Table of Contents
About Bitsight Threat Intelligence
Cyberattacks rarely begin at the login page. They often originate in hidden parts of the internet where credentials are leaked, malware is distributed, and threat actors coordinate their activity. To effectively defend against account takeover, credential stuffing, and insider threats, authentication flows must incorporate external risk signals.
With the Descope and Bitsight Threat Intelligence (formerly Cybersixgill) connector, teams can bring threat intelligence directly into their customer identity workflows. This allows them to surface leaked credentials, enrich suspicious indicators, and respond to emerging risks in real time.
About Bitsight Threat Intelligence
Bitsight is a leader in threat intelligence, delivering deep and dark web insights that help organizations stay ahead of cybercriminals. The platform continuously collects information from closed forums, messaging platforms, code repositories, and marketplaces, transforming raw data into actionable context.
Security teams use Bitsight to detect credential leaks, monitor brand mentions, enrich indicators of compromise (IOCs), and track malicious actors, often identifying threats before a breach occurs.
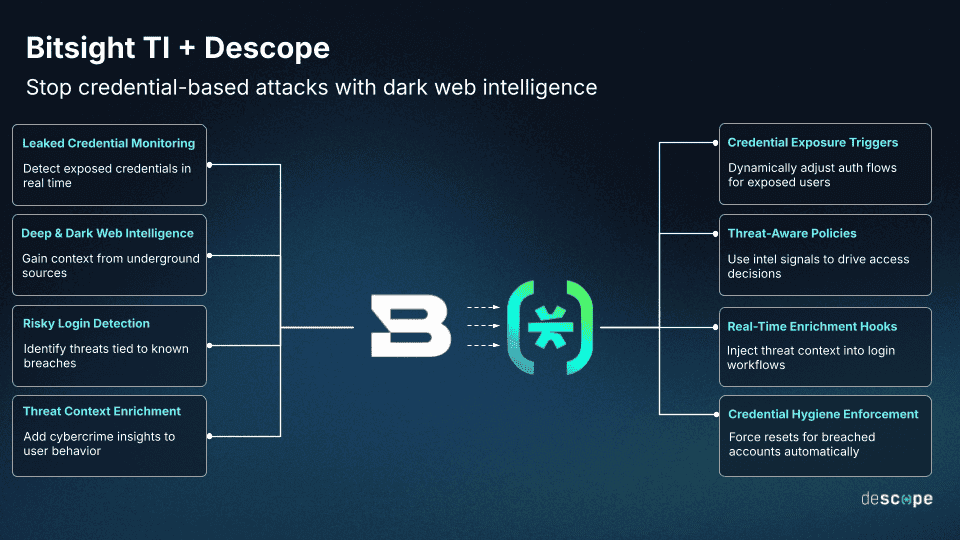
Connector overview
The Descope + Bitsight TI connector provides developers with actionable threat intelligence inside identity flows using the following actions:
Bitsight / Search Leaked Credentials: Check if an email address or domain has been exposed in breach dumps across a specific timeframe—perfect for evaluating login or signup risk.
Bitsight / Enrich IOC: Get STIX-formatted data about a suspicious IP, domain, or hash—ideal for detecting whether an entity is associated with malware, APTs, or criminal campaigns.
These commands can be used in Descope’s no-code Flow builder or with custom logic. They also pair seamlessly with other integrations like Forter, Fingerprint, and Telesign to build layered identity defenses.
Use case: Block risky logins using leaked credential checks
Account takeover attacks are one of the most pervasive and costly threats facing organizations today. In fact, ATO fraud caused over $15 billion in losses in 2024, according to the AARP Identity Fraud Report, driven largely by credential reuse and dark web exposure. Threat actors commonly leverage breached usernames and passwords to gain unauthorized access to user accounts, often going undetected until damage is done.
Despite the rise of MFA and passwordless strategies, many organizations still lack visibility into whether user credentials have already been compromised elsewhere. That’s where Bitsight TI comes in.
By integrating leaked credential checks directly into the login flow, security teams can identify high-risk logins before granting access without disrupting trusted users.
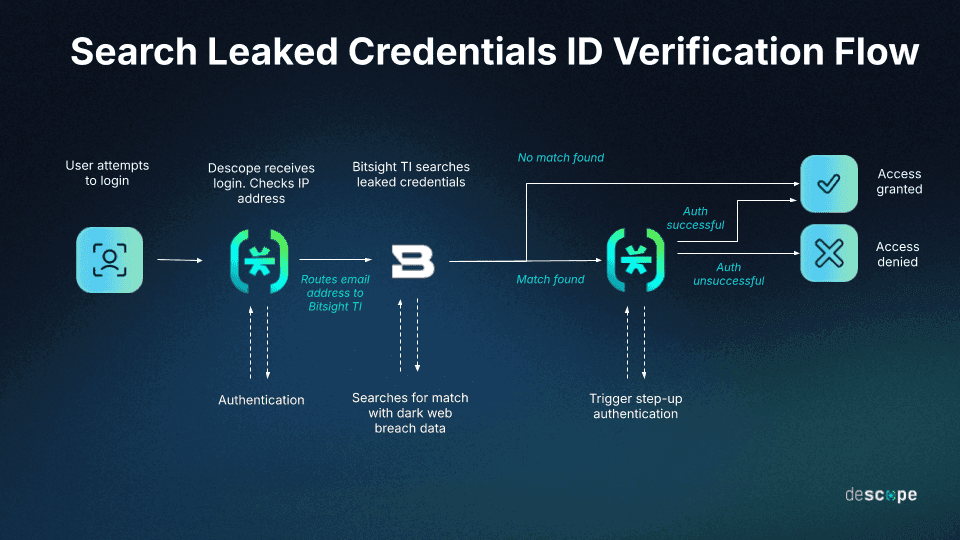
An example of a flow where leaked credentials are checked is below:
A user logs in with their email address.
Descope calls Bitsight TI / Search Leaked Credentials to check if the email has appeared in dark web breach data.
If a match is found, Descope can trigger step-up authentication, notify the user, or block access entirely.
If no exposure is detected, login continues as usual.
This flow helps organizations stay one step ahead of ATO attempts by identifying compromised users early and adapting defenses in real time.
Use Case: Enrich suspicious indicators with threat context
Modern attackers often use infrastructure that has already been flagged in threat intelligence databases. In 2024, more than 80 percent of breaches involved indicators of compromise (IOCs) that could have been identified and acted on beforehand, according to IBM’s Cost of a Data Breach Report.
Despite this, many identity systems ignore the context around suspicious IP addresses, domains, or file hashes during login attempts. Without access to real-time threat intel, organizations risk granting access to users who are actually operating from known malicious infrastructure.
With Bitsight TI’s IOC enrichment integrated into Descope Flows, developers can assess whether login activity is associated with known threats and make smarter access decisions instantly.
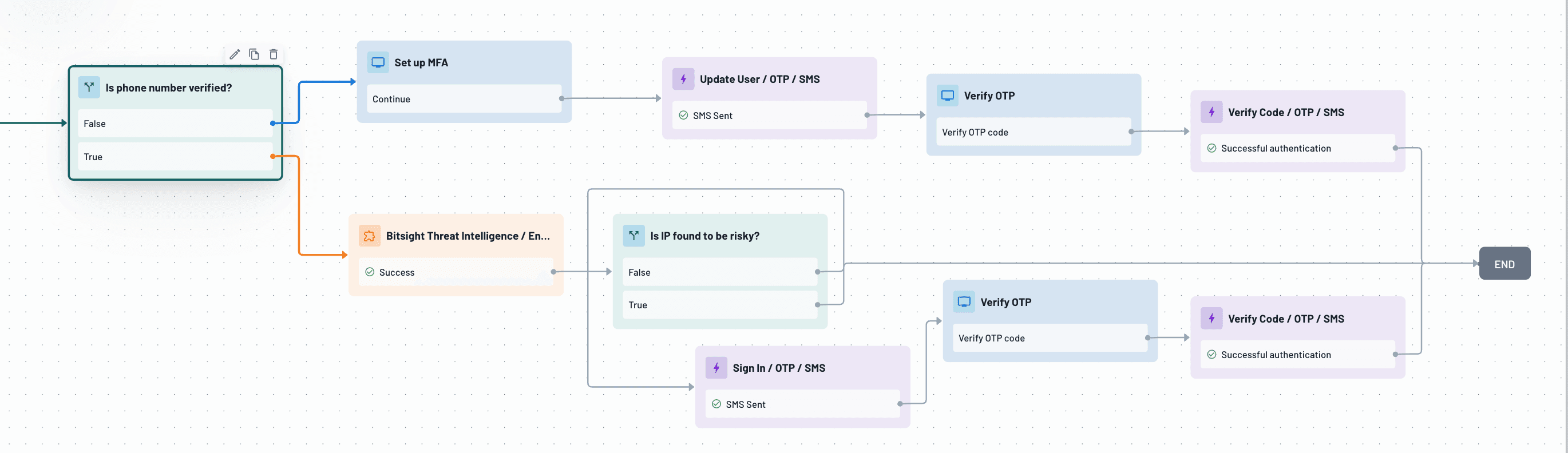
Below is an example of a Descope Flow using Bitsight TI to pull threat intel during a login attempt:
A user attempts to log in from an unfamiliar or high-risk IP address.
Descope calls Bitsight TI / Enrich IOC to pull threat intelligence for the IP, domain, or other indicator.
If the IOC is linked to malware, threat actors, or other threats, a one-time password (OTP) via SMS is sent.
If no threat is detected, login proceeds as normal.
This use case allows identity teams to apply the same level of threat intelligence used by security operations centers, helping to stop breaches before they start.
Get started today by using the Adaptive MFA with Bitsight TI IP check Flow Template, available directly in the Descope Console.
Conclusion
The Descope Bitsight TI connector helps teams inject intelligence into every identity decision, blocking risky users, investigating anomalies, and preventing ATO before it starts. By combining authentication and threat intel, security becomes proactive instead of reactive.
Interested to learn more about the connector? Check out our docs. If you haven’t yet started your Descope journey, sign up for a Free Forever account and set up your own Bitsight connector. To explore other connectors, visit our integrations page.






