Table of Contents
Identity security: the missing piece in the AI and MCP puzzle
Hello Descopers! We’re delighted to share the Agentic Identity Control Plane with you today to provide security teams with policy-based governance, robust auditing, and end-to-end identity lifecycle management for their AI agents and MCP ecosystems. The Agentic Identity Control Plane builds upon the Descope Agentic Identity Hub announced earlier this year to mark a huge step forward in Descope’s vision of becoming the identity provider for AI agents.
Any developer can start using these Descope capabilities today, including those on our Free Forever tier. Visit our docs to learn more, and sign up or book a demo with our team to get started.
For more on the Why, What, and How of the Agentic Identity Control Plane, keep on reading!
Identity security: the missing piece in the AI and MCP puzzle
AI agents are already succeeding in real-world tasks. GitHub Copilot can autocomplete full functions, write tests, and flag security issues. Claude can generate multi-file PRs or explain unfamiliar code. Elsewhere, AI agents are summarizing meetings, resolving customer support tickets, drafting contracts, and automating research. But a look under the surface reveals spotty adoption outside of early adopters – and security worries are the main driver of uncertainty.
56% of developers cited having security and privacy concerns when using AI agents in the Stack Overflow 2025 Developer Survey. These concerns are warranted, with a Replit agent recently deleting a company’s production database by running unauthorized commands.
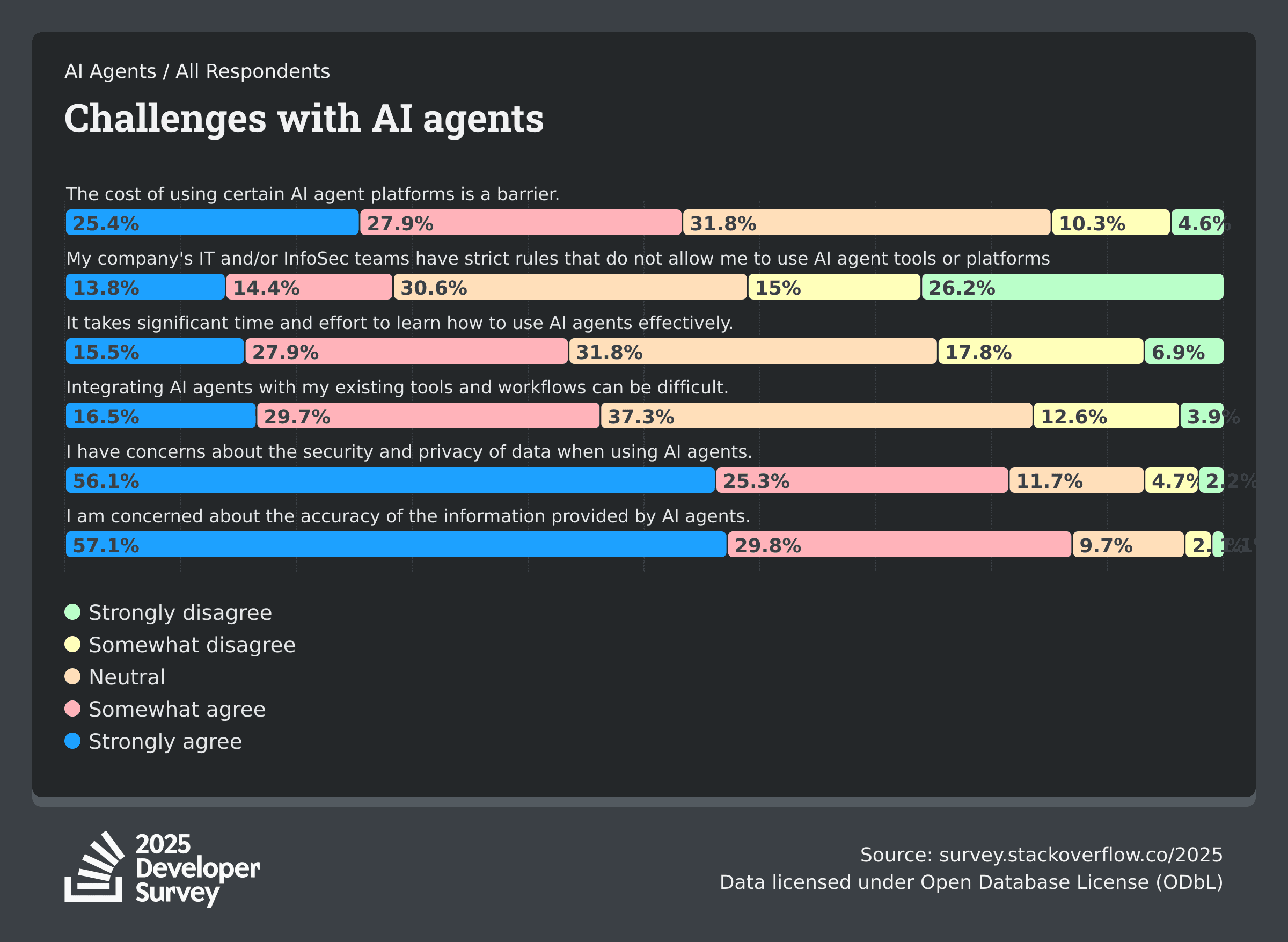
The state of Model Context Protocol (MCP) servers is similar. While over 5000 Model Context Protocol (MCP) servers are already part of a thriving ecosystem, nearly 2000 of them possess no security whatsoever and there is already emerging research about hundreds of MCP servers being vulnerable to tool poisoning, data exfiltration, and malicious backdoor entry.
Security teams face a dilemma: no CISO wants to block the adoption of agentic AI and MCP at their company, but they are also tasked with containing the risk that arises with every new AI agent or MCP server created within their organization or connecting with their products.
This is where the Agentic Identity Control Plane comes in.
Agentic Identity Control Plane overview
The Agentic Identity Control Plane is a suite of capabilities that arm security teams with policy-based governance, auditing, and lifecycle management for AI agents and MCP clients / servers, whether they are used by employees at their organization or by external users connecting to their products. It builds upon existing Descope capabilities of Inbound Apps and Outbound Apps to allow the enforcement of identity security guardrails without hindering AI adoption.
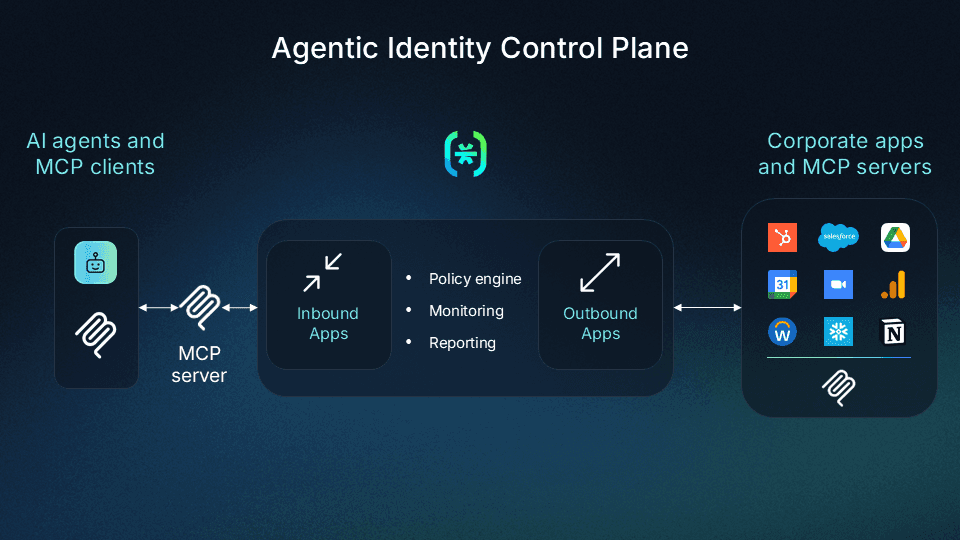
Security teams can now:
Apply scope-based access control to control how AI agents and MCP clients access corporate apps, third-party apps, and MCP servers.
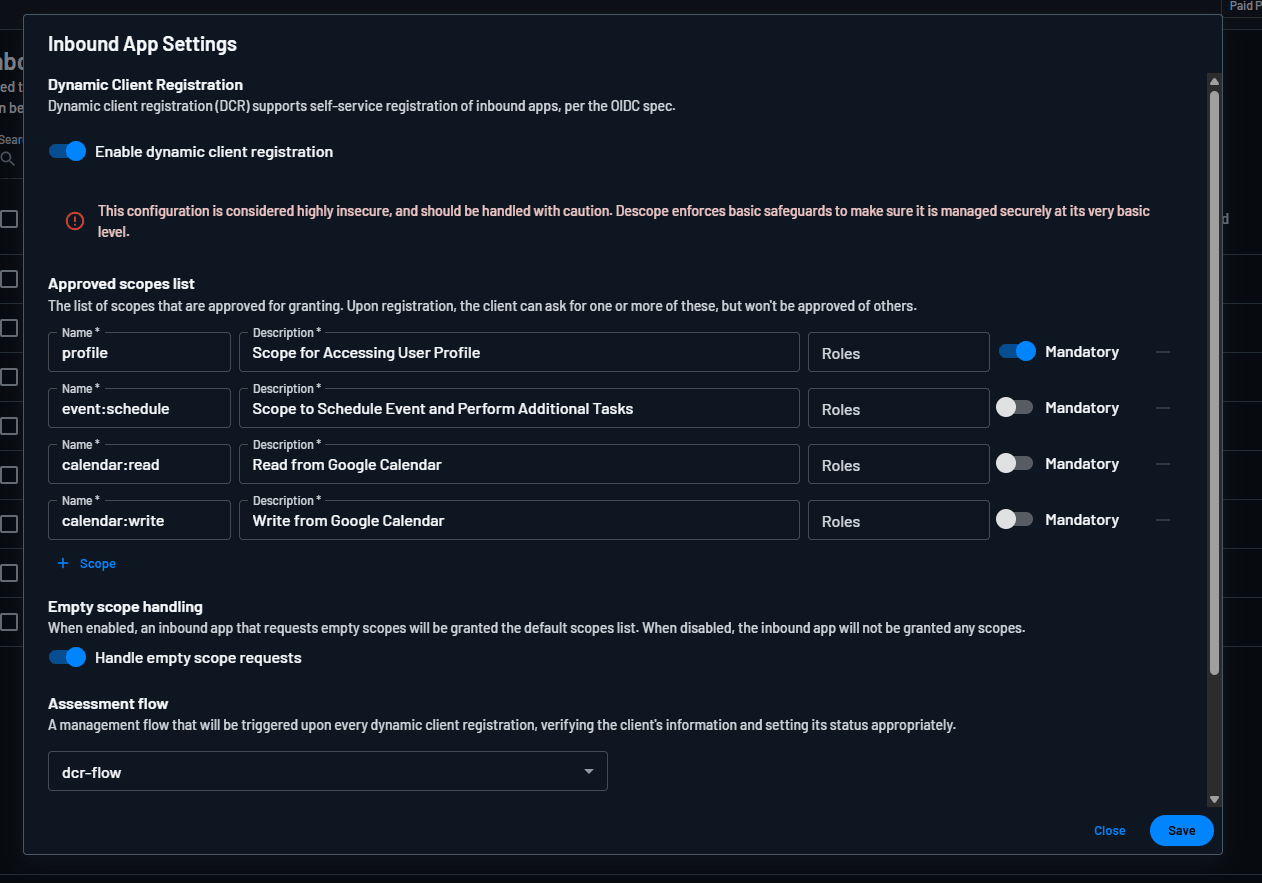
Add access policies for specific AI agents, verified AI agents, and all AI agents created via Dynamic Client Registration (DCR).
Govern AI agent access to specific scopes within specific corporate apps based on user roles.
Enforce rules and grant scopes based on user JWT claims.
Monitor granular audit events on consents granted and AI agent app connections.
Stream audit events to services such as Amazon S3, Datadog, New Relic, etc.
Use cases
Let’s say an organization has AI agents that can be accessed by both internal and external stakeholders and that these AI agents need to connect to Google Calendar and Gmail to perform certain tasks. We’ll now go through some use cases to highlight the power of the Agentic Identity Control Plane.
Restricting access for AI agents created through DCR
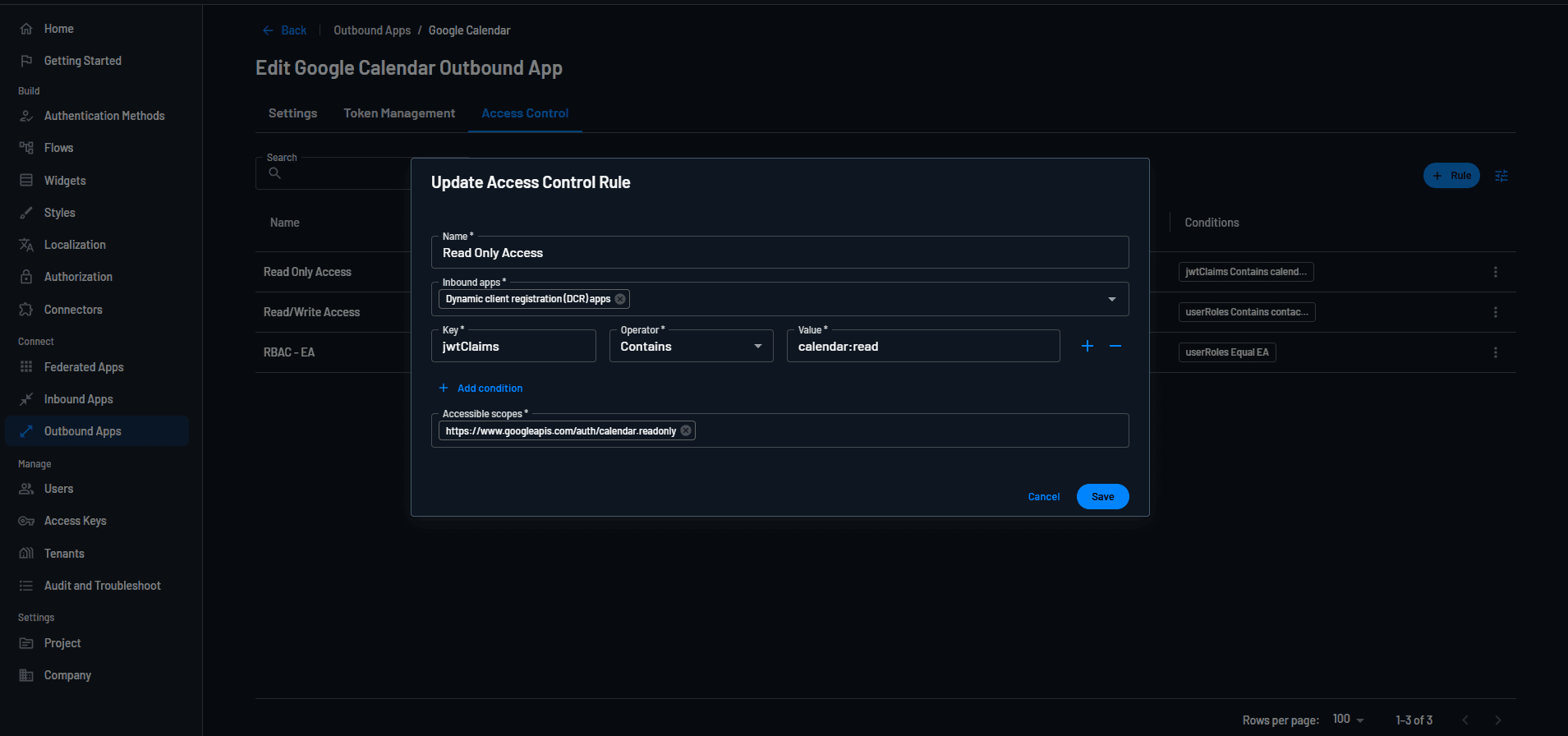
AI agents or MCP clients that connect via DCR do so at high volumes and often tend to be unverified. Customers can create access control rules specifically for AI agents created via DCR and restrict access to minimum viable scopes in external tools.
The screenshot below shows an access control rule that applies to any AI agent connecting via DCR. The rule checks if the JWT claim includes the calendar:read scope and provides read-only access to Google Calendar if so.
Handling unverified AI agents
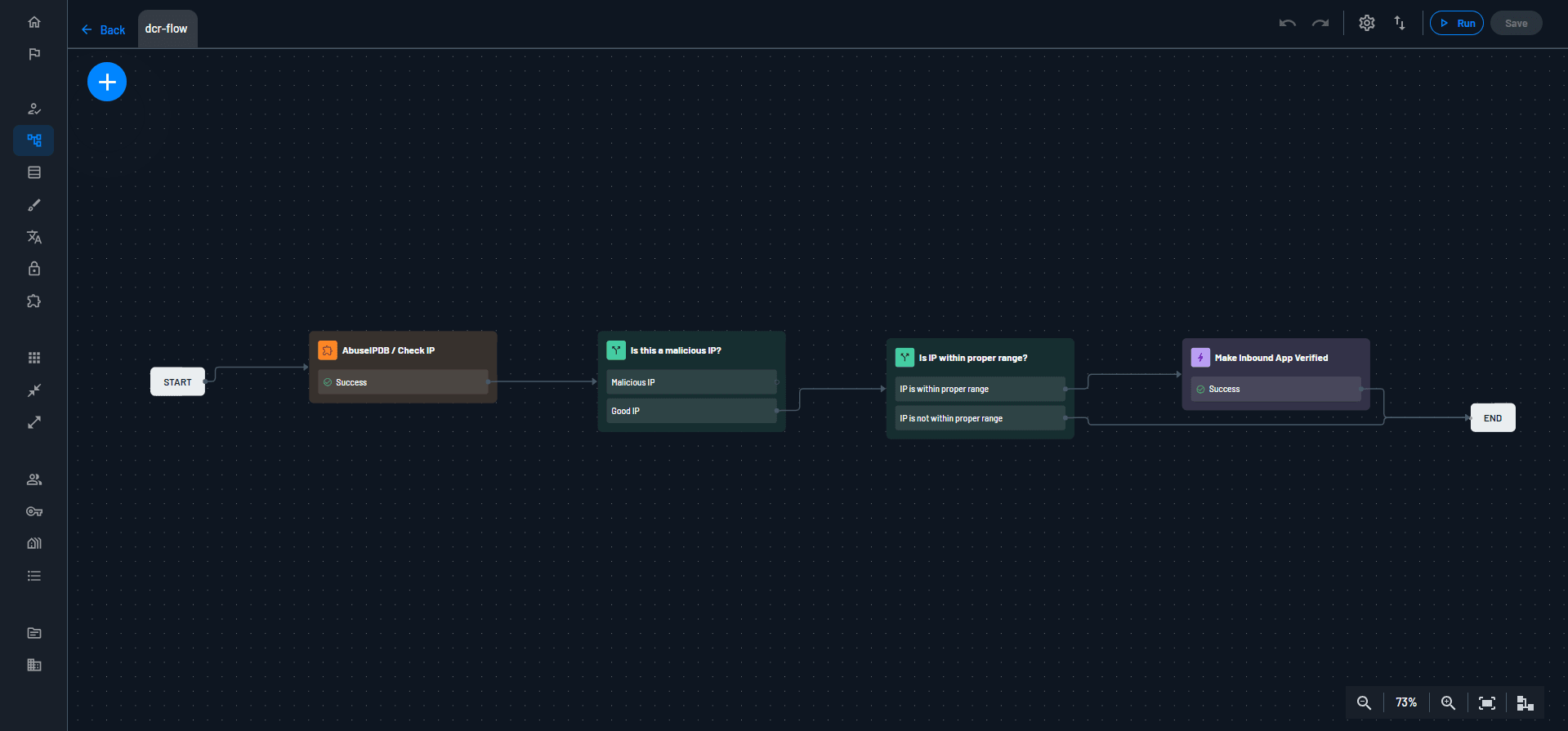
Organizations want to open up their systems to AI agents, but not any AI agent. Customers can use Descope to differentiate between verified and unverified agents and enforce different access control rules accordingly.
The screenshot of the Descope Flow below shows one way to check if the AI agent is verified: by utilizing our AbuseIPDB connector to check for malicious IPs and checking if the request is coming from an approved IP range. If these criteria are met, the AI agent / MCP client is marked as verified.
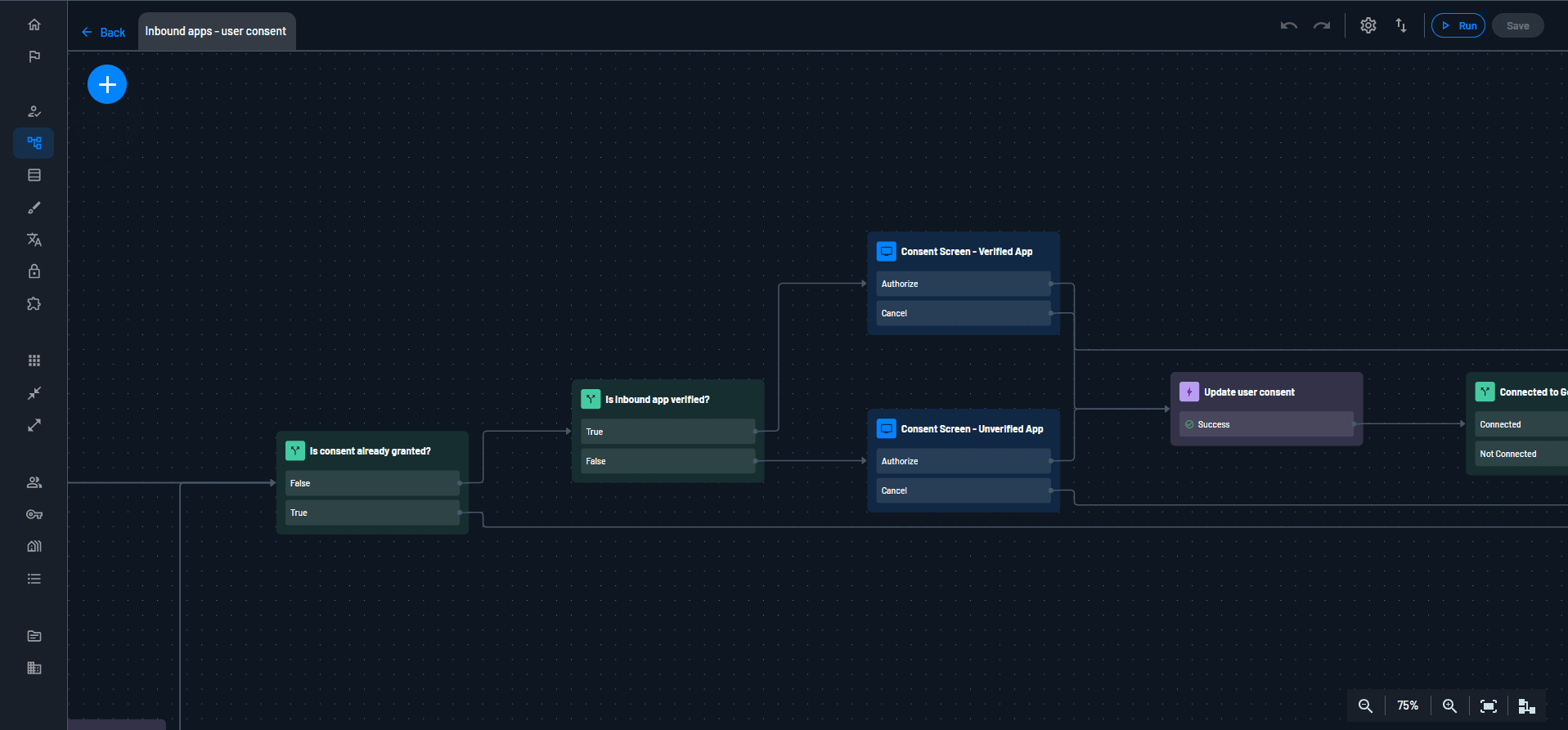
The Descope Flow below shows how two different consent screens can be shown to the user based on whether the AI agent is verified or not.
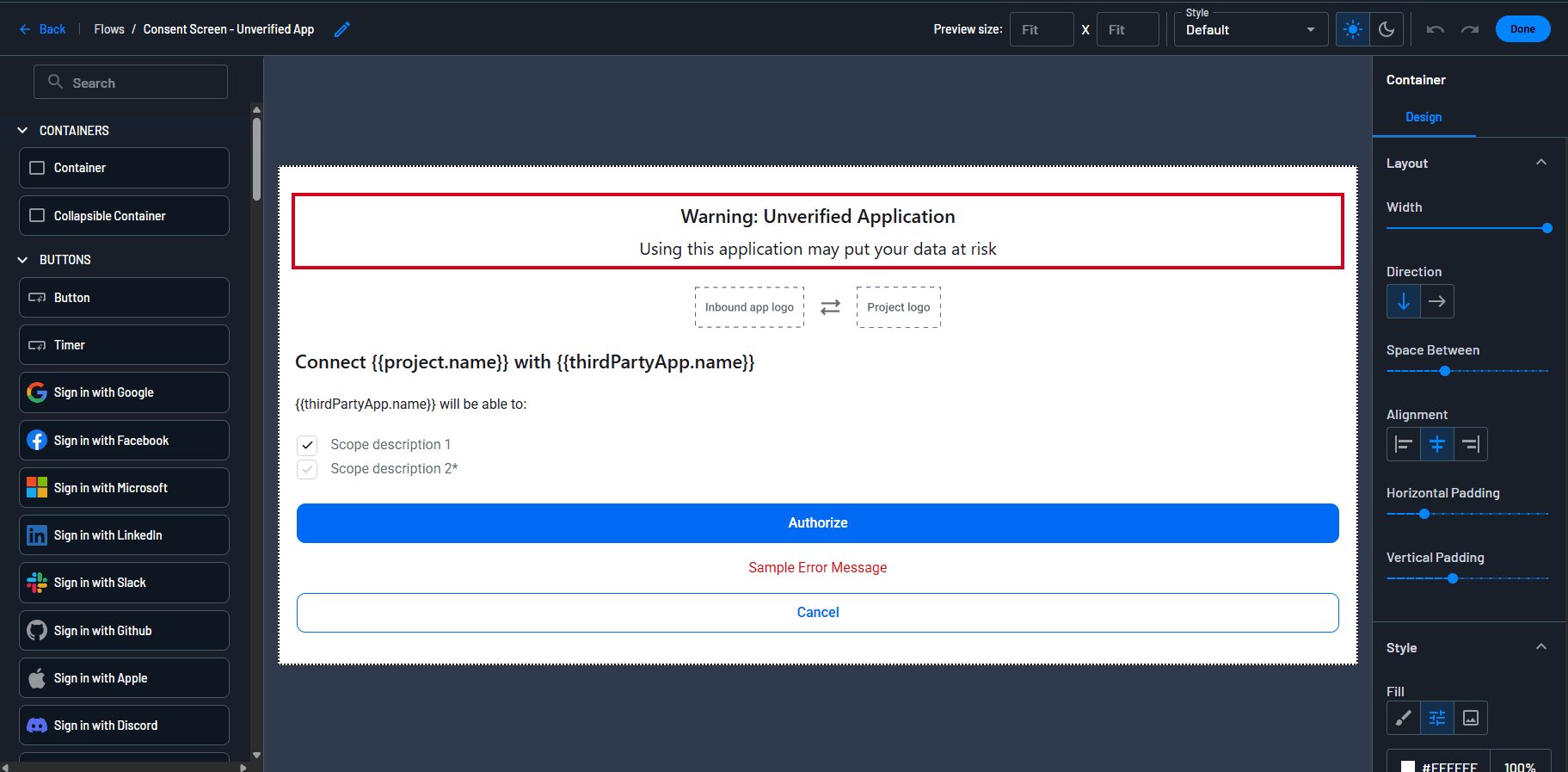
Consent screens for unverified AI agents can come with warning messages to provide users with the appropriate level of context and caution.
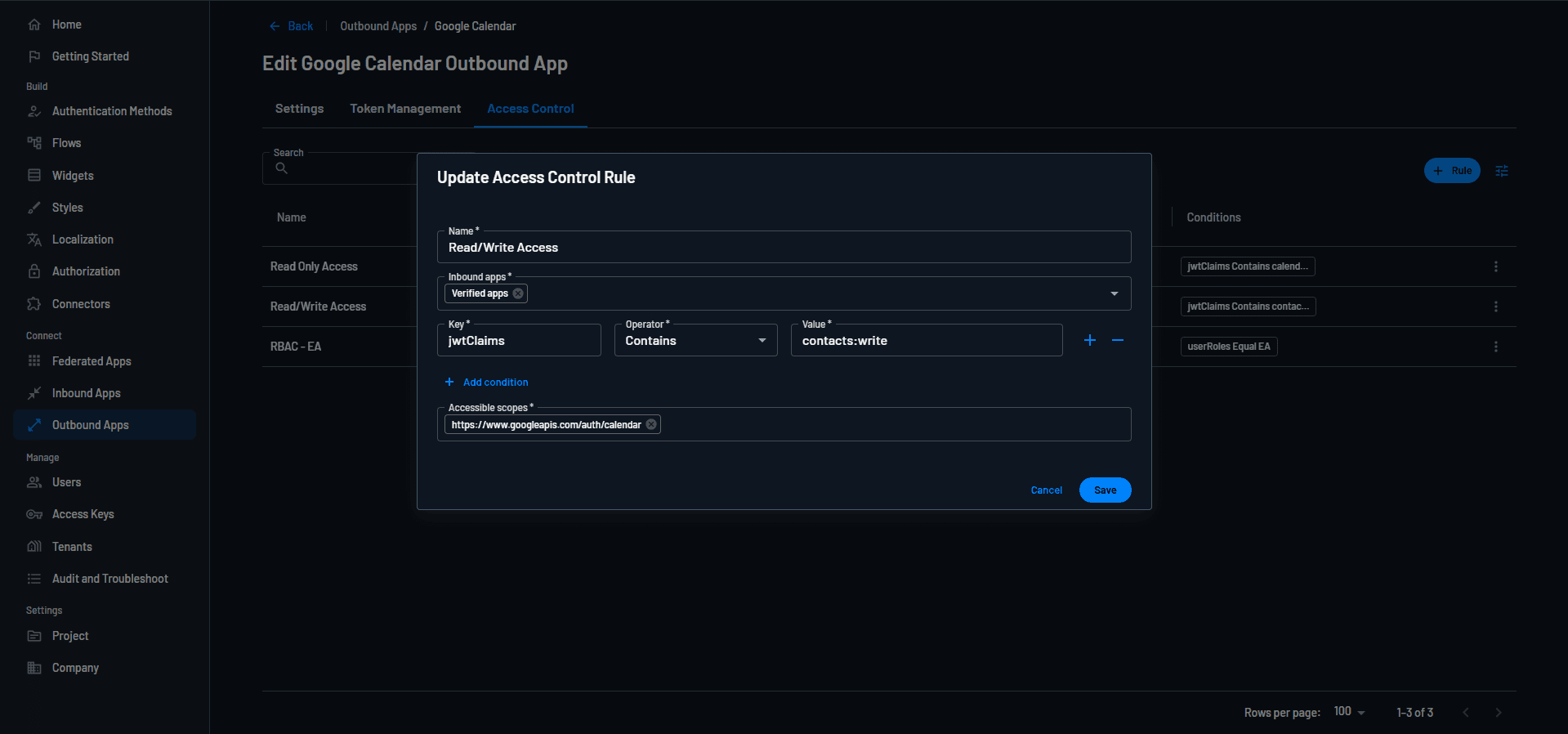
Universal access control rules can be created for verified AI agents. The screenshot below shows an access control rule that applies to all verified AI agents. The rule checks if the JWT claim of the AI agent’s Inbound App includes the contacts:write scope and provides read / write access to Google Calendar if so.
AI agent access based on user roles
AI agent permissions should always be a subset of the permissions of their “bound user” i.e. the user on behalf of which the AI agent is performing any task. Since user permissions are already available to organizations through their roles or SSO groups, Descope customers can now create access control rules that govern AI agent access to third-party tools based on user roles.
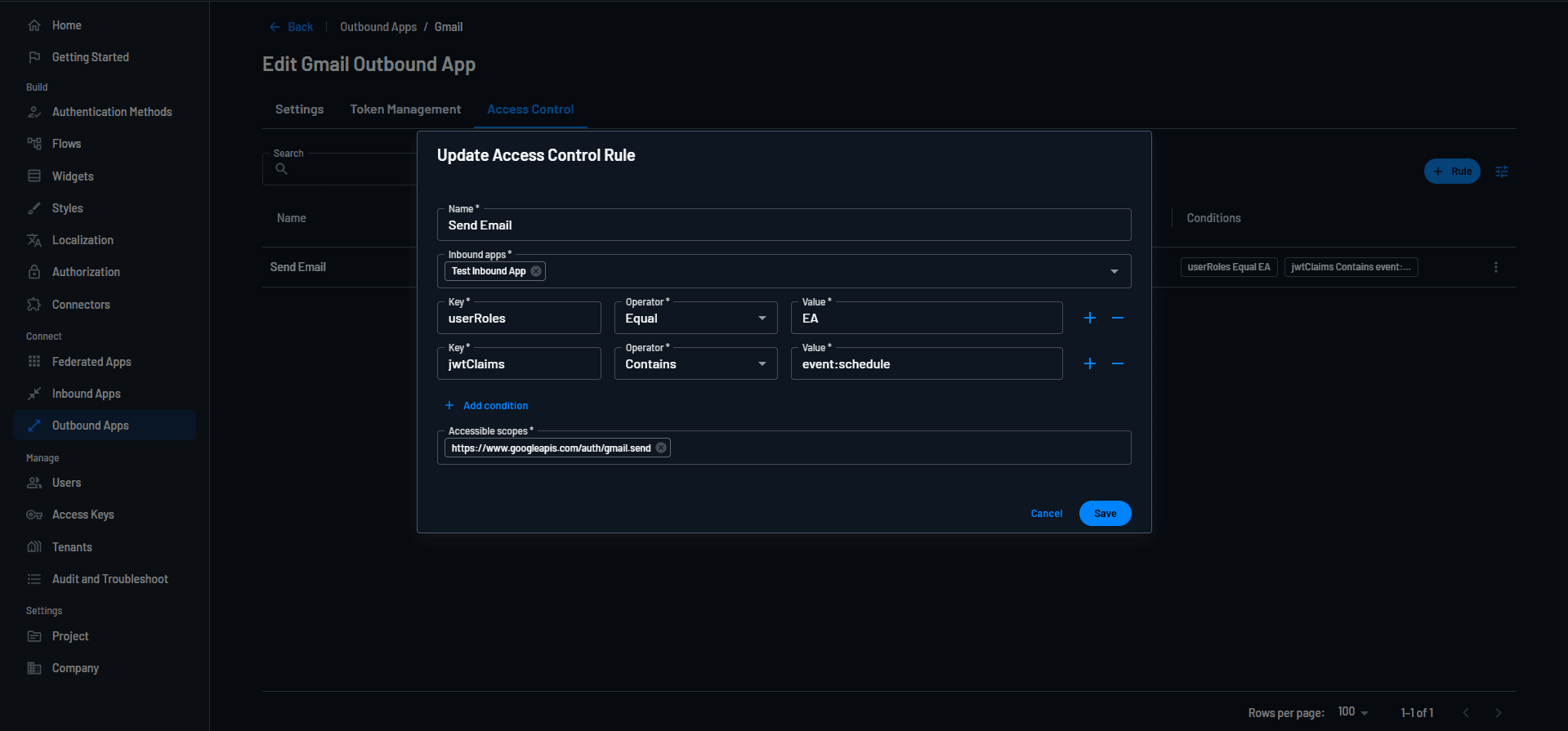
Let’s say there’s an AI agent that schedules meetings and sends emails on the user’s behalf. It’s reasonable for executive assistants (EAs) to use this AI agent and provide it with the ability to send emails. The screenshot below checks if the user role is EA and if the JWT claims include the required values–if they do, the AI agent gets the appropriate Gmail scope to send emails on the user’s behalf.
AI agent identity lifecycle management with Descope
Descope’s agentic identity capabilities now enable customers to enact end-to-end identity lifecycle management for AI agents, MCP clients / servers, and other AI systems.
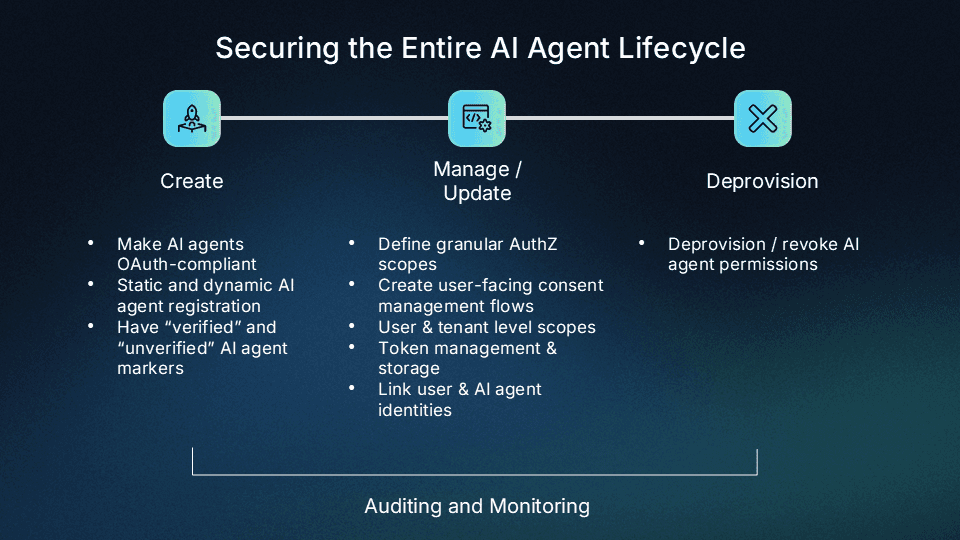
Create
Organizations can open up their applications to AI agents while adding essential security and identity controls to ensure safe adoption.
Protecting AI agents, MCP clients / servers, and APIs with OAuth using Inbound Apps.
Additionally, protecting MCP servers with OAuth using MCP Auth SDKs.
Enabling static and dynamic AI agent registration.
Instituting processes for verifying AI agents.
Adding differing levels of access control for verified and unverified AI agents.
Manage and monitor
Organizations can deliver authorization flows that provide AI agents with the minimum viable permissions they need to do their task, keep users in the loop, save developer time, and provide critical security visibility.
Defining granular scopes for every Inbound App and granting consent on a user or tenant level.
Creating customizable user consent management flows.
Offloading token management and storage for AI agent connections with external tools using Outbound Apps.
Leveraging detailed audits of every consent granted, agent-app connection, and modification action.
Detecting agent-to-app connection requests that were blocked by access control policies to identify potentially rogue AI agents.
Deprovision
Visibility is incomplete without mitigation–Descope customers can easily revoke any granted AI agent permission, downgrade AI agents to unverified, and completely deprovision the Inbound App for the AI agent if needed.
Conclusion
A survey of 400+ IAM-decision makers commissioned by Descope found that 95% consider authentication and access control to be critical for secure AI adoption. The Agentic Identity Control Plane provides the necessary security tools to make this a reality. Visit our docs to learn more.
Sign up or book a demo with our team to start your journey towards secured, scoped, and consented access for your AI agent and MCP ecosystem.