Table of Contents
Tokens are the backbone of your application
Modernizing authentication sounds simple on paper: add passwordless options, roll out MFA, tighten security, and make login smoother for users. But in practice, one often-ignored dependency slows everything down: the token format your backend is built around.
Tokens power some of the most important parts of an application. They decide who can access APIs, maintain mobile sessions, handle service-to-service communication, reach databases, and carry the custom claims that older systems still rely on. Even small changes to a token format can trigger breaking issues across applications and environments.
External Tokens give Descope users a new way to modernize authentication without forcing changes to their existing backend. You can introduce new flows, strengthen security, and update your auth logic — all while still returning the exact token your backend already expects.
Modern auth on the front end. Full compatibility on the backend.
Tokens are the backbone of your application
Most organizations are tightly coupled to the token formats their applications already use. These tokens power core workflows like API authorization, mobile session handling, machine-to-machine communication, and the custom claims or legacy logic that has accumulated over years. Because so much depends on them, changing how tokens look or behave creates a surprising amount of work.
Updating a token format often forces teams to reconfigure API gateways, rework authorization policies, and learn the nuances of a completely new token structure. Backend services across multiple environments need to be updated in sync, and teams have to ensure mobile clients don’t get logged out in the process. And if you’re using platform-as-a-service backends, there’s an added challenge: some of them only support validating tokens from specific issuers, or don’t offer enough flexibility to accept arbitrary OIDC JWTs.
For B2C, B2B, or partner-facing applications, the complexity multiplies. A change that seems small on paper can turn into a sprawling, multi-team effort involving configuration updates, compatibility checks, and downstream coordination. What should be a simple auth modernization quickly becomes a long, friction-heavy migration.
Modernizing authentication shouldn’t require rebuilding the token plumbing your applications already rely on — and it certainly shouldn’t demand a full overhaul of your existing infrastructure just to accommodate a different token format.
Keep your token format, upgrade your authentication
External Tokens allow teams to adopt Descope’s modern authentication features, such as passwordless, MFA, social login, SSO, and identity orchestration, without modifying their backend token logic.
Instead of requiring every service to understand a new Descope token, Descope generates an external token using a configurable connector at the end of each authentication flow.
Your frontend receives a token that matches what your backend already expects. Your backend continues working exactly as before.
In practice, this means:
Your frontend modernizes instantly
Your backend remains unchanged
Your token format stays the same
Upgrades become incremental instead of disruptive
External Tokens are ideal for applications where changing the token layer is too risky, too slow, or too costly.
How External Tokens work
External Tokens are powered by External Token Connectors, which run automatically at the end of a Descope Flow.
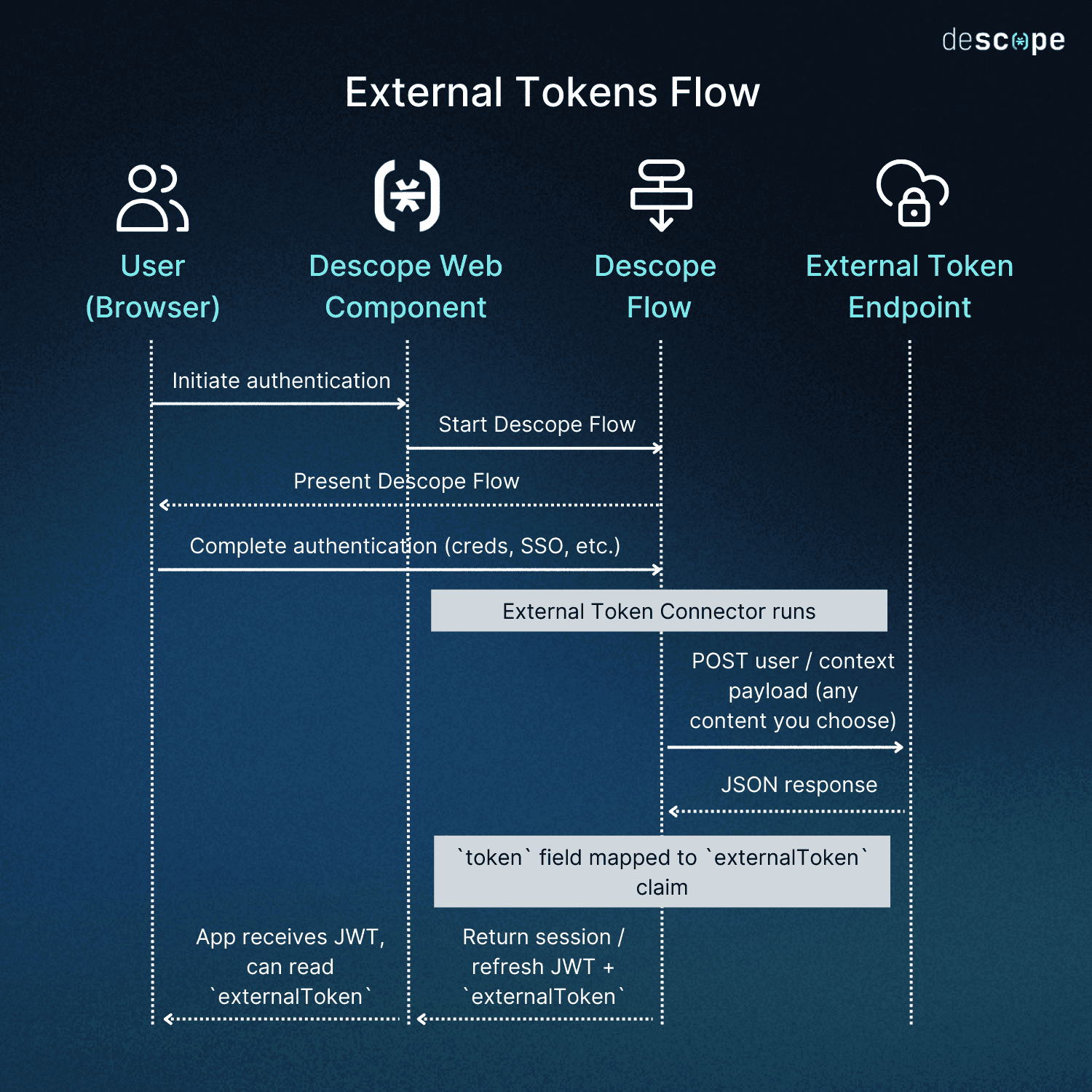
Here’s the lifecycle:
A user authenticates through a Descope Flow: The flow handles passwordless, MFA, SSO, social login — whatever your configuration requires.
Descope triggers your External Token Connector: This can be a prebuilt connector (e.g., Firebase, Supabase) or a generic HTTP endpoint you host.
Descope POSTs user/context data to your connector: You control what fields you use.
Your connector returns a JSON response containing a token field: This is the external token you want your app to receive.
Descope injects that token into the final JWT: It appears under the
externalTokenclaim.Your app receives the final JWT: Using the Descope Web Component, the frontend can access the
externalTokenvalue and pass it directly to your backend.
Connectors: The engine behind External Tokens
Connectors are the mechanism that generates your External Tokens. They define exactly how the external token is created, what it contains, and how it integrates into your existing authentication ecosystem.
Descope provides several connector types, each designed for different modernization strategies:
Firebase Token Connector
This connector allows you to embed Descope’s modern flows like passwordless, MFA, SSO, social login, inside your mobile or web apps while still using Firebase Authentication as your primary auth platform.
After the user completes a Descope Flow, Descope mints a valid Firebase Custom Token. Your app can pass it directly into: firebase.auth().signInWithCustomToken(<externalToken>)
This lets you:
Adopt Descope’s UX and authentication features
Preserve Firebase as the source of truth
Avoid migrating backend logic or Firestore rules
Maintain existing mobile sessions and SDK usage
You get modern Descope experiences without replacing Firebase Auth.
Also Read: Modernize Auth Without Changing Your Firebase Sessions
Supabase Token Connector
Similar to Firebase, the Supabase connector lets you modernize login flows with Descope while keeping Supabase Auth as the main authentication engine.
When a Descope Flow completes, Descope returns a token compatible with Supabase’s custom JWT login endpoint: supabase.auth.signInWithCustomJWT(<externalToken>)
This enables teams to:
Use Descope’s flow components and orchestration
Continue relying on Supabase policies, RLS, and existing auth logic
Avoid rewriting downstream services or database rules
You get all the flexibility of Descope without disrupting your Supabase identity implementation.
Generic HTTP Token Connector
This connector is for organizations with fully custom token formats or proprietary authentication logic.
Descope POSTs user and context data to your endpoint. Your service signs and returns any token structure you want — JWT, opaque session string, multi-claim structure, tenant-specific format, etc.
This is ideal for legacy environments, in-house token formats, or systems with strict claim or signature requirements. It gives you complete control over your external token, while Descope handles the entire authentication journey.
Conclusion
External Tokens make it possible to modernize authentication without rewriting downstream systems. You can adopt Descope’s flows, add passwordless and MFA, improve security posture, and orchestrate identity logic, while your existing apps and APIs continue working exactly as they do today.
If you are ready to try it out, sign up for a Free Forever account or book a demo with our team to see how easy it is to adopt modern authentication flows while preserving your existing backend.