Table of Contents
Why developers seek Auth0 alternatives
Auth0 has long been a go-to choice for developers looking to offload authentication and user management. But as teams scale, priorities evolve, and architectures grow more complex, many developers begin to feel the limitations of Auth0’s platform.
High costs, rigid enterprise support, and the need for constant custom coding often push growing SaaS teams to look elsewhere. Whether it’s a B2B SaaS product needing tenant isolation, a growing bill with each active user, or the need to implement passwordless login without duct-tapping features together, Auth0 may not deliver the flexibility or cost efficiency modern teams expect.
If you're evaluating Auth0 alternatives, you're not alone. This guide will help you find the right fit. We’re covering:
Why developers seek alternatives to Auth0 and what limitations drive that decision
How to evaluate authentication platforms based on flexibility, pricing, and scalability
A side-by-side look at the top 5 Auth0 alternatives
Key takeaways for choosing the best authentication platform for your app
Why developers seek Auth0 alternatives
Many developer teams begin with Auth0 for its convenience, but later outgrow the platform as their app scales and requirements evolve. The shift toward evaluating alternatives to Auth0 usually stems from a few recurring challenges:
Inflexible B2B and multi-tenant support: Auth0’s approach to multi-tenancy often requires custom workarounds or extra infrastructure. Developers end up maintaining complex workarounds to support SSO, roles, and domains across tenants, adding unnecessary friction to deployment.
Build-on-top complexity: Auth0’s platform often forces teams to write and maintain a lot of glue code (custom login UIs, token stitching, extensibility layers) just to get the basics working.
Price creep: Auth0’s pricing structure can jump significantly as usage grows, particularly when advanced features (like SSO or machine-to-machine tokens) are needed.
Limited customization and support responsiveness: Teams report slow responses or limited customization help when running into implementation roadblocks.
In short, as developer priorities shift toward faster builds, passwordless experiences, and flexible B2B identity management, Auth0’s platform can become a constraint rather than a catalyst.
This growing gap is what drives many app builders to explore Auth0 alternatives — platforms that offer modern architectures, better developer control, and predictable pricing.
Each option below is a popular Auth0 alternative, but they differ in strengths depending on your use case.
Descope
Overview
Descope is a modern, developer-first CIAM platform built to help teams add secure authentication and user management without unnecessary complexity. It combines visual workflows, prebuilt UI components, and flexible SDKs that work across B2C, B2B, partner, and agentic AI use cases.
Descope is especially well-suited for multi-tenant SaaS apps, thanks to built-in capabilities for organization management, tenant-specific SSO, and role-based access control. Descope supports identity orchestration for adaptive, context-aware user journeys. In addition, it enables teams to build composable MCP architectures that ensure AI agents get secure, scoped, and consented access.
Key capabilities
Visual workflow editor to create and modify login, signup, and MFA flows
Plug & play connectors ecosystem with dozens of third-party tools
Anonymous user tracking for top-of-funnel B2C user visibility
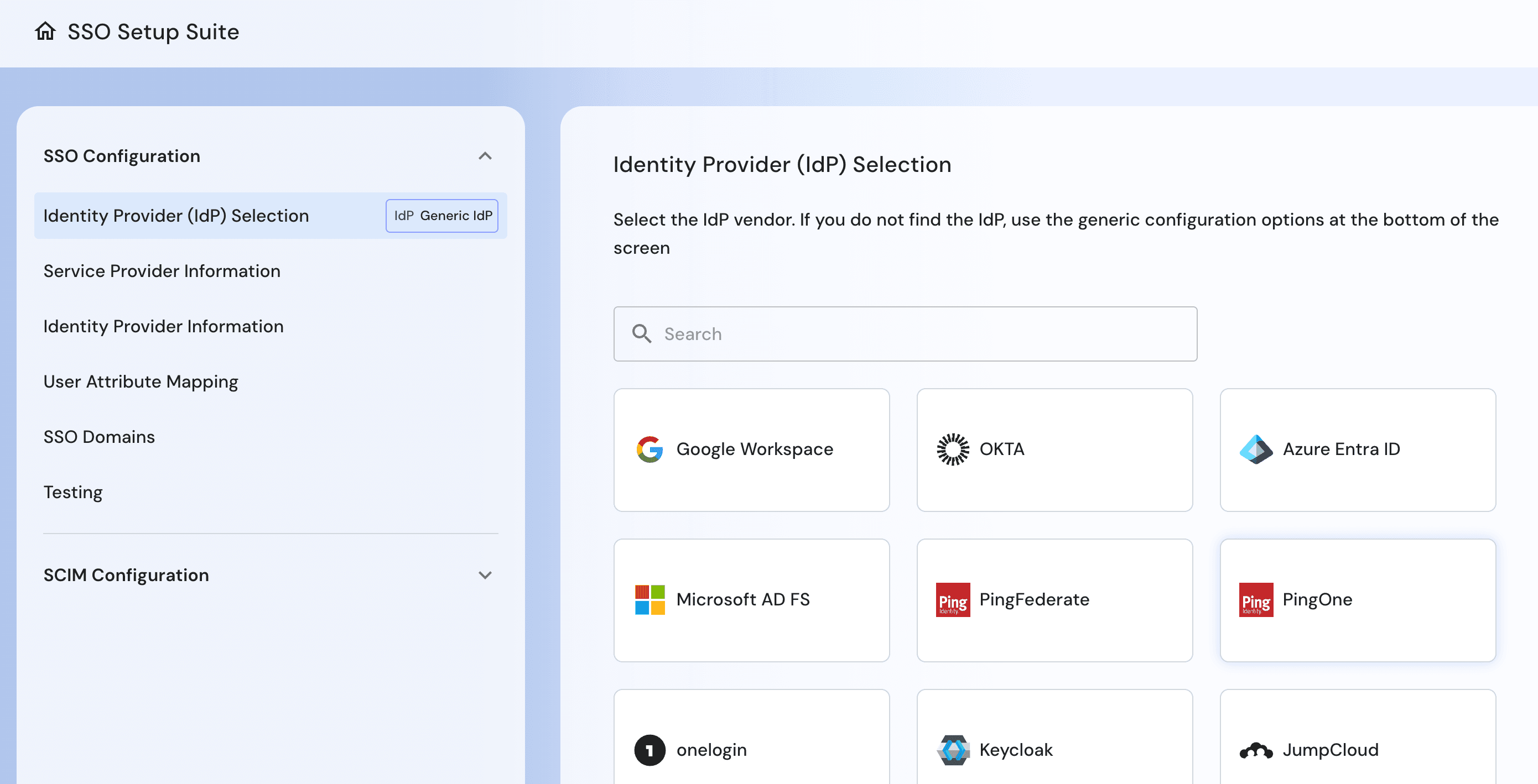
SSO Setup Suite to enable end-to-end SSO and SCIM setup, mapping, and testing
Embeddable UI widgets for self-service identity management and admin
Support for a wide range of auth methods including passkeys, OTP, magic links,social login, and Google One Tap
Support for 15+ web, mobile and backend SDKs and a robust REST API
Identity orchestration across authentication, authorization, risk, and fraud tools
Agentic identity support to get agents enterprise-ready and organizations agent-ready
Strengths
Visual workflows: Descope’s drag & drop editor lets developers design login, signup, MFA, and SSO flows without backend scripting or custom glue code. This simplifies auth implementation and speeds up time to production.
Streamlined SSO: Descope helps developers build and manage SSO journeys with workflows, enable self-service setup, and migrate existing configurations with no disruption.
Passwordless authentication: Descope supports passkeys, magic links, OTP, and social login natively. These methods can be easily added to any flow, reducing reliance on passwords while improving UX and security.
Omnichannel auth flows: Descope provides an easy way to unify authentication flows across web, mobile, and third-party / partner applications while ensuring a native user experience. The same no / low code workflow can be used for auth across apps, resulting in easier modifications and enhancements with time.
Adaptive MFA: Unlike Auth0, where Adaptive MFA is a separate add-on SKU, Descope includes it as a standard feature. MFA can be enforced only when needed using native and third-party risk signals—without overhauling your existing auth systems. You can choose from a wide range of MFA methods and integrate seamlessly into your flows.
Enterprise agent ready: Descope supports secure authentication and access control for agentic AI systems using Inbound Apps, Outbound Apps, and MCP Auth SDKs.
Built for developers: Whether using hosted components or fully custom UIs, Descope gives developers flexibility with SDKs and APIs in React, Node.js, Python, Flutter, and more. The platform fits into any tech stack without locking teams into rigid patterns.
Ideal for
Descope is one of the top Auth0 alternatives for developers seeking a no-code, visual approach to authentication, offering drag-and-drop workflows, passwordless support, and built-in multi-tenant management out of the box. Organizations such as GoodRx, Linktree, Cequence Security, and Pieces have migrated from Auth0 to Descope for better developer and end user experience. It’s perfect for B2B or B2C SaaS teams that want to accelerate time-to-value, reduce dev effort, and scale securely with modern auth practices.
Also read: Detailed Descope vs Auth0 comparison
Amazon Cognito
Overview
Amazon Cognito is AWS’s native authentication and user management service, designed to support secure access control in web and mobile applications. It enables developers to create user pools, handle sign-ups and logins, and manage permissions without building auth from scratch. Cognito is tightly integrated with other AWS services, making it a good choice for teams already operating in the AWS ecosystem.
Key capabilities
Federated identity support with SAML, OIDC, and social providers
User pools for managing and authenticating users
Lambda triggers to customize auth flows
Built-in integration with AWS services like API Gateway and AppSync
Strengths
Deep AWS integration: Cognito works seamlessly with the broader AWS ecosystem, making it easy to connect authentication with services like API Gateway, IAM, and Lambda.
Flexible identity federation: Cognito supports a variety of login methods, including SAML and OIDC, as well as social providers such as Google and Facebook.
Custom logic via Lambda triggers: Developers can insert custom behavior at different points in the auth lifecycle using AWS Lambda.
Ideal for
Amazon Cognito is a reliable Auth0 alternative for teams already using AWS. It’s powerful for serverless apps but less flexible for teams needing custom UIs or simple configuration.
Firebase Authentication
Overview
Firebase Authentication is part of Google's Firebase platform, offering lightweight authentication services for mobile and web apps. It's designed for fast setup and ease of use, especially for small teams and early-stage products. Firebase Authentication supports common authentication methods and integrates seamlessly with other Firebase tools, such as Firestore and Firebase Hosting.
As an Auth0 alternative, Firebase Authentication is best suited for teams that want to get started quickly without managing complex backend infrastructure.
Key capabilities
Prebuilt UI for login and signup flows
Authentication via email/password, social login, phone number, and anonymous users
SDKs for web, Android, iOS, and major frameworks
Integration with other Firebase services like Firestore and Cloud Functions
Strengths
Fast setup and simple integration: Firebase Auth offers a quick path to production with minimal configuration. Developers can enable common login methods in the console and integrate authentication using client-side SDKs.
Mobile-first and cross-platform support: Firebase provides support for Android, iOS, and cross-platform frameworks like Flutter.
Seamless pairing with Firebase tools: Authentication works natively with other Firebase services like Firestore, Realtime Database, and Firebase Hosting, good for teams already building within the Firebase ecosystem.
Ideal for
Firebase Authentication is a strong alternative to Auth0 for startups that prioritize ease of setup, mobile-first support, and Google ecosystem integration, but it may lack the flexibility needed for enterprise use cases.
Keycloak
Overview
Keycloak is an open-source identity and access management solution maintained by Red Hat. It provides enterprise-grade support for authentication, authorization, and user federation across applications and services. Keycloak offers full control over login flows, user management, and identity provider integration, making it a popular choice for organizations that require self-hosting, protocol flexibility, and deep customization.
For teams researching open-source Auth0 alternatives, Keycloak stands out as one of the most established and flexible options, especially for those comfortable with self-hosting and DevOps management.
Key capabilities
Native support for SAML, OIDC, and LDAP
Built-in admin console for managing users, roles, and realms
Customizable login UI and authentication flows
Self-hosted deployment with clustering and high availability options
Strengths
Complete control with open-source flexibility: Keycloak is free to use and fully open source, allowing teams to deploy it in their environment and customize nearly every aspect of its behavior with no licensing fees or feature restrictions.
Enterprise protocol support: Keycloak supports SAML 2.0, OpenID Connect, and LDAP out of the box, which could be a good fit for enterprise use cases that require integration with legacy systems or multiple identity sources.
Customizable UI and flows: Teams can modify the login pages, configure user journeys, and implement custom auth logic using Keycloak’s authentication flows and SPI (Service Provider Interfaces).
Ideal for
Keycloak is a good Auth0 alternative for enterprises or teams with DevOps resources who want a self-hosted solution and full stack visibility while also being committed to devoting full-time engineers to build and manage authentication.
authentik
Overview
authentik is another open-source identity provider that focuses on self-hosted deployments and simplifies administration. It aims to provide a clean user interface and native support for common enterprise protocols. authentik is popular among DevOps teams and privacy-conscious organizations that seek full control over their authentication infrastructure.
Among open-source Auth0 alternatives, authentik is often chosen for its lightweight deployment, modern design, and ease of setup, making it appealing to teams that want open-source flexibility without Keycloak’s complexity.
Key capabilities
Self-hosted, Docker-native deployment with modern architecture
Support for SAML, OIDC, LDAP, and SCIM
Web-based admin UI with policy management and user provisioning
Built-in application proxy for securing internal apps
Strengths
Lightweight and easy to deploy: authentik is designed for quick, containerized deployment using Docker or Kubernetes. Its simple UX makes it a good fit for small teams.
Protocol support for modern and legacy systems: authentik supports key protocols out of the box, including SAML, OpenID Connect, and LDAP.
Clean admin experience and policy control: The admin UI makes it easy to manage users, roles, permissions, and access policies without requiring access to configuration files.
Ideal for
authentik is a lightweight, open-source alternative to Auth0 that’s great for teams looking for a modern, open-source auth solution with fewer legacy constraints. However, it may not include the advanced enterprise and orchestration features found in commercial identity platforms.
Related Reading: What Is an Identity Provider (IdP) & How Does It Work?
Choosing the best Auth0 alternative
Choosing the right Auth0 alternative depends on your stack, scale, and goals. For teams evaluating alternatives to Auth0, the key is to prioritize solutions that simplify development, support multi-tenant identity, and scale with your business model.
Descope stands out for its modern architecture, visual workflows, prebuilt UI components, support for B2C, B2B, partner, and agentic AI use cases, but each option above serves different developer needs. To dig deeper into how Descope connects and manages identities across multiple systems, explore our Identity Federation guide for insights on connecting multiple IdPs securely.
For more detailed information on Descope, check out our docs. If you'd like a demo, meet with our auth experts. Also, if you want to try Descope yourself, sign up for a Free Forever Account and start using Descope today!