Table of Contents
Why workforce IAM no longer fits partner ecosystems
If partner onboarding takes weeks, SSO requests pile up in support queues, or simple access changes require engineering help, identity has already become a bottleneck. Identity has quietly become one of the biggest sources of friction in partner-led growth, surfacing as stalled partner launches, inconsistent login experiences, and rising operational overhead long before teams recognize it as the root cause.
The reasons are scale and complexity. Modern platforms grow through partner ecosystems rather than standalone products. As partners, distributors, and B2B customers become the primary path to end users, identity shifts from an internal service to shared infrastructure. Every login, permission, and access decision now spans organizational boundaries, reshaping how leaders must think about identity to stay competitive.
Why workforce IAM no longer fits partner ecosystems
Traditional IAM platforms were designed around a clearly defined organizational boundary. Users were employees, security policies were shared, and access decisions were centralized. That model worked when identity was primarily an internal IT concern.
Today, that assumption no longer holds for partner IAM. According to S&P Global, external identities now account for 64% of users in many organizations, including vendors, partners, and contractors. This shift means that the majority of authentication and authorization activity now happens outside the enterprise.
External users do not behave like employees. They belong to separate organizations, rely on different identity providers, and operate under their own security and compliance requirements. Workforce IAM systems struggle to accommodate this diversity because they assume uniform policies and a single source of truth. When organizations attempt to stretch these tools to cover partner access, visibility, and control quickly degrade.
The operational cost of partner complexity
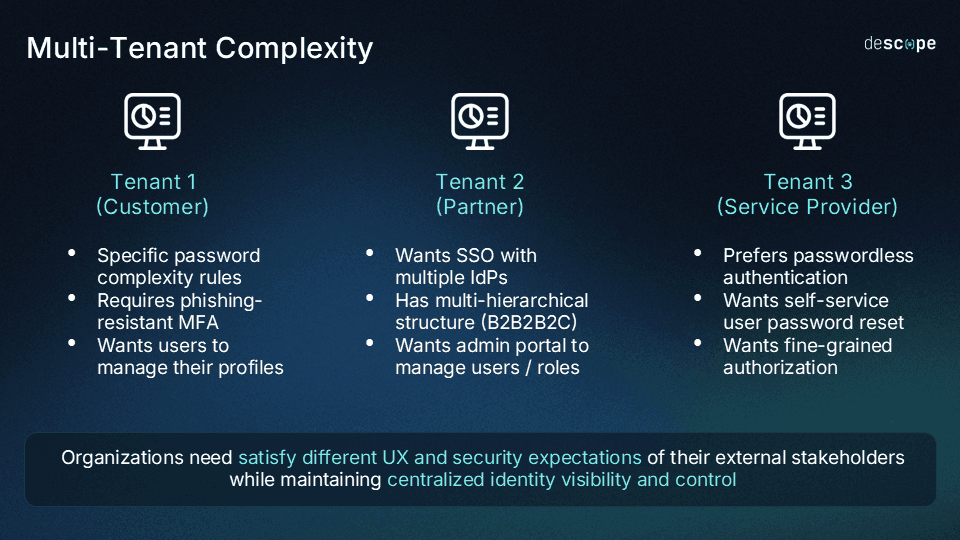
Every partner introduces identity variation. One partner may require SAML-based single sign-on tied to their corporate directory. Another may rely on OIDC. Smaller partners may not support SSO at all. Some require branded login experiences to maintain customer trust, while others must comply with strict regulatory standards.
Supporting this diversity often requires manual setup and custom configuration. Engineering teams become involved in SSO integration, attribute mapping, and user provisioning. Partner onboarding stretches from days into weeks. Support tickets increase as identity logic becomes harder to maintain.
This operational drag is not just inconvenient; it is harmful. Manual processes create opportunities for misconfiguration, stale access, and inconsistent enforcement. As partner ecosystems grow, partner IAM becomes increasingly difficult to manage.
Also Read: Single-Tenant vs Multi-Tenant Architectures
The identity delegation gap
When partners must open tickets to add users, wait for access changes, or escalate basic configuration requests, friction spreads fast. Onboarding slows, support queues grow, and platform teams become bottlenecks for routine tasks.
This friction reflects a deeper issue: partner ecosystems require autonomy, while legacy identity systems enforce central control. Partners expect to manage their own users, roles, and access policies. When they cannot, partner velocity drops and platform scale suffers.
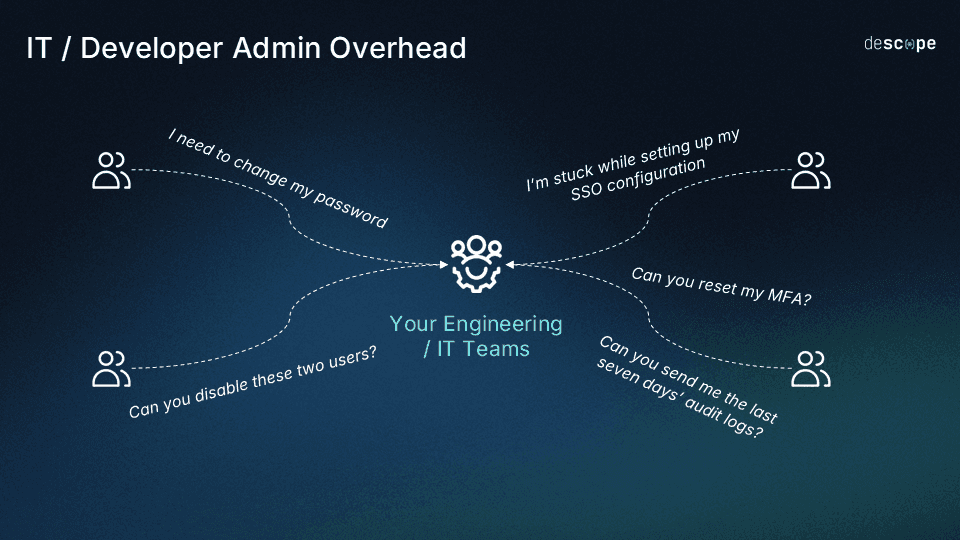
At the same time, the enterprise remains accountable for security, compliance, and auditability.
Security teams need visibility into access across all partners.
Compliance teams must demonstrate control at the tenant level.
Leadership requires confidence that risk is managed consistently across the ecosystem.
Legacy IAM systems were not designed for this balance. Without tenant-aware delegation, IT teams become bottlenecks. Every configuration request flows through a central team, slowing partner activation and increasing operational burden. This model does not scale as ecosystems expand.
This is not an edge case. Descope’s latest State of Customer Identity research found that 51% of companies currently use workforce IAM solutions for customer auth, but only 8% would choose that approach again if starting fresh. The gap between autonomy and oversight is not a process failure; it is a tooling mismatch rooted in systems never designed for partner ecosystems.
What modern identity must enable
If partner onboarding drags on, access changes require manual intervention, or security reviews slow down enterprise deals, the impact goes beyond friction. Revenue is at risk. Deals stall or fall through. Partner launches slip, and teams spend time maintaining identity instead of growing the business. Meanwhile, competitors with modern identity foundations move faster and win.
These are signals that identity has not kept pace with partner-led growth. When identity is treated as internal tooling rather than shared infrastructure, every new partner adds cost, complexity, and risk. Over time, that friction becomes a competitive disadvantage.
Organizations that modernize identity see the opposite effect. Partner onboarding accelerates. Deals close faster. Partners manage their own users and access, reducing operational overhead. Product and support teams regain focus, and customers experience smoother, more consistent access.
Modern partner IAM must enable:
Self-service partner identity administration
Flat, multi-tenant architectures with tenant-aware auth, access control, and session management
Flexible authentication and authorization models
Unified identity visibility across the ecosystem without recreating centralized bottlenecks
When identity supports partner ecosystems instead of constraining them, it becomes a driver of growth rather than a drag on it.
Also Read: How SmithRx Unified Auth Across User and Partner Portals With Descope
How Descope helps scale partner IAM
Partner ecosystems only scale when identity does not slow them down. Descope is purpose-built for B2B2X environments, providing a unified identity layer that adapts to diverse partner needs while preserving central oversight, security, and visibility.
Descope helps organizations manage partner ecosystems by enabling:
Self-service partner onboarding: Partners configure their own SSO and SCIM connections using guided setup portals, reducing onboarding from weeks to minutes and eliminating engineering bottlenecks.
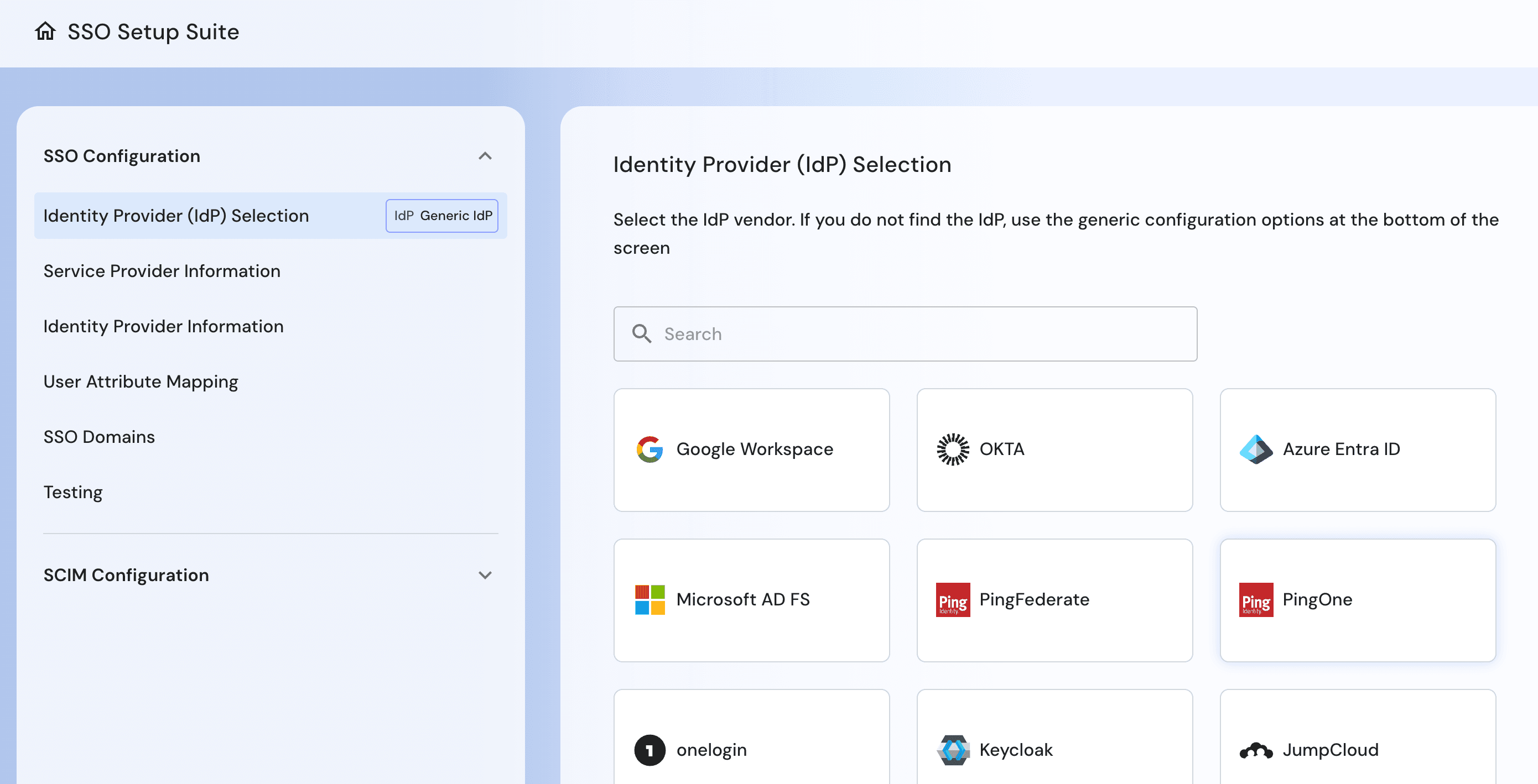
Flexible SSO for diverse partner IdPs: Native support for SAML and OIDC, IdP and SP initiated flows, multiple SSO connections per tenant, and seamless SSO migration from legacy identity providers.
Performant, fine-grained authorization: Support for RBAC, ABAC, and ReBAC enables partner-specific access models without role explosion or brittle logic. Defining authorization controls per-tenant enables flexibility in dealing with different types of partners.
Tenant-aware delegated administration: Partners manage their own users, roles, and access policies, while enterprises retain centralized oversight and auditability across all tenants.
Consistent identity experiences across partner portals: Unified authentication flows across web, mobile, and partner portals reduce friction and deliver predictable experiences for every partner and end user.
Built-in security and compliance controls: Audit logs, consent management, data residency controls, and threat detection support regulatory and security requirements across partner ecosystems.
Multi-tenant isolation with unified visibility: Strong tenant isolation protects partner data, while centralized analytics provide insight into access patterns and risk across the entire ecosystem.
By designing identity specifically for partner ecosystems, Descope helps organizations move faster, reduce operational overhead, and turn identity into an advantage rather than a scaling constraint.
Simplify partner IAM complexity with Descope
When partner onboarding slows, support queues grow, and access issues spread across portals, growth suffers. These are not isolated problems. They signal that identity has not kept pace with partner-led scale. Employee-focused tools were never designed for external, multi-tenant ecosystems, and the friction shows.
Organizations that modernize identity reverse this pattern. Partners onboard faster, operational burden drops, security improves, and experiences become more consistent. Identity stops slowing growth and starts enabling it.
Sign up for a free Descope account and start exploring how to modernize your partner IAM stack with no / low code authentication and user journeys. Have questions? Book a demo with our team to learn more.