Table of Contents
Why developers seek Ory Kratos alternatives
Ory Kratos is an open source identity and user management system that many developers explore when building authentication into their applications. While it offers flexibility and self-hosting, teams often run into challenges once projects scale or enterprise requirements surface.
From upgrade headaches to missing features, these hurdles have many developers searching for Ory Kratos alternatives that can better balance customization, security, and developer experience.
Below, we break down the top reasons developers look beyond Kratos, followed by a closer look at the best alternatives available today.
Why developers seek Ory Kratos alternatives
Many teams outgrow Ory Kratos for a few key reasons:
Upgrade headaches: Frequent breaking changes make upgrades risky and time-consuming. Teams often stay on older versions to avoid breaking existing customizations, leading to security and compatibility issues over time.
High maintenance burden: Running Ory Kratos can feel like maintaining a second product. Manual SSO setup, claim mapping, and schema tweaks require ongoing engineering effort and pull focus away from core product development.
Weak enterprise and multi-tenancy support: Ory Kratos lacks native tenant isolation, fine-grained authorization, and advanced MFA. Features like identity linking and self-service SSO portals require heavy custom code.
Limited SSO and integrations: Out-of-the-box SSO support is minimal. Tenants can’t easily bring their own IdPs or manage multiple connections, creating friction in B2B and enterprise use cases.
Scaling complexity: Configuring Ory Kratos across hybrid environments, multi-instance deployments, and large-scale operations adds operational overhead that slows teams down.
Hidden costs and limited support: While free to download, the real costs appear in developer hours, infrastructure management, and production slowdowns. Community support is helpful but rarely enough for enterprise-grade needs.
Each alternative below addresses these gaps differently, depending on your technical requirements, scale, and roadmap.
Descope
Overview
Descope is a modern external IAM platform purpose-built for developers who want flexible, secure authentication without the overhead of maintaining complex infrastructure. Unlike Ory Kratos, which often requires heavy coding and operational upkeep, Descope focuses on simplicity and speed. It’s particularly strong for B2C and B2B SaaS applications, as well as new frontiers like AI agents and MCP-based ecosystems, where delegated trust is critical.
While Ory Kratos itself does not directly handle authentication or authorization for AI agents (that role is covered by a separate Ory product) Descope, by contrast, supports both human users and AI agents natively. This makes it much easier to build agent-ready applications without stitching together multiple tools.
Also read: Why BalkanID moved from Ory Kratos to Descope
Key capabilities
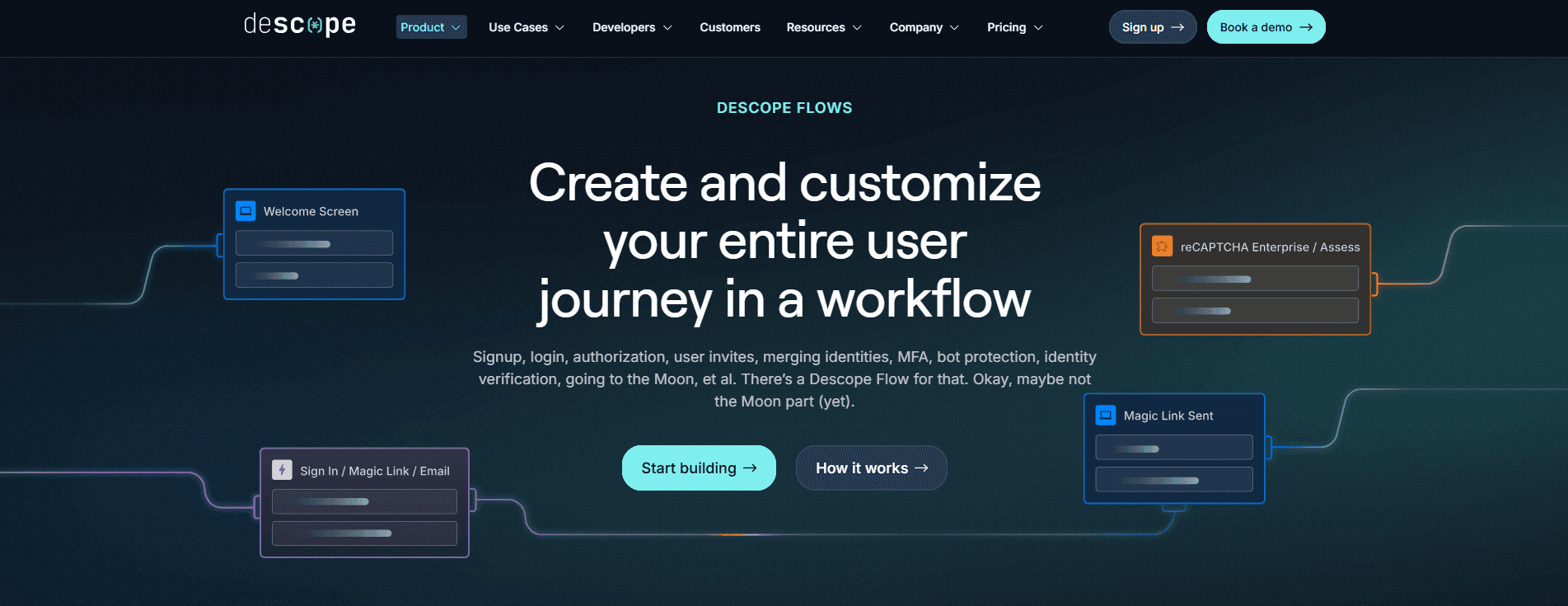
Visual workflow editor to design and update login, signup, MFA, and SSO flows with no backend rewrites.
Plug-and-play connector library for quick integration with third-party services and risk tools.
Anonymous user tracking for better visibility into pre-signup B2C funnels.
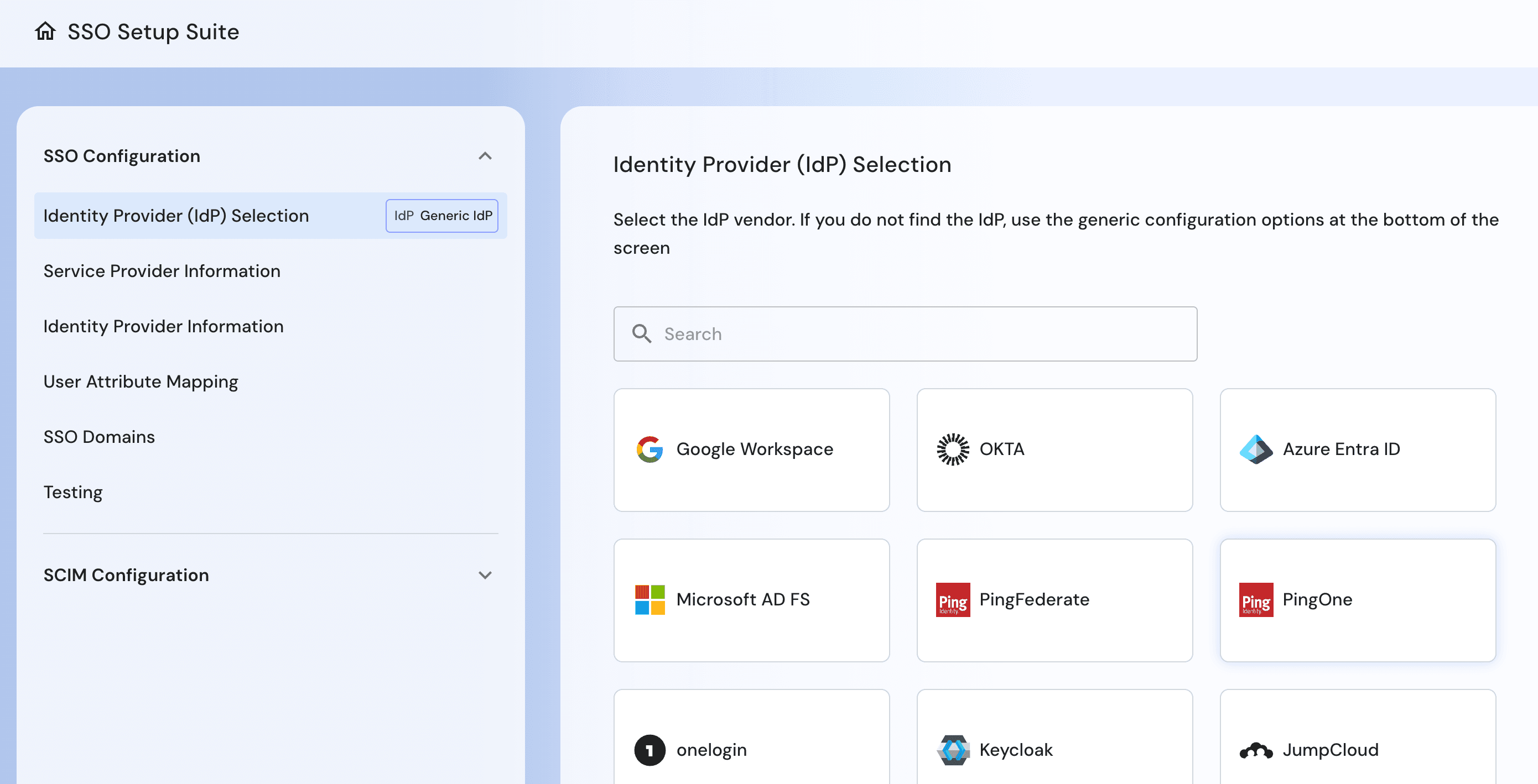
Comprehensive SSO Setup Suite for streamlined IdP configuration, claim mapping, and testing.
Embeddable UI widgets for self-service profile and admin management.
Broad authentication support including passkeys, OTP, magic links,social login, and Google One Tap.
15+ SDKs and APIs spanning web, mobile and a robust REST API.
Identity orchestration that coordinates authentication, authorization, risk, and fraud tools.
Agentic identity to make both applications and AI agents enterprise-ready.
Strengths
Visual workflows: Descope’s drag & drop editor lets developers design login, signup, MFA, and SSO flows without backend scripting or custom glue code. This simplifies auth implementation and speeds up time to production.
Predictable pricing and responsive support: Descope offers transparent, usage-based pricing with no hidden fees or surprise jumps. Teams benefit from fast, knowledgeable support to help them implement, troubleshoot, and scale with confidence, as evidenced by Descope winning the Best Support G2 badge the last four quarters in a row.
Streamlined SSO: Build and manage SSO journeys with workflows, enable self-service setup, and migrate existing configurations with no disruption.
Passwordless authentication: Descope supports passkeys, magic links, OTP, and social login natively. These methods can be easily added to any flow, reducing reliance on passwords while improving UX and security.
Omnichannel authentication: With Descope, authentication flows can be unified across web, mobile, and third-party or partner applications. The same no-code or low-code workflows can be reused across environments, making updates and scaling easier over time.
Adaptive MFA: Descope allows developers to choose from a wide range of MFA methods and integrate seamlessly into their flows. MFA can be enforced only when needed using native and third-party risk signals, without overhauling existing auth systems.
AI agent ready: Descope supports secure authentication and access control for agentic AI systems using Inbound Apps, Outbound Apps, and MCP Auth SDKs.
Built for developers: Whether using hosted components or fully custom UIs, Descope gives developers flexibility with SDKs and APIs in React, Node.js, Python, Flutter, and more. The platform fits into any tech stack without locking teams into rigid patterns.
Ideal for
Developers building multi-tenant, cross-platform, or agent-ready apps who want to launch and update authentication flows quickly without taking on the ongoing maintenance burden that comes with Ory Kratos.
Supabase
Overview
Supabase is an open-source platform that combines authentication, a Postgres database, storage, and edge functions into a single backend stack. Its authentication service, powered by GoTrue, supports multiple login methods with minimal configuration. Compared to Ory Kratos, Supabase offers a more integrated developer experience by bundling database and serverless functionality alongside auth. This makes it attractive to teams that want to avoid managing separate infrastructure components.
Key capabilities
Email/password, magic link, and third-party OAuth providers.
Postgres-based authentication with row-level security (RLS).
Serverless functions (Edge Functions) for backend logic.
SDKs for JavaScript, Flutter, and other platforms.
Flexible deployment options: self-hosted or fully managed.
Strengths
Simpler operations: Unlike Ory Kratos, Supabase runs as a unified service with managed hosting options.
Database integration: Authentication ties directly into Postgres RLS, enabling fine-grained access control without extra coding or orchestration.
Developer productivity: Supabase provides a straightforward console, SDKs, and APIs that help developers move faster, whereas Ory Kratos often requires custom glue code and manual upgrades.
Ideal for
Developers and startups who want to implement authentication with less overhead than Ory Kratos, while benefiting from a fully integrated backend stack that can still be self-hosted if needed.
Keycloak
Overview
Keycloak is a widely adopted open-source IAM solution maintained by Red Hat. It provides a comprehensive set of enterprise-ready features such as SSO, identity brokering, and user federation. Compared to Ory Kratos, Keycloak comes with more functionality out of the box, though at the cost of being heavier to operate and scale.
Key capabilities
Single sign-on (SSO) using OpenID Connect, SAML, and OAuth2.
Identity brokering to connect external IdPs.
User federation with LDAP and Active Directory.
Built-in admin console and user self-service portal.
Fine-grained authorization with policy-based access control.
Strengths
Feature-rich: Keycloak includes federation, brokering, and authorization natively.
Enterprise adoption: Backed by Red Hat and widely deployed in enterprises, Keycloak benefits from a mature ecosystem and strong community support.
Extensible: Plugins and SPI make it possible to customize Keycloak deeply, whereas Ory Kratos typically demands more ground-up coding.
Ideal for
Organizations that want a mature, open-source IAM platform with enterprise-grade features included by default. Keycloak is well-suited for teams that find Ory Kratos too limited or maintenance-heavy.
Amazon Cognito
Overview
Amazon Cognito is AWS’s fully managed authentication and user management service. It provides user pools for authentication, identity pools for temporary AWS credentials, and integrations with the broader AWS ecosystem. Cognito handles infrastructure, scaling, and availability out of the box. This makes it a natural fit for developers already building on AWS who want to offload the operational burden of identity.
Key capabilities
Managed user pools for authentication and user management.
Federation with social logins and enterprise IdPs.
MFA and adaptive authentication options.
Tight integration with AWS services like API Gateway, Lambda, and IAM.
SDKs for iOS, Android, JavaScript, and server-side platforms.
Strengths
Fully managed service: Cognito eliminates the need to self-host and scale identity infrastructure.
AWS integration: Direct ties to AWS services make it easy to connect auth to APIs, storage, and serverless functions.
Scalability: Cognito automatically handles millions of users without requiring custom scaling logic.
Security defaults: Built-in compliance with AWS security practices, reducing the risk of misconfiguration compared to self-managed Ory Kratos deployments.
Ideal for
Teams building inside the AWS ecosystem that want a fully managed identity service instead of maintaining Ory Kratos. Cognito is especially appealing for applications that need to integrate authentication directly with AWS backend resources.
Microsoft Entra External ID
Overview
Microsoft Entra External ID is Microsoft’s cloud-based identity platform for customers, partners, and external users. It delivers enterprise-scale authentication and authorization with built-in compliance and governance features. Entra External ID is fully managed and integrates tightly with Microsoft’s broader security ecosystem, making it especially attractive for organizations in regulated industries.
Key capabilities
Supports self-service registration and sign-in with social or enterprise identities.
Enables branded, customizable user journeys for external apps and portals.
Includes built-in security, conditional access, and MFA options.
Manages user lifecycle with governance, access reviews, and expiration policies.
Strengths
Enterprise compliance: Entra offers certifications, logging, and conditional access policies out of the box.
Scale and reliability: Microsoft’s global infrastructure supports millions of users without the scaling complexity of Kratos.
Governance and security: Deep policy controls, identity protection, and audit features reduce the risk of misconfigurations.
Ecosystem integration: Works seamlessly with Microsoft 365 offering a broad enterprise identity strategy.
Ideal for
Enterprises and organizations that prioritize governance, compliance, and scale. Entra External ID is a strong Ory Kratos alternative for teams that don’t want the operational burden of self-hosting and need advanced policy controls baked in.
Authentik
Overview
Authentik is a modern, open-source identity provider designed with a container-first architecture. It emphasizes flexibility and ease of deployment with Docker and Kubernetes, making it lighter to manage than Ory Kratos for many teams. While not as feature-heavy as Keycloak or Entra ID, Authentik offers a straightforward way to implement authentication, SSO, and policy-based access without the upgrade headaches or manual wiring often required with Ory Kratos.
Key capabilities
SSO with support for OpenID Connect (OIDC) and SAML.
Policy-based access controls for fine-grained authorization.
Built-in support for LDAP and proxy authentication.
Admin UI and APIs for managing users, applications, and flows.
Container-native deployment for Kubernetes and Docker environments.
Strengths
Ease of deployment: Unlike Ory Kratos, which can require heavy manual setup, Authentik ships with simple Docker and Kubernetes support.
Lightweight operations: Offers a modern, container-first design that reduces maintenance overhead compared to Kratos.
Active community: Growing open-source adoption with frequent releases and active contributors.
Flexibility: Balances simplicity and extensibility for teams that want more than Ory Kratos but less complexity than Keycloak.
Ideal for
Smaller teams or Kubernetes-native developers who want an easier-to-manage, open-source alternative to Ory Kratos without giving up flexibility or control.
FusionAuth
Overview
FusionAuth is a full-featured CIAM platform that can be self-hosted or run as a managed cloud service. It’s designed to support any app, framework, or deployment model, and includes advanced capabilities like tenant-aware authentication and WebAuthn-based MFA. Compared to Ory Kratos, which requires custom code for many enterprise features, FusionAuth delivers them out of the box with strong extensibility through hooks and APIs.
Key capabilities
SSO support for OIDC, OAuth2, and SAML.
Advanced MFA options including WebAuthn, TOTP, and SMS.
Multi-tenant management with RBAC and FGA.
Event-driven architecture with webhooks for customization.
SDKs and APIs for a wide range of programming languages.
Strengths
Enterprise features included: Provides MFA, fine-grained authorization, and multi-tenancy natively, avoiding the custom builds Ory Kratos demands.
Flexible deployment: Can be run in the cloud or self-hosted to fit infrastructure needs.
Extensible: Hooks and APIs let developers tailor workflows without modifying the core platform.
Community and support options: Commercial support reduces the reliance on community-only help that can slow Ory Kratos adoption in production.
Ideal for
Organizations that want enterprise-grade features in a self-hosted or managed package. FusionAuth is a strong Ory Kratos alternative for teams that need power and extensibility without rebuilding core identity functionality from scratch.
Conclusion
Ory Kratos offers flexibility as an open source identity system, but many teams quickly encounter its limitations such as upgrade pain, limited enterprise features, scaling challenges, and hidden operational costs. That is why developers often look for alternatives that reduce overhead while delivering the capabilities modern applications demand.
Among the available options, Descope stands out for its developer-friendly workflows, built-in multi-tenancy, and modern features that go beyond traditional user authentication. By simplifying implementation and ongoing management, Descope helps teams focus on building products rather than maintaining infrastructure.
For more detailed information on Descope, check out our docs. If you'd like a demo, meet with our auth experts. Also, if you want to try Descope yourself, sign up for a Free Forever Account and start dragging & dropping your auth today!






