Table of Contents
What is RBAC?
Role-Based Access Control (RBAC) is the foundation of secure, scalable B2B SaaS applications. It defines who can access what, enforces least-privilege by default, and keeps permissions consistent as teams, tenants, and products grow. By assigning permissions to roles rather than individual users, RBAC helps organizations manage access cleanly across complex, multi-tenant environments.
From early-stage B2B products to enterprise SaaS platforms, RBAC is a core component of modern authorization architecture. The right RBAC model makes it easier to support delegated administration, tenant-specific roles, and audit-ready access controls without introducing brittle, hard-coded permission logic. For developers, RBAC is no longer just an internal security concern but a product capability that directly impacts onboarding, enterprise readiness, and long-term scalability.
In this guide, we explore the top RBAC providers for B2B SaaS applications. We break down how each solution approaches roles and permissions, highlight key strengths and tradeoffs, and explain which types of teams and products are best suited for each platform.
What is RBAC?
RBAC is an authorization model that determines what users can access based on the roles they are assigned. Instead of granting permissions directly to individual users, RBAC groups permissions into roles such as Admin, Manager, or Viewer, and assigns users to those roles within an application or organization. This approach reduces complexity and helps enforce least-privilege access across systems.
Modern RBAC extends beyond simple role checks. In B2B SaaS applications, RBAC must operate in multi-tenant environments where the same user may hold different roles across multiple organizations. Effective RBAC systems support tenant-scoped roles, delegated administration, and runtime permission evaluation, ensuring access decisions remain consistent as teams and products evolve.
Core components of RBAC typically include:
Roles: Named collections of permissions that reflect job functions or responsibilities.
Permissions: Discrete actions a user is allowed to perform, such as viewing data, managing users, or configuring integrations.
Assignments: Mappings that associate users or groups with roles within a specific tenant or organization.
Policy enforcement: Mechanisms to evaluate roles and permissions consistently across APIs, services, and user interfaces.
Administration tools: Interfaces or APIs that allow tenant admins to manage roles, permissions, and user access.
Unlike authorization for internal employee systems, RBAC for B2B SaaS must scale across many external organizations, partners, and customer teams. Each tenant may require custom roles, independent administrators, and strict isolation between organizations, all while maintaining a consistent product experience.
The right RBAC solution helps developers deliver secure, predictable access control that grows with their application. Below, we compare seven leading RBAC providers designed to support multi-tenant B2B SaaS platforms and enterprise-ready authorization needs.
What to consider when choosing an RBAC provider for B2B SaaS
Choosing the right RBAC provider depends on your application’s architecture, customer model, and long-term growth plans. While many platforms offer basic role and permission management, B2B SaaS environments demand greater flexibility, stronger tenant isolation, and tighter integration with enterprise identity workflows.
Key factors to evaluate include:
Multi-tenant role management: Support for tenant-scoped roles and permissions, allowing each organization to define access without impacting others.
Role and permission modeling: Flexible role hierarchies, default roles, and least-privilege permission design that scale as your product grows.
Policy enforcement: Consistent authorization checks across APIs, backend services, and user interfaces to avoid fragmented access logic.
Integration with SSO and provisioning: Native support for SAML or OIDC SSO and SCIM provisioning to align RBAC with enterprise onboarding workflows.
Administration experience: Self-service tools or APIs that enable tenant admins to manage users, roles, and permissions without developer intervention.
Developer experience: SDKs, APIs, and clear documentation that make it easy to implement and maintain RBAC without excessive custom logic.
Extensibility beyond RBAC: A path to support more advanced authorization models, such as attribute-based or relationship-based access, as application requirements evolve.
Scalability and compliance: Reliable performance, auditability, and compliance readiness for regulated industries and large customer organizations.
A strong RBAC solution balances security, flexibility, and usability, enabling teams to deliver predictable access control while supporting enterprise customers at scale.
With these considerations in mind, let’s explore the top RBAC providers for B2B SaaS applications.
Descope
Overview
Descope is a modern identity and authorization platform designed to simplify RBAC, fine-grained authorization (FGA), and enterprise SSO for B2B SaaS applications. It enables teams to define tenant-aware roles and permissions, assign access dynamically, and enforce least-privilege authorization consistently across APIs and applications without hard-coded logic.
Descope’s native RBAC and FGA capabilities are built for multi-tenant environments, allowing the same user to hold different roles across organizations while maintaining strict tenant isolation. Authorization decisions can be evaluated in real time, supporting scalable access control as customers, teams, and products grow.
Beyond authorization, Descope integrates RBAC with enterprise-ready authentication workflows, including SAML and OIDC SSO, SCIM provisioning, and delegated administration. Tenant admins can configure SSO, manage users, and assign roles through self-service flows, reducing onboarding friction and operational overhead.
With visual workflows and SDKs for modern frameworks, Descope unifies authentication, authorization, and identity orchestration into a single, developer-friendly platform.
Key capabilities
Tenant-aware RBAC: Define roles and permissions per organization, enabling least-privilege access and strict tenant isolation across B2B SaaS environments.
FGA: Enforce access using relationship- and resource-aware policies for scenarios that go beyond simple role checks.
Enterprise SSO support: Enable SAML and OIDC-based SSO for customer tenants, aligned with RBAC and authorization policies.
Comprehensive authentication methods: Support passkeys, OTP, magic links, social login, security questions, and biometrics to accommodate a wide range of users and use cases.
Adaptive and risk-based protection: Apply context-aware authentication using context-aware MFA, session management, and bot detection to increase security only when needed.
Step-up authentication: Require additional verification before sensitive in-app actions such as account changes or financial operations.
Visual workflow editor: Design authentication and authorization flows using drag-and-drop tools without writing backend code or managing infrastructure.
Journey-time orchestration: Connect authentication with fraud detection, authorization, compliance, and analytics tools to create unified, risk-aware identity journeys.
Prebuilt UI widgets: Embed enrollment, verification, and recovery experiences directly into your app for faster deployment and consistent UX across platforms.
SDKs and APIs for modern frameworks: Integrate quickly using SDKs for frameworks like Next.js, Flutter, and React Native.
Connector ecosystem: Seamlessly integrate with third-party risk, fraud, and directory services for extended authentication intelligence.
Agentic identity support: Secure and manage consented access for AI agents and MCP ecosystems alongside human users.
Strengths
B2B-first RBAC model: Native support for tenant-aware roles and permissions enables least-privilege access and consistent authorization across multi-tenant SaaS environments.
Fine-grained authorization readiness: Pair RBAC with fine-grained authorization (FGA) to model relationship-based permissions and complex access logic as applications evolve.
Enterprise-aligned access control: Tight integration between RBAC, SSO, and provisioning ensures roles and permissions stay aligned with enterprise identity systems.
Fast authorization implementation: Visual workflows and APIs reduce the need for custom authorization logic and speed up deployment without added infrastructure.
Consistent cross-application enforcement: Centralized authorization logic delivers predictable access control across services, APIs, and user interfaces.
Developer-first platform: SDKs, APIs, and prebuilt components simplify integrating and maintaining authorization across modern frameworks.
Scales with customer growth: Designed to support everything from early-stage products to large, multi-tenant SaaS ecosystems.
Transparent pricing and reliable support: Usage-based pricing and responsive developer support help teams adopt RBAC confidently as they scale.
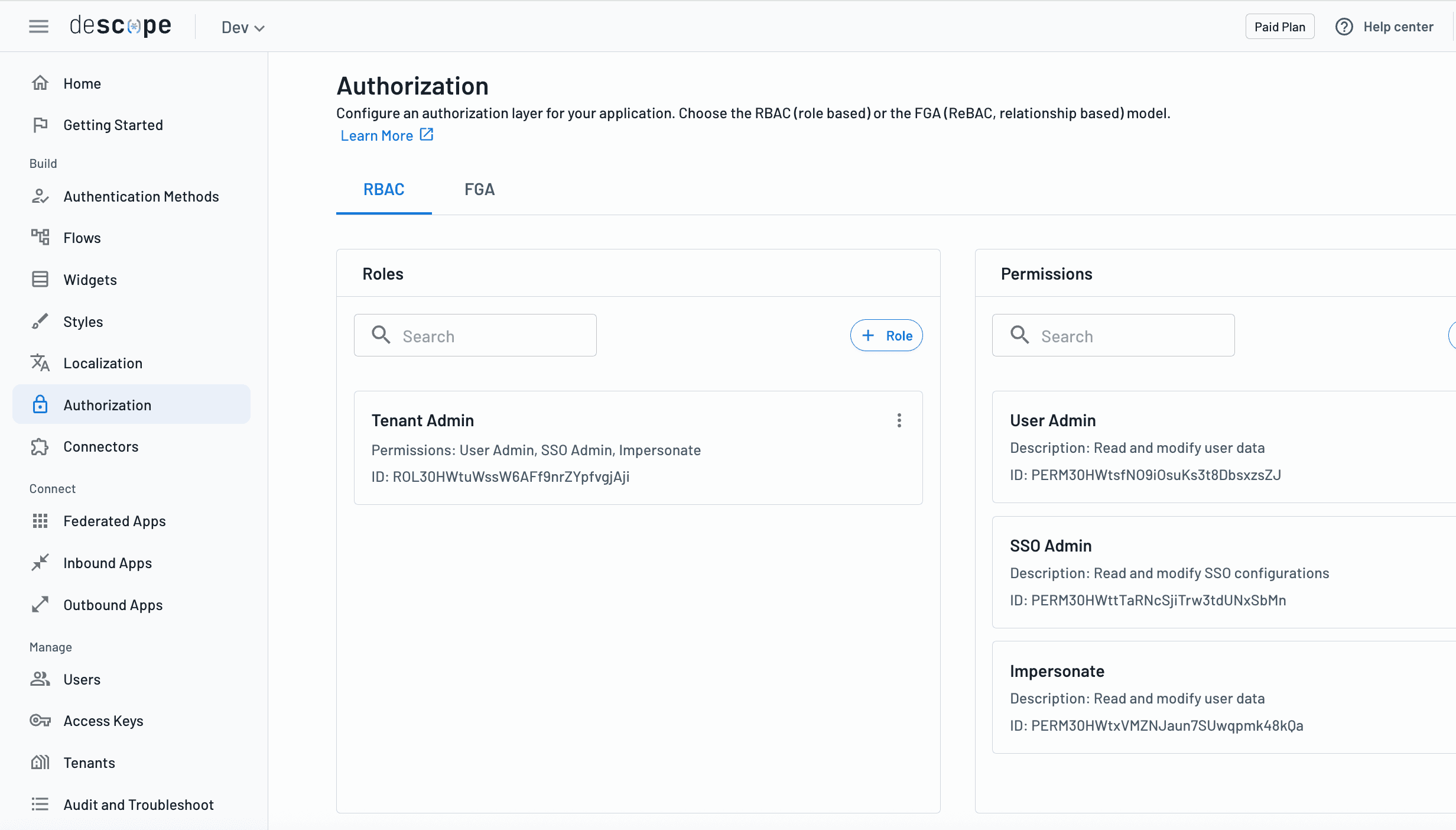
Ideal for
Descope is ideal for developers and product teams building B2B SaaS applications that require tenant-aware RBAC, FGA, and enterprise SSO without managing complex identity infrastructure. It works well for startups establishing scalable access control early and for enterprises modernizing authorization across multi-tenant platforms. With Descope, teams can deliver consistent, least-privilege access that scales as customers, organizations, and products grow.
Also Read: How You.com Runs Millions of FGA Queries Per Day With Descope
Auth0
Overview
Auth0, part of Okta, is a widely used identity platform that provides role-based access control as part of its broader authentication and API authorization capabilities. Auth0 supports defining roles and permissions that can be embedded into access tokens and enforced by applications and APIs. For B2B SaaS teams, this allows RBAC to be implemented alongside customer authentication, SSO, and federation.
Auth0’s RBAC model is primarily API-centric and works best when access decisions are enforced at the service layer using token claims. While suitable for many standard use cases, RBAC configuration can become complex in multi-tenant environments, often requiring custom logic to manage tenant context, role assignments, and delegated administration. As deployments scale, teams may also encounter higher configuration overhead and pricing tied to advanced authorization and enterprise features.
Key capabilities
Role and permission management for API authorization
Token-based RBAC enforcement using JWT claims
Integration with SAML, OIDC, and social identity providers
Support for multi-application and multi-API authorization models
Strengths
Enterprise-ready authorization: Proven support for RBAC in large-scale, production environments.
Developer ecosystem: Extensive SDKs, APIs, and documentation for integrating authorization into applications.
Mature platform: Broad adoption and a large partner and community ecosystem.
Ideal for
Organizations that want a well-established identity platform with built-in RBAC tied to API authorization. Auth0 is best suited for teams that are comfortable managing token-based access control and additional configuration complexity in exchange for enterprise scale and ecosystem maturity.
Also Read: Top Auth0 Alternatives For Modern App Builders
Microsoft Entra External ID
Overview
Microsoft Entra External ID provides identity and access management for external users, including customers and partners, within the Microsoft ecosystem. It supports role-based access through application roles that are assigned to users or groups and enforced by applications using token claims. For B2B SaaS teams serving Microsoft-first enterprises, Entra External ID offers a familiar, standards-based approach to authorization, though tenant-aware RBAC and delegated administration typically require additional application logic or Azure-specific tooling.
Key capabilities
Application roles for defining role-based access to customer-facing apps
Role and group assignments delivered as claims in access tokens
Support for SAML and OIDC-based enterprise authentication
Native integration with Microsoft Entra ID and Azure services
Strengths
Microsoft-aligned authorization: Fits naturally into Microsoft-centric enterprise environments.
Standards-based RBAC: Uses widely adopted role and token models for access control.
Enterprise-grade infrastructure: Backed by Microsoft’s global identity and security platform.
Ideal for
B2B SaaS applications targeting Microsoft-centric enterprises that want RBAC aligned with Entra and Azure identity models, and are comfortable implementing authorization logic within their own applications.
Supabase
Overview
Supabase provides role-based access control as part of its open-source backend platform, with authorization commonly enforced at the database layer using PostgreSQL and Row Level Security (RLS). For B2B SaaS teams, Supabase RBAC works best when access rules are closely tied to data models and enforced directly within the database. While powerful and flexible, implementing tenant-aware RBAC, delegated administration, and cross-service authorization often requires custom policies and application logic beyond Supabase’s built-in primitives.
Key capabilities
Role-based access control integrated with Supabase Auth
PostgreSQL Row Level Security for data-level authorization
Custom role and permission claims tied to database policies
APIs and SDKs for enforcing access in application code
Strengths
Database-native authorization: Enforces access control directly at the data layer.
Developer flexibility: Highly customizable using SQL policies and Postgres features.
Open-source foundation: Strong community and transparent architecture.
Ideal for
B2B SaaS teams building on PostgreSQL that want fine-grained, data-centric authorization and are comfortable managing RBAC through database policies and custom application logic.
Keycloak
Overview
Keycloak is an open-source identity and access management platform that supports role-based access control through realm and client roles. It can be extended with Authorization Services to support more advanced access policies.
For B2B SaaS applications, Keycloak provides flexibility and control, but implementing tenant-aware RBAC, delegated administration, and scalable operations typically requires significant configuration and ongoing maintenance. As a self-hosted solution, teams are responsible for availability, upgrades, and performance tuning.
Key capabilities
Realm and client roles for role-based access control
Authorization Services for policy- and resource-based access
Support for SAML, OIDC, and OAuth 2.0 standards
APIs and admin console for managing users, roles, and permissions
Strengths
Open-source control: Full ownership of identity and authorization infrastructure.
Flexible authorization models: Supports RBAC and policy-based access control.
Standards-compliant: Broad protocol support for enterprise integrations.
Ideal for
B2B SaaS teams that prefer an open-source, self-managed identity solution and have the operational capacity to run, scale, and customize authorization infrastructure in-house.
Also Read: Top Keycloak Alternatives
Ory Keto
Overview
Ory provides a modular identity and authorization stack, with Ory Keto serving as its authorization engine. Ory supports RBAC and more advanced, relationship-based authorization models inspired by Google Zanzibar. For B2B SaaS applications, Ory offers flexibility to model complex access patterns, but requires teams to design, manage, and enforce authorization logic themselves.
Tenant-aware RBAC, admin experiences, and operational tooling are typically built in-house, making Ory better suited for teams with strong infrastructure and authorization expertise.

Key capabilities
Ory Keto authorization service supporting RBAC and relationship-based access
API-driven policy evaluation for fine-grained authorization checks
Separation of authorization from authentication and application logic
Support for scalable, distributed authorization models
Strengths
Authorization-first design: Built specifically for access control and policy evaluation.
Flexible modeling: Supports RBAC and complex relationship-based permissions.
Scalable architecture: Designed for high-volume, distributed authorization use cases.
Ideal for
B2B SaaS teams with complex authorization requirements that go beyond basic RBAC and have the engineering resources to build and maintain custom authorization workflows and admin tooling.
Permit.io
Overview
Permit.io is an Externalized Authorization Platform (EAP) that delivers permissions as a service. It focuses on defining, managing, and enforcing authorization policies outside of application code, while relying on an existing authentication provider for identity context. Permit.io supports RBAC, ABAC, and more advanced authorization models, making it suitable for teams that want centralized, policy-driven access control across multiple services and environments.
For B2B SaaS applications, Permit.io enables flexible role and permission modeling and can act as a shared authorization layer across APIs and microservices. However, teams typically need to build their own tenant management, admin experiences, and identity workflows around it.
Key capabilities
UI-driven role and permission management via a visual dashboard
Policy-based RBAC with support for ABAC and advanced authorization models
Centralized policy store for authorization across multiple services
Runtime authorization checks via SDKs, APIs, and webhooks
Strengths
Externalized authorization control: Keeps access policies out of application code and centralized in one system.
Flexible modeling: Supports RBAC and more advanced authorization approaches as requirements evolve.
Visual management: Dashboard-driven role and permission management improves visibility and control.
Ideal for
B2B SaaS teams that already have authentication in place and need a centralized authorization control plane. Permit.io is best suited for organizations with complex or evolving access control requirements that extend beyond basic RBAC and are prepared to manage the additional operational and engineering complexity.
Conclusion
Modern RBAC is no longer just an internal security mechanism. It has become a core part of how B2B SaaS products scale securely, support enterprise customers, and deliver predictable user experiences. The right RBAC solution enables least-privilege access, simplifies tenant administration, and ensures authorization remains consistent as organizations, users, and products grow. Whether your goal is to support enterprise onboarding, meet compliance requirements, or reduce operational overhead, adopting a flexible and tenant-aware RBAC platform is essential.
Among today’s options, Descope stands out for its native support for tenant-aware RBAC, fine-grained authorization, and enterprise SSO, all delivered through a unified, developer-friendly platform. By combining authorization, SSO, and orchestration in a single system, Descope helps teams implement scalable access control without stitching together multiple tools or building custom infrastructure.
To learn more about implementing RBAC with Descope, check out our docs. If you'd like a demo, meet with our auth experts. Also, if you want to try Descope yourself, sign up for a Free Forever Account to start building secure, enterprise-ready authorization today!