Drag & drop
CIAM
for any app
for any app
Reduce user friction, prevent account takeover, and get a 360° view of your customer identities with the Descope CIAM platform. Use visual workflows, SDKs, and APIs to create and customize the entire user journey for your external applications.
Powering auth for hundreds of customers and thousands of developers











Make your customer identity flow
Get an overview of the Descope CIAM platform in 90 seconds (almost as quick as it takes to build auth with us).

Power endless customer identity use cases
B2C CIAM
Improve onboarding and boost conversions with passwordless auth, A/B testing, anonymous user tracking, and more.
Learn moreB2B CIAM
Get enterprise-ready with self-service SSO and SCIM setup, seamless SSO migration, multi-tenancy, delegated admin, and FGA.
Learn moreATO prevention
Stop fraud, bots, stuffing, and hijacking attacks with strong MFA and a variety of native and third-party risk signals.
Learn moreIdentity orchestration
Turn customer identity into a business enabler with just-in-time provisioning, data syncs, and orchestration across 50+ third-party tools.
Learn moreIdentity federation
Achieve a 360 customer view by unifying identities across multiple apps and identity providers in real-time.
Learn moreAgentic IAM
Secure authentication and granular access control for APIs, AI agents, remote MCP servers, and more.
Learn moreOur no-code CIAM platform
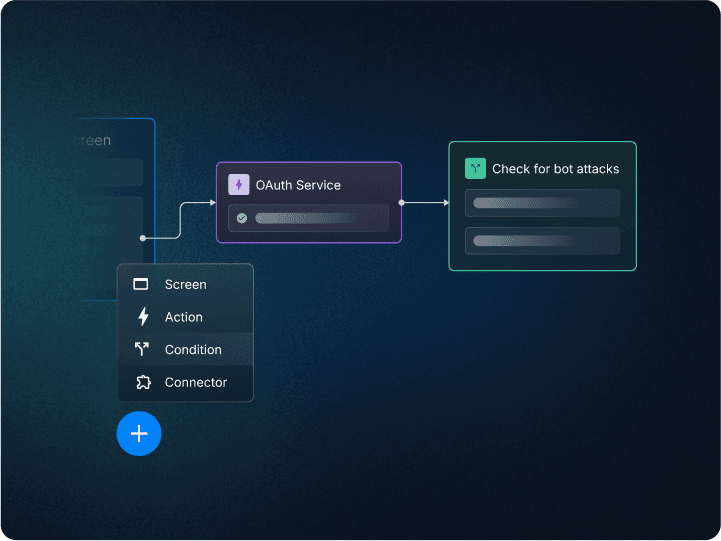
Drag & drop user journeys
Add signup, login, MFA, SSO, step-up, and a whole lot more with a flexible and easy to use workflow interface.
Frontend and backend
Govern both the frontend experience and backend logic from one workflow.
Your screens, your brand
Design beautiful user-facing screens with granular styling controls.
Modify with ease
Make changes to your authentication flows without touching your codebase.
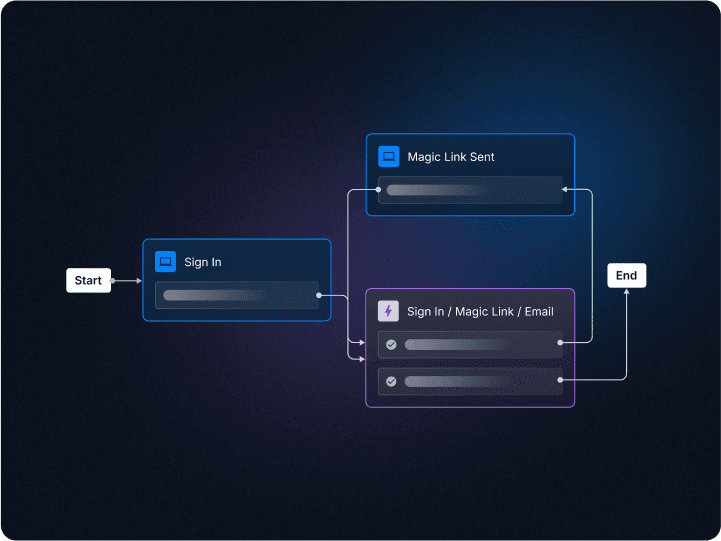
Complete user management
Manage, merge, and sync identities across the user journey.
Accurate user data
Verify user identifiers like email IDs and phone numbers. Securely merge user identities across auth methods.
Fine-grained authorization
Add granular access control capabilities (RBAC, ReBAC, ABAC) to your app.
Customizable self-service experiences
Empower your end users to manage profiles, users, roles, access keys, audits, and SSO configuration on their own.

Security minus friction
Add security controls at the right time instead of every time.
Prevent account takeover
Reduce the likelihood of phishing and credential stuffing attacks with strong passwordless authentication.
Adaptive MFA
Enforce MFA only for risky logins using native and third-party risk signals.
When in doubt, step-up
Easily add step-up authentication before sensitive in-app actions.
Why customers choose Descope
Fast
Set up and migrate in days and weeks rather than months and years with visual workflows.
Flexible
Choose from flows, SDKs, and APIs. Rip-and-replace or augument what you already have.
Future-proof
Change users journeys without redeploying your app or tinkering with your codebase.
We play well with others
Enrich and secure your user journeys with third-party connectors. Go passwordless without changing your primary IdP using OIDC federated authentication.
Auth that meets devs where they are
Code as much (or little) as you want. Your choice: no-code workflows, SDKs / APIs, and everything in between.
Descope SDKs
“I’ll build the authentication screens and flows, but may need help with session management.”
Explore SDKsReady for liftoff?
If you’ve seen all you need to see, sign up and get started with Descope. If you'd like a demo, meet with our auth experts.
































