Table of Contents
Why developers seek WorkOS alternatives
WorkOS is a popular choice for developers who need to add enterprise-grade features like SSO, SCIM provisioning, and audit logs to their applications without building them from scratch. Its focused APIs and clear abstractions make it especially appealing for SaaS teams looking to become “enterprise ready” quickly and unblock sales conversations with larger customers.
As products mature, however, developers often discover that WorkOS’s emphasis on enterprise building blocks shifts more responsibility back to engineering. While SSO and SCIM are handled, teams must still design, implement, and maintain the surrounding authentication flows, authorization logic, and multi-tenant behavior themselves. As organizations add more enterprise customers, introduce more complex B2B use cases, or require richer identity journeys, the amount of custom code and integration work grows—adding complexity, cost, and long-term maintenance overhead.
Below, we break down the top reasons developers look beyond WorkOS, followed by a closer look at the leading alternatives available today.
Why developers seek WorkOS alternatives
Many teams outgrow WorkOS for a few key reasons:
Limited flexibility: WorkOS provides abstractions optimized for enterprise SSO and SCIM. While this simplifies initial setup, it restricts customization for non-standard flows, deeper CIAM use cases, and complex tenant logic, creating a ceiling as products evolve.
Enterprise SSO complexity and cost: Although WorkOS abstracts SAML and directory integrations, enterprise onboarding can remain slow and hands-on. As multi-tenant SaaS products scale, per-connection pricing and limited discounting make costs harder to predict and justify.
Narrow feature scope: WorkOS is fundamentally an SSO and SCIM platform. Capabilities beyond that, such as AuthKit, see limited adoption and depth, forcing teams to layer additional tools for MFA, authentication flows, and broader CIAM requirements.
Product velocity and roadmap depth: WorkOS ships infrequently and rarely expands meaningfully beyond its core SSO focus.
No built-in orchestration: WorkOS does not provide visual flow builders or workflow orchestration, leaving all user journeys, conditional logic, and lifecycle automation to application code.
Multi-tenancy requires custom engineering: Tenant-aware roles, permissions, delegated administration, and tenant-specific policies must be designed and maintained outside the platform.
Limited authorization capabilities: WorkOS does not offer native RBAC, fine-grained authorization, or policy engines, pushing authorization logic into custom services or separate tools.
Developer-owned UX and flows: WorkOS does not ship hosted UIs or end-to-end journeys, so developers must build and maintain login, admin, and onboarding experiences themselves.
Fragmented identity architecture: WorkOS is often added alongside existing authentication systems, leading to multiple identity layers and increased operational complexity over time.
Documentation depth gaps: Core setup documentation is strong, but advanced scenarios such as complex migrations, edge cases, and large-scale multi-tenant patterns are less prescriptive.
Scaling cost predictability: Pricing tied to enterprise connections and feature tiers makes long-term identity costs difficult to forecast. As SaaS platforms mature, this unpredictability becomes a key driver for evaluating alternatives.
Each alternative below addresses these gaps differently depending on your technical requirements, ecosystem, and growth stage.
Descope
Overview
Descope is a modern customer and agentic identity platform built for developers who need flexible, secure authentication without the long-term overhead of stitching together multiple identity systems. It is designed to support both customer-facing and enterprise use cases from a single platform.
Rather than stopping at enterprise SSO and SCIM, Descope delivers a complete identity platform that spans authentication, authorization, and orchestration for customers, partners, admins, AI agents, and MCP-based systems.
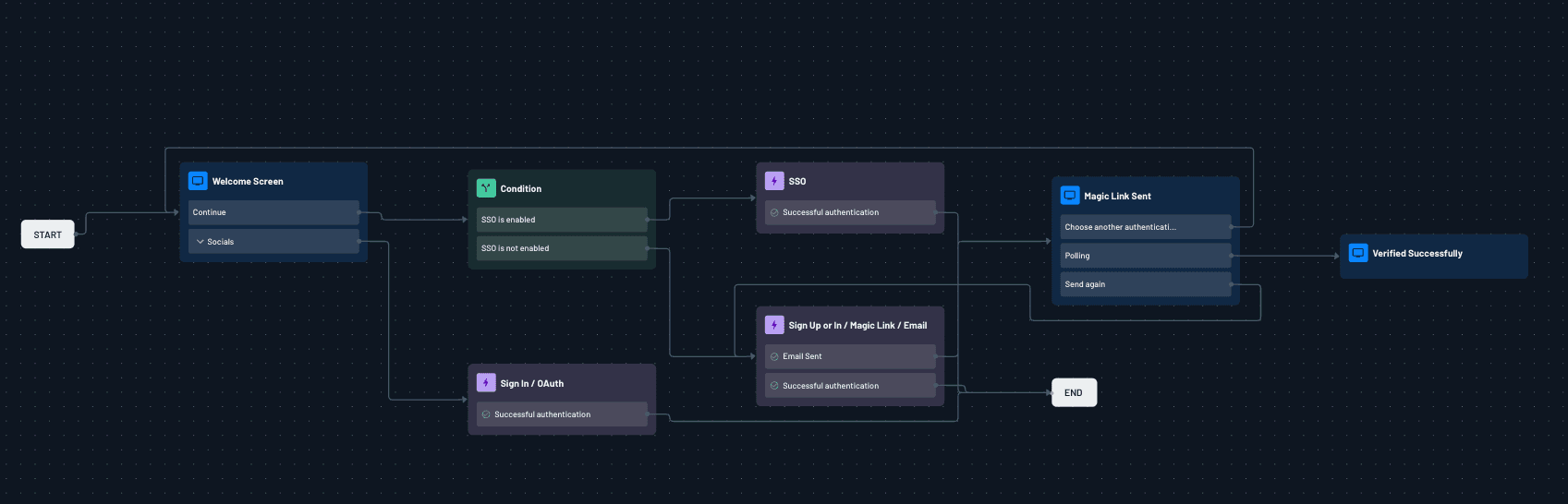
Descope is particularly well suited for B2B SaaS applications that require tenant-aware SSO, fine-grained authorization, and adaptable identity journeys. Its core differentiator is Descope Flows, a no-code / low-code orchestration layer that allows teams to visually design and evolve authentication, MFA, SSO, consent, and agent authentication flows without redeploying application code.
Key capabilities
End-to-end identity orchestration across authentication, authorization, risk, and fraud in one platform.
Visual workflow editor for login, signup, MFA, SSO, and consent flows.
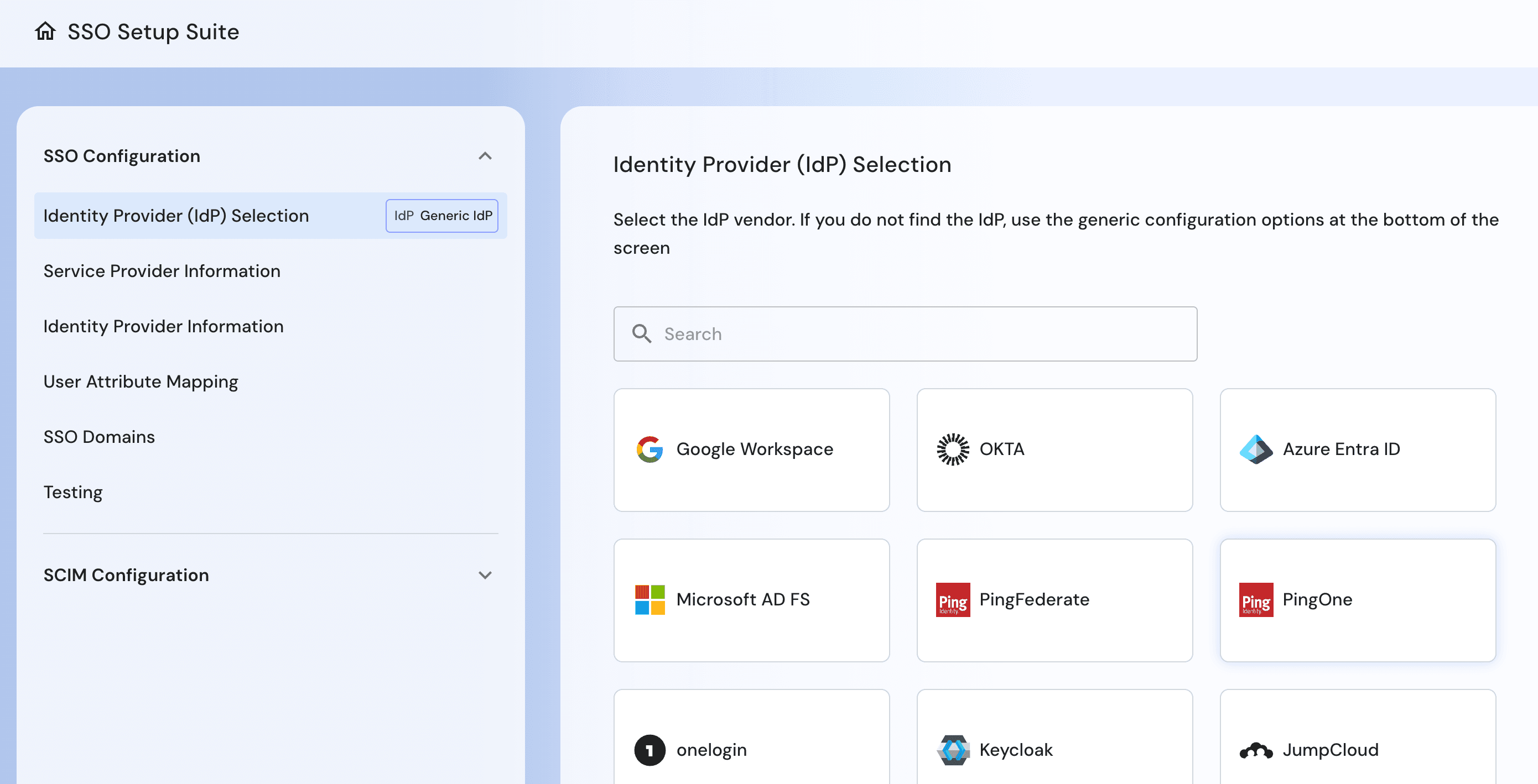
Enterprise SSO Setup Suite for guided SAML and SCIM onboarding and testing.
Adaptive MFA, session protection, and bot detection using native signals and third-party fraud integrations.
Plug-and-play connectors ecosystem with 50+ integrations for identity enrichment.
Support for passkeys, OTP, magic links, social login, and Google One Tap.
Embeddable user and admin UI components for self-service identity management.
15+ SDKs plus robust APIs for web, mobile, and backend integration.
Anonymous pre-auth user tracking for top-of-funnel visibility and conversion insights.
Agentic identity support for AI agents and MCP-based ecosystems.
Strengths
Streamlined enterprise SSO: Descope simplifies enterprise onboarding with guided SAML and SCIM setup, self-service configuration, and workflow-based SSO journeys that reduce customer friction.
End-to-end identity workflows: Descope lets developers design complete authentication, MFA, SSO, and authorization journeys visually, eliminating the need to stitch together custom logic around SSO building blocks.
Predictable pricing and responsive support: Descope offers transparent, usage-based pricing and consistently responsive support, helping teams scale identity without unexpected cost increases or prolonged implementation cycles.
Unified multi-tenant identity: Descope natively supports tenant-aware users, roles, and permissions, removing the need to build multi-tenant identity models on top of separate systems.
Passwordless by default: Descope supports passkeys, magic links, OTP, and social login as first-class methods that can be easily added to any flow without custom engineering.
Adaptive and risk-based MFA: MFA can be enforced dynamically using native signals and third-party risk integrations, improving security while preserving a low-friction user experience.
Developer-controlled UX: Descope supports both hosted components and fully custom UIs, giving developers control over branding and experience without locking them into rigid patterns.
AI agent ready: Descope supports secure authentication and access control for AI agents and MCP servers with its Agentic Identity Hub.
Built for modern architectures: With broad SDK and API support, Descope integrates cleanly into web, mobile, backend, and agent-based systems without becoming an architectural bottleneck.
Ideal for
Descope is a strong choice for developers and product teams that want to move beyond enterprise SSO building blocks and scale identity without accumulating custom code around WorkOS. It is well suited for SaaS applications that require tenant aware authentication, self service enterprise onboarding, and flexible identity flows as products and customer demands grow.
Descope also fits teams building B2B, B2C, or hybrid platforms that need fine grained authorization, orchestration, and secure identity controls for both users and autonomous agents within a single platform.
Auth0
Overview
Auth0, part of Okta, is a well established customer identity platform commonly evaluated by teams that need a mature, enterprise ready solution. While WorkOS focuses on delivering SSO and SCIM as standalone building blocks, Auth0 provides a broader identity platform with support for authentication, authorization, MFA, and extensibility in a single system.
For teams that outgrow WorkOS’s narrow scope, Auth0 is often considered when applications require deep protocol support, advanced SSO capabilities, and compatibility with a wide range of enterprise identity providers across complex customer environments.
Key capabilities
Enterprise SSO with SAML, OIDC, and OAuth2 across a wide range of identity providers
Comprehensive MFA support including WebAuthn, TOTP, SMS, email, and push notifications
Extensible authentication and authorization using Rules and Actions
Hosted login pages with deep customization for enterprise branding and user experience
Strengths
Broad identity coverage: Auth0 delivers authentication, MFA, and extensibility in addition to enterprise SSO and federation.
Flexible extensibility model: Rules and Actions allow teams to customize identity logic without building separate services around SSO.
Established enterprise integrations: Auth0 offers prebuilt integrations with identity providers, analytics platforms, and developer tools.
Ideal for
Auth0 is well suited for teams that need more than SSO and SCIM building blocks and want a mature, enterprise ready identity platform. It is often chosen by organizations that require broader protocol support, advanced MFA, and extensibility to support complex enterprise customer environments.
Amazon Cognito
Overview
Amazon Cognito is AWS’s fully managed authentication and user management service designed to integrate deeply with the AWS ecosystem. It handles scaling, availability, and infrastructure automatically, reducing the operational burden on engineering teams.
Where WorkOS functions as an external enterprise identity layer, Amazon Cognito embeds identity directly into the AWS infrastructure stack. It is often chosen by teams that want identity, access control, and application infrastructure to live entirely within AWS.
Key capabilities
Managed user pools for authentication and user lifecycle management
MFA and adaptive authentication using AWS risk signals
Native integration with API Gateway, Lambda, and AWS IAM
Federation with social and enterprise identity providers
Strengths
Fully managed identity service: Cognito removes infrastructure overhead by handling scaling, availability, and updates automatically.
Deep AWS integration: Identity integrates directly with AWS services for API protection, access control, and backend workflows.
High volume scalability: Designed to support large user populations without custom scaling or operational tuning.
AWS security and compliance alignment: Inherits AWS security best practices, compliance programs, and regional availability.
Ideal for
Amazon Cognito is well suited for teams that want a managed identity service without layering additional providers on top of their AWS stack. It is often evaluated as a WorkOS alternative by organizations that prioritize tight AWS integration, centralized infrastructure, and predictable operational ownership over standalone enterprise SSO tooling.
Firebase Authentication
Overview
Firebase Authentication is Google’s developer focused identity service designed for fast setup across mobile and web applications. It emphasizes ease of use through client side SDKs and tight integration with the Firebase platform.
Unlike WorkOS’s enterprise-focused SSO model, Firebase Authentication prioritizes speed, simplicity, and tight integration with a managed backend. It is often chosen by teams that prioritize rapid development and do not need enterprise SSO, SCIM, or complex multi tenant identity models.
Key capabilities
Email and password authentication with OTP and magic links
Social login with major consumer identity providers
SDKs for iOS, Android, and popular web frameworks
Native integration with Firestore, Storage, and Cloud Functions
Strengths
Fast time to implementation: Common login methods can be enabled quickly with minimal configuration.
Strong mobile SDKs: Well supported libraries for Android, iOS, and cross platform frameworks.
Unified backend experience: Authentication works seamlessly with other Firebase services for simpler application architecture.
Ideal for
Firebase Authentication is well suited for early stage products and mobile first applications that want a simple authentication layer without adding enterprise SSO tooling. Teams evaluating WorkOS often consider Firebase when enterprise requirements are minimal and speed of development matters more than advanced identity capabilities.
Supabase
Overview
Supabase Authentication is built on GoTrue and tightly integrated with Supabase’s Postgres database, storage, and serverless functions. It is designed for teams that want authentication embedded directly into their data layer using open source components.
Rather than acting as an enterprise identity add-on like WorkOS, Supabase embeds authentication directly into the database and backend layer. It is often chosen by teams that prioritize database centric architectures over enterprise identity integrations.
Key capabilities
Email and password authentication with magic links and OAuth providers
Serverless Edge Functions for custom backend logic
Self hosted or fully managed deployment options
Postgres row level security for fine grained access control
SDKs for JavaScript, Flutter, and additional platforms
Strengths
Unified backend architecture: Authentication, database, and serverless functions work together with minimal integration effort.
Database level authorization: Row level security ties access control directly to Postgres, reducing the need for custom authorization services.
Deployment flexibility: Teams can choose managed hosting or self host for greater control over infrastructure.
Ideal for
Supabase is well suited for developers building Postgres based applications that want authentication tightly integrated with their backend. Teams evaluating WorkOS often consider Supabase when enterprise SSO and directory integrations are less important than unified tooling and open source flexibility.
Keycloak
Overview
Keycloak is a widely adopted open source identity and access management platform maintained by Red Hat. It provides built-in SSO, identity brokering, user federation, and an administrative console, offering a broader set of enterprise identity capabilities than WorkOS delivers out of the box.
Compared to WorkOS, which focuses on hosted SSO and SCIM building blocks, Keycloak gives teams full ownership of their identity stack. While it requires more operational effort and infrastructure management, it is often chosen for its extensibility, open source control, and ability to support complex federation and policy requirements.
Key capabilities
Single sign on support for OIDC, OAuth2, and SAML
Identity brokering with social and external identity providers
User federation with LDAP and Active Directory
Built in admin console and user self service portal
Strengths
Full platform control: Open source architecture allows deep customization and self hosting.
Enterprise federation support: Integrates with legacy identity systems and on premise directories.
Extensible architecture: Supports plugins and service provider interfaces for advanced customization.
Large open source community: Backed by broad adoption and ongoing contributions.
Ideal for
Keycloak is well suited for organizations that want complete control over their identity infrastructure and are willing to manage it themselves. Teams evaluating WorkOS often consider Keycloak when they need deeper federation, open source flexibility, or on premise deployment options beyond what hosted SSO tools provide.
Ory Kratos
Overview
Ory Kratos is an open source, API first identity and authentication service that serves as the core identity component of the Ory ecosystem. It is designed for teams that want to build and own their identity layer rather than rely on a hosted, enterprise focused service.
Beyond WorkOS’s managed enterprise abstractions, Ory Kratos offers low-level identity primitives for teams building custom architectures. This flexibility comes with increased engineering and operational responsibility, making it a strong option for teams that need custom identity architectures or self hosted deployments beyond the constraints of managed platforms.
Key capabilities
API driven identity and authentication primitives
Customizable login, registration, and account recovery flows
Self hosted or cloud managed deployment options
Integration with OAuth2 and authorization services through Ory components
Strengths
Deep customization: Identity flows and data models can be tailored to exact application requirements.
Open source control: Full visibility into code, behavior, and infrastructure.
Composable architecture: Works with other Ory components for OAuth2 and authorization.
Deployment flexibility: Supports self hosting for strict compliance or data residency needs.
Ideal for
Ory Kratos is well suited for engineering teams that want full ownership of their identity stack and are willing to manage infrastructure themselves. Teams evaluating WorkOS often consider Ory Kratos when they need deeper customization, self hosted identity services, or distributed architectures that exceed the scope of managed enterprise SSO tools.
Also Read: Why BalkanID Moved From Ory Kratos to Descope
FusionAuth
Overview
FusionAuth is a full featured customer identity platform that can be deployed as a managed cloud service or fully self hosted. It delivers a broad set of authentication and authorization capabilities, including native multi tenancy, advanced MFA, and event driven extensibility.
Compared with WorkOS’s SSO-centric approach, FusionAuth delivers a more complete identity platform. It is often chosen by teams that want stronger enterprise controls and the option to run identity infrastructure on their own terms.
Key capabilities
Support for OAuth2, OIDC, and SAML based enterprise SSO
WebAuthn, TOTP, SMS, and email based MFA options
Native multi tenant user, application, and role management
Event based customization using webhooks and serverless extensions
Strengths
Enterprise capabilities built in: Multi tenancy, SSO, and advanced MFA are included without relying on external services.
Flexible deployment models: Teams can choose managed cloud hosting or full self hosting.
Broad protocol support: Covers modern and legacy SSO standards for enterprise compatibility.
Extensible architecture: Event driven workflows enable customization without rewriting core systems.
Ideal for
FusionAuth is well suited for teams that want a comprehensive identity platform rather than standalone SSO building blocks. Organizations evaluating WorkOS often consider FusionAuth when they need deeper enterprise functionality, stronger authorization controls, and flexibility in how and where identity services are deployed.
Conclusion
WorkOS is a popular solution for adding enterprise SSO and SCIM quickly, but many teams eventually encounter limitations as their identity needs expand. Pricing at scale, limited orchestration, and a narrow feature focus often push developers to evaluate broader identity platforms.
Among the alternatives, Descope stands out for teams that want a unified, developer-friendly platform covering authentication, authorization, enterprise SSO, and orchestration in one system. By reducing custom code and centralizing identity logic, Descope helps teams scale faster with fewer long-term tradeoffs.
If you’re evaluating WorkOS alternatives, the right choice depends on how much flexibility, enterprise depth, and orchestration your product will require as it grows.
For more detailed information on Descope, check out our docs. If you'd like a demo, meet with our auth experts. Also, if you want to try Descope yourself, sign up for a Free Forever Account and start dragging & dropping your auth today!






