Table of Contents
Implementing Descope for a CrewAI Application
A single AI agent can summarize, analyze, or plan, but it struggles to scale across domains, maintain context, or specialize deeply enough for complex enterprise use cases. Multi-agent systems address these gaps by distributing responsibility across many specialized agents. Instead of asking one model to do everything, individual agents receive a defined role and scope. Each agent executes its part before results are stitched together. This avoids overload, reduces errors, and produces better outcomes than a single agent working alone.
Case in point: The CrewAI multi-agent platform structures multi-agent systems much like real-world teams. This design keeps workflows clear, predictable, and scalable while exposing the practical challenge of managing identity and access. But once you’ve got agents interacting, you need to think about safe and reliable orchestration: authentication, identity, permissions, and secure communication.
Enter the Descope Agentic Identity Hub, which helps you manage identity and access control for all agents in such a multi-agent system. Each agent can be managed and assigned the relevant permissions to perform exactly the tasks they are designed for and nothing more.
Let’s put this in practice!
Implementing Descope for a CrewAI Application
To make this concrete, there’s a working example that ties everything together. You can follow the steps in this tutorial, or check out the finished sample app to see the complete implementation in action.
Here’s what we’ll be implementing:
A CrewAI crew with two different agents corresponding to two independent tasks: Calendar and Contacts
Descope Outbound apps for each API with defined OAuth scopes. Each agent will have its own scope and will only be able to perform actions based on these scopes.
User consent flows for granular permissioning
Backend session validation and secure token exchange
A unified output from the crew that combines results from both agents
Prerequisites
You’ll need the following tools:
A Descope account: If you don’t already have one, you can sign up for a Free Forever account.
Google Cloud APIs: Calendar and People/Contacts APIs
CrewAI: Python framework for multi-agent workflows
Python HTTP library: For API requests (requests, http, etc.)
A simple React frontend to connect the backend to
Watch the video below or carry on reading!
Configure Google OAuth credentials
For using google contact and calendar APIs, you need to set up google OAuth credentials.
Create OAuth credentials in the Google Cloud Console for the APIs your agents will access.
Go to your Google Cloud Console > APIs & Services > Credentials.
Create a new OAuth Client ID for each service: one for Calendar, one for Contacts.
Copy the Client ID and Client Secret for each app.
Add Authorized redirect URIs pointing back to your Descope Outbound app configuration.
Add Outbound Apps in Descope
Next, configure the outbound apps inside Descope so that each agent can request access tokens for its task.
In the Descope Console, go to Outbound Apps.
Add Google Calendar and Google Contacts as new apps.
Paste the Client ID and Client Secret from Google for each app.
Set the redirect URIs to match the Google configuration.
The Descope docs provide more detailed instructions on how to set up outbound applications.
While setting up outbound applications, pay attention to scopes. Scopes determine exactly what each agent can access. Configuring scopes in Descope rather than in code makes it easy to audit and update them later.
For this tutorial, we need two sets of scopes:
Calendar app: https://www.googleapis.com/auth/calendar.readonly and https://www.googleapis.com/auth/calendar (so the calendar agent can read existing events and create new ones)
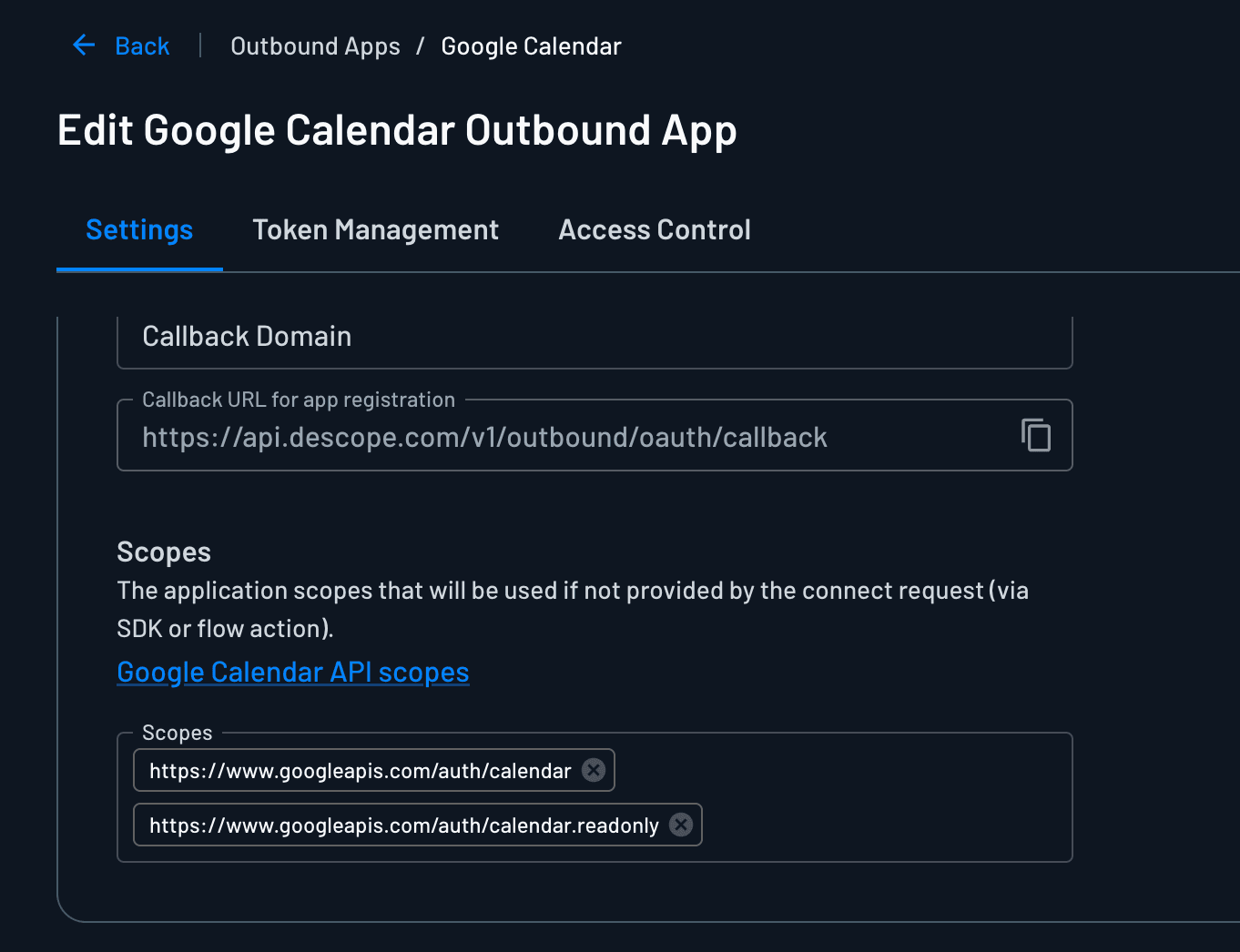
Contacts app: https://www.googleapis.com/auth/contacts.readonly (so the contacts agent can look up user contacts but not modify them)
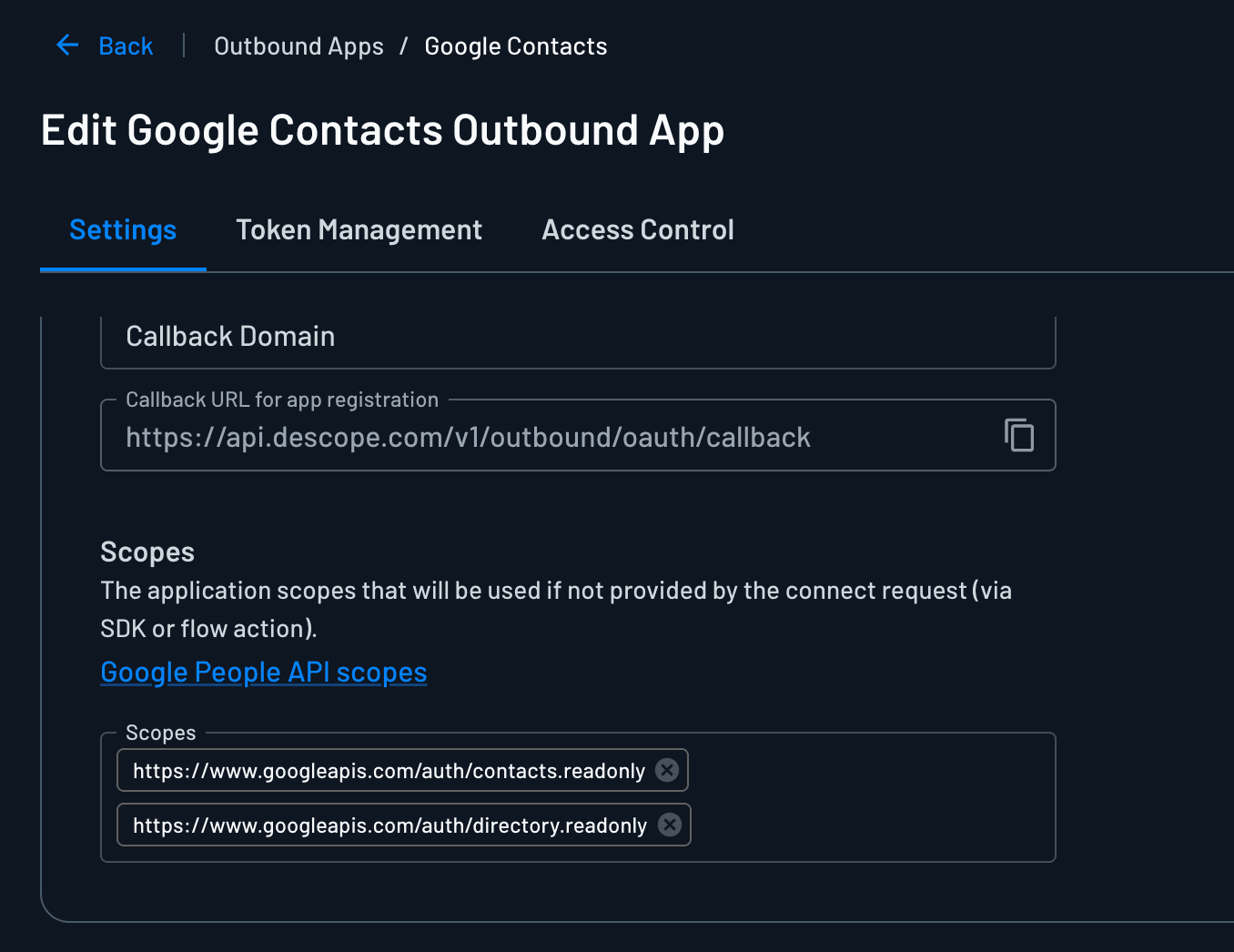
Keeping scopes granular ensures each task is limited to its responsibilities and prevents over-permissioning.
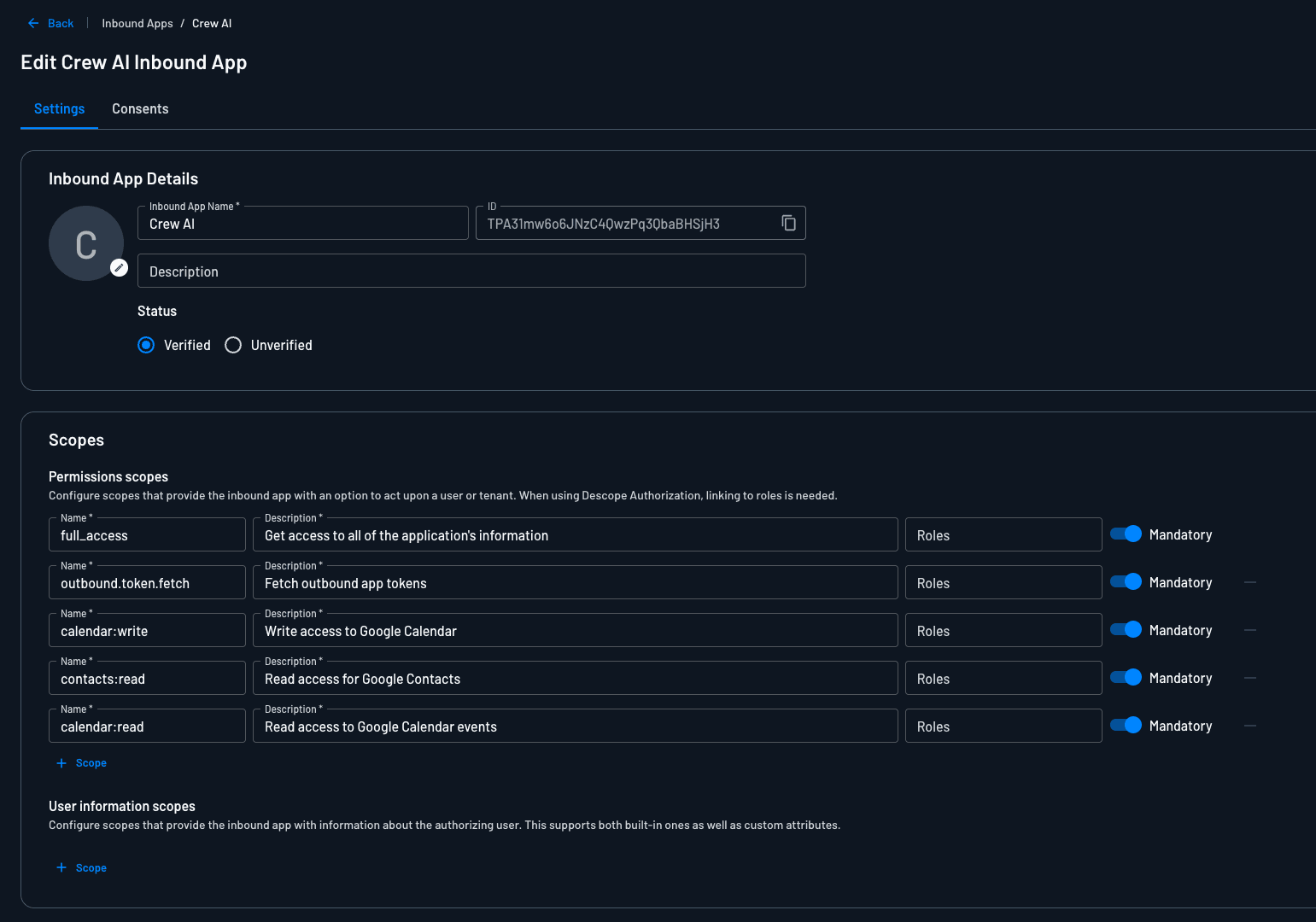
Configure Descope Inbound Application
Configure an Inbound App in your Descope console. The inbound app protects the front end and also has uses the consent flow so that user can grant consent. The token granted by inbound applications is used by the application backend to securely exchange fetch outbound app tokens:
Descope already has a template flow that can be used for inbound applications. Start with that customize as follows:
Insert a consent screen showing requested scopes for Calendar and Contacts.
Consent is stored for auditability and future requests.
Add two Outbound App Connection actions, one for each app. These are required to connect google calendar and contacts during the user login process.
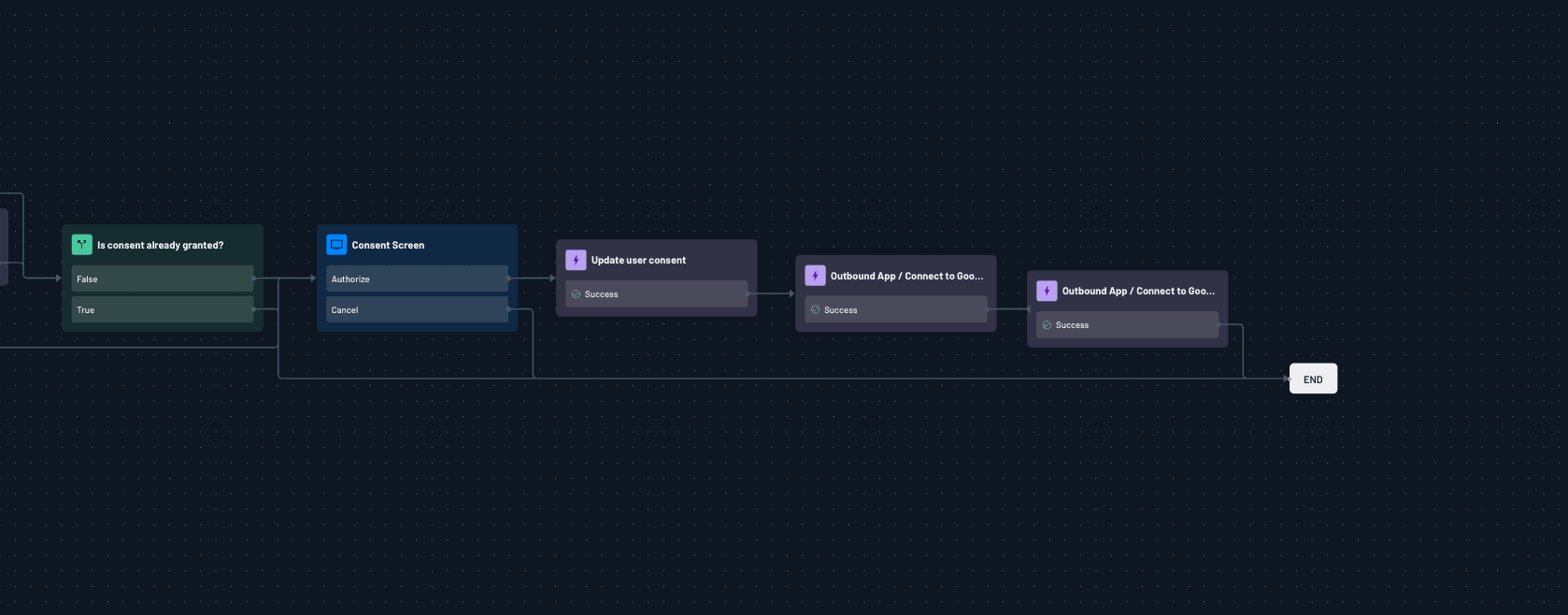
Frontend authentication
When a user signs in through the inbound app, they’re guided through the customized Descope Flow. This flow not only authenticates the user but also presents a consent screen showing the requested Google Calendar and Contacts scopes. Once the user approves, Descope connects the outbound apps behind the scenes, tying the user’s identity to the exact API permissions required.
The result is a session token returned to the frontend. This token represents a verified user identity and their granted scopes. Every request from the frontend to the backend should include this session token, ensuring that the backend can validate the user and securely exchange it for outbound access tokens later.
Configure CrewAI tasks
With authentication and token management in place, the CrewAI application can now operate as a coordinated multi-agent system. In this setup, we’ve defined a crew that manages two independent agents, each with a distinct role and scope.
The Calendar Task is handled by the calendar_manager agent, which uses the Google Calendar access token to read or create events. This agent specializes in interpreting user intent around time and scheduling, ensuring that calendar operations are executed precisely.
The Contacts Task is handled by the contacts_finder agent, which uses the Google Contacts access token to search and retrieve detailed contact information. This agent is optimized for matching names, emails, or partial queries, and always returns structured, well-formatted results.
Each task runs in isolation, bound by the specific OAuth scopes granted through Descope. This means the calendar agent cannot access contacts, and the contacts agent cannot alter calendar events. The crew oversees the process, coordinating the agents’ outputs and merging them into a unified result for the user.
Backend session validation
On the backend, validate the Descope session token using the Descope SDK.
Verify the token and extract the trusted
userIdand session information.Only validated sessions can request Outbound App access tokens.
def validate_session(session_token):
try:
jwt_response = descope_client.validate_session(session_token=session_token, audience=os.getenv("VITE_CLIENT_ID"))
print("Successfully validated user session:")
print(jwt_response)
return jwt_response
except Exception as error:
print("Could not validate user session. Error:")
print(error)
return NoneExchange session for access tokens
Once the session is validated, the backend exchanges it for scoped tokens for each Outbound App:
Calendar access token scoped to Calendar app permissions.
Contacts access token scoped to Contacts app permissions.
Descope handles OAuth flows and refresh logic, so the backend receives short-lived, scoped tokens without needing to store refresh tokens directly.
def get_outbound_token(app_id, user_id, session_token):
"""Fetch Google Calendar access token from Descope outbound token API."""
project_id = os.getenv("VITE_DESCOPE_PROJECT_ID")
management_key = os.getenv("DESCOPE_MANAGEMENT_KEY")
url = "https://api.descope.com/v1/mgmt/outbound/app/user/token/latest"
headers = { "Content-Type": "application/json", "Authorization": f"Bearer {project_id}:{session_token}", }
payload = { "appId": app_id, "userId": user_id, }
response = requests.post(url, headers=headers, json=payload)
if response.status_code != 200:
raise Exception(f"Failed to fetch token: {response.status_code} {response.text}")
data = response.json() token_data = data["token"]
access_token = token_data.get("accessToken")
return access_tokenOrchestrating agent security with Descope
With this setup, you have a secure, multi-agent CrewAI workflow. Each agent operates with least-privilege access, user consent is auditable, and the crew manager produces a unified output efficiently. To explore further or start experimenting right away, the sample app repo contains the complete codebase and configuration.
From here, you can start applying the same pattern to real use cases—for example, a sales workflow where one agent books meetings on Google Calendar while another enriches leads from your CRM, or a support workflow where an agent pulls customer details and another schedules follow-ups automatically.
You might also explore adding new agents tied to other APIs, integrating project management or finance systems, or experimenting with CrewAI’s orchestration features for more complex collaborations. In short, this foundation gives you a practical way to scale multi-agent systems securely, while Descope handles the identity and access challenges behind the scenes.