Frictionless and secure B2C CIAM platform
Simplify user onboarding and increase conversions with passwordless authentication.
Create and customize the entire user journey with drag-and-drop workflows.
Reduce fraud and account takeover without impacting the experience of real users.
From scratch to magic in 10 minutes
Using a sample ecommerce app, the video below shows how you can use Descope Flows to add passwordless user journeys in minutes.

Descope for B2C applications
Passwordless authentication
Boost conversions and block threats with passkeys, magic links, Google One Tap, and more.
Validated identities
Ensure clean, accurate user data by verifying user emails or phone numbers (including for guest checkouts).
Omnichannel user experience
Provide a unified experience across websites, mobile apps, and even WordPress and Shopify sites.
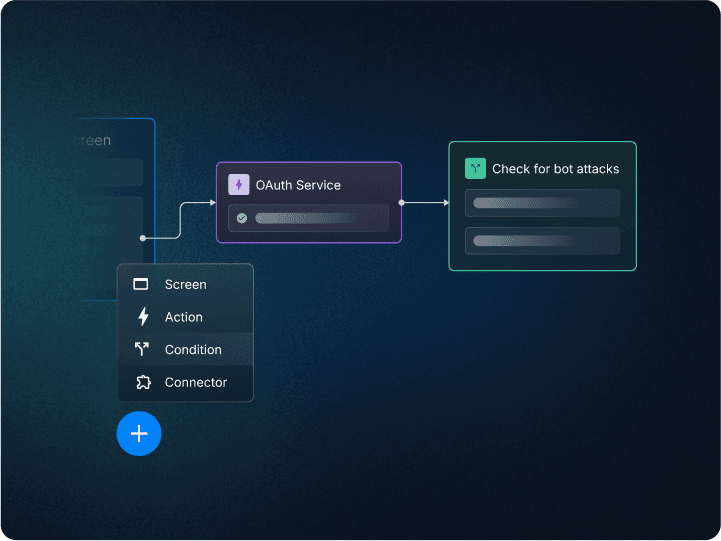
Fraud and bot prevention
Use native signals and 50+ third-party connectors to stop bots and enforce MFA for risky logins.
Our no-code CIAM platform
Drag & drop user journeys
Use a visual workflow interface to create and customize user journeys including signup, login, MFA, and step-up.
Frontend and backend
Govern both the frontend experience and backend logic from one workflow.
Screens your users will love
Design authentication and user-journey screens in a widget-based screen builder.
Align with your brand
Add your brand’s logo, colors, and several other design elements to make user-facing screens your own.
Flexible and adaptable user management
Manage, merge, and sync identities across the user journey.
Self-service profile management
Empower your end users to manage their own profile, reset passwords, change auth methods, and more with a fully customizable widget editor.
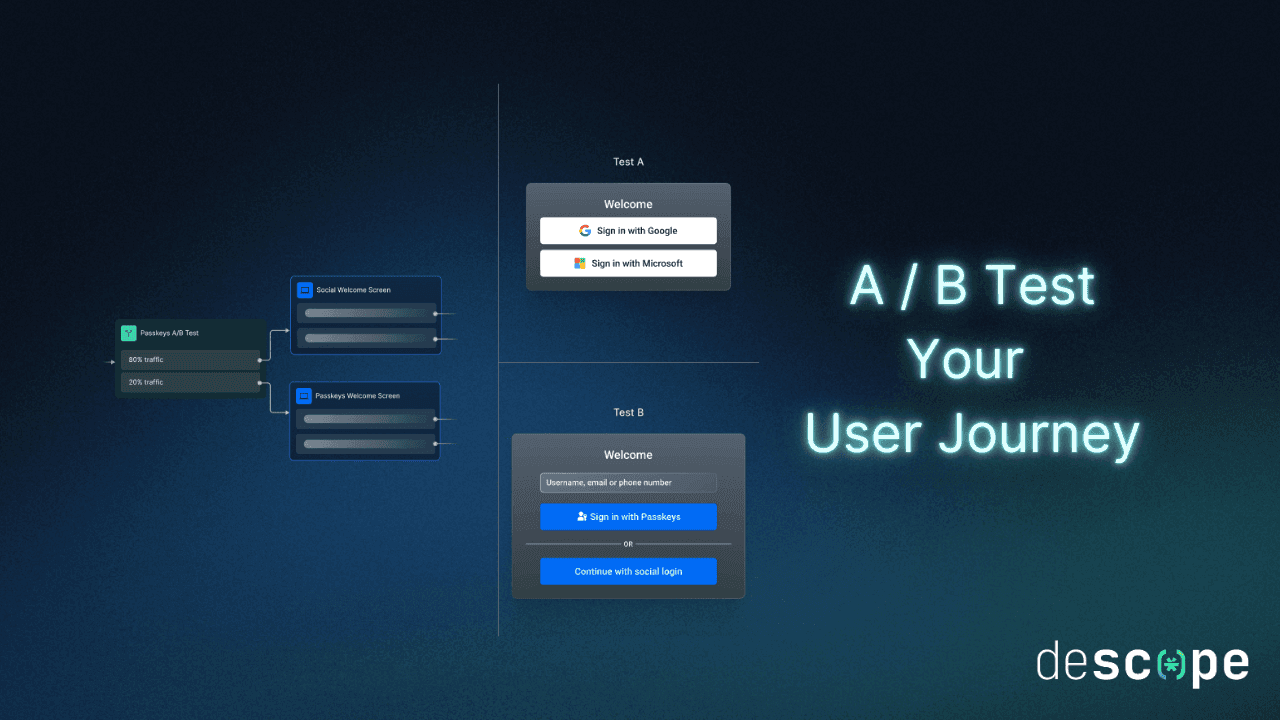
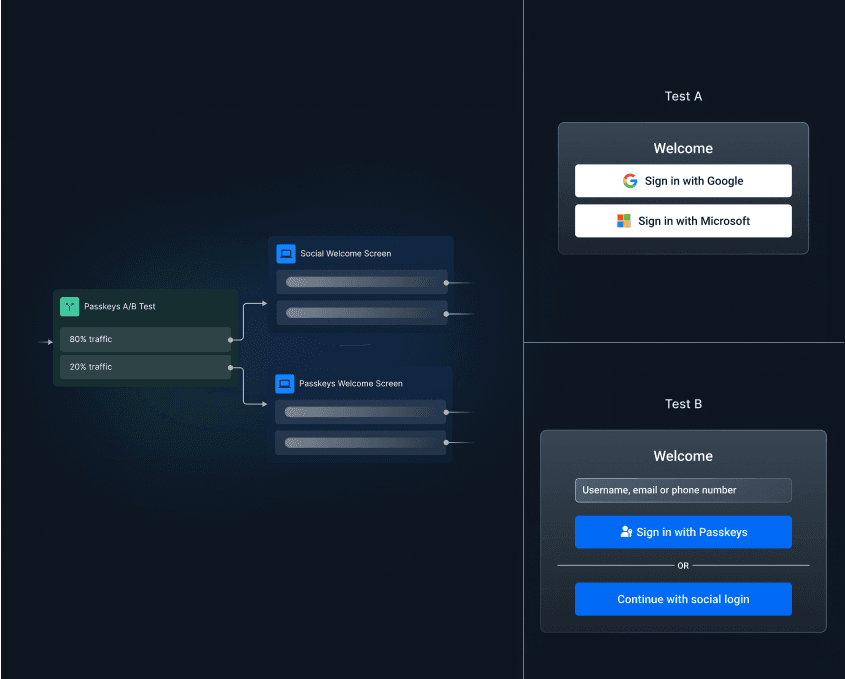
Experiment with your auth flows
Split user traffic to easily run A / B tests between different auth methods, designs, and onboarding paths.
Analytics
Gain insight into new users, active users, popular devices, and step-by-step user journey drop offs for your app.
Security minus friction
Stop account takeover and bot attacks without adding undue friction for real users.
Avoid password-based attacks
Eliminate brute force and credential stuffing attacks with strong passwordless authentication.
Identify risky user signals
Leverage device fingerprinting and third-party fraud connectors to accurately separate real users from bad actors.
When in doubt, step-up
Create step-up authentication and risk-based MFA flows to ensure your users are always who they say they are.
More B2C auth resources
We play well with others
Enrich and secure your user journeys with third-party connectors. Go passwordless without changing your primary IdP using OIDC federated authentication.
Auth that meets devs where they are
Code as much (or little) as you want. Your choice: no-code workflows, SDKs / APIs, and everything in between.
Descope SDKs
“I’ll build the authentication screens and flows, but may need help with session management.”
Explore SDKsReady for liftoff?
If you’ve seen all you need to see, sign up and get started with Descope. If you'd like a demo, meet with our auth experts.