Table of Contents
Why developers seek Keycloak alternatives
Keycloak is a widely used open-source identity and access management (IAM) solution developed by Red Hat. Many teams choose it for its flexibility, open standards support, and vendor-neutral deployment. But while Keycloak gives you full control, it comes with tradeoffs.
Teams often run into challenges when moving from testing to production, from complex setup to scaling limitations to ongoing maintenance. That’s why many developers and enterprises look for alternatives that provide the same flexibility without the operational burden.
This guide explores the top reasons teams seek Keycloak alternatives and compares five modern identity providers so you can choose the right fit for your stack.
Why developers seek Keycloak alternatives
Many teams look for Keycloak alternatives for a few key reasons:
Complex setup and deployment - Getting Keycloak production-ready is difficult, especially with SSL, proxies, and hostname configuration. Documentation often leaves gaps, forcing teams to dig through forums for answers.
Scaling and multitenancy limits - Performance degrades when running large numbers of realms or tenants. Clustering, caching, and startup tuning require extra operational overhead that slows teams down.
Upgrade and maintenance burden - Because Keycloak is self-hosted, teams must handle patches, upgrades, and backups themselves. Major version changes can break custom themes or extensions, making upgrades risky.
Support and documentation gaps - Most help is community-driven. Official documentation doesn’t always cover advanced or real-world scenarios, leaving DevOps teams to figure things out themselves.
Poor admin UX and customization hurdles - The admin console is often seen as unintuitive. Customizing themes or login pages usually means working with complex templates instead of simple, modern UI tooling.
Vendor lock-in and migration difficulty - Exporting user data, passwords, and realm configurations is cumbersome, and custom extensions don’t transfer easily.
Each alternative below addresses these gaps differently, depending on your technical requirements, scale, and roadmap.
Descope
Overview
Descope is a modern external IAM platform built for developers who want flexible, secure authentication without the complexity of managing Keycloak infrastructure. While Keycloak requires self-hosting, manual configuration, and ongoing maintenance, Descope provides a fully managed solution that lets teams design and deploy authentication flows visually, without servers or scripts.
It is especially powerful for B2C and B2B SaaS applications, as well as emerging use cases like agent identity and MCP-based ecosystems, where multi-tenancy, fine-grained access control, and delegated trust are critical.
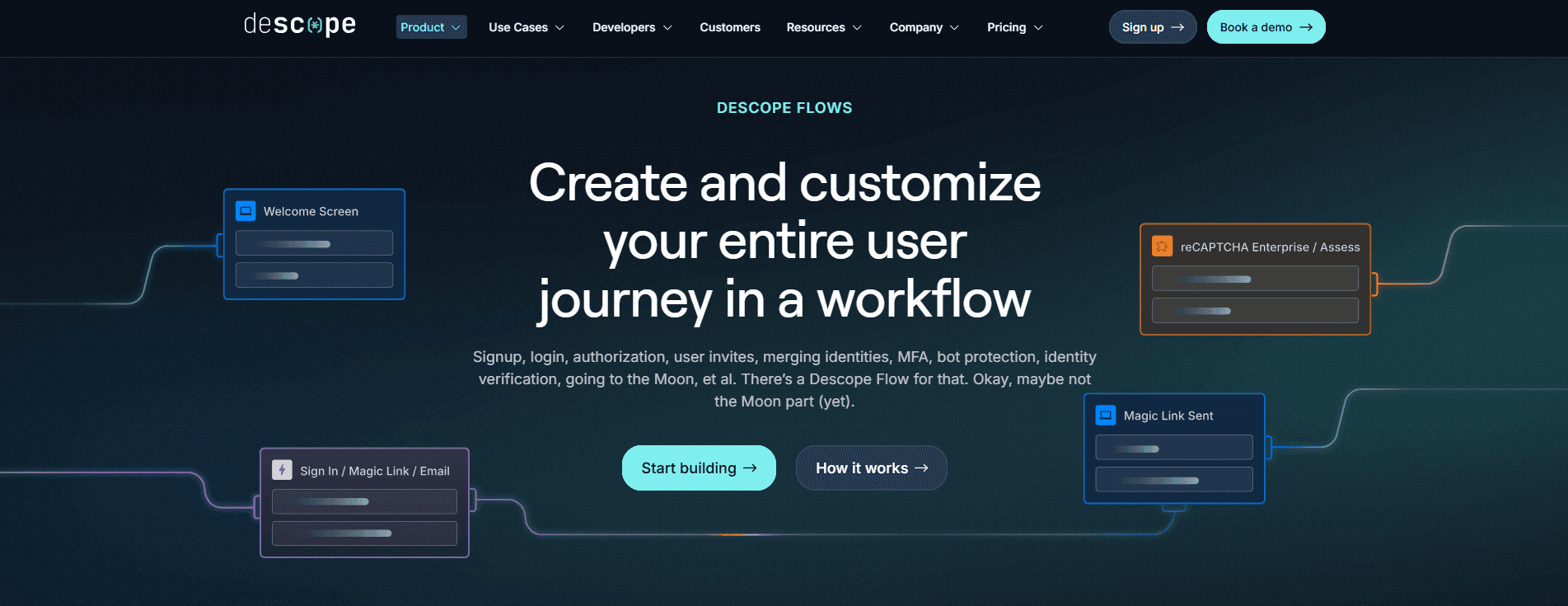
Unlike Keycloak, which demands significant DevOps effort to scale, customize, and integrate with third-party tools, Descope simplifies the process. It unifies authentication, MFA, SSO, and authorization in one platform, supporting both human users and AI agents natively so teams can build secure, user and agent-ready applications without piecing together multiple identity components.
Key capabilities
Drag & drop visual editor to build and update login, signup, and MFA flows without code
Extensive plug & play connector ecosystem for seamless integration with third-party services
Anonymous user tracking for top-of-funnel B2C user visibility
Comprehensive SSO Setup Suite for configuring, mapping, and testing SSO and SCIM connections
Embeddable UI widgets for self-service identity management and admin
Support for a wide range of auth methods including passkeys, OTP, magic links,social login, and Google One Tap
Broad SDK coverage with 15+ SDKs for web, mobile, and backend environments, plus a full-featured REST API
Identity orchestration that coordinates authentication, authorization, risk, and fraud tools
Built-in support for agentic identity to enable scoped, secure access for autonomous AI agents and apps.
Augment existing Keycloak deployments
If teams aren’t ready to fully migrate off Keycloak, Descope can seamlessly augment Keycloak by acting as a federated identity provider to add advanced capabilities such as passwordless authentication, adaptive MFA, and modern SSO experiences without replacing the existing identity stack.
Strengths
Visual workflow editor: Descope includes a drag-and-drop interface that lets developers design, test, and update login, signup, MFA, and SSO flows in minutes. This eliminates the need for backend scripting or XML configuration that Keycloak often requires.
Predictable pricing and responsive support: Descope’s pricing is simple and predictable, based on usage rather than tiers or add-ons. Unlike Keycloak, which depends on community forums for help, Descope offers direct, responsive support and extensive documentation as well as having earned the G2 Best Support badge for multiple consecutive quarters.
Streamlined SSO: With Descope, developers can configure enterprise SSO, SCIM provisioning, and tenant access through visual workflows or self-service portals. Keycloak often needs custom scripting or extensions to achieve similar results, while Descope handles it natively without downtime or user disruption.
Passwordless authentication: Descope supports passkeys, magic links, OTP, and social login natively. These methods can be easily added to any flow, reducing reliance on passwords while improving UX and security.
Omnichannel authentication: With Descope, authentication flows can be unified across web, mobile, and third-party or partner applications. The same no-code or low-code workflows can be reused across environments, making updates and scaling easier over time.
Adaptive MFA: Descope includes adaptive MFA by default, letting teams apply step-up authentication only when risk signals warrant it. Integration with both built-in and third-party risk tools happens directly within the flow, unlike Keycloak where advanced MFA logic often requires separate extensions or scripting.
Enterprise agent ready: Descope supports secure authentication and access control for agentic AI systems using Inbound Apps, Outbound Apps, and MCP Auth SDKs.
Developer-first flexibility: Whether using hosted components or fully custom UIs, Descope gives developers flexibility with SDKs and APIs in React, Node.js, Python, Flutter, and more. The platform fits into any tech stack without locking teams into rigid patterns.
Ideal for
SaaS developers and enterprises who want customizable, modern authentication without running and maintaining their own IAM stack.
Amazon Cognito
Overview
Amazon Cognito is AWS’s fully managed authentication and user management service. Unlike Keycloak, which requires self-hosting, configuration, and maintenance, Cognito handles infrastructure, scaling, and high availability automatically. It provides user pools for authentication, identity pools for temporary AWS credentials, and tight integration with the broader AWS ecosystem. This makes Cognito an appealing choice for developers who want to move away from Keycloak’s operational overhead and leverage AWS-native services for identity.
Key capabilities
Managed user pools for authentication and profile management
Federation with social logins and enterprise identity providers via SAML and OIDC
Built-in MFA and adaptive authentication features
Native integration with AWS services like API Gateway, Lambda, and IAM
SDKs for iOS, Android, JavaScript, and major backend languages
Strengths
Fully managed platform: Cognito removes the need to host or update your own identity stack, unlike Keycloak’s manual deployments and upgrades.
Seamless AWS integration: Easily connect authentication to APIs, databases, and serverless functions using native AWS tools.
Effortless scalability: Cognito automatically scales to millions of users without requiring realm tuning or clustering setups.
Security and compliance: Cognito inherits AWS’s security framework and compliance certifications, reducing the risk of misconfiguration or patching errors that can occur in self-managed Keycloak environments.
Ideal for
Teams already building on AWS who want to simplify identity management, reduce operational overhead, and ensure their authentication stack scales securely with their infrastructure.
Microsoft Entra External ID
Overview
Microsoft Entra External ID is a cloud-based identity and access management service designed for organizations that need to securely manage and authenticate external users. Unlike Keycloak, which requires manual configuration, upgrades, and self-hosted infrastructure, Entra External ID delivers identity as a managed service with deep integrations across the Microsoft ecosystem. It combines secure authentication, user lifecycle management, and governance in a single platform.
Key capabilities
Supports sign-up and sign-in for external users with social or enterprise identities
Customizable branded user journeys for portals and apps
Built-in MFA, conditional access, and risk-based authentication
Lifecycle management tools for access reviews, provisioning, and expiration policies
Seamless integration with Azure AD, Microsoft 365, and other Microsoft cloud services
Strengths
Fully managed enterprise identity: Eliminates the need for self-hosting and manual scaling common with Keycloak deployments.
Compliance and governance ready: Offers built-in support for identity governance, auditing, and access certifications to meet enterprise and regulatory requirements.
Microsoft ecosystem integration: Works natively with Azure and Microsoft 365, simplifying identity management across productivity and infrastructure tools.
Customizable user experiences: Provides visual configuration of user journeys and branding options that would otherwise require custom Keycloak templates or extensions.
Ideal for
Organizations operating within the Microsoft ecosystem or seeking a managed alternative to Keycloak that provides advanced governance, compliance, and lifecycle management out of the box.
FusionAuth
Overview
FusionAuth is a developer-focused identity and access management platform that can be self-hosted or deployed as a managed cloud service. Like Keycloak, it supports open standards such as OAuth2, OIDC, and SAML, but it’s designed to be easier to install, customize, and operate. FusionAuth offers a strong alternative for teams that want control over their identity environment without the operational complexity of maintaining Keycloak.
Key capabilities
Flexible deployment options, including on-premises, private cloud, or FusionAuth Cloud
Support for OAuth2, OpenID Connect, SAML, and SCIM
Multi-tenant and multi-application management from a single dashboard
Built-in MFA, passwordless login, and passkey support
Modern RESTful APIs and SDKs for multiple programming languages
Strengths
Ease of setup and maintenance: Installs quickly with fewer dependencies than Keycloak and requires less tuning to reach production readiness.
Developer-friendly design: Clear documentation, strong APIs, and an intuitive admin UI simplify customization compared to Keycloak’s XML-based configuration and templating.
Flexible hosting model: Teams can self-host for full control or use the managed FusionAuth Cloud to offload maintenance.
Comprehensive feature set: Delivers enterprise protocols, fine-grained roles, and advanced MFA out of the box without relying on community extensions.
Ideal for
Development teams that value open standards and deployment flexibility but want a smoother, more maintainable experience than running Keycloak.
Authentik
Overview
Authentik is an open-source identity provider designed to offer a simpler, more modern alternative to Keycloak. It focuses on ease of deployment, clean configuration, and native integration with modern infrastructure tools. While Keycloak can feel heavy and complex to maintain, Authentik provides a lighter, modular architecture that’s easier to run in containerized or cloud-native environments. It delivers the flexibility of open source without the steep learning curve often associated with Keycloak’s realm and configuration model.
Key capabilities
Support for standard protocols such as OAuth2, OIDC, and SAML
Native directory synchronization with LDAP and SCIM
Application proxy for protecting web applications and internal dashboards
Built-in MFA and policy-based access control
Admin interface and APIs for managing users, groups, and applications
Strengths
Lightweight and easy to deploy: Installs quickly and requires less setup overhead compared to Keycloak’s multi-realm architecture.
Modern admin experience: Offers a clean, straightforward UI that simplifies configuration and reduces errors.
Flexible integrations: Works well with Docker, Kubernetes, and reverse proxies, making it a good fit for modern DevOps environments.
Active community and development: Regular updates and community engagement ensure faster iteration and usability improvements than many older IAM projects.
Ideal for
Teams seeking an open-source identity provider that retains Keycloak’s flexibility but is easier to deploy, manage, and customize for modern infrastructure.
Ory Kratos
Overview
Ory Kratos is an open-source identity and user management system built for modern, cloud-native applications. Like Keycloak, it gives developers full control over authentication and user lifecycle management, but with a more API-driven and headless architecture. Instead of relying on a heavy admin console or complex realm structure, Ory Kratos exposes identity and session management through REST APIs. It’s part of the broader Ory ecosystem, which includes Ory Hydra (OAuth2/OIDC), Ory Keto (authorization), and Ory Oathkeeper (access control).
Key capabilities
Headless API-first architecture for authentication and user management
Support for password, magic link, social, and passwordless login flows
Self-service registration, recovery, and profile management endpoints
Integration with Ory Hydra for OAuth2 and OIDC token issuance
Works natively with Kubernetes, Docker, and other modern DevOps tools
Strengths
API-first and composable: Designed for developers who prefer to build their own UIs and integrate identity directly into microservices.
Lightweight and modern: Built for containerized deployments with a smaller footprint and faster startup than Keycloak.
Modular design: Can be paired with other Ory components to extend capabilities, offering flexibility that aligns with cloud-native architectures.
Open-source and transparent: Maintained under a permissive license with strong community and enterprise support via Ory Cloud.
Ideal for
Engineering teams that want a flexible, open-source identity solution built for modern infrastructure and prefer an API-driven approach over Keycloak’s UI-based configuration and heavier deployment model.
Conclusion
Keycloak remains a powerful open-source identity platform, but its complexity, maintenance overhead, and scaling limitations often become major challenges as projects mature. Teams that start with Keycloak for its flexibility and control frequently find themselves burdened by operational upkeep, difficult upgrades, and limited enterprise features. As a result, many developers look for alternatives that deliver the same standards-based foundation without the heavy infrastructure demands.
Among the available options, Descope stands out for its developer-friendly visual workflows, built-in multi-tenancy, and seamless support for modern authentication methods such as passkeys, SSO, and adaptive MFA. By removing the friction of self-hosting and manual configuration, Descope helps teams launch faster, scale securely, and spend more time building products instead of maintaining identity systems.
For more detailed information on Descope, check out our docs. If you'd like a demo, meet with our auth experts. Also, if you want to try Descope yourself, sign up for a Free Forever Account and start dragging & dropping your auth today!






