Table of Contents
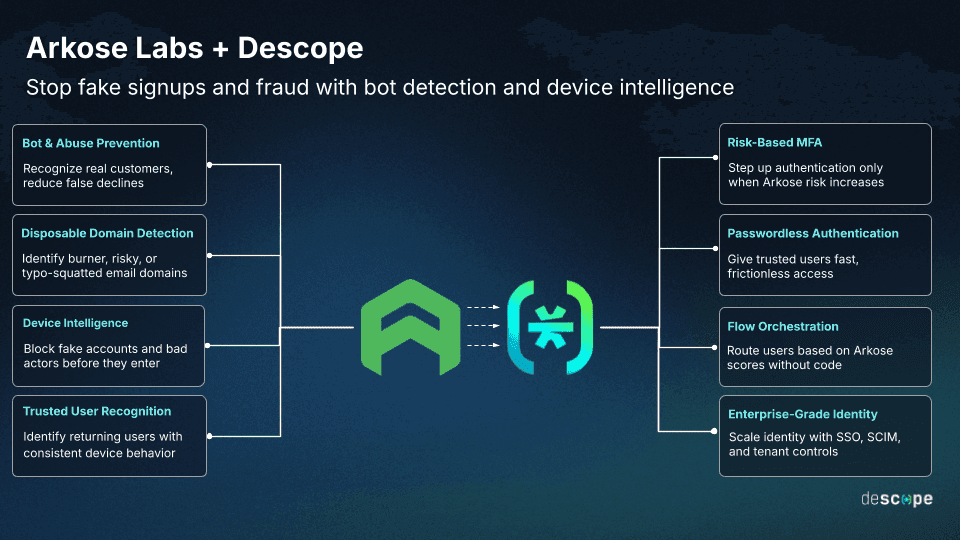
About Arkose Bot Manager
Credential stuffing, account takeover (ATO), and automated authentication attacks represent persistent threats to application security. Attackers leverage bot networks to test stolen credentials at scale, perform distributed brute-force attacks, and execute low-and-slow enumeration campaigns that often evade traditional rate limiting and WAF rules. Without behavioral intelligence at the authentication layer, platforms risk unauthorized access, data exfiltration, and cascading fraud across downstream services.
The Descope Arkose Bot Manager Connector enables developers to integrate real-time bot detection and behavioral risk scoring directly into authentication flows, blocking automated attacks before session creation. By evaluating device reputation, network behavior, and interaction patterns, Arkose Bot Manager identifies and mitigates bot-driven authentication attempts while maintaining a frictionless experience for legitimate users.
About Arkose Bot Manager
Arkose Bot Manager is an enterprise bot mitigation platform deployed by leading financial services, gaming, e-commerce, and SaaS companies to protect high-value authentication endpoints. The platform combines client-side telemetry collection, server-side behavioral analysis, and adaptive enforcement mechanisms to distinguish human users from automated scripts, emulators, and headless browsers.
Arkose Bot Manager provides deep visibility into device fingerprints, network anomalies, behavioral deviations, and known attack patterns, enabling security teams to implement risk-based authentication policies that adapt to real-time threat intelligence.
Connector overview
Arkose Bot Manager performs real-time analysis of authentication attempts to identify automated threats and malicious behavior patterns. The Descope Arkose Bot Manager Connector integrates Arkose's bot detection capabilities directly through Descope's user journey workflows through two powerful signal layers:
Bot Detection Signals
Real-time behavioral analysis that identifies:
Automated scripts and headless browsers attempting credential testing
Human-assisted bot networks (CAPTCHA farms, click farms)
Browser automation tools (Selenium, Puppeteer, Playwright)
Emulators and virtual machines masquerading as legitimate devices
Behavioral anomalies inconsistent with human interaction patterns
Session replay attacks and credential stuffing infrastructure
Arkose Bot Manager detection signals aggregate telemetry from client-side instrumentation, server-side analytics, and Arkose Lab's global threat network to produce risk scores that distinguish genuine users from automated attacks, even when attackers use valid credentials or sophisticated evasion techniques.
Arkose Device ID
Device fingerprints that provide:
Persistent device identification across sessions and IP changes
Device reputation scores based on historical fraud activity
Spoofing indicators detecting virtual environments and automation frameworks
Known malicious device identifiers from Arkose's threat intelligence network
Network metadata including proxy detection, VPN usage, and IP reputation
Cross-account device reuse patterns indicating multi-accounting or fraud rings
Arkose Device ID enables tracking of attack infrastructure over time, revealing distributed credential stuffing campaigns, low-and-slow attacks, and persistent threat actors even when they rotate IPs, user agents, or credential sets.
The Descope Arkose Bot Manager Connector integrates directly into Descope's workflows and can be orchestrated with other authentication security controls including step-up MFA, IP reputation checks, phone intelligence, and custom business logic.
Use case: Mitigate credential stuffing
Credential stuffing attacks leverage valid username and password pairs obtained from data breaches, testing them across multiple platforms to identify reused credentials. According to the Verizon 2025 Data Breach Investigations Report (DBIR) found that, in some cases, credential stuffing accounted for up to 44% of all login attempts in a single day for certain organizations. These attacks often succeed because the credentials themselves are legitimate, and traditional authentication systems cannot reliably distinguish between an authorized user and an attacker using stolen credentials.
Arkose Bot Manager evaluates the behavioral and network context of authentication attempts to identify automated credential testing.
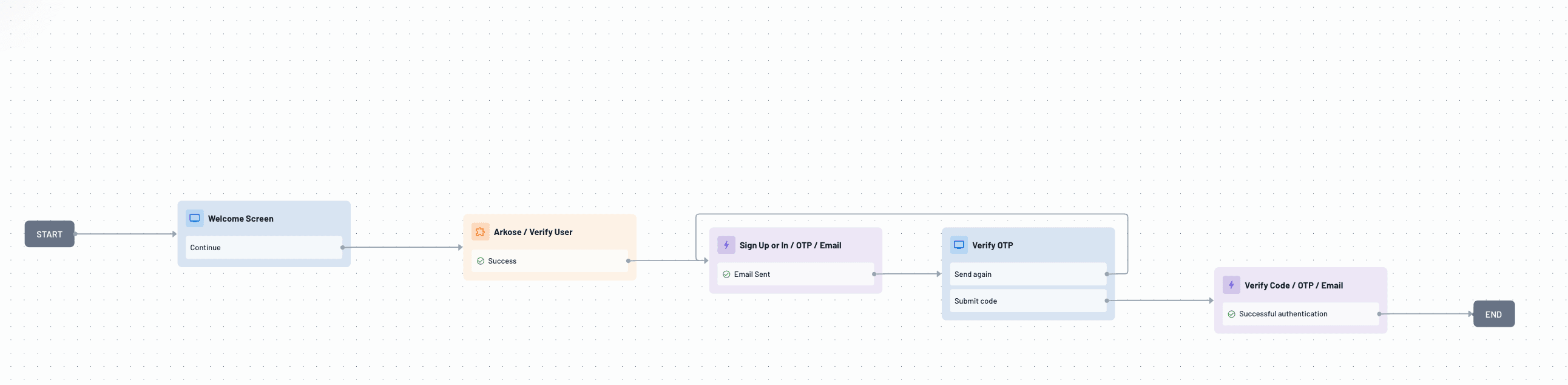
Below is an example of a Descope Flow using Arokse Bot Manager to pull threat intel during a login attempt:
The user submits credentials for authentication.
Descope evaluates credentials and invokes Arkose Bot Manager in parallel.
Arkose analyzes behavioral telemetry, device fingerprint, and network context.
Arkose returns a unified risk score with recommended action.
Descope enforces risk-based logic: allow, challenge with MFA or Arkose enforcement, or block and log.
This approach stops credential stuffing bots while avoiding false positives for legitimate users accessing accounts from new devices or locations.
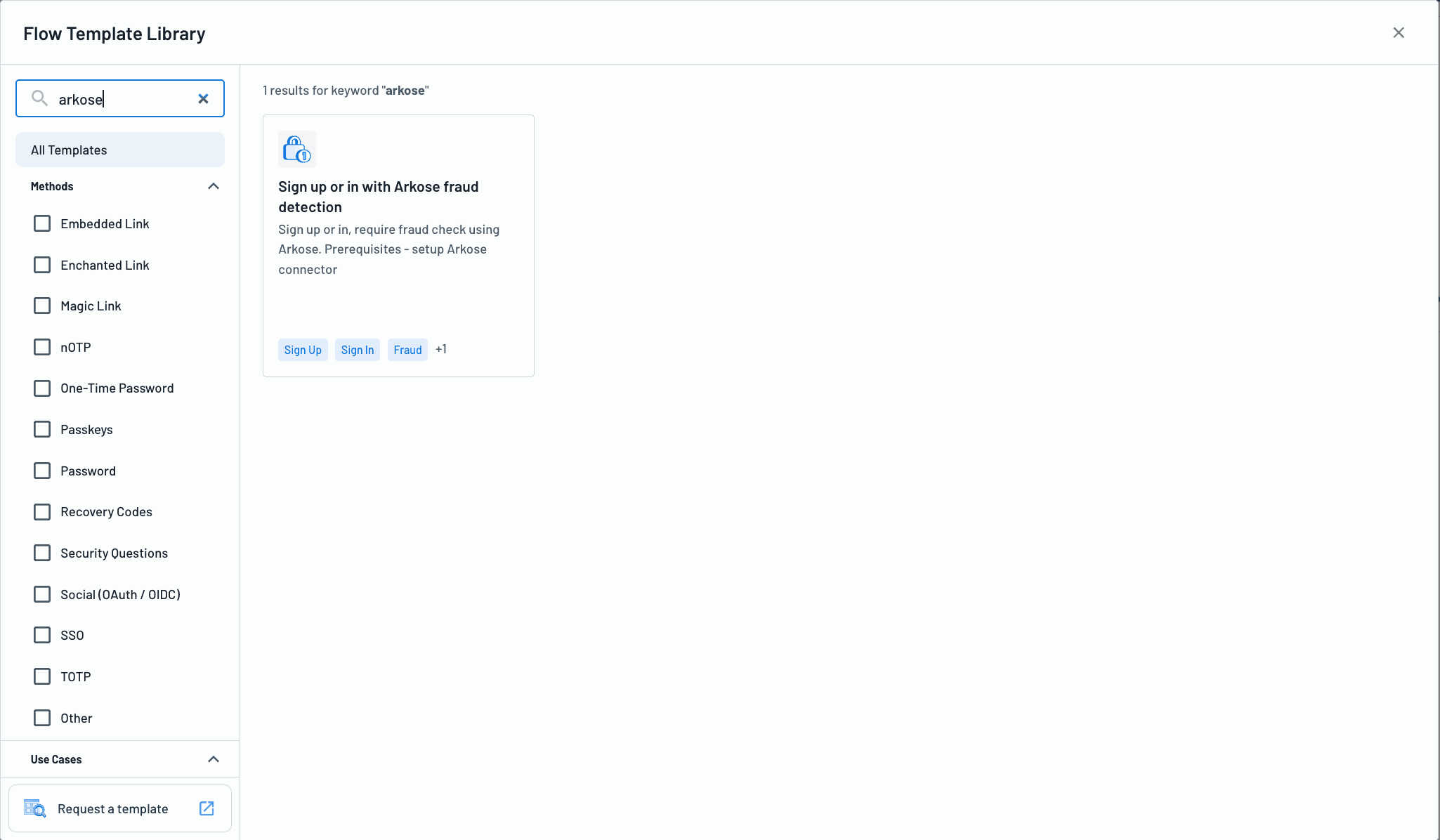
Get started today by using the Sign up or in with Arkose fraud detection Flow Template, available directly in the Descope Console.
Use case: Prevent account takeover through behavioral analysis
Account takeover attempts often exhibit subtle behavioral signatures. Examples include rapid successive login attempts across multiple accounts, unusual access patterns from unfamiliar devices, or authentication requests originating from known fraud infrastructure.
The following sequence illustrates how a Descope Flow can use Arkose Bot Manager to evaluate login risk:
Multiple authentication requests are made and Arkose Bot Manager loads within Descope authentication flows.
Behavioral, device, and network signals are collected at login.
Device ID fingerprints the request and compares it to historical device activity.
Signals are analyzed against human baselines and threat intelligence.
Descope allows, challenges with MFA, or blocks the attempt.
This layered approach adapts authentication requirements based on real-time risk, reducing friction for legitimate users while hardening defenses against targeted account compromise.
Use case: Detect and block low-and-slow attacks
Low-and-slow attacks intentionally distribute authentication attempts across time and IP addresses to evade rate limiting and threshold-based detection. Arkose Bot Manager's device fingerprinting and bot detection signals identify persistent attack infrastructure regardless of IP rotation or temporal distribution.
The following sequence illustrates how a Descope Flow can use Arkose Bot Manager to identify distributed, low-and-slow authentication attacks:
Attacker rotates IPs and throttles requests to stay below rate limits.
Arkose Device ID fingerprints the underlying device/automation tool.
Bot detection signals identify consistent automation patterns across distributed attempts.
Repeated failed authentication attempts from the same device fingerprint—across different IPs and time windows—trigger risk elevation.
Descope Flow enforces adaptive challenges or blocks based on cumulative device reputation and bot signals.
This device-centric detection model defeats distributed attack infrastructure that traditional network-layer controls cannot effectively mitigate.
Use case: Block automation framework reconnaissance
Attackers often use automation frameworks to probe authentication endpoints for valid usernames, rate limit thresholds, and security control behaviors before launching full-scale attacks.
The following example illustrates how automation-driven reconnaissance can be detected and blocked in a Descope Flow:
Automation frameworks probe the authentication endpoint.
Arkose detects scripted interaction and browser automation signals.
Device ID identifies headless browsers or virtualized environments.
Arkose returns a risk assessment based on automation confidence.
Descope challenges, blocks, or logs the attempt based on severity.
This prevents attackers from mapping authentication behaviors and tuning attack parameters before launching credential stuffing or brute force campaigns.
Conclusion
The Descope Arkose Bot Manager Connector provides production-grade bot mitigation for authentication endpoints, enabling security teams to detect and block credential stuffing, account takeover, and automated attacks without custom integration engineering. By embedding Arkose Lab's bot detection signals and Arkose Device ID into declarative authentication flows, developers can deploy adaptive, risk-based security controls that scale with attack sophistication.
If you want to explore how the Arkose Labs connector works, check out our docs. If you haven’t yet started your Descope journey, sign up for a Free Forever account and set up your own Arkose Labs connector. To explore other connectors, visit our integrations page.






