Table of Contents
The hidden costs of broken authentication
As we look back on the state of customer authentication in 2025, we see a number of recurring themes:
Organizations know what good identity looks like, but they’re stuck deploying methods they actively dislike
Legacy authentication (username and password) represents a burden that’s tough to walk away from
Passkeys clearly show a way forward, providing much-needed relief from password fatigue
Developer expertise is stretched thin while AI systems multiply the identity challenge
This collection of statistics is drawn from Descope’s State of Customer Identity 2025 report, along with public resources from organizations like Verizon, CrowdStrike, and leading security firms. The data paints a complex picture of companies wrestling with authentication stagnation while racing toward an AI-powered future they’re not prepared to secure.
We’ll also be covering the hopeful avenues forward: how some companies are using passkeys to succeed in this emerging environment, and how you can learn from these trends.
The hidden costs of broken authentication
82% of organizations suffered tangible business impacts from customer authentication issues (Descope State of Customer Identity)

Authentication failures don’t usually stay contained. They ripple out to impact support operations, dev roadmaps, customer trust, and bottom-line revenue. The hidden “auth tax” hits hardest where organizations least expect it: not in high-profile breaches, but in the daily grind of keeping these systems operational.
52% of companies face increased costs to manage support tickets from auth issues
37% delayed engineering roadmaps to address auth gaps
30% saw user dropoff from overly complex onboarding
28% lost customer trust after auth-related security incidents
The reaction to these challenges is often overcorrection. However, too much friction or not enough enforcement can harm trust and the bottom line:
27% of companies lost revenue after implementing stricter customer auth security
39% of companies experienced incidents from lowering customer auth security

Customers are noticing broken authentication, too, and expecting more from their identity experiences.
In 2025, half (48%) of consumers abandoned an online purchase because they forgot their password (FIDO Alliance Consumer Password and Passkey Trends Report 2025)
At the same time, companies are grappling with the costs of account takeover (ATO):
$17B in ATO losses projected for year-end 2025 (Sift Q3 2025 Digital Trust Index)
75% of users abandon a platform after an ATO incident (Sift)
87% spread negative word-of-mouth after an ATO (Sift)
So, why do organizations put up with this as the status quo? The next section begins to tell a complex story about misaligned priorities, and the unfortunate disconnect between knowledge and practice.
State of Customer Identity 2025
Get identity insights from 400+ customer IAM decision-makers.
Get your copy
Authentication stagnation, and why everyone is stuck
87% of organizations still use username/password-based authentication, but only 2% believe it effectively balances security and user experience (Descope Customer State of Customer Identity 2025)

Companies know passwords are a pain to users, destructive to their bottom line, and a security nightmare. But the path from legacy to modern auth feels impossibly steep when you’re barely keeping the lights on for your setup today.
According to the Verizon Data Breach Investigations Report 2025:
Only 3% of compromised passwords met basic complexity requirements
Brute force attacks nearly tripled (20% in 2024 to 60% in 2025) for Basic Web Application Attacks
2.8 billion passwords were posted for sale/free on criminal boards in 2024
22% of breaches began with credential abuse, the top initial vector (more than exploits and phishing)
Consumers are feeling the pain on a personal level. According to the FIDO Alliance, over a third (36%) of consumers had at least one account compromised due to weak/stolen passwords in the last year alone.
When Descope surveyed over 400 CIAM decision-makers, one theme emerged as the clearest example of authentication remorse: knowing better options exist but being unable to escape earlier choices.
51% of companies currently use workforce IAM solutions for customer auth, but only 8% would choose that approach if starting fresh today (Descope State of Customer Identity).

Here are some of the barriers to auth modernization Descope uncovered:
46% postponed CIAM improvements to deal with other pressures
47% struggle to modernize and stitch together legacy systems
37% believe users are hesitant to adopt newer auth methods
31% lack budget and executive buy-in
Why do the same old attacks keep working, with some even increasing in number and velocity? Perhaps it’s this square-peg-round-hole approach many organizations take with customer authentication, or the misalignment of auth priorities—most likely, it’s both.
Developer expertise and impossible expectations
51% of organizations task developers who have minimal authentication experience to build customer-facing identity systems (Descope State of Customer Identity)

Modern auth is complex and specialized, which typically calls for deep security knowledge that dedicated product developers simply don’t have. Yet organizations consistently ask generalist developers to learn on the job, hoping they’ll master a highly focused domain while shipping product features.
Paradoxically, the very organizations that chose “build” over “buy” are the least likely to invest in the expertise required to ensure its effectiveness:
Among organizations using in-house customer authentication, only 27% have full-time CIAM developers.
50% of those who use open-source CIAM experienced security incidents when relaxing enforcement (vs. 39% with commercial solutions)
51% using open-source reported revenue loss when tightening security controls (vs. 26% with commercial solutions)
So why do companies choose this path when they know it often leads to worse outcomes? The next section sheds some light on their motivations.
The security vs. experience tug-of-war
73% of organizations struggle to find the right balance between security requirements and customer experience (Descope State of Customer Identity)

This year, we saw companies express frustration with what they know and how they actually practice auth implementation. There’s a deep tension at the heart of this disconnect, manifesting as competing priorities across different teams.
When we asked various departments whether they emphasize security, customer experience (CX), or attempt to strike a balance, here’s what we learned:
42% of engineering teams favor security over balance or CX emphasis
36% of identity specialists favor balance, and are the most evenly split between the three choices
39% of security decision-makers favor balance, nearly tied with the 38% of security teams who prefer security emphasis
Fragmented ownership of auth means decisions become tense negotiations between departments owning a fraction of the final solution, each measuring success a little differently. And, as illustrated above, there’s a misalignment of priorities even within individual teams:
64% say developers don’t spend enough time on auth (creating security risks)
36% say developers spend too much time on auth (delaying core features)
The multi-factor authentication gap
Multi-factor authentication (MFA) coverage is at an all-time high, which sounds like a win for security. Unfortunately, companies are deploying MFA only for some applications while leaving others less secure.
94% of organizations have some form of customer MFA, but only 10% offer it across all applications (Descope State of Customer Authentication).

Our take: this is the direct result of competing priorities. MFA is treated like a luxury and not the baseline that it truly is. Meanwhile, more vulnerable MFA methods (like SMS OTPs) are under attack from sophisticated bypass attacks.
The 2025 Verizon Data Breach Investigations Report raised concerns about increasing numbers of such activity:
31% of MFA bypass attacks used token theft (e.g., stealing session cookies)
22% of MFA bypass attacks used MFA interrupts (a.k.a. prompt bombing or MFA fatigue)
9% of MFA bypass attacks used adversary-in-the-middle (AITM) attacks
According to Verizon’s research, however, this isn't a license to drop or lose trust in all MFA. As illustrated in their examination of the high-profile 2024 Snowflake breach, 80% of the accounts involved had prior credential exposure (i.e., leaked passwords).
The attacker in that scenario realized MFA wasn’t enforced at the cloud data provider, exploiting already vulnerable credentials to infiltrate their customers. Snowflake’s breach is hardly an isolated incident, however; many more attacks just like it could have been prevented (or had their impact limited) simply by turning MFA on.
A phishing free-for-all, courtesy of AI
A long-touted “zombie stat” (a figure that’s accepted and repeated ad nauseum in spite of dubious origins) is that 90% of all successful cyberattacks begin with phishing. It’s such a widely believed number that the US Cybersecurity and Infrastructure Security Agency repeats it in their guidance for families, without any sourcing.
In reality, Verizon’s DBIR shows that phishing as an initial access vector (16%) is actually losing out to exploitation of vulnerabilities (20%) and credential abuse (22%)—at least, for the organization-level attacks they examine. But that doesn’t mean phishing is slowing down.
The Interisle Phishing Landscape 2025 Report shows:
1.96M phishing attacks in 2024 (up 182% since 2021)
1.54M unique domains used for phishing attacks (+38% YoY)
37% of the domains used for phishing were registered in bulk (indicating industrial-scale operations)
77% of domains used in attacks were specifically obtained for criminal action
$16.6B in direct US losses in 2024 (+33% YoY)
These numbers, which clearly indicate a rise in phishing attempts, are corroborated by multiple sources:
8.4 out of every 1,000 users clicked a phishing link per month in 2024, nearly triple the previous year’s average (Netskope)
13% increase in phishing attacks from Q1 2025 to Q2, the largest quarterly total since Q2 2023 (Anti-Phishing Working Group)
15.2% increase in phishing emails from March 2025 to September 2025 vs. the previous six months (KnowBe4)
But perhaps the most worrying trend in phishing attacks is the use of AI. Generative AI is making phishing more efficient (meaning it’s easier to produce en masse) and more effective (meaning it has more compelling composition).
The click-through rate for AI-generated phishing emails is 54% vs. 12% for human-written emails (CrowdStrike Global Threat Report).
82% of phishing emails are now created with help from AI (Sift Q2 2025 Digital Trust Index)
40% faster scam generation with AI tools, which can (for example) create much more compelling phishing emails (Sift)
456% increase in reports of GenAI-enabled scams, such as those using deepfakes (TRM Labs, May 2024-April 2025)
441% growth in reports of vishing (voice phishing) between the first and second half of 2024 (CrowdStrike)
70% of users say scams are harder to identify than they used to be (Sift)
78% of users open AI-generated phishing emails, and 21% click on malicious links that attempt to steal credentials (Sift)
Passkeys are finally mainstream
Finally, some good news: passkeys, the FIDO2-based passwordless auth method, are now reaching a critical inflection point.
75% of global consumers are now aware of passkeys, and 28% enable them whenever possible (FIDO Alliance)
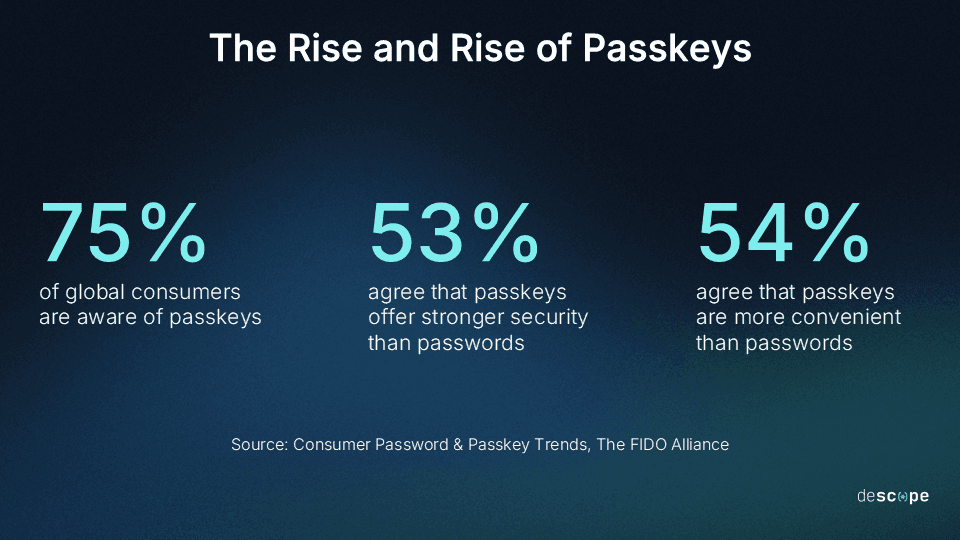
We’re seeing consumer familiarity with passkeys at its historical peak, with the cryptographically secure login method at long last getting the recognition it deserves. Organizations are adopting rapidly (meaning more consumers can opt in), and the passwordless future feels less like science fiction and more like an inevitability.
45% of organizations already have deployed passkeys in one or more applications (Descope)
27% of organizations plan to implement passkeys in the next 2 years (Descope)
38% of the top 100 websites now offer passkeys (more than double since 2022) (FIDO Alliance)
93% of user accounts are eligible for using passkeys (FIDO Alliance Passkey Index 2025)
36% of all accounts have a passkey enrolled (FIDO Alliance)
26% of all sign-ins how use passkeys (FIDO Alliance)
Passkey authentications observed by Dashlane have doubled from 2024 to 2025 to 1.3 million per month (Dashlane Passkey Power 20)
The momentum originates mainly from platform adoption, and sometimes elimination of other options. For example, Google made passkeys default for personal accounts in October 2023. Microsoft made them default in May 2025, later seeing a 120% growth in passkey use (Dashlane). But the benefits are worthwhile, according to Microsoft’s report from late 2024: passkeys users sign in faster (8x vs. password and MFA) and more successfully (98% vs. 32%).
Other organizations are also realizing passkeys aren’t just a fad or luxury. They can improve the user experience and even reduce support overhead:
73% decrease in login time when using passkeys (FIDO Alliance)
8.5 seconds per sign-in with passkeys vs. 31.2 seconds with traditional MFA (4x faster) (FIDO Alliance)
25% improvement in passkey login success rates over passwords at HubSpot (Dashlane)
Passkeys led to 81% reduction in login-related help desk incidents (FIDO Alliance)
Passkeys led to 50% reduction in auth-related support tickets at Branch Insurance (Descope)
Where are passkeys really taking off? Dashlane reports 40% of their users store at least one passkey (up from 20% in 2024). Here’s where they’re using them:
45% of all passkey authentications are ecommerce-related
50% of passkey authentications are from Google
39.9% of passkey authentications belong to Amazon
Roblox has seen an eye-watering 856% increase in passkey authentications over the prior three months
Gemini (the cryptocurrency platform, not the AI model) saw a 269% uptick during the same period
Just as with Google and Microsoft, the Roblox and Gemini explosion in passkey authentications can be easily explained by making it the default. As Dashlane puts it, Roblox went “all in on passkeys, recognizing that its users have something genuinely valuable to protect.” Similarly, in May 2025, Gemini made passkeys the mandatory second factor of MFA.
If you’re still pondering why passkeys are worth it at this point, just remember this number:
301 average passwords managed per person (Dashlane).
Users aren’t just tired of passwords, or merely exhausted by remembering them. They’re completely overwhelmed and incentivized to make them less secure: reusing passwords, constantly relying on resets, and resorting to band-aid fixes. That’s why passkeys matter.
The looming auth crisis of agentic AI
88% of organizations are using or plan to use AI agents, but only 37% have progressed beyond pilot programs (Descope)
Organizations are rushing into AI adoption with auth infrastructure that’s already stretched paper thin. The gulf between AI evangelism and operational readiness is priming a powder keg that’s best understood by the numbers:

95% of organizations believe authentication is critical for AI security
95% of organizations have identity-related concerns about AI agents
57% of organizations worry AI could share data with unauthorized users
57% of organizations worry AI could access information beyond their scope
46% of organizations say engineering teams lack the time/expertise for AI identity
39% of organizations worry users won’t have visibility into what AI does on their behalf
81% of developers have data security and privacy concerns about AI agents (Stack Overflow Developer Survey)
Despite the many apprehensions organizations express about agentic identity security, the outcomes and practices speak for themselves:
21% grant broad data access (scopes) by default to AI systems (Cyera State of AI Data Security Report)
16% treat AI as its own identity class with dedicated policies (Cyera)
9% have actually integrated data security and identity controls for AI (Cyera)
13% have strong visibility into how AI touches their data (Cyera)
66% have caught AI over-accessing sensitive data (Cyera)
97% of organizations that reported an AI-related security incident lacked proper AI access controls (IBM Cost of a Data Breach Report)
Meanwhile, as AI has begun to settle into our technological ecosystem, developer trust is waning. Organizations starting AI deployments see humans as inherently riskier than AI agents (70% vs. 30%). But among those with mature AI deployments, that gap closes significantly (60% vs. 40%), narrowing by 33%.
75.3% of developers surveyed by Stack Overflow don’t trust AI answers
46% of developers actively distrust AI answers
87% of developers are concerned about AI agent accuracy
A 70% positive sentiment toward AI tools in 2023 and 2024 has fallen to 60% in 2025
The pattern is clear: the more companies and developers work with AI, the less they trust it. The only question now is whether organizations will address the novel security challenges AI agents pose, or if the looming crisis will reach its boiling point first.
The state of customer auth in 2025
By the numbers, customer authentication in 2025 is filled with contradictions: Organizations deploy methods they actively dislike (passwords), struggle covering apps with methods they need (MFA), and embrace new technologies they can’t fully trust or secure (agentic AI).
But while the data we’ve covered tells a story of organizational paralysis paired with customer frustration, there’s hope here, too. Passkey adoption is accelerating. Organizations are aware of what needs to be done, and they’re learning from costly mistakes. Consumers are voting with their wallets and showing that auth can be a differentiator and business enabler.
We believe organizations in 2026 will double down on authentication, finally seeing it as a pivotal component of customer experience. They’ll invest in user-centric solutions and shore up gaps that leave identity fragmented. And, hopefully, they’ll recognize that agentic AI deserves its own dedicated identity paradigm—rather than repurposing the same systems that are already stretched to their limits.
For more thoughts on authentication and identity, subscribe to the Descope blog or follow us on LinkedIn.






