Table of Contents
Why session timeouts matter
Every authenticated session has a lifespan, and how you define it determines both the security and usability of your app. Too short, and users get frustrated by constant logouts. Too long, and you increase the risk of token theft or unauthorized access. Striking the right balance requires understanding how session timeouts work and where they fit into your overall authentication flow.
Session timeouts define how long a user or API session can stay active before requiring reauthentication. Configuring them correctly isn’t just about compliance; it’s about balancing security, usability, and system performance across your tenants and auth flows.
This guide will cover:
Why session timeouts matter for compliance, user trust, and data protection.
Different timeout types—idle, absolute, rolling, and hybrid—and where each fits best.
Best practices for implementing secure, context-aware session limits.
Implementation tips to balance UX and security across app tiers and auth flows.
Why session timeouts matter
Session timeouts matter because they prevent and mitigate the risks of unlimited access sessions. They make session hijacking attacks less likely to succeed and minimize the potential impact of successful attacks, reducing the scope and reach of unauthorized access.
Session timeouts are also a critical component of compliance, especially with widely applicable rulesets. For instance, HIPAA requires automatic session expiration after predetermined periods of inactivity per its Technical Safeguards (CFR § 164.312(a)(2)(iii)). Similarly, PCI requires session termination after 15 minutes of inactivity (DSS Requirement 8.1.8). And, while GDPR doesn’t explicitly require session timeouts, it mandates data storage minimization, which prolonged sessions complicate.
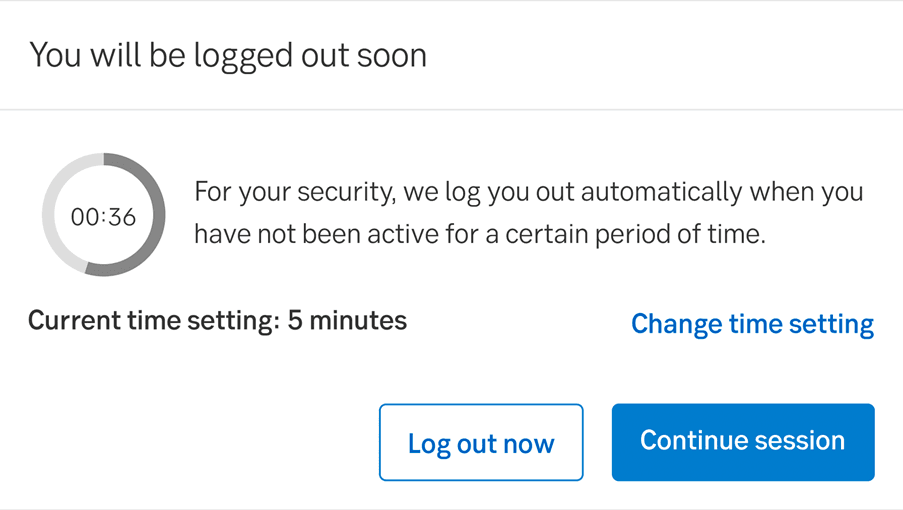
Importantly, security and compliance contribute to user trust and brand reputation. Because an effective session timeout approach makes cyberattacks and infractions less likely, users can trust that their personal information on a platform is safe. Compliance also confirms an organization’s commitment to best practices, providing assurance to potential and existing partners.
Types of session timeouts
Session timeouts come in many different forms, and developers can implement multiple overlapping configurations for maximum coverage. Regardless of the approach, what’s most important is to set a limit on sessions so that inactivity or suspicious activity generally results in access being cut off.
Some of the most common approaches to session timeouts are:
Idle timeout – Sessions are terminated after a period of inactivity (e.g., 15 minutes).
Absolute timeout – Sessions are terminated after set durations, irrespective of activity.
Rolling timeout – Inactive sessions are paused and extended when activity is detected.
Hybrid timeout – Session timeouts are managed using a combination of both idle and absolute timeouts. For example, a session might expire after 30 minutes of continuous inactivity or 8 hours total, whichever comes first.
Understanding best practice: Session timeout configurations
Different session timeout approaches have varying pros and cons depending on the context. You may be obligated to choose a static (absolute) timeout policy for compliance purposes, but non-regulated organizations can aim for more nuanced variations (like rolling and hybrid).
Choosing the shortest session expiration window possible (while balancing user experience) can help you mitigate threats like session fixation attacks, which target vulnerabilities within a user’s browser to hijack access.
Beyond implementing baseline configurations, dev teams can tailor their session timeout settings based on context rather than applying a single duration across all scenarios. For example, in the AWS Console, some user roles can safely remain active for hours while users browse resources and configurations.
Users with access to sensitive data like billing details or root account settings should be on stricter, shorter session durations. As Amazon notes in their documentation, “As a security best practice, we recommend that you do not set the session duration length longer than is needed to perform the role.”
On another level, developers need to consider UX and potential friction points that can come from session timeouts. The appropriate balance between security and usability varies significantly by industry. Financial and healthcare applications typically require stricter timeouts despite potential friction, while retail platforms prioritize seamless experiences.
Another UX feature to consider, with caution, is “remember me.” This works by storing a persistent cookie in the user's browser that enables automatic reauthentication on return visits. However, allowing users to swiftly log back in to platforms they frequent (with the experience of staying logged in) should only be attempted with secure token handling.
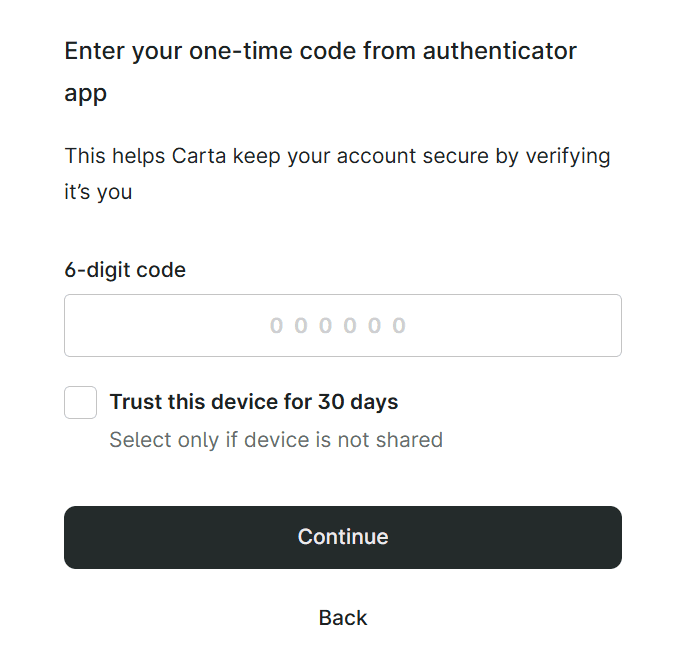
This feature must also align with compliance requirements—for example, organizations handling payment card data or protected health information should avoid “remember me” for any workflows involving regulated data.
Importantly, dev teams should never rely on client-side enforcement alone. Server-side validation ensures security and integrity across access sessions, timeouts, and re-auth.
Implementation tips for developers & IT teams
While the best practices for session timeouts above are aspirational, there are also smaller steps any dev team can take to make effective session controls easier to implement and maintain.
Some essential considerations for effective session timeout management include:
Using secure cookies and being transparent about what data is tracked, why, and how
Validating sessions on the server side to avoid risks inherent to users’ infrastructure
Logging out cleanly with full token invalidation rather than a simple UI redirect
Implementing session management tools for monitoring and risk-based session termination
Regularly auditing session timeout configurations and broader access controls
Another major consideration is implementing a robust, flexible auth solution that can accommodate multiple approaches to session logout along with broader authentication, authorization, and account management for users—ideally in just a few lines of code.
Balancing security and usability
Security is half the battle with session management; UX matters equally. Timeouts that happen too quickly force frequent reauthentication and lead to user frustration. Organizations should set timeout windows that accommodate typical user behavior while maintaining necessary security standards.
One practice for securing sessions without compromising UX is risk-based authentication, which combines factors like device trust, user behavior patterns, and contextual signals to dynamically determine when additional verification is needed.
As noted above, more restrictive controls should be limited to more sensitive use cases to avoid overburdening users in lower-stakes situations. For example, healthcare app users may be more amenable to tighter timeout windows, given the severity of a possible data breach. However, users of a retail store checkout will likely expect a bit more leeway before timing out.
Building secure, reliable session flows
Session timeouts are one of those rare controls that protect both your users and your backend. By combining context-specific limits, secure cookie management, and server-side validation, you can reduce token exposure while maintaining user experience. The key is calibrating your timeout policy to your risk profile—not adopting arbitrary durations.
For teams that want to simplify session management across complex auth flows, Descope offers a straightforward path. With a drag-and-drop interface and a full suite of SDKs, Descope helps developers implement secure, efficient session management without reinventing the wheel.
Sign up for a Free Forever account with Descope and build safer, smarter session flows. Have questions about session management or our platform? Book time with our auth experts.




