Table of Contents
Why organizations seek Akamai Identity Cloud alternatives
Akamai Identity Cloud (formerly Janrain) is a long-standing customer identity platform that many organizations adopted to support social login, profile management, and large-scale consumer authentication. Its enterprise pedigree and integration with Akamai’s broader security portfolio made it a familiar choice for teams operating at global scale. However, Akamai has placed Identity Cloud in maintenance mode with a published end-of-life timeline and no new feature development. That shift fundamentally changes the long-term outlook for teams still running on the platform.
As application requirements evolve, many teams find that Identity Cloud reflects an earlier generation of CIAM design. Implementing modern patterns such as adaptive MFA, passwordless authentication, or flexible identity orchestration often requires significant custom configuration and platform-specific expertise. With feature innovation stopped, organizations face a dual challenge: continuing to support legacy implementations while planning an inevitable migration. Over time, this increases engineering effort, compounds technical debt, and makes everyday changes slower and riskier.
Below, we break down the top reasons teams seek alternatives to Akamai Identity Cloud, followed by a look at the leading options available today.
Why organizations seek Akamai Identity Cloud alternatives
Many teams outgrow Akamai Identity Cloud for a few key reasons:
Sunsetting and roadmap risk: Akamai Identity Cloud is in maintenance mode with a published end-of-life timeline. With feature development stopped, teams face inevitable migration while continuing to carry technical debt.
Limited support for modern CIAM patterns: Adaptive MFA, passwordless authentication, and passkeys are not first-class, composable capabilities. Implementing modern authentication experiences often requires custom configuration or external tooling.
High engineering effort for change: Identity Cloud relies heavily on configuration, rules, and platform-specific constructs. Even small updates to authentication flows can require careful planning, testing, and specialized knowledge.
Weak multi-tenant and B2B support: Identity Cloud was designed primarily for B2C use cases. Supporting B2B, partner, or ecosystem identity requires custom tenant modeling, limited delegated administration, and manual onboarding workflows.
Customization and UX constraints: Branding, embedded authentication, and tailored user experiences are more rigid than modern CIAM platforms, often forcing teams into hosted flows or custom front-end work.
Developer burden for lifecycle automation: User lifecycle workflows such as onboarding, step-up authentication, recovery, and policy changes are not easily automated and typically live in application code.
Operational and support friction: Teams report slower iteration cycles, higher dependency on services and support, and more operational overhead as implementations scale or requirements evolve.
Cost and contract complexity: Long-term contracts, services dependency, and scaling costs can introduce friction, especially when investing in a platform that is no longer evolving.
Momentum shift in the market: With a clear sunset timeline, community attention and innovation have moved toward newer CIAM platforms built for API-first development, orchestration, and rapid iteration.
Each alternative below addresses these gaps differently depending on your technical requirements, ecosystem, and growth stage.
Descope
Overview
Descope is a modern customer and agentic identity platform designed for developers who need secure, flexible authentication without turning identity into a long-term engineering burden. Unlike legacy CIAM platforms such as Akamai Identity Cloud, which are now in maintenance mode and rely on rigid configuration models, Descope delivers a unified, multi-tenant approach built for speed, iteration, and modern identity use cases. It supports customers, partners, and AI agents within a single platform, eliminating the need to stitch together separate tools or identity models.
Descope is particularly well suited for B2C and B2B SaaS applications that require tenant-aware SSO, fine-grained authorization, and rapid evolution of user journeys.
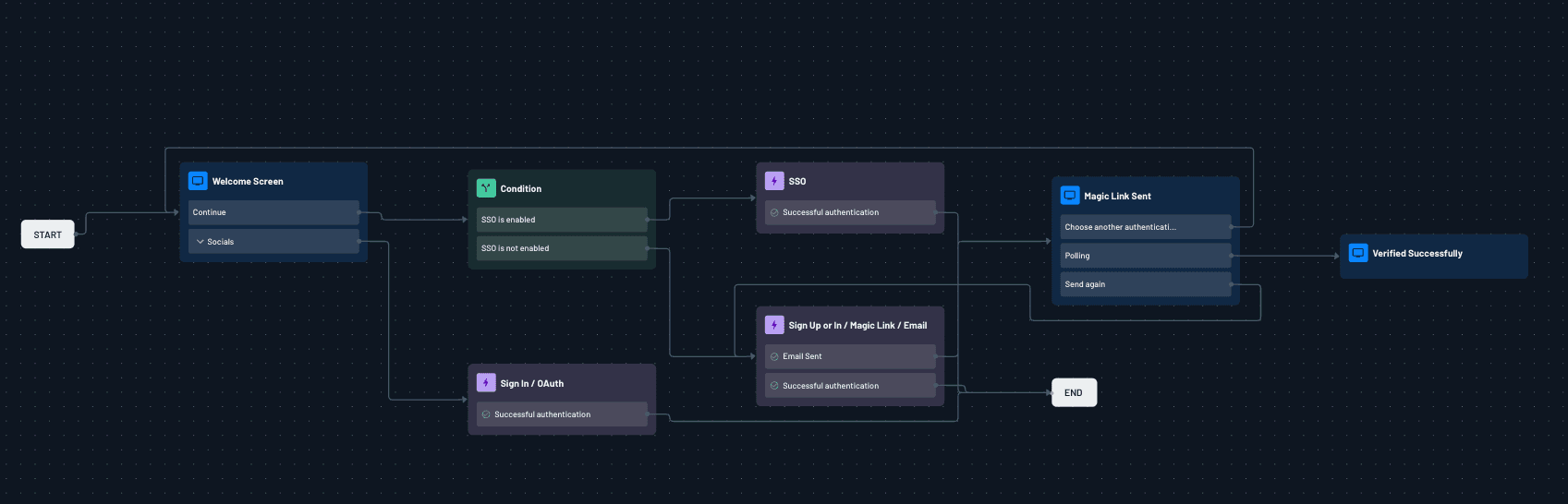
For practitioners familiar with Akamai Identity Cloud’s visual workflow components, the core of Descope’s platform is centered on Descope Flows, a no-code and low-code orchestration layer that allows teams to visually design and modify authentication, MFA, SSO, step-up, and agent authentication flows without rewriting application logic.
Key capabilities
Visual identity orchestration to build and change auth flows without custom engineering.
No / low code workflow editor for login, signup, MFA, SSO, and consent flows.
Unified auth and authorization layer coordinating identity, risk, and fraud decisions centrally.
Built-in modern authentication including passkeys, OTP, magic links, social login, and Google One Tap.
Adaptive MFA, session protection, and bot detection using contextual and risk-based signals.
Native multi-tenant architecture with tenant-aware RBAC and FGA.
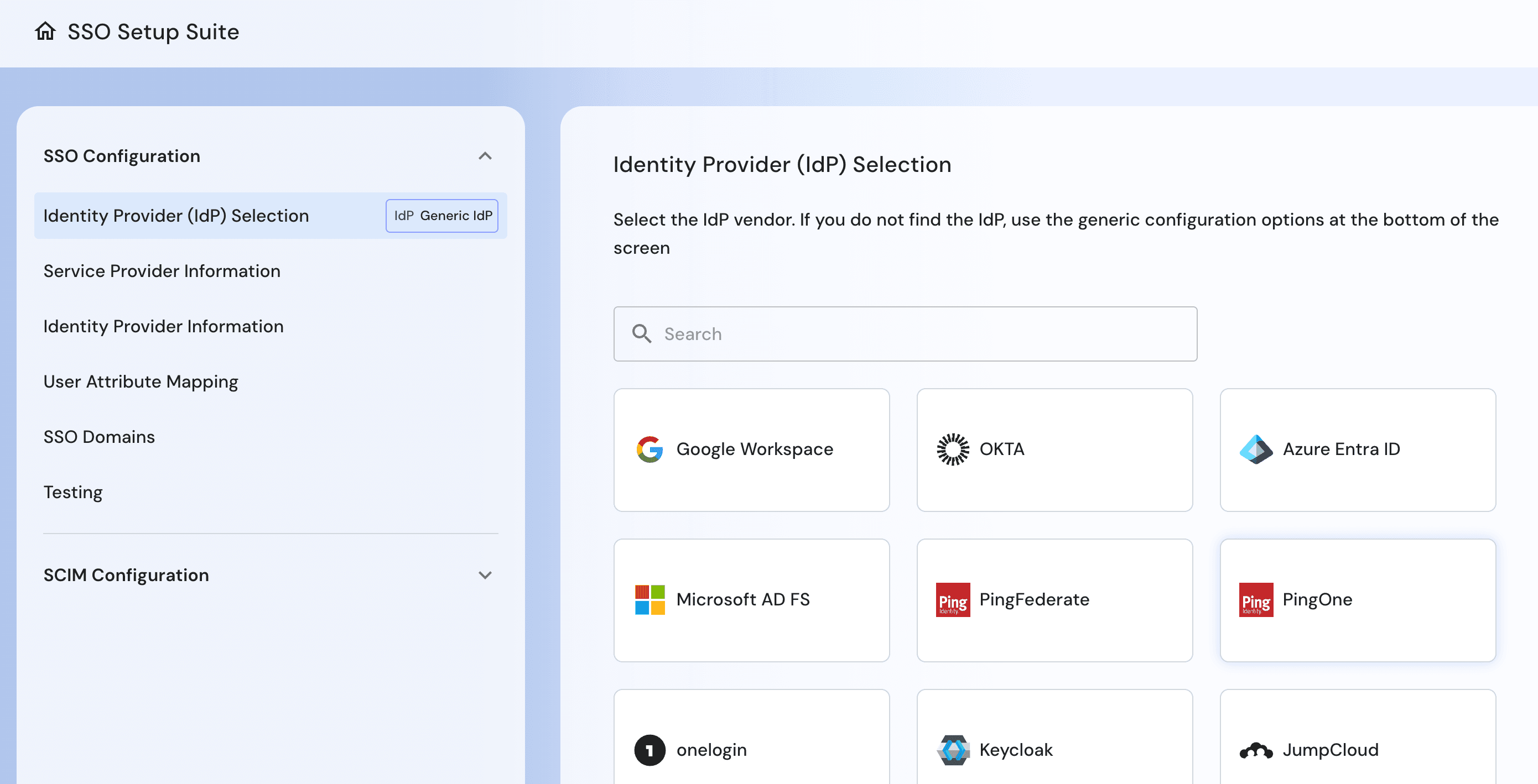
SSO Setup Suite for self-service enterprise SSO and SCIM onboarding and testing.
Extensible connectors ecosystem with 50+ integrations for fraud, risk, and enrichment.
Embeddable, customizable UI components for login, profiles, and admin workflows.
Broad SDK and API support across web, mobile, and backend services.
Anonymous user tracking for early-stage B2C funnel visibility and control.
Agentic identity support for AI agents and MCP-based ecosystems.
Strengths
Modernized enterprise SSO onboarding: Descope streamlines SAML and SCIM setup with guided configuration, self-service tooling, and workflow-based SSO journeys that reduce onboarding friction and services dependency.
End-to-end identity orchestration: Developers can visually design complete authentication, MFA, SSO, and authorization journeys, eliminating brittle, rule-based configurations and custom glue code.
Lower operational overhead: Changes to identity flows can be made safely without redeploying applications, reducing risk and accelerating iteration compared to legacy CIAM platforms.
Unified multi-tenant identity model: Descope natively supports tenant-aware users, roles, permissions, and policies across B2C, B2B, and partner use cases in a single platform.
Passwordless-first experiences: Passkeys, magic links, OTP, and social login are first-class methods that can be added to any flow without complex customization.
Adaptive, risk-based MFA: MFA policies dynamically respond to user context and risk signals, improving security outcomes without introducing unnecessary user friction.
Developer-controlled UX and branding: Teams can choose between hosted components and fully custom UIs, maintaining control over user experience without rigid platform constraints.
Agentic identity readiness: Descope supports secure authentication and authorization for AI agents and MCP servers, enabling organizations to deploy agentic AI systems with identity controls built-in.
Built for modern architectures: With broad SDK and API coverage, Descope integrates cleanly across web, mobile, backend, and agent-driven systems without becoming a long-term bottleneck.
Ideal for
Descope is a strong choice for developers and product teams planning to migrate off Akamai Identity Cloud ahead of its announced end-of-life timeline and feature freeze. It is well suited for B2C and B2B SaaS applications that need tenant-aware SSO, adaptive MFA, and modern identity orchestration without carrying forward legacy complexity.
Descope is also a strong fit for organizations preparing for AI- and MCP-driven architectures, where user consent, delegated trust, and fine-grained access control are critical.
Auth0
Overview
Auth0, part of Okta, is a well-established customer identity platform and a common destination for teams migrating off Akamai Identity Cloud. While Akamai Identity Cloud reflects an earlier generation of CIAM design and is now in maintenance mode, Auth0 offers a more modern, actively developed platform with broad standards support and enterprise-grade capabilities. Auth0 is particularly strong in authentication protocols, enterprise SSO, and extensibility, making it a familiar and trusted option for large organizations.
For teams seeking a stable, mature alternative to Akamai Identity Cloud with ongoing innovation and wide enterprise IdP compatibility, Auth0 remains a popular choice.
Key capabilities
Standards-based SSO with SAML, OIDC, and OAuth 2.0 for enterprise integrations
Comprehensive MFA options including WebAuthn, TOTP, SMS, email, and push
Extensible auth logic using Rules and Actions for custom policies and flows
Hosted and customizable UIs for login, signup, and authentication journeys
Strengths
Broad standards support: Auth0 supports SAML, OIDC, and OAuth 2.0 out of the box, making it easier to integrate with enterprise identity providers than more narrowly scoped platforms like WorkOS.
Flexible extensibility model: Rules and Actions allow teams to implement custom authentication and authorization logic without relying on rigid configuration models found in legacy CIAM platforms such as Akamai Identity Cloud.
Established integration ecosystem: Auth0 offers a large catalog of prebuilt integrations with identity providers, analytics tools, and developer platforms.
Ideal for
Auth0 is well suited for organizations that need a mature, enterprise-ready identity platform with broad protocol support and deep enterprise SSO capabilities. It is a solid choice for organizations modernizing away from Akamai Identity Cloud that want a proven CIAM platform with long-term roadmap stability and wide enterprise compatibility.
Also Read: Why GoodRx Migrated Tens of Millions of Users From Auth0 to Descope
Microsoft Entra External ID
Overview
Microsoft Entra External ID is a cloud-based customer and external identity service designed for organizations that need enterprise-grade security, compliance, and governance for external users.
As Akamai Identity Cloud enters maintenance mode with a defined end-of-life timeline, many enterprises evaluate Entra External ID as a long-term replacement backed by Microsoft’s active roadmap. Entra External ID is built for complex enterprise environments where identity governance, conditional access, and compliance controls are first-class requirements, particularly for organizations already standardized on Microsoft cloud infrastructure.
Key capabilities
Self-service registration and sign-in with social identities and enterprise identity providers
Customizable and branded user journeys for customer and partner-facing applications
Built-in security controls including conditional access, MFA, and risk-based policies
Identity lifecycle management with governance, access reviews, and expiration policies
Strengths
Enterprise governance and compliance: Entra External ID includes native tools for access control, auditing, and identity lifecycle management that align well with regulated enterprise environments.
Microsoft ecosystem integration: Deep integration with Azure, Microsoft 365, and Entra services simplifies operations for organizations already invested in Microsoft infrastructure.
Security-first architecture: Conditional access, MFA, and centralized policy enforcement are built into the platform rather than layered on later.
Ideal for
Microsoft Entra External ID is well suited for large organizations migrating off Akamai Identity Cloud that already rely on Azure, Microsoft 365, or hybrid Microsoft environments.
Amazon Cognito
Overview
Amazon Cognito is Amazon’s fully managed authentication and user management service, commonly evaluated by teams migrating off Akamai Identity Cloud. While Akamai Identity Cloud is now in maintenance mode with a defined end-of-life timeline, Cognito continues to evolve as part of the broader AWS platform. It handles scaling, availability, and infrastructure management automatically, reducing operational risk during and after migration.
Cognito is frequently chosen by teams that want to consolidate customer identity, application infrastructure, and security controls within AWS rather than relying on a standalone CIAM platform.
Key capabilities
Native integration with API Gateway, Lambda, and AWS IAM
Federation support for social login and enterprise identity providers
Managed user pools for authentication, user directories, and token issuance
MFA and adaptive authentication using risk signals and configurable policies
Strengths
Fully managed identity service: Cognito offloads scaling, availability, patching, and operational maintenance, reducing long-term overhead compared to operating a legacy CIAM platform.
Deep AWS-native integration: Tight coupling with AWS services simplifies securing APIs, backend workflows, and service-to-service access.
Proven scalability: Designed to support high-volume consumer applications without requiring custom infrastructure or capacity planning.
Strong security and compliance posture: Benefits from AWS security defaults and compliance certifications, which is attractive for regulated industries.
Ideal for
Amazon Cognito is well suited for teams already invested in AWS that are planning to migrate off Akamai Identity Cloud ahead of its end-of-life timeline. It is a strong option for applications that prioritize backend integration, managed operations, and long-term platform stability over highly customizable authentication journeys or visual orchestration.
Also Read: Why Branch Augmented Amazon Cognito With Descope Passkeys
Keycloak
Overview
Keycloak is a widely adopted open-source identity and access management platform maintained by Red Hat. It provides built-in SSO, identity brokering, user federation, and an administrative console, making it a common option for organizations replacing Akamai Identity Cloud as it approaches end of life.
Unlike Akamai’s hosted, enterprise CIAM model, Keycloak gives teams full ownership of their identity infrastructure. While this comes with increased operational responsibility, it allows organizations to avoid vendor lock-in and support complex federation, policy, and deployment requirements.
Key capabilities
Standards-based SSO using OpenID Connect, OAuth 2.0, and SAML
Identity brokering with social and external identity providers
User federation with LDAP, Active Directory, and other directories
Built-in admin console and user self-service management
Strengths
Full infrastructure control: Open-source architecture enables deep customization and self-hosting, reducing reliance on vendor roadmaps and EOL timelines.
Enterprise federation support: Designed to integrate with legacy identity systems and on-premises directories, supporting complex enterprise environments.
Extensible platform: Plugin model and service provider interfaces allow advanced customization of authentication and policy behavior.
Mature open-source ecosystem: Large community adoption and ongoing contributions provide long-term viability beyond proprietary CIAM platforms.
Ideal for
Keycloak is well suited for organizations migrating off Akamai Identity Cloud that want complete control over their identity stack and are willing to manage infrastructure themselves. It is a strong option for teams with complex federation needs, on-premises requirements, or regulatory constraints that make fully managed CIAM platforms less attractive.
Ory Kratos
Overview
Ory Kratos is an open-source, API-first identity and authentication system designed for teams that want to fully own and control their identity layer. As Akamai Identity Cloud approaches end of life, Ory Kratos is often evaluated by engineering-led organizations that prefer to replace a hosted, enterprise CIAM platform with self-managed identity infrastructure.
Rather than abstracting identity behind managed workflows and configuration, Ory Kratos exposes low-level identity primitives that can be composed into custom architectures. This approach provides maximum flexibility, but shifts responsibility for orchestration, operations, and lifecycle management to the engineering team.
Key capabilities
API-driven identity primitives for authentication, sessions, and user management
Customizable identity flows for login, registration, recovery, and verification
Flexible deployment models supporting self-hosted or managed cloud environments
Composable integration with OAuth 2.0 and authorization services through the Ory ecosystem
Strengths
Full architectural control: Teams can design identity flows, data models, and policies without being constrained by legacy CIAM assumptions or vendor roadmaps.
Open-source transparency: Complete visibility into code and behavior enables auditing, customization, and long-term independence from vendor lock-in.
Composable identity stack: Ory Kratos integrates with other Ory components to support OAuth 2.0, authorization, and access control in modular architectures.
Deployment flexibility: Self-hosting options support strict compliance, data residency, and infrastructure control requirements that hosted CIAM platforms may not satisfy.
Ideal for
Ory Kratos is best suited for experienced engineering teams migrating off Akamai Identity Cloud that want full ownership of their identity stack and are prepared to manage infrastructure and orchestration themselves.
Also Read: Why BalkanID Moved From Ory Kratos to Descope
Conclusion
Akamai Identity Cloud has served many organizations well for large-scale customer identity, but its transition into maintenance mode and published end-of-life timeline change the long-term equation. As identity requirements evolve toward adaptive security, richer user journeys, and multi-tenant B2B use cases, many teams find that extending a legacy CIAM platform increases engineering effort and operational risk.
Among the alternatives, Descope stands out for teams that want to modernize away from Akamai Identity Cloud without carrying forward its constraints. By combining authentication, authorization, enterprise SSO, and visual orchestration in a single platform, Descope reduces custom code and makes identity easier to evolve as products grow.
If you’re evaluating Akamai Identity Cloud alternatives, the right choice depends on how quickly you need to migrate, how much flexibility your identity flows require, and whether your platform must support modern architectures such as B2B ecosystems and AI-driven applications over time.
For more detailed information on Descope, check out our docs. If you'd like a demo, meet with our auth experts. Also, if you want to try Descope yourself, sign up for a Free Forever account and start dragging & dropping your auth today!






