Table of Contents
What is multi-tenancy?
Multi-tenancy is everywhere in modern software, yet it remains one of the most misunderstood concepts today. Whether you’re evaluating vendors, assembling an identity stack, or trying to understand how your existing implementation works, multi-tenancy can directly affect your costs, experience, and compliance.
This beginner-friendly guide will help you understand the standard multi-tenancy models, their key considerations, and how these architectural choices impact your organization.
What is multi-tenancy?
Mutli-tenancy is an architectural model where a single application or service serves multiple discrete groups of users (called “tenants”). Each tenant’s data, configurations, and experiences are logically separated, but they share infrastructure (e.g., servers and the hardware that runs them) and application code. Even though their resources are pooled together, they operate in isolation from one another to varying degrees.
Here’s a simple analogy to visualize it: Picture an office building that rents space to multiple companies. All companies in the building utilize the same underlying resources: elevators, air conditioning, power, security staff, maybe even internet bandwidth or shared dining areas. However, each company is still its own distinct business with separate employees, customers, and products of their own.
Jumping back to a more technological definition, multi-tenancy basically means:
Different organizations use the same software platform
Their data and configurations remain completely separate
They share underlying infrastructure (processing power, memory, bandwidth)
Each organization can only access their own resources
The service provider manages the entire, unified system
Let’s look at an example of how multi-tenancy works: The customer relationship management (CRM) platform Salesforce serves thousands of companies using the same application. While Company A and Company B both use Salesforce CRM, Company A cannot see Company B’s data, configuration, or customers. Both companies access the same application through their web browsers, but their experiences are completely isolated through tenant-specific security controls.
Multi-tenancy operational impacts
A tenant model fundamentally shapes the costs, security, and operational characteristics of modern software platforms. Understanding how multi-tenancy affects your business can help you evaluate vendors, build better services, and make smarter decisions for your users.
Economics and cost
Multi-tenant architecture enables providers to serve exponentially more customers from infrastructure that might only support a handful of single-tenant deployments. Joining as a customer in a multi-tenant cloud typically requires a lower upfront cost than single-tenant deployments because you don’t have to invest in dedicated physical hardware. Recall that multi-tenant architecture shares infrastructure across customers, which means lower operating costs for the service provider, and lower costs for their tenants.
Cost efficiency in multi-tenancy has a significant effect on both providers and customers. Infrastructure overhead often represents a major financial burden for SaaS providers, and providers typically pass at least some of their savings to customers through lower fees.
Security considerations
While sharing infrastructure might seem riskier, multi-tenant systems are designed to be highly resilient and secure, with each tenant’s data isolated from their digital neighbors. However, cross-tenant data leakage is still a potential threat in some implementations. This is a scenario in which one tenant (either maliciously or accidentally) gains access to another tenant’s data. Data isolation failures are relatively rare, but it’s still a concern for organizations beholden to certain regulations or industry standards.
Other security considerations include:
Application-level vulnerabilities (e.g., missing or incorrect tenant ID filtering) that could expose cross-tenant data
Weak partitions, especially in shared models where all the tenants’ data coexists in the same tables
API security gaps, which can serve as entry points for lateral movement if tenants use the same ones
Notably, standard multi-tenant security controls are specifically designed to address these potential problems. These include features like strong authorization (i.e., Role-Based Access Control and Row-Level Security), data isolation, and tenant-specific encryption.
Performance impact
Multi-tenant systems can potentially experience “noisy neighbor” effects when one tenant’s heavy usage impacts the performance for the rest of the tenants sharing the same resources. This is especially relevant in shared database scenarios where a large query from one tenant could slow down operations of others. However, modern multi-tenant architectures typically use load-balancing controls to mitigate or prevent cross-tenant disruption, including strategies like resource quotas or limits, rate limiting, and dynamic allocation.
These methods ensure a single tenant can’t consume more than their allocated share of resources while containing any performance hits to that instance. One implementation pattern called horizontal partitioning or “sharding” is often used to reduce the noisy neighbor effect. Sharding shares the computational load across more hardware, which limits negative performance impacts. Similarly vertical partitioning can reduce load by prioritizing frequently accessed data.
Compliance requirements
Compliance often drives tenancy decisions for organizations in tightly regulated environments. Industries like healthcare (HIPAA), finance (PCI DSS), and government (FedRAMP) may require specific data isolation measures that prefer single-tenant or siloed models. Some regulations mandate physical separation of data, making shared multi-tenant architectures untenable. Others, like the European Union’s GDPR (General Data Protection Regulation), allow logical separation as long as certain controls are in place to ensure privacy for end users.
No matter which regulations affect an organization, it is a joint responsibility between tenant and provider to follow them. Both entities share some liability for the safety of end users: for providers, it is ensuring that infrastructure follows security best practices; for tenants, it is both choosing a compliant environment and safely handling data.
Gartner Buyers Guide for CIAM
Learn common CIAM use cases and recommended evaluation criteria.
Get copy
Tenancy architectural models
Understanding the landscape of modern tenant models is a necessary step in fully grasping what multi-tenancy is all about. The spectrum of tenancy today runs the gamut from complete isolation to fully shared resources, with most real-world organizations using a mixture. Virtually all implementations can be described as one of the following: single-tenant (more isolation), multi-tenant (less isolation), or hybrid models.
Model | Isolation | Performance | Security and compliance | Cost | Best use case |
|---|---|---|---|---|---|
Single-tenant | Highest isolation with dedicated infrastructure; can be physically isolated | Dedicated resources; avoids the “noisy neighbor” effect completely | Complete isolation complies with stricter regulations; eliminates possibility of cross-tenant data leakage | Most expensive; dedicated resources mean higher costs | Regulated industries like government agencies and healthcare providers; companies that crave high performance |
Multi-tenant | Logical separation with shared infrastructure (hardware and software) | Shared resources result in potential performance variability | May not comply with certain regulations; unlikely (but not impossible) chance of data leakage | Lowest; shared costs among all tenants results in lower fees | Most businesses prioritizing cost-effectiveness and simplicity in implementation |
Hybrid | Mix of dedicated and shared resources | Balances cost with isolation needs on a per-service level | May be compliant because critical components are typically isolated; less sensitive services share resources | Variable or medium cost; balances expense with isolation needs | Businesses that can segregate different components with discrete requirements (e.g., user data stores vs. simple microservices) |
Single-tenant
At one end of the spectrum is the single-tenant model, where each customer gets their own dedicated infrastructure. While this can often simply mean per-tenant virtual resources (such as when tenants run on virtual machines), it can also refer to complete physical separation (dedicated hardware). Going back to the office rental analogy, single-tenant configurations are like each company having their own private building.
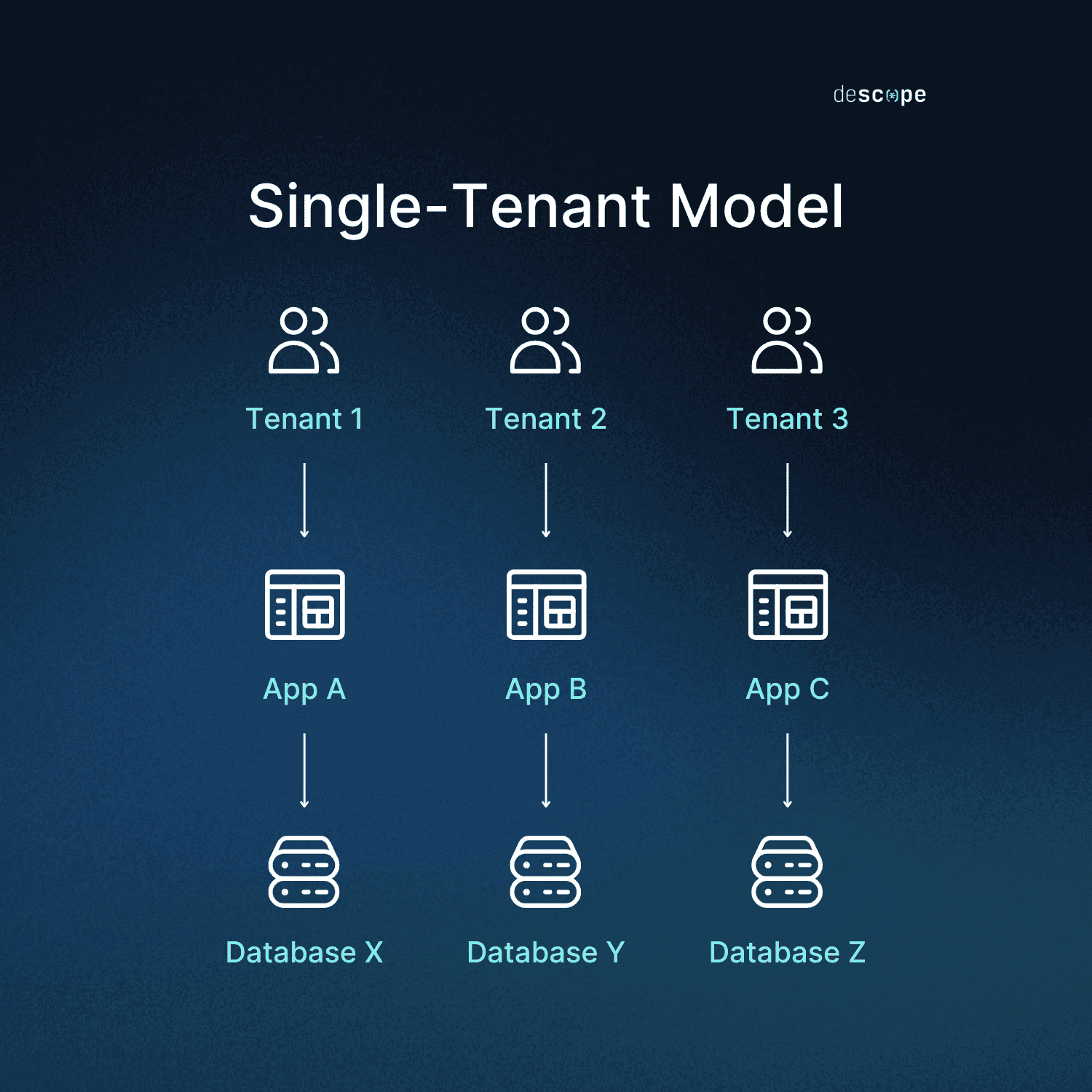
The main elements of the single-tenant model are:
Dedicated resources: Whether virtual or physical, tenants are given isolated resources that are at their complete disposal
High performance: No shared computing resources means maximum performance
Regulatory compliance: Single-tenancy is essentially required by regulations that mandate specific degrees of data isolation
Option of physical separation: A single-tenant approach often goes hand-in-hand with physical isolation from other customers
High cost: Dedicated resources to a single tenant can be expensive, and providers charge more for the exclusivity
The single-tenant model stands out in tightly regulated industries where compliance isn’t optional. A healthcare provider handling personal health information (PHI) might be legally required to use only single-tenant providers for their data. Meanwhile, companies that value speed over cost often look to shave down their transaction times. The difference between shared and dedicated resources can be significant, especially during peak hours.
Multi-tenant
Most SaaS applications live at the opposite end from single-tenancy, sharing resources across hundreds or even thousands of tenants. With this model, isolation occurs through application and server logic rather than infrastructure boundaries. Tenants share computing infrastructure and are often residents of the same physical hardware.
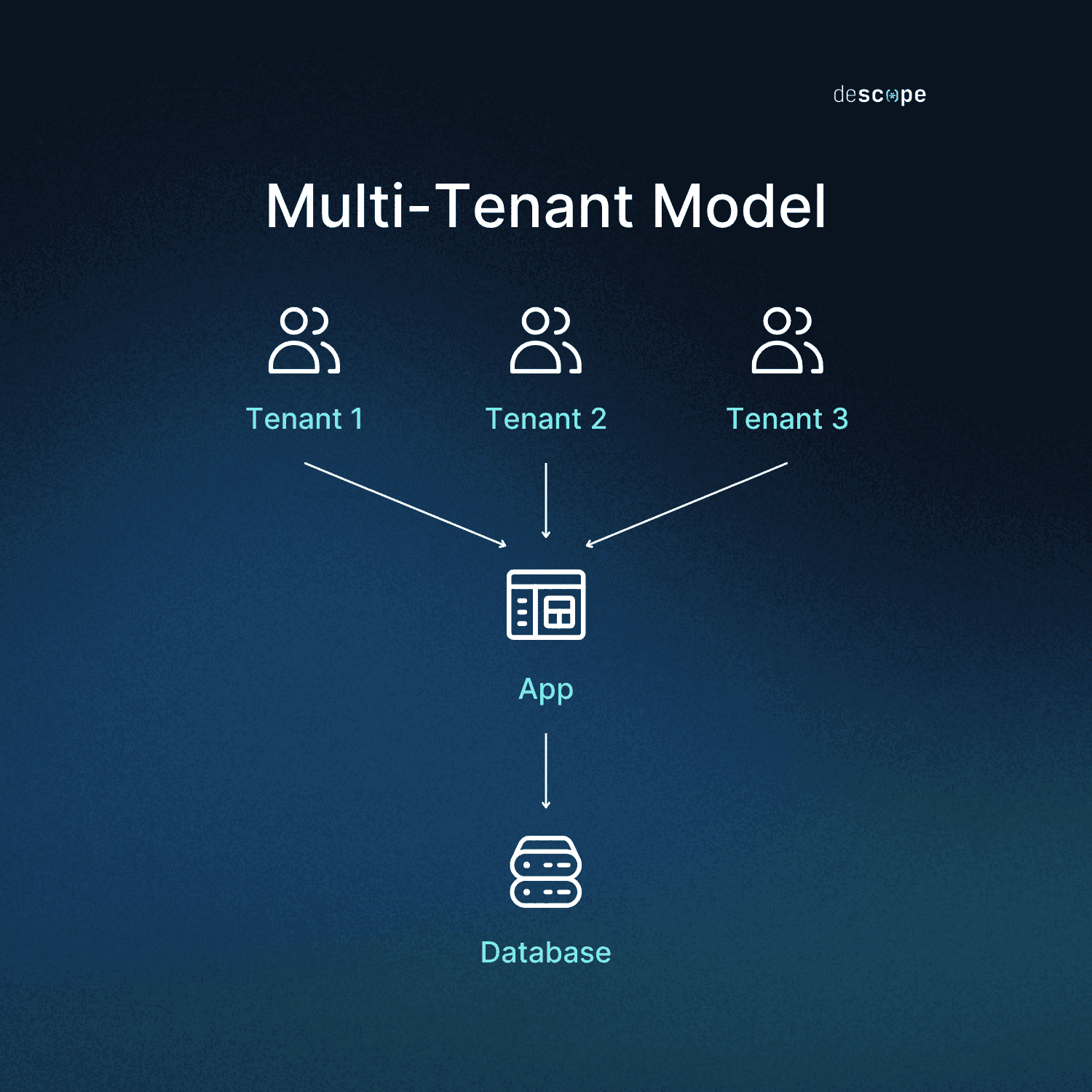
The key characteristics of the multi-tenant models are:
Shared resources: Tenants utilize the same hardware and software infrastructure
Potential performance impact: One tenant’s usage could affect others, though load balancing can mitigate this completely
Security considerations: Some organizations might need specific controls in place to adopt a multi-tenant model, or be unable to due to regulations
Logical separation: While not physically separate, tenants are isolated from each other via software logic
Lower cost: Infrastructure costs are essentially distributed across multiple customers, lessening the financial burden on all tenants
To better understand multi-tenancy, think about how the workplace communication app Slack operates. Countless workspaces share the same infrastructure (cloud storage, servers, bandwidth, etc.) yet each workspace’s messages, uploads, and configurations are separate. This works through elegant data partitioning, where every database query has a tenant ID attached. API calls are validated within tenant’s context including tenant-specific scopes and identifiers.
Hybrid models
Between these two ends of the tenancy spectrum lies the hybrid approach, mixing isolation strategies for different parts of the organization based on individual customer needs, compliance requirements, or technical constraints. For example, a hybrid tenancy model may house some business architecture (like specific microservices) in a single-tenant configuration, while other elements use a multi-tenant configuration.
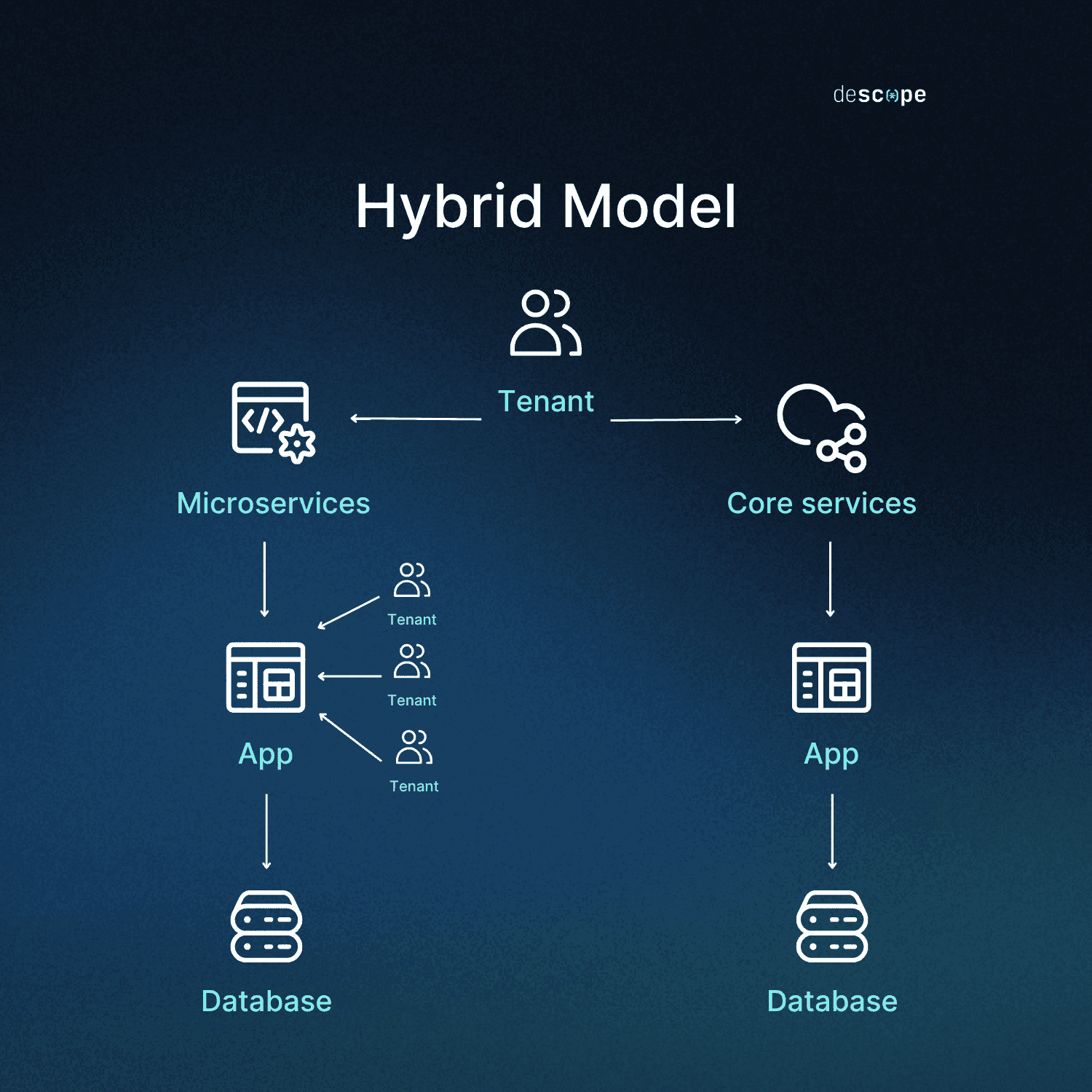
Some hallmarks of hybrid models are:
Varied distribution: In hybrid models, some resources may be shared (like compute infrastructure) while others aren’t (like data storage)
Customer performance: Architecture that doesn’t need blazing-fast speed can be in a shared pool while critical services are single-tenant
Complexity: It’s possible to inadvertently silo systems or services when mixing models, so careful orchestration is required
Selective isolation: While logical separation is standard, customers can choose which business elements receive a single-tenant treatment and which don’t
Cost optimization: Because hybrid models are more granular, companies can achieve their security and performance goals without overspending
The hybrid model is ideal for organizations that can separate their services into various buckets, determining which elements can be safely added to a multi-tenant pool and which require more isolation. Not every organization can break their core components into such groups, but for those that can, hybrid multi-tenancy models can offer significant cost savings.
Multi-tenancy database design
Understanding common implementation patterns in multi-tenancy can help you make better choices when selecting a vendor. The three primary approaches to database design in multi-tenant systems each offer different trade-offs.
Shared database, shared schema: In the first approach, all tenants share the same database and schema, with a tenant identifier column in each table to distinguish between different customers' data. This maximizes resource efficiency but requires careful attention to ensure every query includes proper tenant filtering.
Shared database, separate schema: The second approach uses a shared database but gives each tenant their own schema. This provides better logical separation, as if each tenant has their own set of tables within the same database. While this improves isolation, it can make database maintenance more complex when you need to update table structures across hundreds or thousands of schemas.
Separate databases: The third approach provides each tenant with a completely separate database. This offers maximum isolation and simplifies compliance requirements, but significantly increases operational overhead. Managing thousands of separate databases requires sophisticated automation and can strain database connection resources.
Hybrid approach: The final approach mixes shared and separate databases, much like the hybrid tenant model. Some tenants share a database, while some are isolated. Organizations that use the hybrid tenant model often utilize this approach to database design, but complexity tends to ramp up quickly with many moving parts.
It’s worth noting that all of these database patterns are still under the larger umbrella of multi-tenancy; each of these designs still pools resources between multiple tenants.
Which tenancy model fits your needs?
Choosing the right tenancy model requires systematic evaluation of multiple factors. Below are outlined several considerations to bear in mind when selecting an approach for your organization or customers.
Regulatory compliance requirements are often the primary constraint in tenancy decisions. Different regulations impose different degrees of data isolation. Ensure you’re familiar with which regulations affect your organization, and whether they require specific tenancy configurations (like physical isolation).
Performance expectations: When you’re just starting out, performance may not be as critical to your customers or users. For larger enterprises, however, performance SLAs and avoiding noisy neighbors becomes paramount.
Operational overhead: While most multi-tenant setups are a “no frills” scenario, when implementing strategies like the hybrid model, be aware of your team’s ability to manage both siloed and pooled systems. As complexity increases in your tenant implementation, so does the operational load on your organization.
Growth potential: Future plans for growth should always be an element in vendor selection. Consider whether a provider can scale with your own organization’s growth. If your company starts with multi-tenancy, can you easily move to a single-tenant configuration? What will migration look like? How will costs scale? Would a hybrid model be more efficient?
Getting the most out of your tenant model
As you continue building or refining your application, choosing a tenant model that aligns with your goals becomes key to your organization's success. Exploring the spectrum of options from single-tenant to multi-tenant is all about finding the right balance between isolation, cost, and operational complexity that serves both your business and your customers.
Remember that these decisions aren’t permanent. However, vendor lock-in is absolutely a concern worth navigating. While many successful SaaS companies have migrated between models as their business grew, having a migration plan in place can make the difference between “the next big step” and “mired in tenant limbo.”
Even so, the important thing is choosing an initial approach that supports your immediate needs while keeping a close eye on the horizon. Don’t let the fear of change management lead to analysis paralysis. Tenant models exist to serve customers (like your organization) better, either through cost savings or providing purpose-built digital environments.
Launching or expanding your SaaS application and need auth advice? Connect with the Descope community at AuthTown. Looking to enhance your multi-tenant implementation with enterprise-ready SSO? Reach out to our auth experts to find out how Descope can help, or get started right away by signing up for a Free Forever account.




