordinate amount of our time.
Discovering Descope
In a TechCrunch article on February 15, 2023, I discovered the launch of Descope. At first, I thought, “Great, another authentication company purporting to save the world.” But my initial cynicism gave way to intrigue as I realized Descope offered what I had been looking for – a means to relinquish the burden of authentication via a simple code snippet.
In essence, Descope was to user authentication and identity what Stripe was to payments: an abstraction to make erstwhile complex operations accessible and swiftly operational.
At once, I signed up.
Auth that’s a peach of cake
Around this time, I had been at The University of Texas at Austin for a couple of years and wanted to make a tangible difference in our community. The juxtaposition of food waste and food insecurity became my focus.
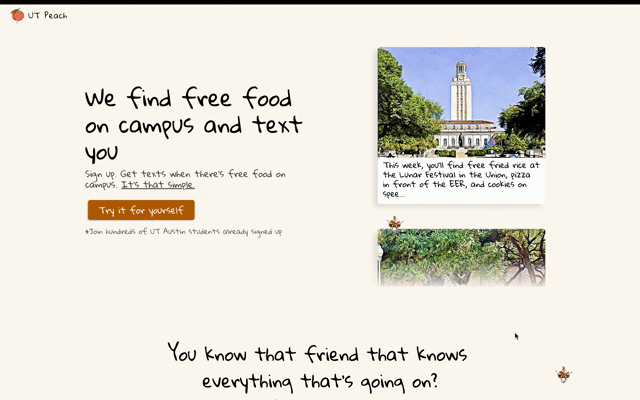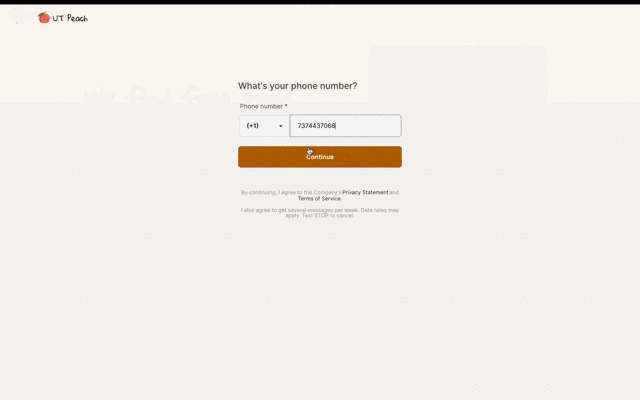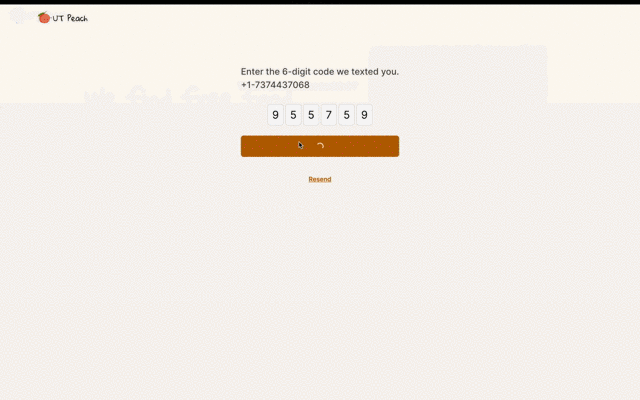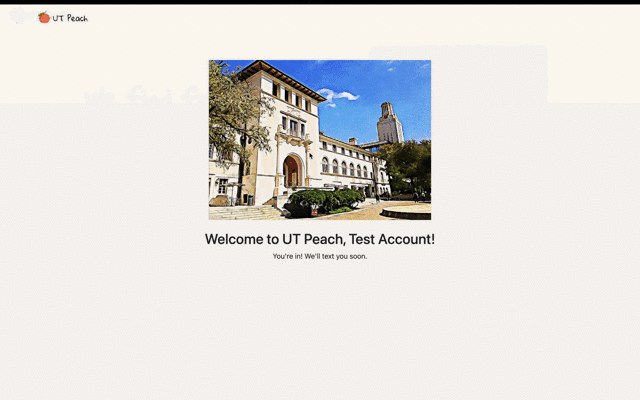
The more I studied, the clearer it became that an information gap was the root cause. How could we bridge the disconnect between available food and those in need? This question led to the conception of UT Peach, a platform connecting college students with free food on campus.
Having purchased the domain, created a promotional site, and linked a database, the final hurdle was authentication.
Descope was put to the test.
Setting up was a breeze, and Descope's Flow Editor caught my attention as a distinguishing factor. In place of laborious code modifications to adjust the authentication flow, Descope offered a simple drag-and-drop solution. Changing from email to SMS authentication and adding username collection would usually be time-consuming, but with Descope, I was done in minutes. The styles were modifiable in the editor, and I could employ my SMS provider, Twilio, at no additional cost.
The application was ready within a few days. Following the tradition of startup launches, we spread the word through physical flyers posted on lampposts, blurbs sent in Discord, and tabling on busy streets filled with students. Before long, users started to register.
Customer service that stands out
Though Descope had simplified the process of setting up authentication, their relentless dedication to customer service also stayed with me. They immediately responded to any queries posted on the Slack community, diligently recorded and valued feedback, and provided support at any time of the day.
Riding the digital tide with Descope
In the battle against the constant tide of technology, finding allies such as Descope can mean the difference between being swept away or riding the wave. The offering they bring and the ease they introduce to a traditionally complex process have profound implications for my work and developers everywhere.
UT Peach, a humble initiative borne out of a need to bridge a gap in our community, found its legs faster than I could have anticipated, primarily due to the support we found in Descope. Their commitment to simplifying and even eliminating the burdensome aspects of software development was, in essence, an echo of our mission—to remove barriers and create connections.
In my journey, I have learned to value those tools that free creators from the mundane, from the necessary but non-differentiating tasks, allowing us instead to focus on the heart of what we're building and on the people we're building it for. Descope embodies that philosophy, making it possible not merely to survive in the digital tide but to thrive, create, and contribute.
Wrap up
Here’s to coding less and creating more; to reducing complexity and increasing connection; to the future and the possibilities that Descope and tools like it hold for us on that bright horizon.
Sign up for Descope and join AuthTown, our open user community for developers to learn more about authentication.