Table of Contents
What is Dynamic Client Registration?
Imagine you’re checking out from a new online store. If you pay with a credit card, you have to enter your shipping address, billing details, and card info every time you shop somewhere new. But if you’ve saved this info before, your browser might offer to autofill your details with a single click—even if you’ve never shopped on that site before.
This is essentially what Dynamic Client Registration (DCR) does in the world of web-based authorization. Just as autofill simplifies sharing a shipping address, DCR automates how applications register with authorization servers so they can participate in OAuth and OIDC flows with minimal manual setup.
In this guide, we’ll walk through everything you need to know about Dynamic Client Registration:
What DCR is and the kinds of problems it solves
How DCR works in practice
Key security and implementation considerations
How DCR impacts AI systems, like those using the Model Context Protocol (MCP)
What is Dynamic Client Registration?
Dynamic Client Registration is an OAuth and OpenID Connect protocol that lets client applications automatically register with an authorization server instead of requiring manual pre-registration. The DCR protocol is formally defined in RFC 7591, with optional registration management extensions in RFC 7592. It was designed to work within the Open Authorization (OAuth) and OpenID Connect (OIDC) ecosystems.
DCR automates the client registration process by:
Letting clients discover authorization servers and their registration endpoints
Allowing clients to submit metadata (e.g., name, redirect URL) programmatically
Receiving client credentials (client ID and optionally a client secret)
Enabling clients to immediately use those credentials in OAuth/OIDC flows
Think of this like the difference between manually filling out a form versus having your browser’s autofill feature complete it for you. In DCR, the entire registration process happens automatically between the client and the authorization server.
In other words, DCR automates the registration step that allows applications to participate in OAuth and OIDC authentication and authorization workflows.
Why did Dynamic Client Registration emerge?
Dynamic client registration solves a long-standing scalability problem in OAuth and OIDC implementations: the need to manually register every application before it could communicate with an authorization server.
In traditional OAuth/OIDC systems, when an application (a “client”) wants to interact with a user’s account, it must be pre-registered with the authorization server. This manual process typically involves:
A developer registering their application through an admin portal
The authorization server issuing a client ID and possibly a client secret
The developer copying those credentials into their application
The application using those credentials to request tokens and participate in OAuth/OIDC flows
While workable for small environments, this process breaks down as organizations add more applications, deploy across multiple environments, or integrate with external services they don’t control. Manual registration becomes slow, error-prone, and difficult to scale.
For example, when a new customer joins a SaaS platform, the system no longer needs an admin to manually create OAuth clients for each integration the customer requires.
Dynamic client registration emerged to remove this bottleneck. Instead of requiring human approval for every application instance, DCR enables clients to register programmatically and securely. This automation supports distributed systems, CI/CD pipelines, mobile app deployments, and any architecture that needs to establish new trust relationships at runtime.
Where Dynamic Client Registration fits in OAuth and OpenID Connect
Dynamic client registration is a specification within Open Authorization (OAuth) and sits alongside OpenID Connect (OIDC) as part of the broader authorization and authentication stack.
OAuth handles delegated authorization, OIDC adds an identity layer on top of it, and DCR automates the step that allows clients to participate in both. Understanding how these protocols relate helps clarify where DCR fits and why it matters. DCR was designed to operate within OAuth and streamline how clients obtain the credentials they need to request authorization.
OAuth is the industry standard for allowing third-party applications to access a user’s account without exposing credentials. All OAuth flows depend on a client ID (and sometimes a client secret), and traditionally those credentials had to be created manually. DCR automates that registration step so apps can obtain client credentials programmatically and begin participating in OAuth flows immediately.
OIDC adds an identity layer to OAuth by issuing ID tokens that confirm the user’s identity.
Why Dynamic Client Registration matters
Dynamic client registration helps developers scale modern identity systems without relying on slow, manual setup. It reduces integration overhead, supports faster deployments, and improves both security and user experience across a wide range of application types.
DCR addresses several recurring challenges:
Reducing integration friction: Clients can connect to new authorization servers without waiting for manual approval or credential provisioning.
Automating DevOps and CI/CD pipelines: OAuth clients can be provisioned automatically during deployment, removing a common bottleneck.
Improving mobile security: Each installation of a mobile app can register as its own client instead of sharing embedded credentials.
Supporting multi-tenant SaaS architectures: When a new organization joins a SaaS platform, OAuth clients can be provisioned programmatically for their environment.
Enabling AI agent ecosystems: AI agents connected through MCP and other non-human identities can register with services at runtime to obtain the credentials they need for secure communication.
Scaling many-to-many environments: Organizations with large app ecosystems avoid the exponential growth of manual registration tasks.
By shifting credential provisioning into an automated, standardized protocol, DCR makes OAuth/OIDC deployments more scalable, maintainable, and secure—whether you’re supporting human users, AI agents, or distributed services. Dynamic client registration streamlines OAuth and OIDC client onboarding, improves scalability for distributed systems, and enables secure machine-to-machine connectivity for modern AI and MCP workflows. Whether using DCR or CIMD, automating client provisioning helps reduce friction, strengthen security, and scale identity systems with confidence.
How the Dynamic Client Registration flow works
Dynamic client registration follows a defined sequence that replaces manual credential provisioning with a fully automated workflow. Understanding these steps helps developers see where DCR removes operational friction and how it integrates with OAuth and OIDC.
Here’s how the process works at a high level:
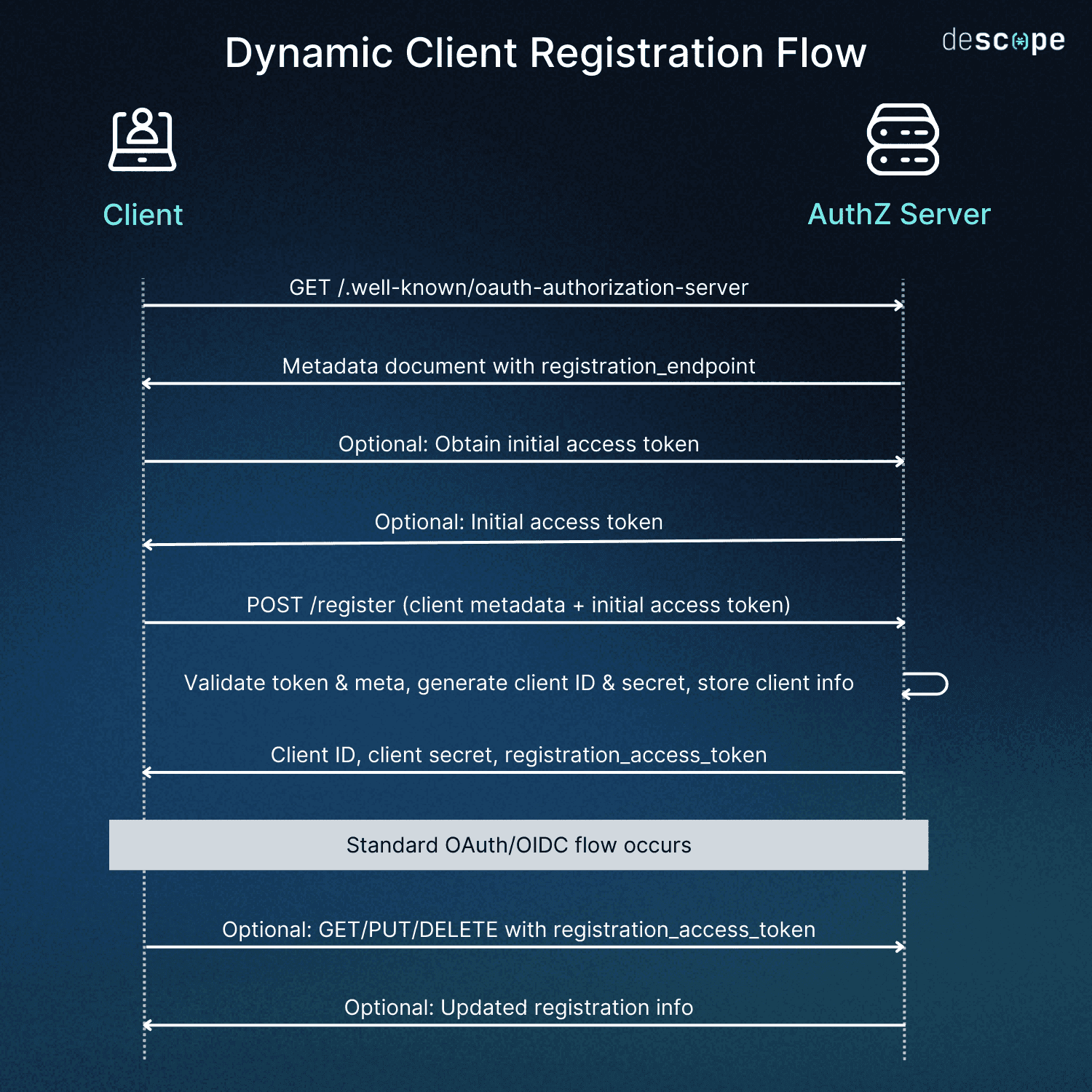
Discovery: Finding where to register
Before a client can register, it must locate the authorization server’s registration endpoint. Traditionally, this required digging through documentation or admin portals. DCR eliminates that manual overhead.
With DCR’s automatic discovery:
The client queries the authorization server’s metadata document (typically at a well-known URL like
/.well-known/oauth-authorization-server)The metadata document contains the
registration_endpointURL and information about supported featuresThe client extracts the registration endpoint and prepares to submit its information
Access control: Getting permission to register (optional)
Not all authorization servers permit open registration, since allowing any unauthenticated client to register can introduce clear security risks. Many servers gate their registration endpoints so only trusted applications can create client records.
To control access, a server may require an initial access token—a credential issued through a trusted channel such as a developer portal, administrative approval, or a pre-established provisioning workflow. The client includes this token as a bearer token in the registration request.
Although the initial access token step is optional under the specification, it is common in production environments and can be reused to register multiple clients programmatically. This maintains automation while preventing untrusted or unknown applications from registering.
This access control layer ensures that DCR remains both flexible and secure before the client proceeds to submit its registration metadata.
Registration request: Sharing application details
At this stage, the client application automatically sends its metadata in a standardized JSON format to the registration endpoint. This can be built into the application’s initialization process, meaning that it requires no human intervention.
The client issues an HTTP POST request containing a standardized JSON payload that includes fields like redirect_uri, client_name, etc. Because this step is typically built directly into the application’s startup or provisioning workflow, it requires no human intervention. Once the request is sent, the server can immediately validate the metadata and create the new client record.
Server processing: Creating the client record
Once the registration request is received, the authorization server validates the provided metadata and applies any relevant policies. The server then generates a unique client_id, issues a client_secret for confidential clients, and saves the client’s metadata in its database. This immediate processing eliminates manual approval delays and allows the new client to begin participating in OAuth and OIDC flows right away.
In processing the request, the server:
Verifies the client metadata complies with its policies
Generates a unique client ID
Generates a client secret for confidential clients
Stores the client information in its database
These sub-steps ensure security and ease of use in both the present access session and future ones. The user is associated with a secure client secret, and information is stored securely.
Registration response: Receiving credentials
At this stage, the server responds with the client’s registered information, and it may provide a registration_access_token (or equivalent) if the client can manage its own registration later.
Additionally, the client application automatically receives the client ID, secret, and other registration details in the API response. The application can store these credentials and begin using them immediately without any manual configuration—again, streamlining future sessions.
OAuth and OIDC flows: Putting credentials to work
With registration complete, the client now operates like any other OAuth/OIDC client. It can authenticate with the authorization server and request tokens as needed. Notably, this is what happens when an MCP client needs to connect to an MCP server.
Key actions the client can now perform include:
Authenticate with the authorization server using its client ID and secret
Initiate authorization requests on behalf of users
Exchange authorization codes for access tokens
Refresh tokens to maintain session continuity
Request ID tokens in OIDC scenarios to confirm a user’s identity
DCR simply handles the initial provisioning step automatically; everything else follows standard OAuth/OIDC behavior.
Registration management: Updating or removing registration (optional)
If the authorization server implements RFC 7592, clients can manage their own registration using the registration_access_token.
This allows clients to:
Retrieve their current registration metadata
Update attributes such as redirect URLs or application names
Delete their registration when the application instance is retired
This self-service capability enables safer, decentralized management—especially in large or dynamic environments where clients evolve frequently.
DCR security and implementation considerations
Using Dynamic Client Registration effectively requires attention to both its security implications and the practical realities of deploying it at scale. Because DCR automates registration—previously a tightly controlled, manual process—organizations must ensure that only trusted clients can register and that the registration workflow cannot be exploited or abused.
Below are the key considerations for implementing DCR safely and reliably.
Practical implementation tips
Open or poorly gated registration endpoints can become high-value targets for adversaries. DCR expands flexibility, but without the right safeguards, it can also expand the attack surface.
1. Document metadata requirements clearly
Make acceptable redirect URIs, domain patterns, grant types, and authentication methods explicit. Human-readable documentation helps developers (and AI agents) debug failed registrations without guesswork.
2. Enforce rate limits on registration attempts
If an attacker obtains or brute-force attacks a client secret—or attempts automated registrations across many service endpoints—rate limiting helps shut down the attack early.
Limiting registration attempts per IP or per token prevents credential stuffing, brute-force enumeration, and rapid-fire abuse of the registration endpoint.
3. Validate all client metadata rigorously
Attackers may try to register clients with malicious or deceptive metadata—such as redirect URLs designed for phishing or token exfiltration.
Authorization servers should validate:
Redirect URIs
Application domain patterns
Allowed grant types
Allowed response types
Token endpoint authentication methods
Rejecting noncompliant metadata ensures that only legitimate, policy-aligned clients complete registration.
4. Enable comprehensive logging
Detailed logs identify who registered what, when, and with which metadata. Logging is essential not only for debugging but also for forensic analysis, anomaly detection, and compliance.
5. Keep your client metadata up to date
If callback URLs or capabilities change but the registered metadata is not updated, authentication flows will fail. Regularly syncing application metadata with the registered metadata is essential for reliability.
6. Implement clear, actionable error handling
When registration fails, the client should surface errors that help developers—or internal support teams—diagnose the issue quickly. Opaque failures complicate debugging and introduce unnecessary delays.
7. Automate registration in CI/CD pipelines
Incorporating DCR into deployment workflows ensures that each environment (staging, QA, production) receives appropriate, fresh credentials automatically. This reduces manual errors and makes the overall system more consistent.
These DCR-specific controls complement (not replace) standard OAuth security guidance—such as secure token storage, Proof Key for Code Exchange (PKCE), and minimizing overscoping—to keep the authentication ecosystem resilient.
Also Read: Tips to Harden OAuth Dynamic Client Registration in MCP Servers
How DCR impacts agentic systems
If you have an AI agent or MCP client like Cursor, Claude, or ChatGPT, DCR allows it to obtain a client ID. This enables it to eventually authenticate with the authorization server and get an access token to be used with an MCP server.
DCR removes what would otherwise be a significant operational bottleneck. Instead of requiring IT teams to manually provision OAuth clients for every new AI agent, workflow, or integration point, agents can:
Register themselves at runtime
Obtain the credentials they need on demand
CIMD for MCP auth with DCR
While Dynamic Client Registration is a major enabler for AI and MCP-connected systems, it introduces overhead and operational complexity at scale. As organizations deploy larger numbers of external-facing MCP servers, potentially millions of clients will register and need its own client ID and secret, creating a burden on authorization servers.
To address these challenges, the MCP community has embraced an alternative model: Client ID Metadata Documents (CIMD). CIMD works by rethinking how clients identify themselves. Instead of registering through a /register endpoint, the client’s client_id becomes an HTTPS URL that points to a JSON document containing the client’s metadata. When an authorization server sees this URL-based client ID, it simply fetches the metadata document directly from the client’s domain.
This model solves many of the biggest pain points that appear when DCR is used at scale:
No registration endpoint: CIMD eliminates the /register endpoint that attackers could attempt to abuse.
Stable, domain-based identities: A single URL identifies an entire application rather than each instance. This allows servers to enforce security policies based on the client’s domain.
No registration database: Authorization servers no longer need to store or update client records, reducing operational overhead; however, in cases with a managed provider, they will anyway because they will want to have authorization policies for specific agents.
Standard HTTP caching: While not unique to CIMD, this approach allows metadata documents to be cached (typically for 24 hours), improving performance while keeping identity documents fresh.
Better suitability for AI workflows: AI agents can expose metadata through a stable URL rather than creating endless client registrations on the fly.
As the identity ecosystem surrounding MCP evolves, many implementations may support both approaches. In these flexible deployments, CIMD will serve as a lightweight default for clients that support it, with DCR remaining available for closed environments or specific use cases.
Optimize DCR workflows with Descope
Because today’s digital ecosystems rely on countless apps, APIs, AI agents, and external services, it’s impossible for developers to pre-plan every integration. MCP simplifies these connections, but securing your server according to the official MCP auth spec can be its own challenge.
Descope's MCP Auth SDKs and APIs remove that burden. They handle OAuth 2.1 authorization, PKCE, Authorization Server Metadata, and Dynamic Client Registration in just a few lines of code—allowing developers to focus on building features rather than managing complex auth flows. Crucially, Descope provides DCR assessment flows that use IP validation checks to ensure client registrations are not malicious.
For enterprise teams, Descope’s Agentic Identity Control Plane provides end-to-end governance. Organizations can enforce scope-based access policies, audit agent activity, detect misconfigurations or rogue behaviors, and manage lifecycle operations from registration through revocation.