Table of Contents
Key identity risks with MCP servers
This article was written by Kevin Gao, Head of DevRel at Descope, and Ashley Jose, Founding PM at Skyflow.
Every enterprise building MCP servers faces the same balancing act: deploying production-grade MCP servers with speed and simplicity, but without multiplying security, privacy, and compliance risks with every new agentic connection.
Two fundamental roadblocks that prevent MCP servers from reaching production are identity and data privacy. AI agents connecting to MCP servers often end up with over-permissioned access to downstream tools, and the risk of exposing sensitive customer data increases with every new agentic connection.
Key identity risks with MCP servers
The AI agent identity vacuum: The first step in securely deploying MCP servers is having visibility into the clients / AI agents that connect to these servers–but without organizations having the concept of dedicated AI agent identities, this becomes a non-starter.
Coarse-grained authorization: Many MCP servers rely on coarse, app-level access or static API keys that often result in AI agents becoming over-permissioned by default. Research from Backslash Security found nearly 2000 MCP servers having no built-in security whatsoever, and most servers lacking any form of user consent before granting access to backend systems.
Moving MCP auth target: The MCP authorization specification is constantly evolving with new recommended OAuth patterns such as DCR and CIMD. This forces every MCP developer to continuously implement, test, and maintain complex OAuth flows themselves, slowing go-live timelines and increasing the likelihood of security mistakes.
Key data security risks with MCP servers
Sensitive data leakage. Without proper privacy guardrails in place, sensitive data like PII, PHI, and financial records can flow through MCP servers, risking access by unauthorized users or MCP clients.
Data residency and compliance: Enterprises need to comply with existing regulations (PCI-DSS, GDPR, HIPAA), data residency requirements, as well as adopt up-and-coming regulations without stifling agentic AI or MCP adoption. Staying in control of data amidst growing, nuanced PII standards is vital.
Runtime access control and policy enforcement: MCP servers operate dynamically—agents, tools, and clients change at runtime. Without real-time governance, static permissions quickly break down. Enterprises need the ability to enforce fine-grained, context-aware access policies (who, what, why, and under what conditions) at the moment data is requested, not just when systems are configured.
Inaction as well as insecure adoption both have real business impact. If enterprises choose to delay MCP and agentic AI deployments, they risk losing ground to competitors. On the other hand, if they choose to deploy MCP servers without the proper identity or data security guardrails in place, resulting compliance violations can potentially run into millions in costs.
As MCP continues gaining traction as the go-to standard for connecting AI applications to real-world data, organizations need interoperable identity and privacy infrastructure that can scale with it.
Privacy-preserving MCP servers with Descope and Skyflow
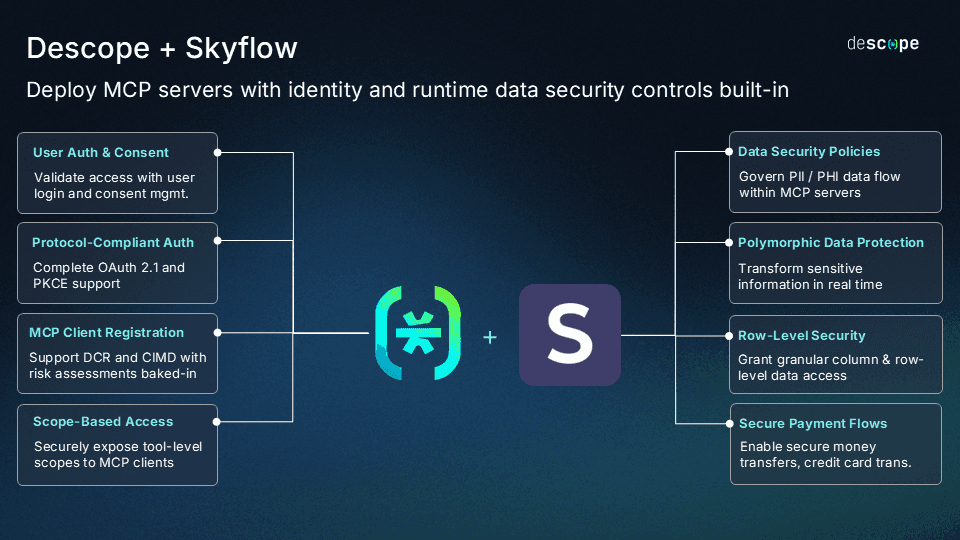
Descope and Skyflow have joined forces to offer the first natively integrated identity and data control layer for organizations building external and internal-facing MCP servers. With Descope acting as the authorization server and Skyflow providing runtime data security, customers can now deploy MCP servers with user authentication and consent, scope and tool based access control, and enterprise-grade privacy guardrails.
With Descope controlling the user and agentic identity and Skyflow controlling what data they can access, organizations can move MCP server deployments forward with confidence and make data access decisions at runtime without rebuilding their entire security infrastructure themselves.
The video below shows how to set up an MCP server with Descope and Skyflow and demonstrates a use case of real-time PII data control.
How the integration works
To use the integration, organizations need to:
Define their MCP server in Descope (which adds Descope as the authorization server), as well as configure it to work with Skyflow APIs and enable OAuth Token Exchange.
Define and map Descope identity roles to Skyflow application roles, enabling differential PII access with context-based, fine-grained enforcement, including dynamic masking and row-level security.
With this configuration in place, Descope’s authentication and access management capabilities work in concert with Skyflow’s data protection capabilities to offer end-to-end identity and privacy protection for any MCP server data flow.
Example: PII data control
Let’s say a person from the marketing team at an organization uses an internal AI agent that uses an MCP server to connect to several enterprise systems. The marketing representative asks, “Retrieve information of all users from our customer Acme Inc. that reside in California and send them an event invitation email using Mailchimp.”
For this request to be completed in a secure, compliant manner, the following control layers are needed:
How can the AI agent get access to send emails from Mailchimp on the marketing user’s behalf?
How can the AI agent get access to email addresses and other authorized customer data from Acme Inc. based on state information without getting access to sensitive data like phone numbers, residential addresses, etc. that may reside in the database?
Here’s a simplified look at how this request would be fulfilled using an MCP server protected by Descope and Skyflow:
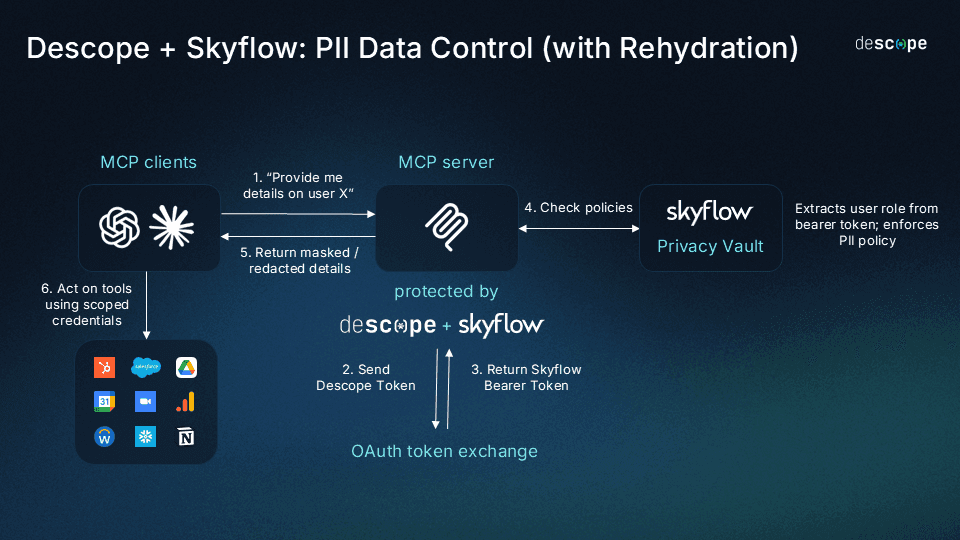
User auth and tool consent: The first time the user connects the AI agent to the MCP server, they go through an authentication / SSO flow (just like they would for any other corporate app). They are also shown a consent screen that asks them to authorize the AI agent’s access request to send emails from Mailchimp on their behalf. The Mailchimp token for the AI agent is then stored in the Descope credential vault.
OAuth Token Exchange: The Descope token generated after the auth and consent process is exchanged for a Skyflow bearer token using OAuth Token Exchange. This bearer token contains contextual information including the user’s role.
Privacy policy checks / RLS enforcement: The Skyflow bearer token is used to check the Skyflow Privacy Vault for any PII policies that may be in place, as well as to enforce Row-level security.
In this example, let’s say policies are in place to allow marketing users–and by extension, the AI agent used by the marketing user–row-level access to names and email addresses of users from Acme Inc. residing in California in plaintext, but other data residing within those rows (phone numbers, residential addresses) are masked or redacted.
Take action using short-lived, scoped credentials: The AI agent would fulfill the request by using the customer data it has access to from Skyflow (names, email addresses) and the tool-level token it can access from Descope to send marketing emails to the relevant Acme Inc. users with Mailchimp.
Descope controls the user / agentic identity and what tools the agent can access on the user’s behalf. Skyflow controls what data the agent can access on the user’s behalf. Importantly, these access control decisions are made at runtime using existing roles and policies, without needing to code any custom application logic.
Other use cases
With protection from Descope and Skyflow built in, MCP servers can power a variety of use cases in a secure, compliant manner.
Row-level security
Let’s say a customer support representative asks an AI agent connected to an MCP server to fetch details from a customer table with PII. Row-level security policies can be set that only provide access to rows in the table containing customer data where they are the designated customer support rep.
Data residency
Let’s say a user based in the US asks an AI agent connected to an MCP server to fetch details of the largest customers in each geography. Policies can be set to align with geography-specific data residency requirements–for example, the user may get back redacted data for customers based in the EU (or may not get access to that data at all).
Secure payment processing
Let’s say a user initiates a credit card transaction using an AI agent connected to an MCP server. Skyflow can pass the credit card details from the Skyflow Privacy Vault directly to multiple payment processors without the credit card number ever entering the agent-to-MCP-server flow, maintaining PCI compliance.
Making MCP real without breaking security
The promise of MCP servers will meet reality only when these systems can work within existing and upcoming privacy and compliance requirements. Descope and Skyflow provide the identity and privacy layer for organizations to build privacy-preserving, protocol-compliant MCP servers.
As MCP adoption becomes more widespread, organizations that adopt these architectural principles now will stand a real advantage by securely exposing their apps, APIs, and enterprise resources (including sensitive data) to AI agents without identity or compliance headaches.
Have questions about the integration? Book a demo with the Descope team to learn more.





